Document
... – moderate overload condition maintained for an extended amount of time or – by the sudden arrival of a very large amount of traffic (traffic burst). ...
... – moderate overload condition maintained for an extended amount of time or – by the sudden arrival of a very large amount of traffic (traffic burst). ...
Lecture 4: Network Layer Security
... used for address translation. LSR is also used to implement mobility in IP networks. • LSR uses a source routing option in TCP/IP to record the set of routers a packet must visit. • The destination of the packet is replaced with the next router the packet must visit. • The name LSR comes from the fa ...
... used for address translation. LSR is also used to implement mobility in IP networks. • LSR uses a source routing option in TCP/IP to record the set of routers a packet must visit. • The destination of the packet is replaced with the next router the packet must visit. • The name LSR comes from the fa ...
CCNA 2
... o The connection between Branch1 and the networks inside OSPF domain requires only one command. You have to reach Branch2 LAN, the serial link HQ-B2 and the HQ’s Loopback1 from any host in Branch1 LANs. The packets will pass through B1-B2 Link. A default static route is not valid. o The connection b ...
... o The connection between Branch1 and the networks inside OSPF domain requires only one command. You have to reach Branch2 LAN, the serial link HQ-B2 and the HQ’s Loopback1 from any host in Branch1 LANs. The packets will pass through B1-B2 Link. A default static route is not valid. o The connection b ...
Chapter 1. Introduction to Data Communications
... John Wiley & Sons, Inc. The purchaser may make back-up copies for his/her own use only and not for distribution or resale. The Publisher assumes no responsibility for errors, omissions, or damages caused by the use of these programs or from the use of the information herein. Copyright 2011 John Wile ...
... John Wiley & Sons, Inc. The purchaser may make back-up copies for his/her own use only and not for distribution or resale. The Publisher assumes no responsibility for errors, omissions, or damages caused by the use of these programs or from the use of the information herein. Copyright 2011 John Wile ...
Chapter 1. Introduction to Data Communications
... John Wiley & Sons, Inc. The purchaser may make back-up copies for his/her own use only and not for distribution or resale. The Publisher assumes no responsibility for errors, omissions, or damages caused by the use of these programs or from the use of the information herein. Copyright 2011 John Wile ...
... John Wiley & Sons, Inc. The purchaser may make back-up copies for his/her own use only and not for distribution or resale. The Publisher assumes no responsibility for errors, omissions, or damages caused by the use of these programs or from the use of the information herein. Copyright 2011 John Wile ...
Lecture01
... Relative importance of bandwidth and “distance” for a small message (e.g. 1 byte), distance (1 ms vs. 100 ms propagation time) is more ...
... Relative importance of bandwidth and “distance” for a small message (e.g. 1 byte), distance (1 ms vs. 100 ms propagation time) is more ...
session2-layer3
... Campus Networking Best Practices Session 2: Layer 3 Dale Smith University of Oregon & NSRC [email protected] ...
... Campus Networking Best Practices Session 2: Layer 3 Dale Smith University of Oregon & NSRC [email protected] ...
Packet Switching
... IRTF (Internet Research Task Force): The Internet Research Task Force is a composed of a number of focused, long-term and small Research Groups. Internet Architecture Board (IAB): The IAB is responsible for defining the overall architecture of the Internet, providing guidance and broad direction ...
... IRTF (Internet Research Task Force): The Internet Research Task Force is a composed of a number of focused, long-term and small Research Groups. Internet Architecture Board (IAB): The IAB is responsible for defining the overall architecture of the Internet, providing guidance and broad direction ...
Evaluating OSPF
... Dijkstra’a SPF (Shortest path first) algorithm used to compute shortest path in terms of COST (OSPF metric), and result stored in RIB(routing information database) OSPF RIB is collection of best paths to each destination, installed in Routing table When information in link state database changes, on ...
... Dijkstra’a SPF (Shortest path first) algorithm used to compute shortest path in terms of COST (OSPF metric), and result stored in RIB(routing information database) OSPF RIB is collection of best paths to each destination, installed in Routing table When information in link state database changes, on ...
R7200 SDSL Routers
... users, branch offices, and business partners. Integrated PPTP Access Concentrator (PAC) and Network Server (PNS) functionality compatible with Microsoft Windows 95/98/NT Dial-Up Networking clients and NT Servers. Can replace NT server to provide VPN access to remote users. Also includes ATMP for int ...
... users, branch offices, and business partners. Integrated PPTP Access Concentrator (PAC) and Network Server (PNS) functionality compatible with Microsoft Windows 95/98/NT Dial-Up Networking clients and NT Servers. Can replace NT server to provide VPN access to remote users. Also includes ATMP for int ...
PPT Version
... Example 4: Triggers for Transport Problem: An access link can go up, go down and change rate Solution: TrigTran intermediary to notify transport end systems of such events Issue: Such notifications should be performed in a secure manner ...
... Example 4: Triggers for Transport Problem: An access link can go up, go down and change rate Solution: TrigTran intermediary to notify transport end systems of such events Issue: Such notifications should be performed in a secure manner ...
