Worksheet 1 (Router Programming)
... LAB_A (config-if)# exit LAB_A (config)# int e1 LAB_A (config-if)# ip address 205.7.5.1 255.255.255.0 LAB_A (config-if)# no shutdown LAB_A (config-if)# exit LAB_A (config)# int s0 LAB_A (config-if)# ip address 201.100.11.1 255.255.255.0 LAB_A (config-if)# clock rate 56000 LAB_A (config-if)# no shutdo ...
... LAB_A (config-if)# exit LAB_A (config)# int e1 LAB_A (config-if)# ip address 205.7.5.1 255.255.255.0 LAB_A (config-if)# no shutdown LAB_A (config-if)# exit LAB_A (config)# int s0 LAB_A (config-if)# ip address 201.100.11.1 255.255.255.0 LAB_A (config-if)# clock rate 56000 LAB_A (config-if)# no shutdo ...
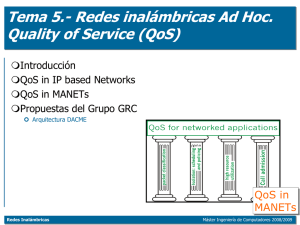
Redes Inalámbricas
... protocol based on the ideas of both DSDV and DSR. We also know that when a node in AODV desires to send a message to some destination node it initiates a Route ...
... protocol based on the ideas of both DSDV and DSR. We also know that when a node in AODV desires to send a message to some destination node it initiates a Route ...
ZebOS Network Platform Troubleshooting Guide
... This documentation is subject to change without notice. The software described in this document and this documentation are furnished under a license agreement or nondisclosure agreement. The software and documentation may be used or copied only in accordance with the terms of the applicable agreemen ...
... This documentation is subject to change without notice. The software described in this document and this documentation are furnished under a license agreement or nondisclosure agreement. The software and documentation may be used or copied only in accordance with the terms of the applicable agreemen ...
Avoiding traceroute anomalies with Paris traceroute - Events
... balancing, Paris traceroute cannot perfectly enumerate all paths in all situations. But it can do considerably better than the classic traceroute, and it can flag those instances where there are doubts. Maintaining certain header fields constant is challenging because traceroute still needs to be able ...
... balancing, Paris traceroute cannot perfectly enumerate all paths in all situations. But it can do considerably better than the classic traceroute, and it can flag those instances where there are doubts. Maintaining certain header fields constant is challenging because traceroute still needs to be able ...
Chapter 1
... Consider the traffic from the router’s viewpoint. in: Traffic that is arriving on the interface. out: Traffic that has already been routed by the router and is leaving the interface. CCNA4-54 ...
... Consider the traffic from the router’s viewpoint. in: Traffic that is arriving on the interface. out: Traffic that has already been routed by the router and is leaving the interface. CCNA4-54 ...
Multicast_I
... •A unicast address identifies a single IP interface •A broadcast address identifies all IP interfaces on the subnet •A multicast address identifies a set of IP interfaces •A multicast datagram is received only by those interfaces interested in the datagram (applications wishing to participate in the ...
... •A unicast address identifies a single IP interface •A broadcast address identifies all IP interfaces on the subnet •A multicast address identifies a set of IP interfaces •A multicast datagram is received only by those interfaces interested in the datagram (applications wishing to participate in the ...
PDF
... devices using Global System for Mobile Communications (GSM), General Packet Radio Service (GPRS), Node Bs using HSPA or LTE, base transceiver stations (BTSs) using Enhanced Data Rates for GSM Evolution (EDGE), Code Division Multiple Access (CDMA), CDMA-2000, EVDO, or WiMAX, and other cell-site equip ...
... devices using Global System for Mobile Communications (GSM), General Packet Radio Service (GPRS), Node Bs using HSPA or LTE, base transceiver stations (BTSs) using Enhanced Data Rates for GSM Evolution (EDGE), Code Division Multiple Access (CDMA), CDMA-2000, EVDO, or WiMAX, and other cell-site equip ...
