* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Towards Wireless Overlay Network Architectures
Survey
Document related concepts
Distributed firewall wikipedia , lookup
Net neutrality law wikipedia , lookup
Wireless security wikipedia , lookup
Distributed operating system wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
TV Everywhere wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Airborne Networking wikipedia , lookup
Zero-configuration networking wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Service-oriented architecture implementation framework wikipedia , lookup
Transcript
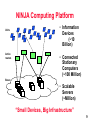
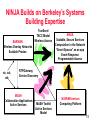
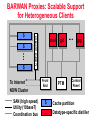
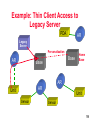
NINJA: A Service Architecture for Internet-Scale Systems Randy H. Katz UMC Distinguished Professor and Chair, EECS Department University of California, Berkeley Berkeley, CA 94720-1776 [email protected] Ninjutsu is a stealth and espionage-oriented art which saw its greatest development in the 13th to early 17th centuries in Japan. Its practitioners, the ninja, were warrior-assassin-spies; most belonged to the Iga and Koga mountain clans. They were the supreme reconnaissance experts and saboteurs of their day. 1 Presentation Outline • • • • • Internet-Scale Systems A New Service Architecture Integration of Computing and Communications Opportunity for Cooperation Summary and Conclusion 2 Presentation Outline • • • • • Internet-Scale Systems A New Service Architecture Integration of Computing and Communications Opportunity for Cooperation Summary and Conclusion 3 Internet-Scale Systems • Extremely large, complex, distributed, heterogeneous, with continuous and rapid introduction of new technologies • Feasible architectures – Decentralized, scalable algorithms – Dynamically deployed agents where they are needed; “Big infrastructure, small clients” – Incremental processing/communications growth – Careful violation of traditional layering • Implementation approach based on incremental prototyping, deployment, evaluation, experimentation 4 Emerging Communications Infrastructure of the Future • The Challenge – Network-based applications becoming increasingly service intensive – Computational resources embedded in the switching fabric – Dealing with heterogeneity, true utility functionality, security & service discovery, in an open, extensible network environment • Computing – Legacy servers – Partition functionality for “small” clients • Communications – High bandwidth backbones plus diverse access networks » Third generation cellular systems » Home networking 5 “From POTS to PANS: Telecommunications in Transition” “Today, the telecommunications sector is beginning to reshape itself, from a vertically to a horizontally structured industry. … [I]t used to be that new capabilities were driven primarily by the carriers. Now, they are beginning to be driven by the users. … There’s a universe of people out there who have a much better idea than we do of what key applications are, so why not give those folks the opportunity to realize them. … The smarts have to be buried in the ‘middleware’ of the network, but that is going to change as more-capable user equipment is distributed throughout the network. When it does, the economics of this industry may also change.” George Heilmeier, Chairman Emeritus, Bellcore 6 Motivation: Why Can’t We ... • • • • • • Control the A/V equipment in this room Get driving directions over the phone Affect other’s calendars directly Screen our calls based on the caller Control things with the interface we want Manage/sort/search our e-mail/v-mail/fax/news intelligently Needed: Ubiquitous connectivity and intelligent processing supported by the network 7 NINJA: A Service Architecture that Provides ... • Tinkertoy wide-area components • Automatic discovery, composition, and use • Powerful operators: clusters, databases, and agents • Viable component economics: subscription, pay per use • Supports great devices, sensors, actuators • Connects everything: ubiquitous support for access and mobility 8 NINJA Computing Platform Units Active routers • Information Devices (~10 Billion) • Connected Stationary Computers (~100 Million) Bases • Scalable Servers (~Million) “Small Devices, Big Infrastructure” 9 NINJA Computing Infrastructure Server Client Proxy Router Compute Node • Computing resources inside the routing topology, not just at the leaves • Paths chosen for location of operators as much as for shortest # of hops • Mobile code that specializes the services provided by servers • Mobility, management of bottleneck links, “integration” services, service handoff 10 NINJA Builds on Berkeley’s Systems Building Expertise BARWAN Wireless Overlay Networks Scalable Proxies vic, vat, wb TranSend TACC Model Wireless Access NINJA Scalable, Secure