* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Asynchronous Transfer Mode (ATM)
SIP extensions for the IP Multimedia Subsystem wikipedia , lookup
Wireless security wikipedia , lookup
Remote Desktop Services wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Dynamic Host Configuration Protocol wikipedia , lookup
Distributed firewall wikipedia , lookup
Network tap wikipedia , lookup
Airborne Networking wikipedia , lookup
Deep packet inspection wikipedia , lookup
Nonblocking minimal spanning switch wikipedia , lookup
Computer network wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Point-to-Point Protocol over Ethernet wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Asynchronous Transfer Mode
(ATM)
NETE0521
Presented by
Dr.Apichan Kanjanavapastit
Definition
• Asynchronous transfer mode (ATM) is a
high-performance, cell-oriented switching
and multiplexing technology that utilizes
fixed-length packets to carry different types
of traffic
• ATM was designed by the ATM Forum and
adopted by the ITU-T
Packet Networks
• Data communications are based on packet switching
and packet networks
• A packet is a combination of data and overhead bits that
can be passed through the network as a self-contained
unit
• The overhead provides identification and addressing
information as well as the data required for routing, flow
control, error control, and so on
• Different protocols use packets of varying size and
intricacy
• As networks become more complex, the information
carried in the header becomes more extensive
Packet Networks (con’t)
• The result is larger overhead relative to the
size of data unit
• Some protocols have enlarged the size of
data unit to make header use more
efficient
• Thus, packets can be as long as 60,000
bytes sharing long-haul links with packets
of fewer than 200 bytes
Mixed Network Traffic
• Since packet networks have unpredictable packet sizes,
switches, multiplexers, and router must incorporate
elaborate software systems to manage the various sizes
of packets
• A grate deal of header information must be read and
each bit counted and evaluated to ensure the integrity of
every packet
• Another problem is that of providing consistent data-rate
delivery when packet sizes are unpredictable and can
vary so dramatically
• To get the most out of broadband technology, traffic must
be time-division multiplexed onto shared paths
Mixed Network Traffic (con’t)
• Because audio and video packets ordinarily are small,
mixing them with conventional data traffic often creates
unacceptable delays of this type and makes shared
packet links unusable for audio and video information
router
Cell Networks
• Many of the problems associated with the packet
internetworking are solved by adoption a concept called
cell networking
• A cell is a small data unit of fixed size; thus all data
loaded into identical cells can be transmitted with
complete predictability and uniformity
• As packets of different sizes and formats reach the cell
network, they are split into multiple small data units of
equal length and loaded into cells
• The cells are then multiplexed with other cells and routed
through the cell network
• Since each cell is the same size and all are small, the
problem associated with multiplexing different-sized
packets are avoided
Cell Networks (con’t)
• In this way, a cell network can handle realtime transmission, such as phone call,
without the parties aware of the
segmentation or multiplexing at all
MUX
Asynchronous TDM
• ATM uses asynchronous time-divisionmultiplexing to multiplex cells coming from
different channels. It uses fixed-size slots the
size of a cell
• ATM multiplexers fill a slot with a cell from any
input channel that has a cell; the slot is empty if
none of the channels has a cell to send
• ATM uses fixed-size slots (total 53 bytes: 48
bytes for payload and 5 bytes for overhead)
Asynchronous TDM (con’t)
A3
A2
B2
B1
C3
C2
A1
C3
C1
B2
A3
C2
B1
A2
C1
A1
WHY USE A 48-BYTE PAYLOAD?
48 bytes corresponds to approximately 6 milliseconds of voice
• Losing one 48-byte payload wouldn’t be disruptive to a listener (a speech phoneme is
about 32 milliseconds long)
The U.S. preferred a 64-byte payload
• Studies indicated that data communication efficiency would be improved with somewhat
larger cells (i.e., less overhead per PDU)
Europe preferred a 32-byte payload
• Echo cancellers for audio wouldn’t be needed in smaller countries if PDU sizes were
kept small enough
Everyone wanted the payload size to be a power of two
• Memory transfer and switching would all be simplified
The Solution?
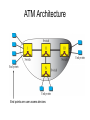
ATM Architecture
End points are user access devices
ATM Architecture (cont.)
