* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download cis185-ROUTE-lecture2-EIGRP-Part2
Distributed firewall wikipedia , lookup
Wireless security wikipedia , lookup
Internet protocol suite wikipedia , lookup
Point-to-Point Protocol over Ethernet wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Deep packet inspection wikipedia , lookup
IEEE 802.1aq wikipedia , lookup
Network tap wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Computer network wikipedia , lookup
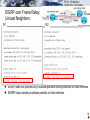
Serial digital interface wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Airborne Networking wikipedia , lookup
Routing in delay-tolerant networking wikipedia , lookup
Packet switching wikipedia , lookup
Wake-on-LAN wikipedia , lookup
CIS 185 Advanced Routing Protocols EIGRP Part 2 Rick Graziani Cabrillo College [email protected] Fall 20101 EIGRP Part 2 EIGRP over Frame Relay EIGRP over MPLS EIGRP Load Balancing EIGRP Bandwidth across WAN Links Authentication EIGRP Scalability in Large Networks 2 Materials Book: Implementing Cisco IP Routing (ROUTE) Foundation Learning Guide: Foundation learning for the ROUTE 642-902 Exam By Diane Teare Book ISBN-10: 1-58705-882-0 ISBN-13: 978-1-58705-882-0 eBook ISBN-10: 0-13-255033-4 ISBN-13: 978-0-13-255033-8 3 Configuring and Verifying EIGRP in an Enterprise WAN Physical Frame-Relay Multipoint and point-to-point Frame-Relay subinterfaces Multiprotocol Label Switching (MPLS) virtual private networks (VPNs) Ethernet over Multiprotocol Label Switching (EoMPLS) 4 Frame Relay Basics Frame Relay Basics A switched WAN technology Virtual circuits (VCs) are created by a Service Provider (SP) Multiple logical VCs to be multiplexed over a single physical interface. Typically PVCs identified by a locally significant data link connection identifier (DLCI). For IP connectivity: A mapping between IP addresses and DLCIs must be defined, either dynamically or statically. 5 Frame Relay Basics By default, a Frame Relay network is an NBMA network. Like multiaccess networks (Ethernet LANs) All routers are on the same subnet But broadcast (and multicast) packets CANNOT be sent just once as they are in a broadcast environment such as Ethernet. Cisco IOS implements pseudo-broadcasting Router creates a copy of the broadcast or multicast packet for each neighbor reachable through the WAN media (over the PVC). Sends the copy of the broadcast or multicast packet over the appropriate PVC for that neighbor. 6 EIGRP over Frame Relay: Physical Interface with Dynamic Mapping R1 Same Subnet DLCI 100 DLCI 130 Inverse ARP is on by default Automatically maps the IP address of the devices at the other end of the PVCs to the local DLCI number. Split horizon is disabled by default on Frame Relay physical interfaces. Routes from Router R2 can be sent to Router R3, and vise-versa. Note: Inverse ARP does not provide dynamic mapping for the communication between routers R2 to R3 because they are not connected with a PVC; this must be configured (mapped) manually 7 EIGRP over Frame Relay: Physical Interface with Dynamic Mapping R1 forms the adjacency with router R2 and R3 over the serial0/0 physical interface. R3 (and R2) forms an adjacency with router R1. No EIGRP relationship exists between routers R2 and R3. 8 EIGRP over Frame Relay: Physical Interface with Static Mapping R1 interface Serial 0/0 R3 encapsulation frame-relay ip address 192.168.1.103 255.255.255.0 frame-relay map ip 192.168.1.101 130 broadcast router eigrp 110 network 192.168.1.0 Using static mapping disables Inverse ARP No changes to the basic EIGRP configuration. Manual IP-to-DLCI mapping commands on the serial 0/0 interface are necessary on all three routers. Again, because split horizon is disabled by default on Frame Relay physical interfaces, routes from R2 can be sent to R3, and vise-versa. Note: R1 includes a Frame Relay map to its own IP address so it can ping its own interface. 9 EIGRP over Frame Relay: Physical Interface with Static Mapping interface Serial 0/0 R3 encapsulation frame-relay ip address 192.168.1.103 255.255.255.0 frame-relay map ip 192.168.1.101 130 broadcast frame-relay map ip 192.168.1.102 130 broadcast router eigrp 110 network 192.168.1.0 The adjacencies formed on R1 using static mapping are the same as those formed using dynamic mapping. R2 and R3 also form an adjacency with router R1. R2 and R3 can also form an EIGRP adjacency to each other if the IP-to-DLCI mapping for that connectivity is provided. Output shows that R3 has two neighbors (router R1 and R2), indicating that this mapping was provided on R3 (but not required between R2 and R3). 