* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Document
Survey
Document related concepts
Deep packet inspection wikipedia , lookup
Zero-configuration networking wikipedia , lookup
IEEE 802.11 wikipedia , lookup
Internet protocol suite wikipedia , lookup
Computer network wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Network tap wikipedia , lookup
Nonblocking minimal spanning switch wikipedia , lookup
IEEE 802.1aq wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Airborne Networking wikipedia , lookup
Multiprotocol Label Switching wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Virtual LAN wikipedia , lookup
Spanning Tree Protocol wikipedia , lookup
Transcript
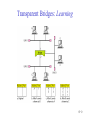
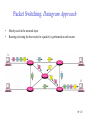
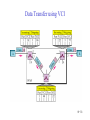
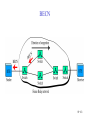
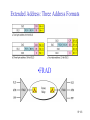
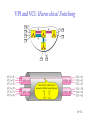
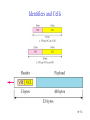
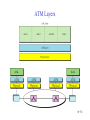
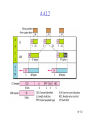
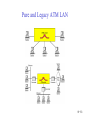
Connecting LANs, Backbone Networks, and Virtual LANs • • • Connecting devices Backbone networks Virtual LANs 15-1 Five Categories of Connecting Devices • • • • • Below the physical layer: passive hub At the physical layer: repeater or active hub At the physical and data link layers: bridge or two-layer switch At the physical, data link, network layers: router or three-layer switch At all five layers: gateway 15-2 Repeater • • • • A repeater operates only in the physical layers A repeater connects segments of a LAN A repeater forwards every frame; it has no filtering capability The repeater is a two-port device that extends the LANs’ physical length 15-3 Function of a Repeater • A repeater is a regenerator, not an amplifier 15-4 Active Hubs • • • An active hub is actually a multiport repeater It is normally used to create connections between stations in a star topology Hubs can also be used to create multiple levels of hierarchy; removing the length limitation of 10Base-T (100m) 15-5 Repeaters/Hubs 15-6 Bridges • • • A bridge operates in both physical and data link layers A bridge has filtering capability: Having a table used in filtering decisions A bridge can check, does not change the physical (MAC) addresses in a frame 15-7 Bridges • Transparent bridges – A bridge in which the stations are completely unaware of the bridge’s existence – Three criteria for a transparent bridge • Frames must forward from one station to another • The forwarding table is automatically made by learning frame movements in the network • Loops in the system must be prevented • Source routing bridges – A sending station defines the bridges that the frame must visit – Not very common today – It can prevent loops in a system with redundant bridges 15-8 Transparent Bridges: Learning 15-9 Loop Problem in a Learning Bridge 15-10 Transparent Bridges: Spanning Tree • • Spanning tree is a graph in which there is no loop To solve the looping problem, IEEE spec requires that bridges use the spanning tree algorithm 1. Select the root bridge • The one with the smallest built-in ID 2. Select the root port of each bridge • The port with the least-cost path from the bridge to the root bridge 3. Choose a designated bridge for each LAN • • The bridge with the least-cost path from the LAN to the root bridge The corresponding port is the designated port 4. Mark the root port and designated port as forwarding port, others as blocking port 15-11 Spanning Tree: Graph Representation 15-12 Spanning Tree:Finding the Shortest Path 15-13 Spanning Tree: Forwarding and Blocking Ports 15-14 Bridges Connecting Different LANs • • • • • • • Many technical issues to connect LANs using different protocols at the data link layer Frame format Maximum data size Data rate Bit order Security Multimedia support and QoS 15-15 Two-Layer (Layer 2) Switch • Layer 2 switch is an N-port bridge • Ethernet switch or LAN switch • Switched Ethernet (←) • Full-duplex switched Ethernet (↓) 15-16 Two-Layer and Three-Layer Switch • Two-Layer Switch : bridge with many ports – Filtering based on the MAC address of the frame it received – Builds switching table by “learning” host addresses from source addresses of incoming packets – Unknown destination addresses are flooded out other ports – Broadcast frames are flooded out other ports • Router – Three-layer device that routes packets based on their logical (network layer) address. – Builds routing table by neighbor routers using routing protocols – Unknown IP packets are discarded – Broadcast frames are discarded • Three-Layer Switch : a router, but a faster and more sophisticated – Router and three-layer switch interchangeably 15-17 Broadcast and Collision Domains 15-18 LAN Segmentation 15-19 Backbone Network: Bus Backbone • • The topology of the backbone is a bus To connect different buildings in an organization 15-20 Star Backbone • • • Collapsed or switched backbone The topology of the backbone is a star; the backbone is just one switch Mostly used as a distribution backbone inside a building 15-21 Connecting Remote LANs • • • When a company has several offices with LANs Remote bridges A point-to-point link acts as a LAN in a remote backbone connected by remote bridges 15-22 Virtual LANs • • LAN configured by software, not by physical wiring VLANs create broadcast domains 15-23 Example • Membership is characterized by port numbers, MAC addresses, IP addresses, multicast IP addresses or a combination of the above 15-24 VLAN • Membership – • Configuration – • VLAN can be configured in one of three ways: manual, semiautomatic, and automatic Communication between