• Virtual Connection
– Connection between two end points is accomplished through
transmission paths (TPs), virtual paths (VPs), and virtual
circuits (VCs)
• A transmission path (TP) is the physical connection (wire,
cable, satellite, and so on) between an end point and a switch or
between two switches
• A transmission path is divided into several virtual paths. A virtual
path provides a connection or a set of connections between two
switches
• Cell networks are based on virtual circuits (VCs). All cells
belonging to a single message follow the same virtual channel
and remain in their original order until they reach their destination
ATM Architecture (cont.)
Since the virtual connections need to be identified, there
are two levels of identifier: a virtual path identifier (VPI)
and a virtual circuit identifier (VCI).
VP-only Switching
ATM Layers
• The ATM standard defines three layers, from the top to
bottom, the application layer, the ATM layer, and the
physical layer. The physical and ATM layer are used in
both switches and end points. The AAL is used only by
the end points.
ATM Reference Model Relates to
the OSI Reference Model
Application Adaptation Layer (AAL)
• The AAL allows existing networks (such as
packet networks) to connect to ATM facilities
• AAL protocols accept transmissions from upperlayer services (e.g., packet data) and map them
into fixed-sized ATM cells
• These transmissions can be of any type (voice,
data, audio, and video) and can be of variable or
fixed rates
• At the receiver, this process is reversed–
segments are reassembled into their original
formats and passed to the receiving service
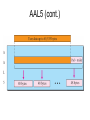
AAL (con’t)
Upper Layers
Convergence Sublayer
• Provide application-specific interface
• Handle lost and delayed cells
• Error detection and handling
Segmentation and Reassembly Sublayer
• Pack Convergence Sublayer information into 48-byte
blocks for transfer down to the ATM Layer.
• Unpack ATM Layer cells for transfer up to the
Convergence Sublayer.
ATM Layer
Physical Layer
TRAVERSING THE AAL
Application Layer
Message
Convergence Sublayer
CS
Trailer
CS
Header
Segmentation and Reassembly Sublayer
Pa
d
Segmentation and Reassembly Sublayer (continued)
SAR
Hdr
SAR
Trlr
SAR
Hdr
SAR
Trlr
SAR
Hdr
SAR
Trlr
SAR
Hdr
SAR
Trlr
SAR
Hdr
ATM Layer
ATM
Hdr
ATM
Hdr
ATM
Hdr
ATM
Hdr
ATM
Hdr
SAR
Trlr
AAL (cont.)
• AAL Type 1 supports constant bit rate (CBR),
synchronous, connection oriented traffic. Examples
include T1 (DS1), E1, and x64 kbit/s emulation.
• AAL Type 2 supports time-dependent Variable Bit Rate
(VBR-RT) of connection-oriented, synchronous traffic.
Examples include Voice over ATM. AAL2 is also widely
used in wireless applications due to the capability of
multiplexing voice packets from different users on a
single ATM connection.
• AAL Type 3/4 supports VBR, data traffic, connectionoriented, asynchronous traffic (e.g. X.25 data) or
connectionless packet data (e.g. SMDS traffic) with an
additional 4-byte header in the information payload of the
cell. Examples include Frame Relay and X.25.
AAL (cont.)
• AAL Type 5 is similar to AAL 3/4 with a
simplified information header scheme. This
AAL assumes that the data is sequential
from the end user and uses the Payload
Type Indicator (PTI) bit to indicate the last
cell in a transmission. Examples of
services that use AAL 5 are IP over ATM,
Ethernet Over ATM
AAL5
• AAL 5 is sometimes called the simple and efficient
adaptation layer (SEAL), assumes that all cells
belonging to a single message travel sequentially and
that control functions are included in the upper layers of
the sending application (addressing, sequencing, or
other header information)
• AAL5 accepts an IP packet of no more than 65,535
bytes and adds an 8-byte trailer as well as any padding
required to ensure that the position of the trailer falls
where the receiving equipment expects it (at the last 8
bytes of the last cell)
AAL5 (cont.)