10 EIGRP over Frame Relay: Multipoint Subinterfaces Same Subnet DLCI 100 DLCI 103 DLCI 130 Separating a physical interface into multipoint subinterfaces allows each subinterface to be on a separate network. Multipoint subinterfaces are configured with the command: interface serial number.subinterface-number multipoint 11 EIGRP over Frame Relay: Multipoint Subinterfaces R1 interface Serial 0/0 no ip address encapsulation frame-relay interface serial 0/0/0.1 multipoint ip address 192.168.1.101 255.255.255.0 no ip split-horizon eigrp 110 frame-relay map ip 192.168.1.102 102 broadcast frame-relay map ip 192.168.1.103 103 broadcast router eigrp 110 network 192.168.1.0 network 172.16.1.0 0.0.0.255 R3 interface Serial 0/0 no ip address encapsulation frame-relay interface serial 0/0/0.1 multipoint ip address 192.168.1.103 255.255.255.0 frame-relay map ip 192.168.1.101 130 broadcast router eigrp 110 network 192.168.1.0 IP address-to-DLCI mapping on multipoint subinterfaces is done by either: Specifying the local DLCI value (frame-relay interface-dlci dlci) and relying on Inverse ARP Using manual IP address-to-DLCI mapping. The physical interface serial 0/0 is configured for Frame Relay encapsulation and does not have an IP address assigned to it. 12 Note: The spoke router does not have a multipoint-subinterface. EIGRP over Frame Relay: Multipoint Subinterfaces R1 interface Serial 0/0 no ip address encapsulation frame-relay interface serial 0/0/0.1 multipoint ip address 192.168.1.101 255.255.255.0 no ip split-horizon eigrp 110 frame-relay map ip 192.168.1.102 102 broadcast frame-relay map ip 192.168.1.103 103 broadcast router eigrp 110 network 192.168.1.0 network 172.16.1.0 0.0.0.255 R3 interface Serial 0/0 no ip address encapsulation frame-relay interface serial 0/0/0.1 multipoint ip address 192.168.1.103 255.255.255.0 frame-relay map ip 192.168.1.101 130 broadcast router eigrp 110 network 192.168.1.0 Split horizon is enabled by default on Frame Relay multipoint interfaces. R2 and R3 need to provide connectivity between their connected networks so… EIGRP split horizon is disabled on the multipoint subinterface of router R1 with the no ip split-horizon eigrp as-number command. 13 EIGRP over Frame Relay: Multipoint Subinterfaces Verify with show ip eigrp neighbors R1 forms an adjacency with routers R2 and R3 over the serial0/0.1 multipoint subinterface. R2 and R3 form the adjacency with R1 Note: R2 and R3 could form an adjacency between each other if the IP address14 to-DLCI mapping for that connectivity is provided. (not required) EIGRP over Frame Relay: Unicast Neighbors R1 R2 Not all Frame Relay service providers support multicasts/broadcasts so routing information must be sent as unicasts. router configuration command: neighbor {ip-address | ipv6-address} interface-type interface-number Defines a neighboring router to exchange EIGRP routing information. Instead of using multicast packets, EIGRP exchanges routing information with the specified neighbor using unicast packets. 15 EIGRP over Frame Relay: Unicast Neighbors R1 R2 EIGRP does not process any multicast packets coming inbound on that interface EIGRP stops sending multicast packets on that interface. 16 EIGRP over Frame Relay: Unicast Neighbors R1 R2 R1 is configured with a neighbor command for R2. R1 will therefore not accept multicast packets on Serial 0/0.1 anymore. R2 must also be configured with a neighbor command for R1 to establish an adjacency. R1 and R3 are not configured with a neighbor command for each other. Therefore, R1 and R3 will not form an adjacency. 17 EIGRP over Frame Relay: Unicast Neighbors R1 R3 interface Serial 0/0 no ip address encapsulation frame-relay interface serial 0/0/0.1 multipoint ip address 192.168.1.103 255.255.255.0 frame-relay map ip 192.168.1.101 130 broadcast router eigrp 110 network 192.168.1.0 Because R3 is not using the neighbor command it tries to communicate with multicast packets on its Serial 0/0/.1. However, neighborship is not established because neither R1 nor Router R2 is accepting multicast packets. 18 EIGRP over Frame Relay: Point-to-Point Subinterfaces Same Subnet DLCI 100 DLCI 103 DLCI 130 Point-to-point subinterfaces are logical interfaces: Emulates a leased line network Provide a routing equivalent to point-to-point physical interfaces As with physical point-to-point interfaces, each interface requires its own subnet. Frame Relay point-to point is applicable to hub and spoke topologies. 