Services Computation in the Network “Smart Spaces” as an app Event-Response Programmable Access RTPGateway Service Discovery MASH Collaboration Applications Active Services MASH Toolkit Active Services Model NOW/Millennium Computing Platform 11 BARWAN Wireless Overlays: Ubiquitous Connectivity Satellite Regional Area Low-tier High-tier Local Area Wide Area High Mobility Low Mobility Seamless mobility among local and wide-area wireless networks via vertical handoff 12 $ $ $ Cache control BARWAN Proxies: Scalable Support for Heterogeneous Clients To Internet NOW Cluster SAN (high speed) Utility (10baseT) Coordination bus html Front End gif PTM jpg Control Panel $ Cache partition ... Datatype-specific distiller BARWAN: Support for Thin Clients • Top Gun Wingman – World’s only graphical browser for PalmPilot – Greater than 10,000 users worldwide • Top Gun MediaBoard – Combines MASH tools with proxy – Interoperates with laptops, workstations Superiority of proxy-based approach to enabling “thin” clients successfully demonstrated 14 Presentation Outline • • • • • Internet-Scale Systems A New Service Architecture Integration of Computing and Communications Opportunity for Cooperation Summary and Conclusion 15 Vertically Integrated Services vs. Component Services Vertically Integrated Services Component Services • • • • • • • • • • • Fixed composition Static deployment No reuse Mixed presentation/data Fixed UI Worse pieces Dynamic composition Rapid deployment Reuse Data only UI defined dynamically -based on device/connection • Competition at every level NINJA Service Architecture: Basic Elements of the Model Units: – – – – sensors/actuators PDAs/SmartPhones Laptops, PCs, NCs heterogeneous Active Routers: – – – – soft-state basestations localization local mobility support Bases: – – – – – – – highly available persistent state databases computing agents “home” base per user “global” mobility support 17 NINJA Active Infrastructure “Smart Spaces” Active Routers: Active network routers Soft state Interchangeable Bases: Scalable, available servers Persistent state Service discovery Public-key infrastructure Databases Home Base Units: Client Devices Sensors & Actuators User state E-mail User tracking 18 Example: Thin Client Access to Legacy Server PDA AR Legacy Server Personalization AR Base Base Home Base AR AR Unit Sensor Unit Sensor 19 Example: Sensor Aggregation PDA AR Legacy Server AR Base Base Agent Aggregator AR AR Unit Sensor Unit Sensor 20 Example: TopGun WingMan/Mediaboard Operation PDA Legacy Server Image Converter AR PDA Proxy Base MediaBoard Un-Zip Multicast Connector Aggregator PC AR Mic Camera 21 NINJA Service Architecture • Operators/Connectors/Interfaces • Paths – Wide-Area Paths – Interface Interconnection – Path Optimization • Services – Service Discovery – Automatic Path Generation • Example Applications – Universal remote control/smart spaces – Universal In-Box/Personal Information Management 22 Operators/Connectors Operators: – transformation – aggregation – agents Connectors: – – – – abstract wires ADUs varying semantics uni/multicast Interfaces: – – – – strongly typed language independent set of AM handlers Leverage all COM objects 23 Wide-Area Paths • Path is a first-class entity • Explicit or automatic creation • Can change dynamically – change path or operators • Unit of authentication: delegate along the path • Unit of resource allocation 24 WAN Paths: Economics • Key Idea: securely delegate authority to any path component – access your e-mail remotely – authorized services (subscriptions) – authenticated sensor data • Digicash: – Pay-per-use services – Can be one-time (or subscription) 25 WAN Paths: Optimization • Insert operators into the path: – forward error-correction, e.g., for error-prone wireless links – compression/decompression, e.g., bandwidth constrained links • Change parameters – retransmission windows – settings for wireless or satellites • Reroute path dynamically 26 Connecting Interfaces • Goal: trivial to connect – can be automated • Connectors are polymorphic – wires carry a generic ADU of type T – automatic marshall/unmarshall » code must be created at instantiation • Enables automated connection and use 27 Interoperability • Wrapper operators for legacy servers – HotBot, Zip2, Patent server – Generic wrappers for each MIME type • Connectors use TCP, UDP, multicast • Leverage COM objects as operators – Control Excel remotely – Lots of third party components • ODBC/JDBC databases 28 Services • Service – Highly available program with fixed interface at a fixed location • Strongly Typed Interfaces – Multiple services of a given type compete – Compete on location, price, robustness, “quality”, brand name • Service Discovery – Find “best” service of given type 29 Automatic Path Creation • Query goal is path creation • Find logical path of operators – Path must type check • Place