ATM Layer
• The ATM layer provides
routing, traffic management,
switching, and multiplexing
services
• It processes outgoing traffic by
accepting 48-byte segments
from the AAL and transforming
them into 53-byte cells by the
addition of a 5-byte header
• Most of the header is occupied
by the VPI and VCI. The
combination of VPI and VCI
can be thought of as a label
that defines a particular virtual
connections
Physical Layer
• The physical layer defines the transmission
medium, bit transmission, encoding, and
electrical to optical transformation
• It provides convergence with physical transport
protocol such as SONET/SDH as well as the
mechanisms for transforming the flow of cells
into a flow of bits
• The ATM Forum has left most of the
specifications for this level to the implementer
QoS, PVC, and SVC
• Quality of Service (QoS) requirements are handled at
connection time and viewed as part of signaling.
• ATM provides permanent virtual connections and
switched virtual connections.
– Permanent Virtual Connections (PVC)
permanent connections set up manually by network
provider. The VPIs and VCIs are defined for the
permanent connections and the values are entered in a
table for each switch
– Switched Virtual Connections (SVC)
set up and released on demand by the end user via signaling
procedures.
ATM Signaling Protocol
• Signaling protocol consists of two parts
• User-Network Interface (UNI)
– defines how end points talk to switches
• Network-Network Interface (NNI)
– defines how switches talk to other switches
• Cell formats of the two protocols are slightly different
UNI Signaling
• UNI signaling is performed between an end station
and a private ATM switch, or between a private ATM
switch and the public ATM network
• The UNI signaling is simpler because it does not
involve routing. The standards are produced by the
ATM Forum and are called UNI 3.1 (1994) and UNI
4.0 (1996)
• UNI 4.0 is an addition to UNI 3.1, UNI 3.1 is derived
from the Public Network Signaling protocol Q.2931
brought by the ITU-T which is further derived from
Q.931 used in ISDN and Frame Relay
UNI Header Format
• GFC---4 bits of generic flow control that are used to
provide local functions, such as identifying multiple
stations that share a single ATM interface. The GFC field
is typically not used and is set to a default value.
• VPI---8 bits of virtual path identifier that is used, in
conjunction with the VCI, to identify the next destination
of a cell as it passes through a series of ATM switch
routers on its way to its destination.
• VCI---16 bits of virtual channel identifier that is used, in
conjunction with the VPI, to identify the next destination
of a cell as it passes through a series of ATM switch
routers on its way to its destination.
UNI Header Format (cont.)
• PT---3 bits of payload type. The first bit indicates
whether the cell contains user data or control
data. If the cell contains user data, the second
bit indicates congestion, and the third bit
indicates whether the cell is the last in a series
of cells that represent a single AAL5 frame.
• CLP---1 bit of congestion loss priority that
indicates whether the cell should be discarded if
it encounters extreme congestion as it moves
through the network.
• HEC---8 bits of header error control that are a
checksum calculated only on the header itself.
UNI Header Format (cont.)
NNI Signaling
• NNI signaling is performed between the switches of a
public ATM network. Since a public network generally
involves several (or many) switches the routing becomes
very important component of the NNI signaling
• NNI signaling has two major standards: IISP (Interim
Inter-switch Signaling Protocol) and PNNI (Private
Network-to-Network Interface)
• IISP is a simple signaling protocol which uses static
routing which have to be manually created and
maintained and is designed for small private ATM
networks
• PNNI is a signaling protocol that uses very elaborate
dynamic routing algorithms which can easily handle
small to large ATM networks which can have hundreds,
thousands and even tens of thousands of ATM switches
NNI Header Format
• The GFC field is not present in the format of the NNI
header. Instead, the VPI field occupies the first 12 bits,
which allows ATM switch routers to assign larger VPI
values. With that exception, the format of the NNI header
is identical to the format of the UNI header.
ATM End System Addressing
(AESA)
• All ATM switches and end stations in an ATM network must have a
unique ATM address
• The address is a crucial part of ATM signaling. This address must be
long enough to accommodate a potentially huge number of ATM
devices.
ATM End System Addressing
(AESA) (cont.)