IPv6 Here and Now
... • AARNet has 2001:388::/32, and can not advertise smaller blocks than this – no longer “small allocations” to sites, but large chunks to “aggregators”. • Can have multiple addresses, which provides the same as multi-homing. ...
... • AARNet has 2001:388::/32, and can not advertise smaller blocks than this – no longer “small allocations” to sites, but large chunks to “aggregators”. • Can have multiple addresses, which provides the same as multi-homing. ...
Network Working Group S. Blake Request for
... general forwarding behaviors than relative delay or discard priority. An example of a service marking model is IPv4 TOS as defined in [RFC1349]. In this example each packet is marked with a request for a "type of service", which may include "minimize delay", "maximize throughput", "maximize reliabil ...
... general forwarding behaviors than relative delay or discard priority. An example of a service marking model is IPv4 TOS as defined in [RFC1349]. In this example each packet is marked with a request for a "type of service", which may include "minimize delay", "maximize throughput", "maximize reliabil ...
paced invocations - Google Project Hosting
... SCTP combines best features of TCP and UDP and adds several new features SCTP can be used to improve network fault tolerance and improve QoS Under normal network conditions, SCTP compares well with TCP and UDP – In addition, it can utilize redundant links to provide higher effective throughput ...
... SCTP combines best features of TCP and UDP and adds several new features SCTP can be used to improve network fault tolerance and improve QoS Under normal network conditions, SCTP compares well with TCP and UDP – In addition, it can utilize redundant links to provide higher effective throughput ...
Impact of IPsec and 6to4 on VoIP Quality over IPv6
... offers a solution to this problem as well as several others, it requires Teredo gateways, Teredo relays, and Teredoaware clients. Issues related to implementing Teredo servers and the performance of public Teredo servers is described in [4]. We do not include Teredo in the present study due to the i ...
... offers a solution to this problem as well as several others, it requires Teredo gateways, Teredo relays, and Teredoaware clients. Issues related to implementing Teredo servers and the performance of public Teredo servers is described in [4]. We do not include Teredo in the present study due to the i ...
Chapter 7 - Lehigh CSE
... Payload Type (7 bits): Indicates type of encoding currently being used. If sender changes encoding in middle of conference, sender informs receiver via payload type field. •Payload type 0: PCM mu-law, 64 kbps •Payload type 3, GSM, 13 kbps •Payload type 7, LPC, 2.4 kbps •Payload type 26, Motion JPEG ...
... Payload Type (7 bits): Indicates type of encoding currently being used. If sender changes encoding in middle of conference, sender informs receiver via payload type field. •Payload type 0: PCM mu-law, 64 kbps •Payload type 3, GSM, 13 kbps •Payload type 7, LPC, 2.4 kbps •Payload type 26, Motion JPEG ...
Chapter 7 outline
... If you use these slides (e.g., in a class) in substantially unaltered form, that you mention their source (after all, we’d like people to use our book!) If you post any slides in substantially unaltered form on a www site, that you note that they are adapted from (or perhaps identical to) our sl ...
... If you use these slides (e.g., in a class) in substantially unaltered form, that you mention their source (after all, we’d like people to use our book!) If you post any slides in substantially unaltered form on a www site, that you note that they are adapted from (or perhaps identical to) our sl ...
mobicom-old - Computer Science, Columbia University
... requirements – RSVP (IntServ) – DiffServ with DSCPs – PDP context ...
... requirements – RSVP (IntServ) – DiffServ with DSCPs – PDP context ...
SpeedStream - Bell Customer Support Centre
... 2. Restrictions. The license granted is a limited license. You may NOT: sublicense, assign, or distribute copies of the Software to others; decompile, reverse engineer, disassemble or otherwise reduce the Software or any part thereof to a human perceivable form; modify, adapt, translate or create de ...
... 2. Restrictions. The license granted is a limited license. You may NOT: sublicense, assign, or distribute copies of the Software to others; decompile, reverse engineer, disassemble or otherwise reduce the Software or any part thereof to a human perceivable form; modify, adapt, translate or create de ...
cPacket Networks - Semantic Scholar
... increased in 2009. Furthermore, new regulations put more responsibility on brokers and exchanges to ensure that trades are executed at the best available price. Distributed trading applications with their ultra low latency requirements, where milliseconds and microseconds matter, coexist with other ...