operators on nodes – Some operators have affinity – Place them first • Add connectors as needed • Create any authentication keys 30 Service Discovery and Use Four basic steps: • Find a local Active Router • Query Service-discovery service • Automatic path creation, including transformations • Generate UI from interface specification 31 Application: Universal Remote Control • Adapt device functionality to services in new environment – Beacon augmentation – Adaptive user interfaces – Composed behaviors • Deployment within our building Universal Interaction? – Light, video, slide projector, VCR, audio receiver, camera, monitor, A/V switcher control – Local DNS/NTP/SMTP servers, HTTP proxies, RTP/multicast gateways – Audited printer access – Interactive floor maps, protocols for advertising object locations – Coarse-grained user tracking 32 Generalization: Smart Spaces • Walk into a A/V room and control everything with your own wireless PDA – – – – – Services for each device Automated discovery and use Automated UI generation Composite behaviors Local scope, no authentication (yet) • Phones as well as PalmPilots – Speech-enabled control 33 Experimental Testbed Fax IBM WorkPad Image/OCR Text Speech MC-16 Ericsson CF788 306 Soda Motorola Pagewriter 2000 WLAN 405 Soda 326 Soda “Colab” Pager GSM BTS Network Infrastructure Millennium Cluster Smart Spaces Personal Information Management Millennium Cluster 34 Target Applications: Personal Information Management • • • • • • Universal Inbox: e-mail, news, fax, voice mail Notification: e-mail, pager Priorities, Folders, Search Access: internet or telephone Peer-to-peer calendar Control of environment 35 Personal Information Management Speech-to-Voice Mail Speech-to-Voice Attached-Email Call-to-Pager/Email Notification Email-to-Speech All compositions of the above! Universal In-box Policy-based Location-based Activity-based 36 Presentation Outline • • • • • Internet-Scale Systems A New Service Architecture Integration of Computing and Communications Opportunity for Cooperation Summary and Conclusion 37 Current Vision of 3rd Generation Cellular PSTN ISDN Circuit-Sw itched 64 kbit/s trunks Internet Direct IP-Access for CS Data CS-based "core-GSM network" SS7-based Signalling GSM BSS Circuit-Sw itched Voice Circuit-Sw itched Data (HSCSD) GPRS IP-Backbone UMTS BSS Packet-Sw itched Data (GPRS) 3rd Generation Radio Circuit-Switching (CS) Paket-Switching / IP-Routing Vision for Beyond 3rd Generation Cellular PSTN ISDN CS / IP Gatew ay Internet High Bandw idth Trunks IP-based "core-GSM network" IP-Sw itching Backbone Mobile-IP & RSVPbased Signalling Voice & Data ov er IP ov er GPRS GSM BSS QoS Support in GPRS IP-Multicast Proxies (Security, Transcoding) UMTS BSS 3rd Generation Radio ICEBERG Vision • How far can we go with a packetswitched cellular core network? • How do you provision an IP network for large numbers of voice users? • What new kinds of data-oriented services can be deployed? 38 Mobility Management • Mobile IP-GSM Mobility Interworking – Mobile IP-GSM authentication interworking – GSM HLR/VLR interaction in an Internet signaling context – Scalability of Mobile IP/hierarchical agents • Multicast support for mobility – Alternative approach for mobility based on M/C addresses – Exploit multicast routing to reach mobile nodes without explicit handoff – Combine with real-time delivery of voice and video • Generalized redirection agents – Policy-based redirection: e.g., 1-800 service, email to pagers, etc. – Redirection agents collocated with multicast tree branching points 39 Packet Scheduling • Validated VINT modeling suite for GSM media access, link layer, routing, and transport layers – GSM channel error models – Better understanding of sources of latency in cellular link and methods to circumvent this • QoS-aware High Speed Circuit Switched Data (HSCSD), General Packet Radio System (GPRS), and Wideband CDMA (W-CDMA) link scheduling – – – – RSVP signaling integration with bottleneck link scheduling Fairness and utilization for TCP and RTP flows Delay bound scheduling for R/T streams Exploiting asymmetries in downstream/upstream slot assignment, CDMA self-interference 40 New Services • Proxies for Telephony-Computing Integration – GSM-vat-RTP interworking: handset-computer integration – Encapsulating complex data transformations » Speech-to-text, text-to-speech – Composition of services » Voice mail-to-email, email-to-voice mail – Location-aware information services » E.g., traffic reports – Multicast-enabled information services » Multilayered multicast: increasing level of detail as number of subscribed layers increase • Demonstrate the speed and ease with which new services can be developed • Develop innovative new services at the intersection of voice and data 41 Potentially Any Network Service (PANS) Same service in different networks Service handoff between