Automatic Address Registration in UNI
• The ATM addresses (prefix only) of switches
must be entered manually by the network
manager
• Once the address is in place, each work station
(edge device) attached to that switch can now
be configured automatically
• The configuration is dynamic, it happens each
time a device is attached to the switch, or when
the device is moved from one switch to another
• Automatic address registration is performed
through the Integrated Local Management
Interface (ILMI)
Integrated Local Management Interface (ILMI)
• ILMI is based on IP's SNMP and uses a similar MIB and
access procedures like Get, Set and Trap requests and
responses
• All ILMI communications go over a dedicated (default)
VC (VPI = 0, VCI = 16)
• Each ATM device (edge device or switch) that
implements UNI (private or public) has ILMI and a
component called Interface Management Entity (IME)
• This entity acts as a symmetric component that can both
send requests and respond to a peer IME
• IME is responsible to maintain MIB and interpret/respond
to SNMP messages. There are four types of SNMP
messages used in automatic address registration: trap,
get, getnext, set
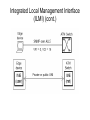
Integrated Local Management Interface
(ILMI) (cont.)
Automatic Address Registration in UNI
(cont.)
Edge Device
ATM Switch
UNI Signaling
• Once an AESA address is established the user
can place a call across an ATM network
• The calls are accomplished by a set of signaling
frames
– connection setup frames
– maintenance frames
– connection teardown frames
• All frames use dedicated VC, VPI = 0, VCI = 5
UNI Call Set-Up
NNI Signaling: IISP
• IISP (Interim Interswitch Signalling Protocol) is an extension of UNI
3.1/4.0 (approved in 1994) which includes simple hop-to-hop routing
based on AESA addresses
• Usually, the routing table has two additional fields for output ports:
the second and the third routing choice in case the link for the first
choice fails.
• For routing are used only the first n octets of the address (n is the
column indicated by "Octets to use"). An IISP routing table must be
configured by the network administrator.
NNI Signaling: IISP (cont.)
Routing Loop Problem in IISP
ATM Classes of Services
• Constant Bit Rate (CBR)
– This class is used for emulating circuit switching. The cell
rate is constant with time. CBR applications are quite
sensitive to cell-delay variation. Examples of applications
that can use CBR are telephone traffic (i.e., nx64 kbps),
videoconferencing, and television
• Variable Bit Rate–Non-Real Time (VBR–NRT)
– This class allows users to send traffic at a rate that varies
with time depending on the availability of user information.
Statistical multiplexing is provided to make optimum use of
network resources. Multimedia e-mail is an example of
VBR–NRT
ATM Classes of Services (con’t)
• Variable Bit Rate–Real Time (VBR–RT)
– This class is similar to VBR–NRT but is designed for applications
that are sensitive to cell-delay variation. Examples for real-time
VBR are voice with speech activity detection (SAD) and
interactive compressed video
• Available Bit Rate (ABR)
– This class provides rate-based flow control and is aimed at data
traffic such as file transfer and e-mail. Although the standard does
not require the cell transfer delay and cell-loss ratio to be
guaranteed or minimized, it is desirable for switches to minimize
delay and loss as much as possible. Depending upon the state of
congestion in the network, the source is required to control its
rate. The users are allowed to declare a minimum cell rate, which
is guaranteed to the connection by the network
ATM Classes of Services (con’t)
• Unspecified Bit Rate (UBR)
– The bandwidth allocation service of this class does
not guarantee any throughput levels and uses only
available bandwidth. UBR is often used when
transmitting data that can tolerate delays. The most
widely use today is the TCP/IP data
ATM Technical Parameters
• Cell Loss Ratio (CLR)
– CLR is the percentage of cells not delivered at their destination
because they were lost in the network due to congestion and
buffer overflow
• Cell Transfer Delay (CTD)
– The delay experienced by a cell between network entry and exit
points is called the CTD. It includes propagation delays, queuing
delays at various intermediate switches, and service times at
queuing points
• Cell Delay Variation (CDV)
– CDV is a measure of the variance of the cell transfer delay. High
variation implies larger buffering for delay-sensitive traffic such
as voice and video
ATM Technical Parameters (con’t)
• Peak Cell Rate (PCR)
– The maximum cell rate at which the user will transmit.
