* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download lectures5-6
Survey
Document related concepts
Multiprotocol Label Switching wikipedia , lookup
Deep packet inspection wikipedia , lookup
IEEE 802.1aq wikipedia , lookup
SIP extensions for the IP Multimedia Subsystem wikipedia , lookup
Network tap wikipedia , lookup
Computer network wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Airborne Networking wikipedia , lookup
Internet protocol suite wikipedia , lookup
Wake-on-LAN wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Transcript
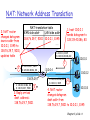
Chapter 4: Network Layer Introduction IP: Internet Protocol IPv4 addressing NAT IPv6 Routing algorithms Link state Distance Vector Routing in the Internet RIP OSPF BGP Chapter 4, slide: 1 Sharing an IP address Home networks, other small LANs Expensive to have unique IP address for each host Want to share internet access through just one IP address Want to maintain security/privacy Install router … but how does it work? Chapter 4, slide: 2 Network Address Translation NAT is an extension of the original IP addressing scheme Motivated by exhaustion of IP address space Allows multiple computers at one site to share a single global IP address Requires a device to perform packet translation In-line configuration All traffic entering or leaving the network must go through the NAT device Should be transparent to all users • Virtual private connection Chapter 4, slide: 3 NAT: Network Address Translation local network uses just one IP address as far as outside world is concerned (external address) range of addresses not needed from ISP: just one IP address for all devices can change addresses of devices in local network without notifying outside world can change ISP / external address without changing addresses of devices in local network devices inside local net not explicitly addressable by outside world (a security plus). Chapter 4, slide: 4 NAT: Network Address Translation rest of Internet local network (e.g., home network) 10.0.0/24 10.0.0.4 10.0.0.1 10.0.0.2 138.76.29.7 10.0.0.3 All datagrams leaving local network have same single source NAT IP address: 138.76.29.7, different source port numbers Datagrams with source or destination in this network have 10.0.0/24 address for source, destination (as usual) Chapter 4, slide: 5 Implementation To send datagram out to the internet from a computer in the private network: Computer constructs datagram with source address and destination address, sends to NAT box NAT box translates the source address in the datagram to the site's IP address NAT keeps source and destination addresses in its translation table Note: checksum must be recalculated and datagram must be reconstructed Chapter 4, slide: 6 Implementation To forward an incoming datagram from the internet to a computer in the private network: Datagrams arrive addressed to the site's IP address NAT finds source and destination addresses in its translation table NAT changes the destination address in the datagram to the internal address for the target computer NAT reconstructs the datagram (with new checksum, etc.) and forwards it to the computer in the private network Chapter 4, slide: 7 Implementation Software solutions Standard PC with • NAT software, e.g.: – Linux masquerade – Windows RRAS (Routing and Remote Access Server) • extra NIC required OK for slower speed networks (e.g., 10 Mbps) NAT box must translate addresses in time for the usual network functions to work • detecting congestion, etc. Hardware solutions Special-purpose hardware for high-speed networks (e.g., gigabit Ethernet) Hybrid solutions Routers can incorporate software for NAT Used in medium-speed networks (e.g., 100 Mbps) Chapter 4, slide: 8 Virtual connection The effect of NAT is to form a virtual private connection between a computer in a private network and a remote host (internet site). Of course, the connection may be to a computer in a separate private network (through another NAT box) Internal communications do not use the NAT box Chapter 4, slide: 9 Problems with basic NAT If two computers inside the private network both want to communicate with the same external site, the basic translation table is not sufficient If one computer inside the private network is running applications with two remote hosts, the basic translation table is not sufficient If a remote