19 EIGRP over Frame Relay: Point-to-Point Subinterfaces R1 and R3: The physical interface serial 0/0 is configured for Frame Relay encapsulation The physical interface does not have an IP address assigned to it 20 EIGRP over Frame Relay: Point-to-Point Subinterfaces Point-to-point subinterfaces are created with the command: interface serial number.subinterface-number point-to-point IP address-to-DLCI mapping on point-to-point subinterfaces with: frame-relay interface-dlci dlci R1 has two point-to-point subinterfaces, one for each subnet and DLCI. Note: R3 does not need a subinterface. 21 EIGRP over MPLS MPLS (Multiprotocol Label Switching) is an IETF standard. Combines the: Advantages of Layer 3 routing Benefits of Layer 2 switching Short fixed-length labels are assigned to each packet at the edge of the MPLS network. Allows for scalable VPNs, end-to-end QoS, and other IP services that allow efficient utilization of existing networks with simpler configuration, management, and quicker fault correction. 22 What is MPLS? New WAN technology originally defined in RFC 3031 by: Cisco Systems Force 10 Networks Juniper networks Started out as Tag Switching introduced by Ipsilon (now part of Nokia) What is the problem MPLS is trying to solve? Layer 3 End-to-end circuits Advantages IP routing provides dynamic, automatic path setup Provides best path and backup paths Provides QoS Disadvantages Latency in hop-by-hop Layer 3 lookup Latency in routing – switching – packet forwarding process What is the problem MPLS is trying to solve? Layer 2 End-to-end circuits (ATM, Frame Relay) Advantages Circuits (SVC or PVC) means destinations are pre-established at switches Less latency, switched only - no Layer 3 lookups Disadvantages Circuits difficult to manage - must use management software or human configuration. QoS and SLAs are individually managed MPLS WAN Connectivity MPLS extends Layer 2 or Layer 3 natively between sites. The MPLS network although owned by a service provider but is an extension of the enterprise network. MPLS network is like a single router or switch with multiple interfaces. MPLS philosophy is that the Layer 3 header contains significantly more information than is necessary to forward the packet. MPLS Terms MPLS domain – A contiguous set of nodes performing MPLS routing and forwarding. These are typically in one routing or administrative domain. Label Switching Router (LSR) – An MPLS node that is capable of forwarding labeled packets. Label – A short, fixed-length, physically contiguous identifier used to identify a group of networks sharing a common destination, usually of local significance. MPLS Ingress Node – An MPLS node that handles traffic entering an MPLS domain. MPLS Egress Node – An MPLS node that handles traffic leaving an MPLS domain. MPLS Operation A label identifies a flow of packets (for example, voice traffic between two nodes), also called a Forwarding Equivalence Class (FEC). Grouping of packets which can be used for QoS requirements Packets belonging to the same FEC receive the same treatment in the network. Determined by various parameters including: source or destination IP address port numbers IP protocol IP precedence 28 MPLS Operation MPLS network nodes are called Label-Switched Routers (LSRs) Use the label to determine the next-hop for the packet. Do not need to examine the packet’s IP header Forwards packets based on the label. After a path has been established: Packets destined to the same endpoint with the same requirements can be forwarded based on these labels without a routing decision at every hop. Labels usually correspond to Layer 3 destination addresses, which makes MPLS equivalent to destination-based routing. 29 MPLS Operation A Label-Switched Path (LSP) must be defined for each FEC before packets can be sent. Labels are locally significant to each MPLS node only Therefore nodes must communicate what label to use for each FEC. Label Distribution Protocol Enhanced version of the Resource Reservation Protocol. An interior routing protocol, such as OSPF or EIGRP is also used within the MPLS network to exchange routing information. 30 MPLS Operation Each of the MPLS nodes has previously communicated the labels it uses for each of the defined FECs to its neighboring nodes. Packet A and Packet B represent different flows; for example, Packet A might be from an FTP session, whereas Packet B is from a voice conversation. Without MPLS, these packets would take the same route through the network. 31 R6 – Layer 3 Routed R5 – MPLS Switched 94 R4 – MPLS Switched 94 17 R3 – MPLS Switched 17 5 R2 – MPLS Switched (popped) 5 R1 – Layer 3 Routed Note: Label allocation, label imposing, label swapping, and label popping usually happen in the service provider network, not the customer (enterprise) network. Customer routers never see a label. 