PCR is the inverse of the minimum cell inter-arrival
time
• Sustained Cell Rate (SCR)
– This is the average rate, as measured over a long
interval, in the order of the connection lifetime
• Burst Tolerance (BT)
– This parameter determines the maximum burst that
can be sent at the peak rate. This is the bucket-size
parameter for the enforcement algorithm that is used
to control the traffic entering the network
IP-over-ATM: why?
• because it’s there- use ATM network as a
link-layer to connect IP routers
• can manage traffic more carefully in ATM
network (e.g., rate-limit source/dest pairs,
provide CBR service)
• leave IP untouched – leverage the fact
that many users have IP addresses
already
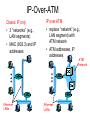
IP-Over-ATM
Classic IP only
• 3 “networks” (e.g.,
LAN segments)
• MAC (802.3) and IP
addresses
IP over ATM
• replace “network” (e.g.,
LAN segment) with
ATM network
• ATM addresses, IP
addresses
ATM
network
Ethernet
LANs
Ethernet
LANs
IP-Over-ATM
app
transport
IP
Eth
phy
IP
AAL
Eth
ATM
phy phy
ATM
phy
ATM
phy
app
transport
IP
AAL
ATM
phy
IP Over ATM
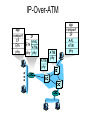
• Set of IP hosts within a same IP domain
(subnet) communicate with each other
directly over ATM network.
• The IP hosts outside their subnet
(domain)
communicate with other IP hosts in
another subnet via an IP router.
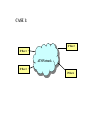
CASE 1:
IP Host 3
IP Host 1
ATM Network
IP Host 2
IP Host 4
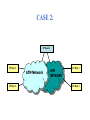
CASE 2:
IP Router
IP Host 1
ATM Network
IP Host 2
ATM
NETWORK
IP Host 3
IP Host 4
Classical IP-over ATM [RFC 1577]
A
B
LIS1
R1
C
LIS2
D
LIS3
R2
LIS: logical IP subnet
E
• end systems in same LIS
have same IP network addr
• LIS looks like a LAN
• ATM net divided into multiple
LIS
• Intra-LIS communication via
direct ATM connections
– How to go from IP addr to
ATM addr: ATMARP
resolves IP addr to ATM
addr (similar to ARP)
Classical IP-over ATM [RFC 1577]
A
B
LIS1
R1
C
LIS2
D
LIS3
R2
E
Inter-LIS communication:
• source, dest. in different LIS
• each LIS looks like a LAN
• hop-by hop forwarding:
– A-R1-R2-E
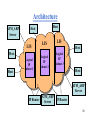
Architecture
ATM_ARP
Server
LIS
Host
Host
Host
Host
Logical
IP
Subnet 1
LIS
LIS
Host
Logical
IP
Subnet 2
Logical
IP
Subnet 3
Host
ATM_ARP
Server
ATM_ARP
IP Router
Server
IP Router
59
Configuration Requirements
(Intra-subnet)
ATM ARP Server
IP Host 1
LIS 1
(ATM Network)
IP Host 2
IP Router
ATM ARP Server
LIS 2
IP Host 3
ATM Network
IP Host 4
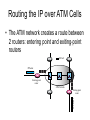
Routing the IP over ATM Cells
• The ATM network creates a route between
2 routers: entering point and exiting-point
routers
ATM cell
IP Packet
I
II
III
Entering-point
router
ATM Network
IP Packet
Exiting-point
router
Routing the IP over ATM Cells
(cont.)
• Routing the cells requires 3 types of addressing:
IP addresses, physical addresses, and virtual
circuit identifiers
• Each router connected to the ATM network has
also a physical address associated with the ATM
network. It plays the same role as the MAC
address in a LAN.
• The ATM Forum defines 20-byte addresses for
ATM networks. Each address must be unique in
a network and is defined by the network
administrator.
Address Binding
•
1.
2.
3.
