* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download No Slide Title - Columbia University
Survey
Document related concepts
Internet protocol suite wikipedia , lookup
Point-to-Point Protocol over Ethernet wikipedia , lookup
Net neutrality law wikipedia , lookup
Bus (computing) wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Backpressure routing wikipedia , lookup
Direct memory access wikipedia , lookup
Computer network wikipedia , lookup
Airborne Networking wikipedia , lookup
Wake-on-LAN wikipedia , lookup
IEEE 802.1aq wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Multiprotocol Label Switching wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Transcript
W4140 Network Laboratory
Lecture 5
Oct 9 - Fall 2006
Shlomo Hershkop
Columbia University
Announcements
Please do not reset password, and let me know if you find someone has done it to
your station
Please log out when done
how many groups are having hardware / software issues ?
this week’s lab
if you have done part 1-4 of lab 4…..you have a free week!!
else this week you have a chance to catch up
also start to think about projects, the wireless equipment have arrived and so will setup more
project proposals based on those
wireless bridges and configuration
security with wireless
wireless mesh networks
capacity, interference, and overlap with wireless systems
ISSUES ??
is there any issues with the labs ?
please be aware that VOIP will be using the lab, so if you can,
please coordinate with the TA’s about extra lab time…they will be in
touch with VOIP
our lab times, represent reserved times, so feel free to ask people to
move over (nicely please)
Dynamic routing protocols I
1. Overview of router architecture
2. Overview Dynamic Routing Protocols: Distance Vector Routing
3. Intra-Domain Routing Protocols: RIP
Routing and Forwarding
Forwarding is selecting the next-hop machine for each
outgoing packet.
Routing is the process of deciding the path from a
source to a destination.
Forwarding table, FIB (Forwarding Information Base).
Routing table, RIB (Routing Information Base).
Why two tables and not just one?
Routing and Forwarding
Control plane: run
routing protocols:
(RIP, OSPF, BGP)
Data plane: forwarding
packets from incoming to
outgoing link
Routing and Forwarding
Select the next-hop router.
Find the outgoing interface.
Find the MAC address of the next-hop router.
In Unix, you specify the IP address of the next-hop router.
Longest-prefix first.
Default routing (implied by longest-prefix rule: default
has prefix of length 0).
Routing and Forwarding
Routing functions include:
route calculation
maintenance of the routing table
execution of routing protocols
On commercial routers handled by a single general
purpose processor, called route processor
IP forwarding is per-packet processing
On high-end commercial routers, IP forwarding is
distributed
Most work is done on the interface cards
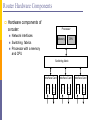
Router Hardware Components
Hardware components of
a router:
Processor
Network interfaces
Switching fabrics
Processor with a memory
and CPU
Memory
CPU
Switching fabric
Interface Card
Interface Card
Interface Card
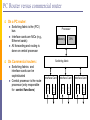
PC Router versus commercial router
On a PC router:
Switching fabric is the (PCI)
bus
Interface cards are NICs (e.g.,
Ethernet cards)
All forwarding and routing is
done on central processor
On Commercial routers:
Switching fabrics and
interface cards can be
sophisticated
Central processor is the route
processor (only responsible
for control functions)
Processor
Memory
CPU
Switching fabric
Interface Card
Interface Card
Interface Card
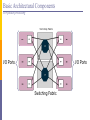
Basic Architectural Components
Per-packet processing
I/O Ports
I/O Ports
Switching Fabric
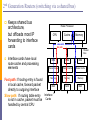
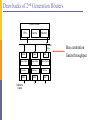
Evolution of Router Architectures
Early routers were essentially general purpose
computers
Today, high-performance routers resemble
supercomputers
Exploit parallelism
Special hardware components
Until 1980s (1st generation): standard computer
Early 1990s (2nd generation): delegate to interfaces
Late 1990s (3rd generation): Distributed architecture
Today: Distributed over multiple racks
1st Generation Routers (switching via memory)
This architecture is still
used in low end routers
Route Processor
CPU
Arriving packets are copied to
main memory via direct
memory access (DMA)
Switching fabric is a
backplane (shared bus)
All IP forwarding functions are
performed in the central
processor.
Routing cache at processor
can accelerate the routing
table lookup.
