* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download network
Survey
Document related concepts
Wireless security wikipedia , lookup
IEEE 802.1aq wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Distributed firewall wikipedia , lookup
Deep packet inspection wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Computer network wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Network tap wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Airborne Networking wikipedia , lookup
Internet protocol suite wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Transcript
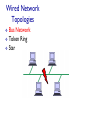
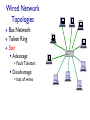
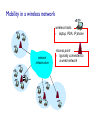
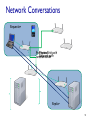
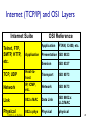
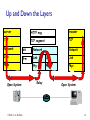
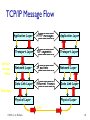
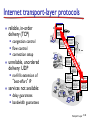
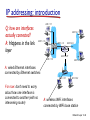
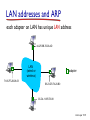
CSCI411 Introduction to Computer Networking ©2011, MA Doman 1 Today – General Overview Introduce basic concepts and vocabulary Networking overview Internet: What is the internet Architecture Layers ©2011 MA Doman 2 What is a Network? Basically, the collection of elements needed to enable information exchange between people, systems, or people and systems Hardware • End points, routers, switches.. Software • Protocols, end applications .. Transmission media • Wires, air … Services • Reliability • Completeness of messages ©2011 MA Doman 3 Wired Network Topologies Bus Network Token Ring Star Wired Network Topologies Bus Network Token Ring Star Wired Network Topologies Bus Network Token Ring Star Advantage: • Fault Tolerant Disadvantage: • lots of wires Mobility in a wireless network wireless hosts r laptop, PDA, IP phone network infrastructure Access point r typically connected to a wired network Mobility in a wireless network Ad hoc mode r no base stations r nodes can only transmit to other nodes within link coverage r nodes organize themselves into a network: route among themselves Network Structure Local-Area Network (LAN) – designed to cover small geographical area. Wide-Area Network (WAN) – links geographically separated sites What’s the Internet ? Internet: “network of networks” mobile network Interconnected ISPs protocols control sending, receiving of msgs e.g., TCP, IP, HTTP, Skype, 802.11 global ISP Internet standards home network regional ISP RFC: Request for comments IETF: Internet Engineering Task Force institutional network Introduction 1-11 A closer look at network structure: network edge: mobile network hosts: clients and servers servers often in data centers access networks, physical media: wired, wireless communication links global ISP home network regional ISP network core: interconnected routers network of networks institutional network Introduction 1-12 Network Conversations Requester End-to-end Physical link path Network path communication Replier 13 What’s a protocol? human protocols: “what’s the time?” “I have a question” introductions … specific msgs sent … specific actions taken when msgs received, or other events network protocols: machines rather than humans all communication activity in Internet governed by protocols protocols define format, order of msgs sent and received among network entities, and actions taken on msg transmission, receipt Introduction 1-14 A Layered Architecture… also known as a Stack of Protocols LAYERS: Each system is viewed logically as composed of an ordered set of subsystems. INTERFACE: Adjacent subsystems in the vertical hierarchy (the layers) communicate through a common boundary. ENTITIES: Functional module of each layer. Entities in the same layer but installed on different systems are called “peer” entities. PROTOCOLS: Peer entities communicate through peer “protocols” at the appropriate (containing) layer. 16 The OSI Reference Model Open Systems Interconnection, OSI Adopted as an international standard in 1983 identifies functions and services that are fundamental to providing reliable, cost-effective, secure, and transparent communications defines the concept of layered architecture in terms of functions, services, and protocols became a framework for defining standards for linking heterogeneous computers… NO precise definition of how the functions would be accomplished is the basis for connecting “open” systems for distributed application processing by creating and implementing a protocol stack ©2005, L.A. DeNoia 17 OSI Layers OSI Reference Application FTAM, X.400, etc. Presentation ISO 8823 Session ISO 8327 Transport ISO 8073 Network ISO 8473 Data Link ISO 8802.x LLC/MAC Physical physical ©2005, L.A. DeNoia 18 Internet protocol stack application: supporting network applications FTP, SMTP, HTTP transport: process-process data transfer Application Transport TCP, UDP network: routing of datagrams from source to destination IP, routing protocols link: data transfer between neighboring network elements Ethernet, 802.111 (WiFi), PPP Network Link