An ATM network needs virtual circuit identifiers to route
the cells. The IP datagram contains only source and
destination IP addresses. The virtual circuit identifiers
must then be determined from the destination IP
address by the following steps:
The entering-point router receives an IP datagram. It
uses the destination address and its routing table to
find the IP address of the exiting-point router
The entering-point router uses the services of a
protocol called ATMARP to find the physical address of
the exiting-point router
The virtual circuit identifier is bounded to the physical
address
•
•
•
•
•
ATMARP SERVER
Primary purpose is to maintain a table or cache of IP address mappings.
At least one ATMARP server must be configured for each LIS, along with a
specific IP and ATM address.
A single ATMARP server may service more than one LIS as long as it is IP and
ATM addressable within each LIS.
An ATMARP server learns about the IP and ATM addresses of specific members
(IP clients) of the LIS through the use of ATMARP and InATMARP messages
exchanged between the ATMARP server and LIS members.
Finally, an ATMARP server can run on an IP host or router.
Figure shows an LIS with 2 IP clients and a stand-alone ATMARP server.
ATMARP server
IP address=176.13.11.99
ATM address=ZZZ
IP Client# 1
IP address=176.13.11.1
ATM address=AAA
ATM
Switch
IP Client# 2
IP address=176.13.11.2
ATM address=BBB
ADDRESS RESOLUTION
• If the ATMARP server contains an IP/ATM address entry for IP Client #2,
it will return that information in an ATMARP reply message.
• IP Client #1 then knows the ATM address of IP Client #2 and can set up
an SVC.
• If not, then the ATMARP server will return an ARP NAK message.
IP Client# 1
IP address=176.13.11.1
ATM address=AAA
ATMARP server
IP address=176.13.11.99
ATM address=ZZZ
ATM
Switch
ATMARP_Req (IP addr of Client #2, ATM addr ???)
ATMARP_Reply (ATM addr = BBB)
Setup VC and Send Data
IP Client# 2
IP address=176.13.11.2
ATM address=BBB
How does the ATMARP server
build its mapping table?
• This is done through the use of ATMARP and
the two inverse messages
• When a router is connected to an ATM network
for the first time and a PVC is established
between the router and the server, the server
sends an inverse request message to the router
• The router sends back an inverse reply
message
• Using these two addresses, the server creates
an entry in its routing table to be used if the
router becomes an exiting-point router in the
future
Registration
•
The registration process flow for IP Client #1 is shown in
Figure.
• Of course, IP Client #2 will register its own address with the
ATMARP server once it is initialized.
IP address=176.13.11.99
ATM address=ZZZ
IP Client #1
IP address=176.13.11.1
ATM address=AAA
ATM
Switch
Setup VC
InATMARP_Req (IP addr of client #1???)
InATMARP_Reply (176.13.11.1)
ATMARP
Server
IP Client #2
IPaddress=176.13.11.2
ATM address=BBB
Figure 7.28
Address binding in IP over ATM
Packet Format of ATMARP
Packet Format of ATMARP (cont.)
• Operation (OPER). This 16-bit field
defines the type of the packet. Five packet
types are defined as shown in the table.
ATMARP Operation on PVC Connection
• If a permanent virtual circuit is established between 2
routers, there is no need for an ATMARP server
• However, the router must be able to bind a physical
address to an IP address. The inverse request
message and inverse reply message can be used for
the binding.
• When a PVC is established for a router, the router sends
an inverse request message. The router at the other end
receives the message (which contains the physical and
IP address of the sender) and sends back an inverse
reply message (which contains its own physical and IP
address)
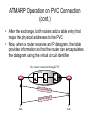
ATMARP Operation on PVC Connection
(cont.)