site wants to make the first contact with a computer inside the private network, there will be no translation table entry. Chapter 4, slide: 10 NAPT Network Address and Port Translation Most popular implementation of NAT Usually just called NAT Keeps track of local addresses and IP addresses Also can keep track of (and change) TCP and UDP protocol port numbers Allows • multiple computers in the private network to communicate with a single destination • multiple applications on a single computer in the private network to communicate with multiple destinations Chapter 4, slide: 11 Example NAPT table Entry in table records protocol port number as well as IP address Port numbers are re-assigned to avoid conflicts Note: this requires the NAT box (router) to have some transport-layer functionality Direction Initial value Translated Unchanged out IP SRC:TCP SRC 10.0.0.125:30000 IP SRC:TCP SRC 128.210.24.6:40001 IP DST:TCP DST 68.18.6.225:80 out IP SRC:TCP SRC 10.0.0.77:30000 IP SRC:TCP SRC 128.210.24.6:40002 IP DST:TCP DST 68.18.6.225:80 in IP DST:TCP DST 128.210.24.6:40001 IP DST:TCP DST 10.0.0.125:30000 IP SRC:TCP SRC 68.18.6.225:80 in IP DST:TCP DST 128.210.24.6:40002 IP DST:TCP DST 10.0.0.77:30000 IP SRC:TCP SRC 68.18.6.225:80 Chapter 4, slide: 12 NAT table For an out-going datagram: Source address is changed to the site address. Source port number is re-assigned and recorded Checksum is recalculated Datagram is reconstructed Destination address / port number are not changed Translation table records • Internal source address / original port number • Destination address / re-assigned source port number Chapter 4, slide: 13 NAT table For an in-coming datagram: Destination address is changed to the internal address recorded in the translation table. Destination port number is changed to the port number recorded in the translation table. Checksum is recalculated Datagram is reconstructed Source address / port number are not changed Chapter 4, slide: 14 NAT: Network Address Translation 2: NAT router changes datagram source addr from 10.0.0.1, 3345 to 138.76.29.7, 5001, updates table 2 NAT translation table WAN side addr LAN side addr 1: host 10.0.0.1 sends datagram to 128.119.40.186, 80 138.76.29.7, 5001 10.0.0.1, 3345 …… …… S: 10.0.0.1, 3345 D: 128.119.40.186, 80 S: 138.76.29.7, 5001 D: 128.119.40.186, 80 138.76.29.7 S: 128.119.40.186, 80 D: 138.76.29.7, 5001 3: Reply arrives dest. address: 138.76.29.7, 5001 3 1 10.0.0.4 S: 128.119.40.186, 80 D: 10.0.0.1, 3345 10.0.0.1 10.0.0.2 4 10.0.0.3 4: NAT router changes datagram dest addr from 138.76.29.7, 5001 to 10.0.0.1, 3345 Chapter 4, slide: 15 First contact When initial contact is attempted from outside the site, there is no translation table entry E.G., a private network might be running multiple servers through a NAT system Chapter 4, slide: 16 NAT traversal problem client wants to connect to server with address 10.0.0.1 server address 10.0.0.1 local to LAN (client can’t use it as destination addr) only one externally visible NAT’ed address: 138.76.29.7 Client 10.0.0.1 ? 10.0.0.4 138.76.29.7 NAT router Chapter 4, slide: 17 NAT traversal problem Solution 1: statically configure NAT to forward incoming connection requests at given port to server e.g., (123.76.29.7, port 2500) always forwarded to 10.0.0.1 port 25000 Client 10.0.0.1 ? 10.0.0.4 138.76.29.7 NAT router Chapter 4, slide: 18 NAT traversal problem Solution 2: Universal PnP Internet Gateway Device (IGD) Protocol. Allows NAT’ed host to: map (private IP, private port #) with (public IP, public port #) advertise (public IP, public port #) 10.0.0.1 So DNS can work IGD add/remove port mappings 10.0.0.4 138.76.29.7 NAT router Chapter 4, slide: 19 Summary: Network Address Translation 16-bit port-number field: ~65,000 simultaneous connections with a single LAN-side address! NAT is controversial. Objections include: • routers should only process up to layer 3 • address shortage should instead be solved by IPv6 Chapter 4, slide: 20 Chapter 4: Network Layer Introduction Virtual circuit and datagram networks IP: Internet Protocol IPv4 addressing NAT IPv6 Routing algorithms Link state Distance Vector Routing in the Internet RIP OSPF BGP Chapter 4, slide: 21 IPv6 Initial motivation: 32-bit address space soon to be completely allocated. Additional motivation: header changes to facilitate QoS Major changes from IPv4: Fragmentation: no