Cache
Memory
Shared Bus
DMA
DMA
DMA
Interface
Card
Interface
Card
Interface
Card
MAC
MAC
MAC
Drawbacks of 1st Generation Routers
Forwarding Performance is limited by memory
and CPU
Capacity of shared bus limits the number of
interface cards that can be connected
Input
Port
Memory
Output
Port
System Bus
2nd Generation Routers (switching via a shared bus)
Keeps shared bus
architecture,
but offloads most IP
forwarding to interface
cards
Interface cards have local
route cache and processing
elements
Fast path: If routing entry is found
in local cache, forward packet
directly to outgoing interface
Slow path: If routing table entry
is not in cache, packet must be
handled by central CPU
Route Processor
CPU
Cache
Memory
slow path
fast path
Shared
Bus
DMA
DMA
DMA
Route Cache
Route Cache
Route Cache
Memory
Memory
Memory
MAC
MAC
MAC
Interface
Cards
Another 2nd Generation Architecture
IP forwarding is done by
separate components
(Forwarding Engines)
Forwarding operations:
1. Packet received on interface:
2.
3.
Store the packet in local
memory. Extracts IP
header and sent to one
forwarding engine
Forwarding engine does
lookup, updates IP
header, and sends it back
to incoming interface
Packet is reconstructed
and sent to outgoing
interface.
Control Bus
Forwarding Bus
(IP headers only)
Data Bus
Interface
Cards
Forwarding
Engine
Forwarding
Engine
Route Processor
CPU
CPU
CPU
Cache
Cache
Memory
Memory
Memory
IP header
IP datagram
Memory
Memory
Memory
MAC
MAC
MAC
Drawbacks of 2nd Generation Routers
Route Processor
CPU
Cache
Memory
Shared
Bus
DMA
DMA
DMA
Route Cache
Route Cache
Route Cache
Memory
Memory
Memory
MAC
MAC
MAC
Interface
Cards
Bus contention
limits throughput
3rd Generation Architecture
Switching fabric is an
interconnection network (e.g., a
crossbar switch)
Distributed architecture:
Interface cards operate
independent of each other
No centralized processing for IP
forwarding
These routers can be scaled to
many hundred interface cards and
to aggregate capacity of > 1 Terabit
per second
Switch
Fabric
Switch
Fabric
Interface
Switch
Fabric
Interface
Route
Processor
Route
Processing
Route
Processing
CPU
Memory
Memory
Memory
MAC
MAC
Cisco Express Forwarding (distributed mode)
Cisco Express Forwarding Benefits
Scalability & Efficiency
Adjacency Tables for local hosts (same network)
Layer 2 switching is faster.
The line cards perform the express forwarding between port
adapters, relieving the RSP (Route Switch Processing) of
involvement in the switching operation.
Resilience
No route cache: several data structures for CEF switching
Line Cards maintain an identical copy of the FIB and adjacency
tables.
More at Cisco on-line documentation
Slotted Chassis
R
Pr o u t
oc e
(C esso
PU r
)
e cards
Interfac
Large routers are built as a slotted chassis
Interface cards are inserted in the slots
Route processor is also inserted as a slot
This simplifies repairs and upgrades of components
Dynamic Routing Protocols
Distance Vector Routing
Routing Protocols
Recall: There are two parts to routing IP packets:
1. How to pass a packet from an input interface to the
output interface of a router (packet forwarding) ?
2. How to find and setup a route ?
We already discussed the packet forwarding part
Longest prefix match
There are two approaches for calculating the routing
tables:
Static Routing (We modify manually the Routes)
Dynamic Routing: Routes are calculated by a routing protocol
Routing protocols vs routing algorithms
Routing protocols establish routing tables at routers.
A routing protocol specifies
What messages are sent between routers
Under what conditions the messages are sent
How messages are processed to compute routing tables
At the heart of any routing protocol is a routing algorithm
that determines the path from a source to a destination
IGP : interior gateway protocols
1.
used within an autonomous system
Distance-vector routing protocol
1.
2.
3.
information on who is next to you and cost (hop) (route table)
share info
update info
1.
2.
2.
relatively slow to propagate
can insert bad info
Link-state routing protocol
1.
2.
have a network map by everyone
calculate best path
1.
can end up with loops if two points have different starting maps
Overview Routing Protocols
Routing protocol
Routing Algorithm
Routing information protocol (RIP)
Distance vector
Interior Gateway routing protocol
(IGRP, Cisco proprietary)
Distance vector
Open shortest path first (OSPF)
Link state
Intermediate System-to-Intermediate Link state
System (IS-IS
Border gateway protocol (BGP)
Path vector
Intra-domain routing versus inter-domain routing
Recall Internet is a network of networks.