32 MPLS Features MPLS Only one examination of the packet Only one assignment to the FEC This is done at the MPLS ingress node Service Provider Offerings VPNs: First built using leased lines with PPP and HDLC encapsulations. Later, Layer 2 VPNs based on point-to-point data link layer connectivity, using ATM or Frame Relay virtual circuits. MPLS VPNs were introduced to provide a unified network for Layer 3 VPN services. Any Transport over MPLS (AToM) was introduced to facilitate this Layer 2 connectivity across an MPLS backbone. 34 Layer 2 and Layer 3 MPLS VPN Solutions Layer 2 MPLS VPN provides a Layer 2 service across the backbone R1 and R2 are connected together on the same IP subnet. Layer 3 MPLS VPN provides a Layer 3 service across the backbone R1 and R2 are connected to ISP edge routers; on each side, a separate IP subnet is used. 35 Layer 2 and Layer 3 MPLS VPN Solutions Site #3 The network is divided into: Customer-controlled part (C-network) Provider-controlled part (P-network) Contiguous portions of C-network are called sites and are linked to the P-network via Customer Edge routers (CE-routers). The CE-routers are connected to the PE-routers (Provider Edge routers). The core devices in the provider network (P-routers) provide transport across the provider backbone and do not carry customer routes. 36 The service provider connects customers using MPLS VPNs. Layer 2 and Layer 3 MPLS VPN Solutions Site #3 Each customer is assigned an independent routing table - the virtual routing and forwarding (VRF) table in the PE router. PE routers maintain separate routing tables for each customer. Routing across the provider backbone is performed by another routing process that uses global IP routing table, the P-router. 37 Layer 3 MPLS VPNs In a Layer 3 MPLS VPN, the following requirements must be met: The customer routers (the CE-routers) are not be MPLS VPN-aware Run standard IP routing software. The provider core routers (the P-routers) must not carry customer (VPN) routes, to make the MPLS VPN solution scalable. The provider edge routers (PE-routers) must support MPLS VPN services and traditional IP services. 38 Layer 3 MPLS VPNs L3 192.168.1.0/30 network 192.168.2.0/30 network R1 and R2 are configured for EIGRP as if there were a corporate core network between them. EIGRP parameters between R1 and R2 (such as the AS number, authentication password, and so on) are often governed/coordinated by the service provider. 39 Layer 3 MPLS VPNs L3 R1 establishes an EIGRP neighbor relationship with the PE1 router, R2 establishes an EIGRP neighbor relationship with the PE2 router. Routers R1 and R2 do NOT establish an EIGRP neighbor relationship with each other. 40 Layer 2 MPLS VPNs Layer 2 MPLS VPN, an MPLS backbone provides a Layer 2 Ethernet port-toport connection between the two customer routers R1 and R2. R1 and R2 are exchanging Ethernet frames. PE1 router: Takes the Ethernet frame received from the directly connected R1 Encapsulates it into an MPLS packet Forwards it across the backbone to the PE2 router. The PE2 router decapsulates the MPLS packet and reproduces the Ethernet frame on its Ethernet link to router R2. This process is a type of AToM, called EoMPLS (a type of Metro Ethernet Service. 41 Layer 2 MPLS VPNs 192.168.1.100/27 network EIGRP over EoMPLS: No changes to the EIGRP configuration from the customer perspective. EIGRP needs to be enabled with the same AS number on both routers. network command includes the interface toward the PE router (PE1 and PE2) over which the routers R1 and R2 will form their neighbor relationship. From the EIGRP perspective, the MPLS backbone and routers PE1 and PE2 are not visible. 42 Layer 2 MPLS VPNs A neighbor relationship is established directly between routers R1 and R2 over the MPLS backbone. 43 EIGRP Load Balancing 44 Variance command Router(config)# router eigrp 1 Router(config-router)# variance multiplier Cisco IOS allows up to 16 equal-cost paths, 4 by default. EIGRP does unequal cost load balancing, forwarding packets relative to the metric. The variance command: Instructs the router to include routes with a metric less than or equal to n times the minimum metric route for that destination n is the number specified by the variance command (1 -128). Default = 1 The maximum-paths number EIGRP is used to sent the number of loadbalancing paths (up to 16 paths). 1 disables load balancing Note: If a path isn't a feasible successor, then it isn't used in load balancing. Note: Load balancing is only performed on traffic that passes through the router, not traffic generated by the router. 