• After the exchange, both routers add a table entry that
maps the physical addresses to the PVC
• Now, when a router receives an IP datagram, the table
provides information so that the router can encapsulates
the datagram using the virtual circuit identifier
Two routers connected through PVC
ATM
I
II
III
1
Inverse Reque
st
Inverse Reply
time
2
time
ATMARP Operation on SVC Connection
• In a SVC, each time a router wants to make a
connection with another router, a new virtual circuit must
be established
• However, the virtual circuit can be created only if the
entering-ping router knows the physical address of the
exiting-point router
• To map the IP addresses to physical addresses, each
router runs a client ATMARP program, but only one
computer runs an ATMARP server program
• The process of establishing a virtual connection requires
3 steps: connecting to the server, receiving the physical
address, and establishing the connection
Connecting to the Server
• Normally, there is a permanent virtual
circuit established between each router
and the server
• If there is no PVC connection between the
router and the server, the router must at
least know the physical address of the
server to crate an SVC connection just for
exchanging ATMARP request and reply
messages
Receiving the Physical Address
• When there is a connection between the
entering-point router and the server, the
router sends an ATMARP request to the
server
• The server sends back an ATMARP reply
if the physical address can be found or an
ATMARP NACK otherwise
• If the entering-point router receives a
NACK, the datagram is dropped
Establishing Virtual Circuits
• After the entering-point router receives the
physical address of the exiting-pint router, it can
request an SVC between itself and the exitingpoint router
• The ATM network uses the two physical
addresses to set up a virtual circuit which lasts
until the entering-point router asks for
disconnection
• In this step, each switch inside the network adds
an entry to its tables to enable them to route the
cells carrying the IP datagram
Operation of Classical IP over ATM
Source
Switch
Registration
Host 1
ATM_ARP
Server
Destination
Switch
Host 2
Set Up
Set Up
Connect
Connect
Connection Established
InARP request
Connection
Establishment
Address
Resolution
InARP RP
ARP Request
ARP Response
Set Up
Set Up
Set Up
Connect
Connect
Connect
Connection Established
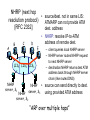
Next Hop Resolution Protocol (for Inter-Subnets)
(NHRP: pronounced nerp)
Hos
t
Hos
t
LIS
(ATM
Network)
LIS
(ATM
Network)
Go through a router that is aRouter
member of multiple logical IP
subnets. This router may become a bottleneck.
Solution
NHRP
NHRP (next hop • source/dest. not in same LIS:
resolution protocol)
ATMARP can not provide ATM
[RFC 2332]
dest. address
A
C
B
D
LIS1 LIS2 LIS3
NHRP
server, S1
NHRP
server, S2
E
• NHRP: resolve IP-to-ATM
address of remote dest.
– client queries local NHRP server
– NHRP server routes NHRP request
to next NHRP server
– destination NHRP returns dest ATM
address back through NHRP server
chain (like routed DNS)
• source can send directly to dest.
NHRP
server, S3
using provided ATM address
“ARP over multiple hops”
NHRP Terminology
1.
NON-BROADCAST MULTI-ACCESS NETWORK (NBMA)
An NBMA network is defined as:
* Does not support an inherent broadcast or multicast capability.
* Enables any host (or router) attached to the NBMA network to
communicate directly with another host on the same NBMA network.
ATM, Frame Relay, SMDS, and X.25 are all examples of NBMA
networks. An NBMA ATM network may contain one or more LISs.
* The NBMA is partitioned into administrative domains.
Logical NBMA Subnets (LNS)
* Each LNS is served by an NHS (Next Hop Server)
NHRP Terminology (Cont.)
2. NEXT HOP SERVER (NHS)
(These are responsible for answering NHRP resolution
requests by means of NHRP replies.)
• NHS serves a set of hosts (or NHRP stations) in the NBMA network and answers
NHRP resolution requests from these stations called NHC (Next Hop Clients).
• Both NHS and NHC contain a CACHE
or table of IP & ATM addresses for devices
attached to the ATM network (Address Resolution Cache).
• If the desired destination IP address is not on the ATM network, then the NHS will
provide the ATM address of the router nearest to the destination.
• The NHS should run on a router so as to facilitate forwarding of NHRP requests,
replies, and other messages over the default-routed path.
• The NHS responds to queries from NHRP clients.
• The NHS serves a specific set or domain of NHRP clients for whom it is
responsible.
NHRP Terminology (Cont.)
3. NEXT HOP CLIENTS (NHC)
•
•
NHRP cloud contains entities called NHCs.
These are responsible for initiating NHRP resolution
request packets.
REMARK:
• Both NHC and NHS maintain an ADDRESS RESOLUTION
CACHE.