Administrative autonomy
internet = network of networks
each network admin may want to control routing in its own
network
Scale: with 200 million destinations:
can’t store all destinations’s in routing tables!
routing table exchange would swamp links
Autonomous systems
Ethernet
Router
Ethernet
Ethernet
Autonomous
System 1
Router
Router
Router
Ethernet
Router
Ethernet
Autonomous
System 2
Router
Ethernet
aggregate routers into regions, “autonomous systems” (AS) or
domain
routers in the same AS run the same routing protocol
“intra-AS” or intra-domain routing protocol
routers in different AS can run different intra-AS routing protocol
Autonomous Systems
An autonomous system is a region of the Internet that is
administered by a single entity.
Examples of autonomous regions are:
UCI’s campus network
MCI’s backbone network
Regional Internet Service Provider
Routing is done differently within an autonomous system
(intradomain routing) and between autonomous system
(interdomain routing).
RIP, OSPF, IGRP, and IS-IS are intra-domain routing
protocols.
BGP is the only inter-domain routing protocol.
Distance Vector Routing
Variations of Bellman-Ford algorithm.
Each router starts by knowing:
Each router advertises only to its neighbors:
All prefixes it knows about.
Its distance from them.
Each router learns:
Prefixes of its attached networks (“zero” distance).
Its next hop routers (how to find them?)
All prefixes its neighbors know about.
Their distance from them.
Each router figures out, for each destination prefix:
The “distance” (how far away it is).
The “vector” (the next hop router).
Distance Vector Routing Properties
DV Computes the Shortest Path
“Routing by rumor”
Each router believes what its neighbors tell it.
In steady-state, each router has the “shortest” (smallest
metric) path to the destination.
Convergence time is (on the average) proportional to the
diameter of the network.
Any link change affects the entire network.
Distance vector algorithm
A decentralized algorithm
A router knows physically-connected neighbors and link costs to
neighbors
A router does not have a global view of the network
Path computation is iterative and mutually dependent.
A router sends its known distances to each destination (distance
vector) to its neighbors.
A router updates the distance to a destination from all its
neighbors’ distance vectors
A router sends its updated distance vector to its neighbors.
The process repeats until all routers’ distance vectors do not
change (this condition is called convergence).
Bellman-Ford Algorithm
Bellman-Ford Equation
Define
dx(y) := cost of the least-cost path from x to y
Then
dx(y) = minv{c(x,v) + dv(y) }, where min is taken over
all neighbors of node x
Distance vector algorithm: initialization
Let Dx(y) be the estimate of least cost from x to y
Initialization:
Each node x knows the cost to each neighbor: c(x,v). For each
neighbor v of x, Dx(v) = c(x,v)
Dx(y) to other nodes are initialized as infinity.
Each node x maintains a distance vector (DV):
Dx = [Dx(y): y 2 N ]
Distance vector algorithm: updates
Each node x sends its distance vector to its neighbors,
either periodically, or triggered by a change in its DV.
When a node x receives a new DV estimate from a
neighbor v, it updates its own DV using B-F equation:
If c(x,v) + Dv(y) < Dx(y) then
Dx(y) = c(x,v) + Dv(y)
Sets the next hop to reach the destination y to the neighbor v
Notify neighbors of the change
The estimate Dx(y) will converge to the actual least cost
dx(y)
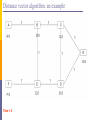
Distance vector algorithm: an example
1
1
1
1
1
1
1
Time = 0
1
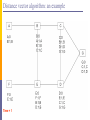
Distance vector algorithm: an example
Time = 1
Distance vector algorithm: an example
Time = 2 (End)
How to map the abstract graph to the physical network
c(v,w)
Net(v,w)
w
v
Net
c(v,n)
Net(v,n)
n
Nodes (e.g., v, w, n) are routers, identified by IP addresses, e.g. 10.0.0.1
Nodes are connected by either a directed link or a broadcast link (Ethernet)
Destinations are IP networks, represented by the network prefixes, e.g.,
10.0.0.0/16
Net(v,n) is the network directly connected to router v and n.
Costs (e.g. c(v,n)) are associated with network interfaces.