45 Variance command FS Succ FS Successor: R3 with a FD of 20 Feasible Successors: R2 and R5 R2’s AD of 10 < R3’s FD of 20 R5’s AD of 10 < R3’s FD of 20 R4 is NOT a FS because it’s AD of 25 > R3’s FD of 20 46 Variance command FS Succ FS x 2 = 40 R1(config)# router eigrp 110 R1(config-router)# variance 2 Variance = 2 R3’s FDv 2 x 20 (FD) = 40 R2 is added as successor to R1’s routing table: R2’s FD of 30 < R3’s FDv of 40 R5 is NOT added to R1’s routing table: R5’s FD of 50 > R3’s FDv of 40 R5 would still be a Feasible Successor Note: R4 is not considered even if it’s FD was < or = R3’s FDv of 40 because it is not a FS The load in is balanced proportional to the bandwidth. FD of the route via router R2 is 30 FD of the route via router R3 is 20 Ratio of traffic between the two paths is via R2: 3/5 and via R3: 2/5 47 EIGRP Bandwidth Across WAN Links 48 The bandwidth-percent command ip bandwidth-percent eigrp as-number percent interface serial 0/0/0 bandwidth 56 ip bandwidth-percent eigrp 209 75 The bandwidth-percent command configures the percentage of bandwidth that may be used by EIGRP on an interface. By default, EIGRP is set to use only up to 50% of the bandwidth of an interface to exchange routing information. In order to calculate its percentage, the bandwidth-percent command relies on the value set by the bandwidth command. Allows EIGRP to use up to 75 percent (42 kbps) of a 56-kbps serial link in autonomous system 209. 49 Link Utilization on Frame Relay Cisco IOS assumes that point-to-point Frame Relay subinterfaces are operating at the default speed of the interface. In many implementations, however, only fractional speeds (such as a fractional T1) are available. Therefore, when configuring these subinterfaces, set the bandwidth to match the contracted CIR (Committed Information Rate). 50 Multipoint interfaces Multipoint interfaces the bandwidth is shared equally by all neighbors. EIGRP uses the bandwidth command on the physical interface divided by the number of Frame Relay neighbors connected on that physical interface to get the bandwidth attributed to each neighbor. When configuring multipoint interfaces, configure the bandwidth to represent the minimum CIR times the number of circuits. 51 Frame Relay Multipoint All VCs have same CIRs Bandwidth of 224 kbps Configured bandwidth on the interface, resulting in (224 / 4 = ) 56 kbps allocated per circuit. This 56-kbps allocation matches the provisioned CIR of each circuit. 52 Frame Relay Multipoint All VCs have different CIRs One circuit = CIR of 56 kbps Other three circuits = CIR of 256 kbps. The interface on Router C has been configured for a bandwidth equal to: The lowest CIR times the total number of circuits 56 * 4 = 224 This configuration protects against overwhelming the slowest-speed circuit in the topology. 53 Frame Relay Multipoint Point-to-Point and Multipoint The low-speed circuit configured as point-to-point. The remaining circuits are multipoint Their respective CIRs are added up to set the interface’s bandwidth 256 + 256 + 256 = 768 On the multipoint interface, the bandwidth is shared equally among all circuits. Thus, the bandwidth will be split into 3, with 256 kbps allocated to each circuit. 54 Frame Relay Multipoint Hub and Spoke oversubscribed 256 kbps CIR 64 BW 25 CIR 64 BW 25 CIR 64 BW 25 CIR 64 BW 25 256 kbps link from Router C to the Frame Relay provider. Hub-and-spoke oversubscribed topology with 10 VCs to the remote sites. (Only 4 of the 10 remote sites are shown in the figure.) The circuits are provisioned as 64-kbps links, but there is insufficient bandwidth on Router C (the hub) to support the allocation. For example, if the hub tries to communicate to all remote sites at the same time, the bandwidth that is required exceeds the available link speed of 256 kbps for the hub—10 times the CIR of 64 kbps equals 640 kbps. EIGRP AS 63 55 Frame Relay Multipoint Hub and Spoke oversubscribed 256 kbps CIR 64 BW 25 CIR 64 BW 25 CIR 64 BW 25 CIR 64 BW 25 EIGRP AS 63 In a point-to-point topology: All VCs are treated equally and are therefore configured for exactly onetenth of the available link speed (25 kbps). Alternatively the Serial 0 main interface could be configured with the bandwidth 256 command. 56 Authentication 57 Simple and MD5 Authentication Neighbor router authentication - Routers only participate in routing based on predefined passwords. Routers use two types of authentication: Simple password authentication (also called plain text authentication) Supported by Integrated System-Integrated System (IS-IS), OSPF, and Routing Information Protocol Version 2 (RIPv2) MD5 authentication Supported by OSPF, RIPv2, BGP, and EIGRP Provides authentication but does not provide confidentiality. The contents of the protocol packets are not encrypted. By default, no authentication is used for EIGRP packets. 