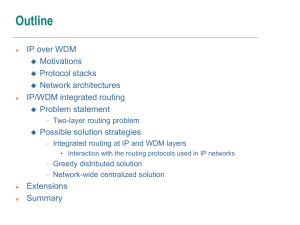
Basic Concepts
... Figure 1-24: Cryptographic Protections • Message-by-Message Protections – Encryption to provide confidentiality so that an eavesdropper cannot reach intercepted messages – Electronic signatures provide message-by-message authentication to prevent the insertion of messages by an impostor after initi ...
... Figure 1-24: Cryptographic Protections • Message-by-Message Protections – Encryption to provide confidentiality so that an eavesdropper cannot reach intercepted messages – Electronic signatures provide message-by-message authentication to prevent the insertion of messages by an impostor after initi ...
Broadband Services Router BSR 64000
... The BSR 64000 delivers the per-flow packet treatment needed to enable end-to-end SLAs across broadband access networks – including handoffs to metropolitan or core networks using Diff-Serv and/or MultiProtocol Label Switching (MPLS). High-density interfaces to locally-attached Web or video caches re ...
... The BSR 64000 delivers the per-flow packet treatment needed to enable end-to-end SLAs across broadband access networks – including handoffs to metropolitan or core networks using Diff-Serv and/or MultiProtocol Label Switching (MPLS). High-density interfaces to locally-attached Web or video caches re ...
IP Optical Networks - City University of New York
... Currently OSPF Link State Advertisements (LSAs) mainly include operator-assigned link weights Shortest-path algorithms used to determine routing table entries based on these link weights (Dijkstra’s, Bellman-Ford) Example: Shortest path from R3 to R7 is via R4 and R5 ...
... Currently OSPF Link State Advertisements (LSAs) mainly include operator-assigned link weights Shortest-path algorithms used to determine routing table entries based on these link weights (Dijkstra’s, Bellman-Ford) Example: Shortest path from R3 to R7 is via R4 and R5 ...
Convergence VoIP
... • Voice over IP (VoIP) indicates that an analog voice signal has been digitized and converted into the packet format used by IP. This is done in order to allow telephony and other audio signals to be transported over the same network as regular data traffic. Thus, VoIP refers to a conversion and tra ...
... • Voice over IP (VoIP) indicates that an analog voice signal has been digitized and converted into the packet format used by IP. This is done in order to allow telephony and other audio signals to be transported over the same network as regular data traffic. Thus, VoIP refers to a conversion and tra ...
Routing Scalability
... • If an application can implement a functionality correctly, implement it a lower layer only as performance enhancement but iff it does not impose burden on applications that do not require that functionality • Don’t put application semantics in network: leads to loss of flexibility – Cannot change ...
... • If an application can implement a functionality correctly, implement it a lower layer only as performance enhancement but iff it does not impose burden on applications that do not require that functionality • Don’t put application semantics in network: leads to loss of flexibility – Cannot change ...
TDC 363 Local Area Networks
... technology for both TDM-based circuit switched networks, and most overlay data networks • Unfortunately, SONET has a number of shortcomings ...
... technology for both TDM-based circuit switched networks, and most overlay data networks • Unfortunately, SONET has a number of shortcomings ...
Simulation was carried out with the help of ns 2.29
... AODV is an on-demand routing protocol. The AODV algorithm gives an easy way to get change in the link situation. For example if a link fails notifications are sent only to the affected nodes in the network. This notification cancels all the routes through this affected node. It builds unicast routes ...
... AODV is an on-demand routing protocol. The AODV algorithm gives an easy way to get change in the link situation. For example if a link fails notifications are sent only to the affected nodes in the network. This notification cancels all the routes through this affected node. It builds unicast routes ...
Lecture 6
... Layers of a Network • Networking is complex • Networking is divided into several layers • Each layer represents a different level of abstraction between the physical hardware and the information to be transmitted • Layering: the grouping of the communication functions into related and manageable se ...
... Layers of a Network • Networking is complex • Networking is divided into several layers • Each layer represents a different level of abstraction between the physical hardware and the information to be transmitted • Layering: the grouping of the communication functions into related and manageable se ...
Chapter 4 Routing Protocols
... hoc routing. In Proceedings of the ACM/IEEE International Conference on Mobile Computing and Networking, pages 70–84, Rome, Italy, July 2001. ...
... hoc routing. In Proceedings of the ACM/IEEE International Conference on Mobile Computing and Networking, pages 70–84, Rome, Italy, July 2001. ...
Chapter1
... Q: How to provide circuit-like behavior? bandwidth guarantees needed for audio/video apps still an unsolved problem (chapter 7) ...