Physical physical: bits “on the wire” Introduction 1-19 Internet (TCP/IP) and OSI Layers Internet Suite OSI Reference Application Telnet, FTP, SMTP, HTTP, etc. Application TCP, UDP FTAM, X.400, etc. Presentation ISO 8823 Session ISO 8327 Host-tohost Transport ISO 8073 Network IP, ICMP, etc. Network ISO 8473 Link 802.x MAC Data Link ISO 8802.x LLC/MAC Physical 802.x phys Physical physical ©2005, L.A. DeNoia 20 Up and Down the Layers server HTTP msg browser TCP TCP segment TCP Network Link pkt Network frm Link Link Link Phy Phys Phys Phys bits Open System A Network Relay Node Open System B router ©2005, L.A. DeNoia 21 View of Encapsulation TCP hdr IP hdr Linkh dr MAC hdr User Data TCP segment Network segment Link layer segment MAC trlr MAC frame ©2005, L.A. DeNoia 22 TCP/IP Message Flow Application Layer Service Access Point HTTP messages Application Layer Transport Layer TCP segments Transport Layer Network Layer IP packets Network Layer Data Link Layer Ethernet frames Data Link Layer Interface Physical Layer Physical Layer bits ©2005, L.A. DeNoia 23 Application Layer User Message Application hdr Transport layer hdr Network layer hdr Link Layer hdr MAC hdr Payload Payload Payload Payload MAC trlr MAC frame ©2010, M.A.Doman 24 Creating a network app write programs that: run on (different) end systems communicate over network e.g., web server software communicates with browser software no need to write software for network-core devices network-core devices do not run user applications applications on end systems allows for rapid app development, propagation application transport network data link physical application transport network data link physical application transport network data link physical Application Layer 2-25 Client-server architecture server: always-on host permanent IP address data centers for scaling clients: client/server communicate with server may be intermittently connected may have dynamic IP addresses do not communicate directly with each other Application Layer 2-26 P2P architecture no always-on server arbitrary end systems directly communicate peers request service from other peers, provide service in return to other peers self scalability – new peers bring new service capacity, as well as new service demands peers are intermittently connected and change IP addresses complex management peer-peer Application Layer 2-27 What transport service does an app need? data integrity some apps (e.g., file transfer, web transactions) require 100% reliable data transfer other apps (e.g., audio) can tolerate some loss timing some apps (e.g., Internet telephony, interactive games) require low delay to be “effective” throughput some apps (e.g., multimedia) require minimum amount of throughput to be “effective” other apps (“elastic apps”) make use of whatever throughput they get security encryption, data integrity, … Application Layer 2-28 DNS: domain name system Domain Name System: distributed database implemented in hierarchy of many name servers application-layer protocol: hosts, name servers communicate to resolve names (address/name translation) note: core Internet function, implemented as applicationlayer protocol complexity at network’s “edge” DNS services hostname to IP address translation host aliasing canonical, alias names mail server aliasing load distribution replicated Web servers: many IP addresses correspond to one name Application Layer 2-29 DNS: a distributed, hierarchical database Root DNS Servers … com DNS servers yahoo.com amazon.com DNS servers DNS servers … org DNS servers pbs.org DNS servers edu DNS servers poly.edu umass.edu DNS serversDNS servers client wants IP for www.amazon.com; 1st approx: client queries root server to find com DNS server client queries .com DNS server to get amazon.com DNS server client queries amazon.com DNS server to get IP address for www.amazon.com Application Layer 2-30 Processes communicating process: program running within a host within same host, two processes communicate using inter-process communication (defined by OS) processes in different hosts communicate by exchanging messages clients, servers client process: process that initiates communication server process: process that waits to be contacted aside: applications with P2P architectures have client processes & server processes Application Layer 2-31 Sockets process sends/receives messages to/from its socket socket analogous to door sending process shoves message out door sending process relies on transport infrastructure on other side of door to deliver message to socket at receiving process application process socket application process transport transport network network link physical Internet link controlled by app developer controlled by OS physical Application Layer 2-32 Addressing processes to receive messages, process must have identifier host device has unique 32bit IP address Q: does IP address of host on which process runs suffice for identifying the process? A: no, many processes can be running on same host identifier includes both IP address and