58 Planning for EIGRP Authentication Configuring EIGRP MD5 authentication requires the following steps: Step 1: Configure the authentication mode for EIGRP Step 2: Configure the key chain Step 3: Optionally configure the keys’ lifetime parameters Step 4: Enable authentication to use the key(s) in the key chain 59 MD5 Configuration Example EIGRP router configuration is not shown. 60 MD5 authentication is configured on the serial 0/0/1 interface with: MD5 Configuration Example ip authentication mode eigrp 100 md5 The key chain R1chain command enters configuration mode for the R1chain key chain. Two keys are defined in this key chain. Key 1 has the string: firstkey Key 2 has the string secondkey Each key has an authentication string and lifetime specified. The administrator wants to change the keys on all the routers in the network each month to improve the security. The administrator configures an overlap of one week to change the keys on all the routers The validity of key 2 is configured 1 week before the expiration of key 1 to allow the new key to be applied to all 61 the routers in the network. Send and Receive Keys MD5 Configuration Example Sending: send-lifetime Only one key is used for sending EIGRP packets depending upon the lifetime of that key. The router will use the first key (by key number) which has a valid lifetime for sending EIGRP packets. Receiving: accept-lifetime When receiving an EIGRP packet any valid key can be used as long as it’s lifetime matches and the keystring matches. If there are multiple valid keys the router will use the first key (by key number) which has a valid lifetime for accepting EIGRP packets. 62 MD5 Configuration Example Key 1 is set to firstkey. Acceptable for receiving EIGRP packets received from January 1, 2009 onward: accept-lifetime 04:00:00 Jan 1 2009 infinite However, send-lifetime 04:00:00 Jan 1 2009 04:00:00 Jan 31 2009 specifies that this key is only valid for use when sending packets until January 31, 2009 It is no longer valid for use in sending packets after January 31st 2009. Key 2 is set to secondkey Acceptable for receiving EIGRP packets from January 25, 2009 onward: accept-lifetime 04:00:00 Jan 25 2009 infinite. This key can also be used for sending EIGRP packets from January 25, 2009 onward send-lifetime 04:00:00 Jan 25 2009 infinite 63 MD5 Configuration Example The authenticating key ID (number) and the key string on both the sending router and the receiving router must be the same. The key chain can be different EIGRP router configuration is not shown. 64 MD5 Configuration Example The authenticating key and a key ID on both the sending router and the receiving router must be the same. The key chain can be different The router uses the first, by key number, valid key for sending packets. R1 (sending): Will use key 1 for sending, from January 1st to 31st, 2009, Will use key 2 for sending as of 4:00 am on January 31st 2009. 65 MD5 Configuration Example The authenticating key and a key ID on both the sending router and the receiving router must be the same. The key chain can be different R1 (receiving): Will accept key 1 for received packets, from January 1st 2009, Will also accept key 2 for received packets, from January 25th 2009. All other MD5 packets will be dropped. 66 Verifying Authentication 67 Verifying Authentication Key chain R1chain and both keys key 1 (with authentication string firstkey) and key 2 (with authentication string secondkey) are displayed. Under each key, the lifetime of the key is also shown. 68 EIGRP Scalability in Large Networks 69 EIGRP Scalability Operating one large flat EIGRP network is normally not scalable. Some issues to consider include: Large routing tables that need to be processed High memory demands: Large topology table Large number of routes in a routing table Large number of neighbors in the neighbor table (some cases) High bandwidth demands Exchange of a large number of routing updates Sending many queries and replies 70 EIGRP Queries and Stuck in Active Router loses a route and does not have an FS in its topology table, it looks for an alternative path to the destination. This is known as going active on a route If a neighbor does not have an alternative route, it queries each of its own neighbors for an alternative path. The queries then propagate through the network, thus creating an expanding tree of queries. When a router answers a query, it stops the spread of the query through that branch of the network . 