Router1(config)# router rip
Router1(config-router)# offset-list 0 out 10 Ethernet0/0
Router1(config-router)# offset-list 0 out 10 Ethernet0/1
Distance vector routing protocol: Routing Table
c(v,w): cost to transmit on the
interface to network Net(v,w)
Net(v,w): Network address of the network between v
and w
RoutingTable of node v
Dest
v
Net(v,w)
c(v,w)
Net(v,n)
c(v,n)
via
(next hop)
cost
w
Net
Net
n
D(v,Net)
n
D(v,net) is v’s cost to Net
Distance vector routing protocol: Messages
RoutingTable of node v
Dest
Net
v
via
(next hop)
n
cost
D(v,Net)
[Net , D(v,Net)]
n
• Nodes send messages to their neighbors which contain
distance vectors
• A message has the format: [Net , D(v,Net)] means“My cost to
go to Net is D (v,Net)”
Distance vector routing algorithm: Sending Updates
RoutingTable of node v
Dest
via
(next hop)
cost
Net1
m
D(v,Net 1)
Net2
n
D(v,Net 2)
NetN
w
D(v,Net N)
Periodically, each node v
sends the content of its routing
table to its neighbors:
m
[Net1,D(v,Net1)]
[Net1,D(v,Net1)]
[NetN,D(v,NetN)]
[NetN,D(v,NetN)]
v
w
[Net1,D(v,Net1)]
[NetN,D(v,NetN)]
n
Initiating Routing Table I
Suppose a new node v becomes active.
The cost to access directly connected networks is zero:
D (v, Net(v,m)) = 0
D (v, Net(v,w)) = 0
D (v, Net(v,n)) = 0
RoutingTable
c(v,m)
Net(v,m)
m
c (v,w)
Net(v,w)
v
via
(next hop)
cost
w
c(v,n)
Net(v,n)
n
Dest
Net(v,m)
m
0
Net(v,w)
w
0
Net(v,n)
n
0
Initiating Routing Table II
RoutingTable
Dest
via
(next hop)
cost
Net(v,m)
m
0
Net(v,w)
w
0
Net(v,n)
n
0
Node v sends the routing table entry to all its neighbors:
[n,0]
[Net(v,n),0]
[w,0]
[Net(v,w),0]
m
[n,0]
[Net(v,n),0]
[m,0]
[Net(v,m),0]
v
w
[m,0]
[Net(v,m),0]
[w,0]
[Net(v,w),0]
n
Initiating Routing Table III
Node v receives the routing tables from other nodes and
builds up its routing table
[Net1,D(m,Net1)]
[Net1,D(w,Net1)]
[NetN,D(m,NetN)]
[NetN,D(w,NetN)]
m
v
w
[Net1,D(n,Net1)]
[NetN,D(n,NetN)]
n
The Count-to-Infinity Problem
What happens on a link failure?
X
A: 0
B:1,B
C:2,B
C:4,B
C:6,B
A: 1,A
B:0
C:1,C
C:C:3,A
C:5,A
A: 2,B
B:1,B
C:0
Count-to-Infinity
The reason for the count-to-infinity problem is that each
node only has a “next-hop-view”
For example, in the first step, A did not realize that its
route (with cost 2) to C went through node B
How can the Count-to-Infinity problem be solved?
Count-to-Infinity
The reason for the count-to-infinity problem is that each
node only has a “next-hop-view”
For example, in the first step, A did not realize that its
route (with cost 2) to C went through node B
How can the Count-to-Infinity problem be solved?
Solution 1: Always advertise the entire path in an
update message to avoid loops (Path vectors)
BGP uses this solution
Count-to-Infinity
The reason for the count-to-infinity problem is that each
node only has a “next-hop-view”
For example, in the first step, A did not realize that its
route (with cost 2) to C went through node B
How can the Count-to-Infinity problem be solved?
Solution 2: Never advertise the cost to a neighbor if this
neighbor is the next hop on the current path (Split
Horizon)
Example: A would not send the first routing update to B, since B is the
next hop on A’s current route to C
Split Horizon does not solve count-to-infinity in all cases!
You can produce the count-to-infinity problem in Lab 4.
Characteristics of D.V. Routing Protocols
Periodic Updates: Updates to the routing tables are
sent at the end of a certain time period. A typical value is
30 seconds.
Triggered Updates: If a metric changes on a link, a
router immediately sends out an update without waiting
for the end of the update period.
Full Routing Table Update: Most distance vector
routing protocol send their neighbors the entire routing
table (not only entries which change).