switches – – • Membership is characterized by port numbers, MAC addresses, IP addresses, Multicast IP addresses, or a combination of the above Each switch must know not only which station belongs to which VLAN, but also the membership of stations connected to other switches Three methods are devised: table maintenance, frame tagging, and TDM Advantages of VLAN – – – Cost and time reduction Creating virtual workgroups Security 15-25 Virtual-Circuit Networks: Frame Relay and ATM • Frame Relay • ATM • ATM LANs 18-26 Wide area network and switching methods 18-27 Circuit switching • • Create a real circuit (dedicated line) between source and destination Physical layer technology 18-28 Packet Switching: Datagram Approach • • Mostly used in the network layer Routing (selecting the best route for a packet) is performed at each router 18-29 Packet Switching: Virtual Circuit Approach • • Packets (frames) are switched along a pre-determined path from source to destination Virtual circuit network has two addresses – Global address which is unique in the WAN – Virtual circuit identifier which is actually used for data transfer • • VCI has switch scope; it is used between two switches Each switch can use its own unique set of VCIs 18-30 VCI Phases • Two approaches for the VC setup – Permanent virtual circuit (PVC): – Switched virtual circuit (SVC): setup, data transfer, teardown 18-31 Data Transfer Phase • All switches need to have a table entry for the virtual circuit 18-32 Data Transfer using VCI 18-33 SVC Setup: Request and Acknowledgment 18-34 Frame Relay • • Frame Relay is a virtual circuit wide area network VCIs in Frame Relay are called DLCIs(Data Link Connection Identifier) 18-35 Frame Relay Features • • • • • • • Frame relay operates at a higher speed. It can easily be used instead of a mesh of T1 or T-3 lines (1.544 Mbps or 44.376 Mbps) Frame relay operates just the physical and data link layers. It is good as a backbone to provide services to protocols that already have a network layer protocol, such as Internet It allows bursty data It allows a frame size of 9000 bytes accommodating all LAN frame sizes It is less expensive than other traditional WANs It has error detection at the data link layer only. There is no flow control pr error control X.25 Leased Lines Frame Relay 18-36 Frame Relay vs. T-line Network 18-37 Frame Relay vs. X.25 Network 18-38 Frame Relay Layers • Frame relay operates only at the physical and data link layers 18-39 Comparing Layers: X.25 & Frame Relay 18-40 Frame Relay Frame 18-41 Congestion Control • Frame relay requires congestion control, because – Frame Relay does not have a network layer – No flow control at the data link layer – Frame Relay allows the user to transmit bursty data • Congestion avoidance – Two bits in the frame are used – BECN(Backward Explicit Congestion Notification) – FECN(Forward Explicit Congestion Notification) • Discard eligibility(DE): – Priority level of the frame for traffic control – Discarding frame to avoid the congestion or collapsing 18-42 BECN 18-43 FECN 18-44 Four Cases of Congestion 18-45 Extended Address: Three Address Formats •FRAD 18-46 ATM • • • • • Asynchronous Transfer Mode ATM is the cell relay protocol designed by ATM forum and adopted by ITU-T ATM uses asynchronous TDM Cells are transmitted along virtual circuits Design Goals – – – – – – Large bandwidth and less susceptible to noise degradation Interface with existing systems without lowering their effectiveness Inexpensive implementation Support the existing telecommunications hierarchies Connection-oriented to ensure accurate and predictable delivery Many functions are hardware implementable 18-47 Multiplexing using Cells • • The variety of packet sizes makes traffic unpredictable A cell network uses the cell as the basic unit of data exchange – A cell is defined as a small, fixed sized block of information – Cells are interleaved so that non suffers a long delay – A cell network can handle real-time transmissions – Network operation is more efficient and cheaper 18-48 Synchronous vs. Asynchronous TDM 18-49 ATM Architecture • UNI: user-to-network interface • NNI: network-to-network interface 18-50 Virtual Connection • Connection between two endpoints is accomplished through – Transmission path (TP) – Virtual path (VP) – Virtual circuit (VC) • A virtual connection is defined by a pair of numbers: VPI and VCI 18-51 VPI and VCI: Hierarchical Switching 18-52 Identifiers and Cells 18-53 VP Switch and VPC Switch 18-54 ATM Layers 18-55 ATM Layer and Headers 18-56 Application Adaptation Layer (AAL) • • • • • Convert data from upper-layer into 48-byte data units for the ATM cells AAL1 – constant bit rate (CBR) video and voice AAL2 – variable bit rate (VBR) stream low-bit-rate traffic an short-frame traffic such as audio (ex: mobile phone) AAL3/4 – connection-oriented/connectionless data AAL5 – SEAL (Simple and Efficient Adaptation Layer) No sequencing and error control mechanisms 18-57 AAL1 18-58 AAL2 18-59 AAL3/4 18-60 AAL5 18-61 ATM LAN • ATM is mainly a wide-area network (WAN ATM); however, the technology can be adapted to local-area networks (ATM LANs). The high data rate of the technology has attracted the attention of designers who are looking for greater and greater speeds in LANs. 18-62 Pure and Legacy ATM LAN 18-63 Mixed Architecture ATM LAN 18-64 LAN Emulation (LANE) • • • • Connectionless versus connection-oriented Physical addresses versus virtual-circuit identifiers Multicasting and broadcasting delivery Interoperability • Client/Server model in a LANE – LANE Configuration Server (LECS), LANE Server (LES), LANE Client (LEC) – Broadcast/Unknown Server (BUS) 18-65 Mixed Architecture Using LANE 18-66