networks 2-way Paging GSM PSTN IAP IAP IAP E.g., “follow me” service e.g., any-to-any service IP IAP WIP IAP Iceberg Access Points (Beyond H.323 gateways) • Provide policy engine • Handle routing, security 42 PANS Issues • • • • • • • • Entities: What are the endpoints? Naming: “What’s in a name?” Authentication: Entity to Entity authentication Billing: Charging entities, not “lines” Routing: QoS and cost issues Source conversion: Text-to-Speech, etc. Network management: Monitoring, provisioning Intelligent terminals: Services at the terminal 43 Service Mobility as a First-Class Object “Randy@Berkeley” Universal Names: Globally unique IDs An Entity has a universal name and a profile; Entities are people or processes OfficePSTN (Teaching): 510-642-8778 OfficePSTN (Chair): 510-642-0253 DeskIP: dreadnaught.cs.berkeley.edu:555 LaptopIP: polo.cs.berkeley.edu:555 PCS: 510-388-8778 Cellular: 510-409-6040 E-mail: [email protected] Home: 415-777-3382 Profile: set of domain-specific names 44 Iceberg Inter-Domain Naming Protocol • Naming: – Reuse network’s local naming services – Single resolution point for universal names • Routing: – – – – Handles inter-network signaling Users provide policies IDNP gatekeepers provide policy engine IDNP provides replication and consistency control 45 IDNP Issues IAP Call(Randy@Berkeley, Caller’s network, Interactive, CallerID certificate) IDNP Server Profile weeks/months Replicated Information: System • Real-time? State • Lazy? minutes/hours • Epidemic? Policy days/weeks IDNP Server 46 Authentication and Billing • Networks uses different mechanisms – PSTN autheticates “on-line” – GSM uses SIM card (Carrier-carrier agreement) » Original cellular networks used personal agreements – IP uses host address, X.509, etc. • Iceberg certificates - two versions – Online verification by home network (Carrier) – Offline verification by local network (Personal/Visa) 47 Call-Forwarding Example • Called party can change policy and profiles from any network – Secure identification of entities – IDNP handles propagation of changes • IDNP can expose domain-specific addresses or hide them for privacy • Domain-specific information exposed to apps – Interactive? – Billing policies 48 Presentation Outline • • • • • Internet-Scale Systems A New Service Architecture Integration of Computing and Communications Opportunity for Cooperation Summary and Conclusion 49 Berkeley Tradition of Experimental Computing Systems Research Evaluate existing technology to understand its weaknesses Time Travel using today’s too expensive technology to prototype tomorrow’s systems Design new computing systems architectures Deploy understand implementation complexities and sources of performance gain/loss 50 Internet-Scale Systems Research Group Lead the evolution of the Internet through long-term research combined with the deployment of novel realworld large-scale systems and protocols – Unify on-going and future research projects in distributed computing, network protocols, services, access, new applications – Facilitate technology transfer and standardization – Work closely with industrial partners in an open laboratory environment We would like AT&T to be a charter member 51 Benefits of Sponsorship • Involvement with outstanding Berkeley graduate students • Participation in large-scale, inter-disciplinary, precompetitive research efforts with only modest investment, leveraging investment of other industrial partners • Access to all ISRG-developed software, prototypes, simulation tools, and testbeds • Early access to group’s research results through on-campus participation and retreats • Support the expansion of cadre of researchers with expertise in Internet-scale systems 52 Presentation Outline • • • • • Internet-Scale Systems A New Service Architecture Integration of Computing and Communications Opportunity for Cooperation Summary and Conclusion 53 Emerging Distributed System Architecture Spanning Processing and Access Personal Information Management and “Smart Spaces” Distributed Videoconferencing Room-scale Collaboration Speech and Location Aware Applications ICEBERG Computer-Telephony Services MASH Media Processing Services Active Services Architecture TranSend Extensible Proxy Services Distributed Computing Services: NINJA Computing and Communications Platform: Millennium/NOW 54 NINJA and ICEBERG • NINJA: Distributed Service Architecture – Service model based on Operators, Paths, Services – Platform model based on Units, Active Routers, Bases • ICEBERG: Computer-Telephony Integration – IP-based backbone for cellular networks » Mobility and service interoperability in the context of diverse access networks » Performance issues: GPRS scheduling and IP scaling for mobile telephony applications » New services: Smart Spaces and PIM • Internet Systems Research Group – “Lucent establishes research wing at Stanford” !?!?!? 55