• An NHC in NHRP replaces an ATMARP client in CLIP
(Classical IP over ATM Case)
• NHS replaces an ATMARP server.
NHRP Configuration
• NHRP clients must be attached to an ATM network and
must be configured with the ATM address of the NHS
that is serving the client. Alternatively, it should have a
means of locating its NHS.
•NHRP clients can be serviced by more than one NHS.
• NHRP Servers are configured with their own IP and ATM
addresses, a set of IP address prefixes that correspond to the
domain of NHRP clients it is serving, and an NBMA (ATM)
network identifier.
• If the NHRP server is located on an egress router attached
to a non-ATM network, then the NHRP server must exchange
routing information between the ATM and non-ATM
network.
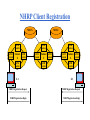
NHRP Client Registration
• NHRP clients register with their NHRP server in one of the
two ways:
1- Manual Configuration
2- NHRP Registration Packets
• The NHRP registration packet contains the following
information along with additional values:
{NHC’s ATMaddress, NHC’s IPaddress, NHS’s IPaddress}
• With this information, the NHRP server can begin to build
its table of IP and ATM addresses.
NHRP Client Registration
NHS X
NHS Z
ATM
Switch
ATM
Switch
Subnet ATM
Switch
X
ATM
Switch
X.1
ATM
Switch
ATM
Switch
Subnet ATM
Switch
Y
ATM
Switch
ATM
Switch
ATM
Switch
Subnet ATM
Switch
Z
ATM
Switch
Z.3
NHRP Registration Request
NHRP Registration Request
NHRP Registration Reply
NHRP Registration Reply
NHRP ADDRESS RESOLUTION
NHS X
NHS Z
ATM
Switch
Subnet X
ATM
Switch
ATM
Switch
X.1
ATM
Switch
ATM
Switch
ATM
Switch
ATM
Switch
Subnet Y
ATM
Switch
ATM
Switch
NHRP Resolution Request
NHRP Resolution Reply
Subnet Z
First Packet
ATM
Switch
ATM
Switch
Z.3
IP address = Z.3
ATM address = BBB
IP address = X.1
ATM address = AAA
First Packet
ATM
Switch
First Packet
NHRP Resolution Request
NHRP Resolution Reply
Setup SVC
Data
A single NBMA ATM network that contains 2 LISs: X and Z. Actually 3 if we
count the LIS connecting the two routers
omitted.
NHRP ADDRESS RESOLUTION
• The LISs are connected by two routers that serve as NHRP servers
for subnets X and Z, respectively.
• The routers are running a normal intra-AS routing protocol, OSPF, and
are connected by an ATM PVC so they are exchanging routing
information.
• The station attached to subnet X with the IP address of X.1 wishes
to communicate with station Z.3.
•
•
•
•
•
•
•
Station X.1 builds a packet and addresses it to Z.3.
If Z.3 ATM address known, then X.1 uses an existing VCC to send its data.
If not, I.e., X.1 does not know the ATM address of Z.3, then it sends NHRP.
This packet is forwarded over an existing ATM VC to the default router.
This causes X.1 to send a NHRP Next Hop Resolution Request message to NHS
X with the following information: [AAA, X.1, Z.3].
Station X.1 may also opt to hold onto the packet until a NHRP reply is received
or drop it.
The first option, the default, is the better choice because that allows data to
flow over the default-routed path.
NHRP ADDRESS RESOLUTION
•
•
•
•
•
•
•
•
NHS X checks to see if it serves station Z.3.
It also checks to see if it has an entry in its cache for Z.3.
SUPPOSE Neither is true so the NHRP (Next Hop Resolution
Request) is forwarded to the adjacent NHRP server, NHS Z.
NHS Z receives the NHRP Next Hop Resolution Request from NHS X.
NHS Z determines that it serves the destination IP address contained
in the request message.
An entry is contained in the cache or table of NHS Z which contains an
IP to ATM address mapping for the destination IP address of Z.3.
NHS Z resolves the destination IP address, Z.3, with its matching ATM
address, BBB.
It places this information in a NHRP Next Hop Resolution Reply and
returns it to station X.1 over a default-routed path that the request
came from.