port numbers associated with process on host. example port numbers: HTTP server: 80 mail server: 25 to send HTTP message to gaia.cs.umass.edu web server: IP address: 128.119.245.12 port number: 80 Application Layer 2-33 Transport layer User Message Application hdr Transport layer hdr Network layer hdr Link Layer hdr MAC hdr Payload Payload Payload Payload MAC trlr MAC frame ©2010, M.A.Doman 34 Transport services and protocols provide logical communication between app processes running on different hosts transport protocols run in end systems send side: breaks app messages into segments, passes to network layer rcv side: reassembles segments into messages, passes to app layer more than one transport protocol available to apps Internet: TCP and UDP application transport network data link physical application transport network data link physical Transport Layer 3-35 Internet transport-layer protocols reliable, in-order delivery (TCP) congestion control flow control connection setup unreliable, unordered delivery: UDP no-frills extension of “best-effort” IP services not available: application transport network data link physical network data link physical network data link physical network data link physical network data link physical network data link physical network data link physical network data link physical application transport network data link physical delay guarantees bandwidth guarantees Transport Layer 3-36 Internet transport protocols services TCP service: UDP service: reliable transport between sending and receiving process flow control: sender won’t overwhelm receiver congestion control: throttle sender when network overloaded does not provide: timing, minimum throughput guarantee, security connection-oriented: setup required between client and server processes unreliable data transfer between sending and receiving process does not provide: reliability, flow control, congestion control, timing, throughput guarantee, security, orconnection setup, Q: why bother? Why is there a UDP? Application Layer 2-37 Network layer User Message Application hdr Transport layer hdr Network layer hdr Link Layer hdr MAC hdr Payload Payload Payload Payload MAC trlr MAC frame ©2010, M.A.Doman 38 Network layer transport segment from sending to receiving host on sending side encapsulates segments into datagrams on receiving side, delivers segments to transport layer network layer protocols in every host, router router examines header fields in all IP datagrams passing through it application transport network data link physical network data link physical network data link physical network data link physical network data link physical network data link physical network data link physical network data link physical network data link physical network data link physical network data link physical network data link physical application transport network data link physical Network Layer 4-39 Routing Strategies Fixed routing - A path from A to B is specified in advance; path changes only if a hardware failure disables it Since the shortest path is usually chosen, communication costs are minimized Virtual circuit - A path from A to B is fixed for the duration of one session. Different sessions involving messages from A to B may have different paths Partial remedy to adapting to load changes Ensures that messages will be delivered in the order in which they were sent Router architecture overview two key router functions: run routing algorithms/protocol (RIP, OSPF, BGP) forwarding datagrams from incoming to outgoing link forwarding tables computed, pushed to input ports routing processor routing, management control plane (software) forwarding data plane (hardware) high-seed switching fabric router input ports router output ports Network Layer 4-41 IP addressing: introduction Q: how are interfaces actually connected? A: Happens in the link layer 223.1.1.1 223.1.2.1 223.1.1.2 223.1.1.4 223.1.1.3 223.1.2.9 223.1.3.27 223.1.2.2 A: wired Ethernet interfaces connected by Ethernet switches 223.1.3.1 For now: don’t need to worry about how one interface is connected to another (with no intervening router) 223.1.3.2 A: wireless WiFi interfaces connected by WiFi base station Network Layer 4-42 NAT: network address translation rest of Internet local network (e.g., home network) 10.0.0/24 10.0.0.1 10.0.0.4 10.0.0.2 138.76.29.7 10.0.0.3 all datagrams leaving local network have same single source NAT IP address: 138.76.29.7,different source port numbers datagrams with source or destination in this network have 10.0.0/24 address for source, destination (as usual) Network Layer 4-43 Routing Strategies (Cont.) Dynamic routing - The path used to send a message form site A to site B is chosen only when a message is sent Usually a site sends a message to another site on the link least used at that particular time Adapts to load changes by avoiding routing messages on heavily used path Messages may arrive out of order • This problem can be remedied by appending a sequence number to each message Connection Strategies Circuit