Fall 2008 - 2 Hours - School of Computer Science
... Assume that four (4) datagrams are received in sequence and are then checked for parity errors. The first datagram bit string contains the 7-bit pattern 1011010, followed by the second datagram pattern 0000111, third datagram pattern 1111110, and fourth datagram pattern 0110011. Each of the bit patt ...
... Assume that four (4) datagrams are received in sequence and are then checked for parity errors. The first datagram bit string contains the 7-bit pattern 1011010, followed by the second datagram pattern 0000111, third datagram pattern 1111110, and fourth datagram pattern 0110011. Each of the bit patt ...
A Value-based Framework for Internet Peering Agreements
... • What should be the destination? Can be either destination IP address, prefix, or MPLS tunnel endpoint – Need to observe sufficient flow volume – We choose MPLS tunnel endpoint ...
... • What should be the destination? Can be either destination IP address, prefix, or MPLS tunnel endpoint – Need to observe sufficient flow volume – We choose MPLS tunnel endpoint ...
Binary Soliton-Like Rateless Coding for the Y
... protocol in the presence of a single source in a session is the RSD. Proof: Suppose that S2 has left the network. In this case, R can assume that only degree-zero packets have been received from S2. ...
... protocol in the presence of a single source in a session is the RSD. Proof: Suppose that S2 has left the network. In this case, R can assume that only degree-zero packets have been received from S2. ...
Click to add title
... – Non-real time phase self-organizes p-cycles – Real time phase is essentially BLSR switching – p-cycles in continual self-test while in “storage” • Centralized “oversight” but not low-level control – Method is autonomous, adaptive • Networks actual state on the ground is the database ...
... – Non-real time phase self-organizes p-cycles – Real time phase is essentially BLSR switching – p-cycles in continual self-test while in “storage” • Centralized “oversight” but not low-level control – Method is autonomous, adaptive • Networks actual state on the ground is the database ...
05. Reference Models and Example Networks
... joining of another regional networks - NSFNET, BITNET, EARN, …, thousands of LANs; early 90’ the term “internet” widely accepted as net name “The Internet” Internet machine is each machine that (1) inter-communicates with others under TCP/IP and (2) has a specific IP address. ...
... joining of another regional networks - NSFNET, BITNET, EARN, …, thousands of LANs; early 90’ the term “internet” widely accepted as net name “The Internet” Internet machine is each machine that (1) inter-communicates with others under TCP/IP and (2) has a specific IP address. ...
Introduction to computer networkd #9
... – R1 checks its routing table and finds that the next hop for the route to the network for Host B is router R2. – If Host A and R2 are on the same network that is also directly attached to R1, an ICMP Redirect message is sent to Host A informing it that R2 is the better route when sending to Host B. ...
... – R1 checks its routing table and finds that the next hop for the route to the network for Host B is router R2. – If Host A and R2 are on the same network that is also directly attached to R1, an ICMP Redirect message is sent to Host A informing it that R2 is the better route when sending to Host B. ...
lecture14_1
... Lack of information about other AS’s network (Link-state not possible) Crossing trust boundaries Link-state protocol will not scale Routing protocol based on route propogation ...
... Lack of information about other AS’s network (Link-state not possible) Crossing trust boundaries Link-state protocol will not scale Routing protocol based on route propogation ...
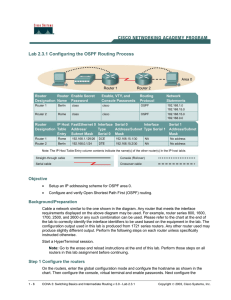
Lab 2.3.1 Configuring the OSPF Routing Process Objective
... Step 6 Configure OSPF routing on router Rome a. Configure an OSPF routing process on each router Rome. Use OSPF process number 1 and ensure all networks are in area 0. Rome(config)#router ospf 1 Rome(config-router)#network 192.168.0.0 0.0.0.255 area 0 Rome(config-router)#network 192.168.15.0 0.0.0.3 ...
... Step 6 Configure OSPF routing on router Rome a. Configure an OSPF routing process on each router Rome. Use OSPF process number 1 and ensure all networks are in area 0. Rome(config)#router ospf 1 Rome(config-router)#network 192.168.0.0 0.0.0.255 area 0 Rome(config-router)#network 192.168.15.0 0.0.0.3 ...
PowerPoint version
... Flow Label: identify datagrams in same “flow.” (concept of“flow” not well defined). Next header: identify upper layer protocol for data ...
... Flow Label: identify datagrams in same “flow.” (concept of“flow” not well defined). Next header: identify upper layer protocol for data ...
SEMESTER 1 Chapter 5
... within a very small LAN, in a LAN that requires low throughput requirements, or when finances are limited. What does a switch do regenerates each bit of the frame on to the when it receives a frame? appropriate destination port What is the advantage of A switch segments a network into multiple using ...
... within a very small LAN, in a LAN that requires low throughput requirements, or when finances are limited. What does a switch do regenerates each bit of the frame on to the when it receives a frame? appropriate destination port What is the advantage of A switch segments a network into multiple using ...
network
... transport 5. Data flow begins network 4. Call connected data link 1. Initiate call physical ...
... transport 5. Data flow begins network 4. Call connected data link 1. Initiate call physical ...