* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download ITGS
Survey
Document related concepts
Dynamic Host Configuration Protocol wikipedia , lookup
Network tap wikipedia , lookup
Computer security wikipedia , lookup
Computer network wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Airborne Networking wikipedia , lookup
Wireless security wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Remote Desktop Services wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Transcript
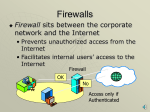
ITGS Network Architecture ITGS • Network architecture – The way computers are logically organized on a network, and the role each takes. • Client/server network - One or more computers act as servers that provide services to the rest of the network (the clients) – Many advantages because files are located on a server can be accessed by owners from any client » If a computer needs to be repaired, files are not lost since they are saved on the server, not the computer » Because the server authenticates users, security is improved ITGS • Thin client network - client computers rely heavily on a server not only to store files and applications, but run software on a client’s behalf (sometimes including even the OS) – The thin client merely acts as a terminal for accepting input and displaying output • The client only contains enough software to initialize the hardware and network connection, and connect to the server • Because this is all they do, clients have very low specifications – No secondary storage – Slow processors – Small amount of RAM ITGS • Peer-to-peer networks - every client (peer) has equal status, and there is no central authority or server – Common in homes and small businesses where a server is too expensive/ not necessary • Each computer shares the files from its own hard disk, and other machines are able to access them • With more than a few users, the lack of a server to aid in security and storage becomes a problem ITGS • Firewalls – Hardware or software that determines which data is allowed to enter and leave a network • Can be dedicated computers or built into network routers – Firewalls help secure a computer by preventing network access from unauthorized users – They also control which users and programs are allowed to connect to an external network such as the Internet • Firewalls can be configured to allow or block traffic using several methods: – IP addresses - IP addresses of specific computers can be allowed or denied access » Denial of Service (DoS) - an attack by malicious computer users that bombards a site’s servers until the site doesn’t work » In one of these attacks, the IP addresses of the attacking machines can be blocked ITGS •Domain names - access to particular websites such as social networks can be blocked by specifying their name •Protocols and ports - different protocols can be blocked or allowed as needed: •Web browsing (HTTP) •Mail (SMTP and POP3) •File transfer (FTP) •These protocols use a standard port , and the ports can be blocked as well •For example, HTTP is port 80 •Application program - individual programs can be granted or denied network access •This is most important for programs that try automatically to update themselves or update themselves ITGS • Controversy over firewalls – While they can be used for protections, governments can also use them to deny services • Proxy servers – Act as a middle step between two computers • Usually between a computer on a LAN and a web server on the internet – All communication through the two computers passes through the proxy » The proxy caches, filters, and logs data (like users’ web activity) • Caching - (saves time and bandwidth) – A process used to speed up activities like web browsing » Proxy servers keep a copy of commonly requested material, such as a web page, in a storage area called a cache. » When a user requests the webpage, the proxy server provides it from the local cache rather than retrieving it from the internet