switching - A permanent physical link is established for the duration of the communication (i.e., telephone system) Message switching - A temporary link is established for the duration of one message transfer (i.e., post-office mailing system) Packet switching - Messages of variable length are divided into fixed-length packets which are sent to the destination Each packet may take a different path through the network The packets must be reassembled into messages as they arrive Circuit switching requires setup time, but incurs Contention Several sites may want to transmit information over a link simultaneously. Techniques to avoid repeated collisions include: CSMA/CD - Carrier sense with multiple access (CSMA); collision detection (CD) A site determines whether another message is currently being transmitted over that link. If two or more sites begin transmitting at exactly the same time, then they will register a CD and will stop transmitting When the system is very busy, many collisions may occur, and thus performance may be degraded CSMA/CD is used successfully in the Ethernet system, the most common Contention (Cont.) Token passing - A unique message type, known as a token, continuously circulates in the system (usually a ring structure) A site that wants to transmit information must wait until the token arrives When the site completes its round of message passing, it retransmits the token A token-passing scheme is used by some IBM and HP/Apollo systems Message slots - A number of fixed-length message slots continuously circulate in the system (usually a ring structure) Since a slot can contain only fixed-sized messages, a Link Layer of Encapsulation User Message Application hdr Transport layer hdr Network layer hdr Link Layer hdr MAC hdr Payload Payload Payload Payload MAC trlr MAC frame ©2010, M.A.Doman 48 Link layer: introduction terminology: hosts and routers: nodes communication channels that connect adjacent nodes along communication path: links wired links wireless links LANs layer-2 packet: frame, encapsulates datagram global ISP data-link layer has responsibility of transferring datagram from one node to physically adjacent node over a link Link Layer 5-49 Link layer services framing, link access: encapsulate datagram into frame, adding header, trailer channel access if shared medium “MAC” addresses used in frame headers to identify source, dest • different from IP address! reliable delivery between adjacent nodes we learned how to do this already (chapter 3)! seldom used on low bit-error link (fiber, some twisted pair) wireless links: high error rates • Q: why both link-level and end-end reliability? Link Layer 5-50 Link layer services (more) flow control: pacing between adjacent sending and receiving nodes error detection: errors caused by signal attenuation, noise. receiver detects presence of errors: • signals sender for retransmission or drops frame error correction: receiver identifies and corrects bit error(s) without resorting to retransmission half-duplex and full-duplex with half duplex, nodes at both ends of link can transmit, but not at same time Link Layer 5-51 Where is the link layer implemented? in each and every host link layer implemented in “adaptor” (aka network interface card NIC) or on a chip Ethernet card, 802.11 card; Ethernet chipset implements link, physical layer attaches into host’s system buses combination of hardware, software, firmware application transport network link cpu memory controller link physical host bus (e.g., PCI) physical transmission network adapter card Link Layer 5-52 Channel partitioning MAC protocols: TDMA TDMA: time division multiple access access to channel in "rounds" each station gets fixed length slot (length = pkt trans time) in each round unused slots go idle example: 6-station LAN, 1,3,4 have pkt, slots 2,5,6 idle 6-slot frame 6-slot frame 1 3 4 1 3 4 Link Layer 5-53 Channel partitioning MAC protocols: FDMA FDMA: frequency division multiple access channel spectrum divided into frequency bands each station assigned fixed frequency band unused transmission time in frequency bands go idle example: 6-station LAN, 1,3,4 have pkt, frequency bands 2,5,6 idle FDM cable frequency bands Link Layer 5-54 Random Access Check for collision Transmit only if the line is free 5-55 MAC addresses and ARP 32-bit IP address: network-layer address for interface used for layer 3 (network layer) forwarding MAC (or LAN or physical or Ethernet) address: function: used ‘locally” to get frame from one interface to another physically-connected interface (same network, in IPaddressing sense) 48 bit MAC address (for most LANs) burned in NIC ROM, also sometimes software settable e.g.: 1A-2F-BB-76-09-AD hexadecimal (base 16) notation (each “number” represents 4 bits) Link Layer 5-56 LAN addresses and ARP each adapter on LAN has unique LAN address 1A-2F-BB-76-09-AD LAN (wired or wireless) adapter 71-65-F7-2B-08-53 58-23-D7-FA-20-B0 0C-C4-11-6F-E3-98 Link Layer 5-57 Thank You! Be sure to start the first lab: Introduction to the OpNet Simulator 58