... increased in 2009. Furthermore, new regulations put more responsibility on brokers and exchanges to ensure that trades are executed at the best available price. Distributed trading applications with their ultra low latency requirements, where milliseconds and microseconds matter, coexist with other ...
Wireless Router Setup Manual
... • Wireless: The wireless light (2) should be lit after turning on the router. • Internet: The Internet port light (3) should be lit. If not, make sure the Ethernet cable is securely attached to the wireless router Internet port and the modem, and the modem is powered on. • LAN: A LAN light (4) shoul ...
... • Wireless: The wireless light (2) should be lit after turning on the router. • Internet: The Internet port light (3) should be lit. If not, make sure the Ethernet cable is securely attached to the wireless router Internet port and the modem, and the modem is powered on. • LAN: A LAN light (4) shoul ...
Ch11
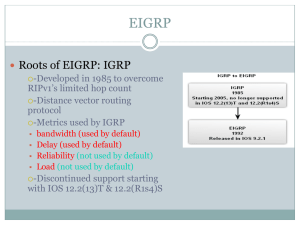
... 11-7 DISTANCE VECTOR ROUTING Distance vector and link state routing are both interior routing protocols. They can be used inside an autonomous system. Both of these routing protocols become intractable when the domain of operation becomes large. Distance vector routing is subject to instability if ...
... 11-7 DISTANCE VECTOR ROUTING Distance vector and link state routing are both interior routing protocols. They can be used inside an autonomous system. Both of these routing protocols become intractable when the domain of operation becomes large. Distance vector routing is subject to instability if ...
Integrating Cisco Press Resources into the
... – During the initial discovery process, link-state routing protocols flood the network with LSAs • Significantly decreases the network’s capability to transport data • This is temporary, but noticeable ...
... – During the initial discovery process, link-state routing protocols flood the network with LSAs • Significantly decreases the network’s capability to transport data • This is temporary, but noticeable ...
Document
... TCP/IP Protocol Suite Copyright © The McGraw-Hill Companies, Inc. Permission required for reproduction or display. ...
... TCP/IP Protocol Suite Copyright © The McGraw-Hill Companies, Inc. Permission required for reproduction or display. ...
Wireless Router Setup Manual 4500 Great America Parkway Santa Clara, CA 95054 USA
... Note: If you are configuring the router from a wireless computer and you change the router’s SSID, channel, or security settings, you will lose your wireless connection when you click Apply. You must then change the wireless settings of your computer to match the router’s new settings. 6. Configure ...
... Note: If you are configuring the router from a wireless computer and you change the router’s SSID, channel, or security settings, you will lose your wireless connection when you click Apply. You must then change the wireless settings of your computer to match the router’s new settings. 6. Configure ...
A Traffic-aware Power Management Protocol for
... arrange the sleep mode of each node to conserve energy. However, the high complexity and overhead are incurred. Flat schemes do not maintain the hierarchical structure. SPAN [14] forms a multi-hop forwarding backbone to preserve the original capacity of the network. Other nodes can go to sleep more ...
... arrange the sleep mode of each node to conserve energy. However, the high complexity and overhead are incurred. Flat schemes do not maintain the hierarchical structure. SPAN [14] forms a multi-hop forwarding backbone to preserve the original capacity of the network. Other nodes can go to sleep more ...
JNCIA Study Guide - Open Shortest Path First (OSPF)
... to send a Unicast hello packet to that neighbor within the specified hello interval period. 2-Way The 2-Way state indicates that the local router has received a hello packet with its own router ID in the Neighbor field. Thus, bidirectional communication has been established and the peers are now OSP ...
... to send a Unicast hello packet to that neighbor within the specified hello interval period. 2-Way The 2-Way state indicates that the local router has received a hello packet with its own router ID in the Neighbor field. Thus, bidirectional communication has been established and the peers are now OSP ...