longer allowed; drop packet if too big Checksum: removed to reduce processing time; already done at transport and link layers Options: allowed, but outside of header, indicated by “Next Header” field Chapter 4, slide: 22 New features of IPv6 Support for audio and video “flow labels” and “quality of service” allow audio and video applications to establish appropriate connections Extensible new features can be added more easily Chapter 4, slide: 23 IPv6 datagram format Chapter 4, slide: 24 IPv6 base header format Chapter 4, slide: 25 IPv6 base header Contains less information than IPv4 header VERSION (4 bits) TRAFFIC CLASS (8 bits) • specifies the traffic class (used to choose a route) FLOW LABEL (20 bits) PAYLOAD LENGTH (16 bits) NEXT HEADER (8 bits) HOP LIMIT (8 bits) (old TTL) • used to associate datagrams belonging to a flow or communication between two applications • indicates the length of data (i.e. payload) excluding header • points to first extension header • specifies the maximum number of hops a packet can travel through before being discarded SOURCE ADDRESS (128 bits) DESTINATION ADDRESS (128 bits) Chapter 4, slide: 26 NEXT header Chapter 4, slide: 27 Parsing IPv6 headers Base header is fixed size - 40 octets NEXT HEADER field in base header defines type of next header Next header appears at end of fixed-size base header Some extensions headers are variable sized NEXT HEADER field in extension header defines type HEADER LEN field gives size of extension header Chapter 4, slide: 28 Multiple headers Efficiency header only as large as necessary Flexibility can add new headers for new features Incremental development can add processing for new features Chapter 4, slide: 29 Fragmentation and Path MTU Fragmentation information is in fragmentation extension header IPv6 source (not intermediate routers) is responsible for fragmentation Source must find path MTU Routers simply drop datagrams larger than path MTU No more fragmenting by routers ICMP message sent to source Must be dynamic - path may change during transmission of datagrams Source determines path MTU Uses path MTU discovery • Source sends probe message of various sizes • Gets ICMP messages until destination reached Constructs datagrams to fit within that MTU Chapter 4, slide: 30 IPv6 addressing 128-bit addresses Includes network prefix and host suffix No address classes prefix/suffix boundary can fall anywhere Longest matching prefix Chapter 4, slide: 31 Address notation in IPv6 128-bit addresses unwieldy in dotted decimal requires 16 numbers example: • 105.220.136.100.255.255.255.255.0.0.18.128.140.10.255.255 IPv6 uses groups of 16-bit numbers in hex separated by colons colon hexadecimal (colon hex) example: • 69DC:8864:FFFF:FFFF:0:1280:8C0A:FFFF Add /bits to specify netmask example: • 69DC:8864:FFFF:FFFF:0:1280:8C0A:FFFF/64 Chapter 4, slide: 32 Address shorthand in IPv6 Zero-compression series of zeroes indicated by two colons example: • FF0C:0:0:0:0:0:0:B1 becomes • FF0C::B1 An IPv6 address with 96 leading zeros is interpreted to hold an IPv4 address Chapter 4, slide: 33 Transition From IPv4 To IPv6 Can all routers be upgraded simultaneously ?? Answer: it can’t; no “flag days” Analogy: (IP for Internet) ~ (foundation for House) To change the foundation, you need to tear down the house!! Solution gradually incorporate IPv6 (may take few years) How will the network operate with mixed IPv4 and IPv6 routers? Tunneling?? Chapter 4, slide: 34 Tunneling Logical view: Physical view: Be aware that: • • IPv6 nodes have both IPv4 & IPv6 addresses Nodes know which nodes are IPv4 and which one are IPv6 (use for e.g. DNS) A B IPv6 IPv6 A B C IPv6 IPv6 IPv4 Flow: X Src: A Dest: F data A-to-B: IPv6 E F IPv6 IPv6 D E F IPv4 IPv6 IPv6 tunnel What is the problem here? Why can’t B just send an IPv4 packet to C ? Problem: D won’t be able to send an IPv6 packet to E? Why? Chapter 4, slide: 35 Tunneling Logical view: Physical view: Be aware that: • • IPv6 nodes have both IPv4 & IPv6 addresses Nodes know which nodes are IPv4 and which one are IPv6 (use for e.g. DNS) A B IPv6 IPv6 A B C IPv6 IPv6 IPv4 Flow: X Src: A Dest: F data A-to-B: IPv6 E F IPv6 IPv6 D E F IPv4 IPv6 IPv6 tunnel Src:B Dest: E Src:B Dest: E Flow: X Src: A Dest: F Flow: X Src: A Dest: F data data B-to-C: IPv6 inside IPv4 B-to-C: IPv6 inside IPv4 Flow: X Src: A Dest: F data E-to-F: IPv6 Chapter 4, slide: 36