Route invalidation timers: Routing table entries are
invalid if they are not refreshed. A typical value is to
invalidate an entry if no update is received after 3-6
update periods.
Inter-domain Routing Protocols: RIP
RIP - Routing Information Protocol
A simple intradomain protocol
Straightforward implementation of Distance Vector
Routing
Each router advertises its distance vector every 30
seconds (or whenever its routing table changes) to all of
its neighbors
RIP always uses 1 as link metric
Maximum hop count is 15, with “16” equal to “”
Routes are timeout (set to 16) after 3 minutes if they are
not updated
RIP - History
Late 1960s : Distance Vector protocols were used in the
ARPANET
Mid-1970s: XNS (Xerox Network system) routing
protocol is the ancestor of RIP in IP (and Novell’s IPX
RIP
and Apple’s routing protocol)
1982
Release of routed for BSD Unix
1988
RIPv1 (RFC 1058)
- classful routing
1993
RIPv2 (RFC 1388)
- adds subnet masks with each route
entry
- allows classless routing
1998
Current version of RIPv2 (RFC 2453)
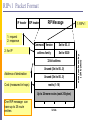
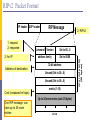
RIPv1 Packet Format
IP header UDP header
RIP Message
1: RIPv1
2: for IP
Command Version
Set to 00...0
address family
Set to 00.00
32-bit address
Unused (Set to 00...0)
Address of destination
Cost (measured in hops)
Unused (Set to 00...0)
metric (1-16)
Up to 24 more routes (each 20 bytes)
One RIP message can
have up to 25 route
entries
32 bits
one route entry
(20 bytes)
1: request
2: response
RIPv2
RIPv2 is an extends RIPv1:
Subnet masks are carried in the route information
Authentication of routing messages
Route information carries next-hop address
Uses IP multicasting
Extensions of RIPv2 are carried in unused fields of
RIPv1 messages
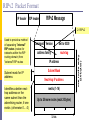
RIPv2 Packet Format
1: request
2: response
2: for IP
Address of destination
RIP Message
Command Version
Set to 00...0
address family
Set to 00.00
32-bit address
Unused (Set to 00...0)
Unused (Set to 00...0)
Cost (measured in hops)
metric (1-16)
Up to 24 more routes (each 20 bytes)
One RIP message can
have up to 25 route
entries
32 bits
2: RIPv2
one route entry
(20 bytes)
IP header UDP header
RIPv2 Packet Format
IP header UDP header
RIPv2 Message
Used to provide a method
of separating "internal"
RIP routes (routes for
networks within the RIP
routing domain) from
"external" RIP routes
Subnet mask for IP
address
Identifies a better nexthop address on the
same subnet than the
advertising router, if one
exists (otherwise 0….0)
Command Version
Set to 00.00
address family
route tag
IP address
Subnet Mask
Next-Hop IP address
metric (1-16)
Up to 24 more routes (each 20 bytes)
32 bits
one route entry
(20 bytes)
2: RIPv2
RIP Messages
This is the operation of RIP in routed. Dedicated port
for RIP is UDP port 520.
Two types of messages:
Request messages
used to ask neighboring nodes for an update
Response messages
contains an update
Routing with RIP
Initialization: Send a request packet (command = 1, address
family=0..0) on all interfaces:
RIPv1 uses broadcast if possible,
RIPv2 uses multicast address 224.0.0.9, if possible
requesting routing tables from neighboring routers
Request received: Routers that receive above request send their
entire routing table
Response received: Update the routing table
Regular routing updates: Every 30 seconds, send all or part of the
routing tables to every neighbor in an response message
Triggered Updates: Whenever the metric for a route change, send
entire routing table.
RIP Security
Issue: Sending bogus routing updates to a router
RIPv1: No protection
RIPv2: Simple authentication scheme
RIPv2 Message
IP header UDP header
Command Version
Set to 00.00
0xffff
Authentication Type
Password (Bytes 0 - 3)
Password (Bytes 4 - 7)
Password (Bytes 8- 11)
Password (Bytes 12 - 15)
Up to 24 more routes (each 20 bytes)
32 bits
2: plaintext
password
Authetication
RIP Problems
RIP takes a long time to stabilize
RIP has all the problems of distance vector algorithms,
e.g., count-to-Infinity
Even for a small network, it takes several minutes until the
routing tables have settled after a change
RIP uses split horizon to avoid count-to-infinity
The maximum path in RIP is 15 hops