... Q: How to provide circuit-like behavior? bandwidth guarantees needed for audio/video apps still an unsolved problem (chapter 7) ...
old_Ch1
... has an internet routing part and a local routing part. Subnet addressing was introduced to facilitate the routing and administration within organizations. If forms part of the local part and does not affect the internet routing. IPv4 has 5 address classes. An organization is assigned an address spac ...
... has an internet routing part and a local routing part. Subnet addressing was introduced to facilitate the routing and administration within organizations. If forms part of the local part and does not affect the internet routing. IPv4 has 5 address classes. An organization is assigned an address spac ...
Semester 4 Chapter 6 - Institute of Technology Sligo
... When your routers are parts of different networks or subnets, then you must either physically attach them on different interfaces or use subinterfaces on a single interface. First step is to set the encapsulation type of the serial interface and state no IP address. RouterA(config)#int s0 RouterA(co ...
... When your routers are parts of different networks or subnets, then you must either physically attach them on different interfaces or use subinterfaces on a single interface. First step is to set the encapsulation type of the serial interface and state no IP address. RouterA(config)#int s0 RouterA(co ...
ppt - University of Alberta
... • Reliability: the probability that a system operates without a service-affecting failure for a given amount of time. R(t) can be thought of as the probability distribution function of timeto-first-failure from a known-good starting state. • Availability: the probability that a continuously operatin ...
... • Reliability: the probability that a system operates without a service-affecting failure for a given amount of time. R(t) can be thought of as the probability distribution function of timeto-first-failure from a known-good starting state. • Availability: the probability that a continuously operatin ...
Document
... Circuit-switched network was unacceptable for the Internet. Data had to be able to move through different routes so that if one circuit went down, it didn’t affect communication on the rest of the network. ...
... Circuit-switched network was unacceptable for the Internet. Data had to be able to move through different routes so that if one circuit went down, it didn’t affect communication on the rest of the network. ...
ECE544_Lec5_DR08
... – Multihomed AS: large corporation (no transit): multiple connections to other AS’s – Transit AS: provider, hooking many AS’s together ...
... – Multihomed AS: large corporation (no transit): multiple connections to other AS’s – Transit AS: provider, hooking many AS’s together ...
Internet In A Slice - Princeton University
... Ingress assigns a private IP address to client All of the client’s packets are sent into the overlay ...
... Ingress assigns a private IP address to client All of the client’s packets are sent into the overlay ...
4Links Flexible SpaceWire Router, FSR
... In a SpaceWire network, the only way to monitor traffic from within the network is inside the routing switches. The FSR-RG408 provides a means to monitor traffic statistics in the routing switch and hence in the network, together with the Network layer routing switch capabilities specified in the EC ...
... In a SpaceWire network, the only way to monitor traffic from within the network is inside the routing switches. The FSR-RG408 provides a means to monitor traffic statistics in the routing switch and hence in the network, together with the Network layer routing switch capabilities specified in the EC ...
PPT - CS.Duke
... • Establish multicast forwarding state – Flood to all destinations (reverse path flooding) • Key design challenge: loop-avoidance • Q: how many broadcast loop-avoidance mechanisms have we learned? – Prone those not in the group ...
... • Establish multicast forwarding state – Flood to all destinations (reverse path flooding) • Key design challenge: loop-avoidance • Q: how many broadcast loop-avoidance mechanisms have we learned? – Prone those not in the group ...
group7
... The router will flood its connected hosts for a response , If a router that is closer than to the host than the Routing Controller, it will respond with the packet. The host will discard any duplicate packet it received ...
... The router will flood its connected hosts for a response , If a router that is closer than to the host than the Routing Controller, it will respond with the packet. The host will discard any duplicate packet it received ...
1 - Harding University
... CIDR impacts routing & forwarding Routing tables and routing protocols must carry IP address and mask Multiple entries may match a given IP destination address Example: Routing table may contain ...
... CIDR impacts routing & forwarding Routing tables and routing protocols must carry IP address and mask Multiple entries may match a given IP destination address Example: Routing table may contain ...
Introduction to Multimedia Systems
... PT: payload type. For example, 7 is for LPC audio, and 34 is for H263 video. ...
... PT: payload type. For example, 7 is for LPC audio, and 34 is for H263 video. ...
Week_Seven_Network_ppt
... IS-IS is a routing protocol designed to move information efficiently within a computer network, a group of physically connected computers or similar devices. It accomplishes this by determining the best route for datagrams through a packet-switched network. The protocol was defined in ISO/IEC 10589: ...
... IS-IS is a routing protocol designed to move information efficiently within a computer network, a group of physically connected computers or similar devices. It accomplishes this by determining the best route for datagrams through a packet-switched network. The protocol was defined in ISO/IEC 10589: ...