71 Stuck in Active (SIA) Router B Queries Replies SIA Router C Router D X Router A X X When EIGRP returns a stuck in active (SIA) message, it means that it has not received a reply to a query. Summarization can help prevent SIA. 72 Stuck-in-Active EIGRP 101 EIGRP 102 The most common reasons for SIA routes are as follows: The router is too busy to answer the query The link between the two routers is not good A failure causes traffic on a link to flow in only one direction. This is called a unidirectional link. Misconceptions Using multiple EIGRP domains (AS’s) to simulate OSPF areas (later) will help limit the scope of the queries. This is not true, the boundary router will create a new EIGRP query into the other EIGRP domain. 73 Preventing SIA Cisco IOS Software Release 12.1(5) and later, with the Active Process Enhancement feature. This feature enables an EIGRP router to monitor the progression of the search for a successor route and ensure that the neighbor is still reachable. 74 BEFORE Active Process Enhancement feature. X A X B 10.1.1.0/24 gone; no FS Never heard from B So after 3 min reset adjacency along with all networks Query 3 min timer 10.1.1.0/24 gone; no FS No entry so sends Query Bad link; reply never makes it C No entry send Reply 10.1.1.0/24 gone; Remove 10.1.1.0/24 75 AFTER Active Process Enhancement feature. Thanks for letting me know, A I will not terminate our adjacency. After 1.5 min SIA Query SIA Reply: I’m ok but waiting on C B After 1.5 min SIA Query (3 attempts until I terminal adjacency with C) C X 10.1.1.0/24 gone; no FS Query The neighbor relationship between Routers A and B remains intact. 10.1.1.0/24 gone; no FS No entry so sends Query Bad link; reply never makes it No entry send Reply 10.1.1.0/24 gone; Remove 10.1.1.0/24 76 EIGRP Query Range Limiting the scope of query propagation through the network (the query range), also known as query scoping. 77 Router A was FS Now Successor Can’t reply until I hear From Router A X Router A was FS Now Successor SIA Timers Expire and adjacencies are reset NO FS Can’t reply until I hear From Routers C,D,E Router A was FS Now Successor Example in the book – this is the simplified version (What if there were 100 routers!) When the query process starts, each path receives duplicate queries because of the redundant topology. Not only are the remote routers required to respond to queries from the regional offices, but they also continue the search by reflecting the queries back toward the other regional office’s router. This significantly complicates the convergence process on the network. 78 EIGRP Query Range Scalable Nonscalable Configure route summarization using the ip summary-address eigrp command on the outbound interfaces of the appropriate routers. Network must be designed so it is scalable Configure the remote routers as stub EIGRP routers. 79 When a router has received only a summary route, the specific network is not in the routing table. So the router replies to the query with a “network 10.0.0.0/24 unreachable” message and does not extend the query any further. 80 Stub Routers Stub Routers Introduced with IOS 12.0 Stub router Only has one neighbor Only needs a default route Commonly used in a hub and spoke network topology. Helps with convergence 82 Stub Routers Queries X I’m a Stub Only the remote router is configured as a stub. Only specified routes are propagated from the remote (stub) router. Any neighbor will not query the stub router for any routes. Stub router will send a special peer information packet to all neighboring routers to report its status as a stub router. 83 Stub Routers router eigrp 1 network 10.0.0.0 eigrp stub 84 Queries Stub Routers X I’m a Stub receive-only – Stub does not send any route. No other keyword can be specified, Use this option if there is a single interface on the router. connected (default) – Stub sends connected routes if the EIGRP network command is used (10.1.1.0/24). Otherwise you will need to use the redistribute connected command under the EIGRP process (later). static – Stub sends static routes in its routing table. Redistributing static routes with the redistribute static command is still necessary (later). summary (default) – Stub will send summary routes. Configured with the ip summary-address eigrp command or automatically at a major network border router with the auto-summary command enabled. redistribute - Stub will send redistributed routes. Redistributing routes with the redistribute command is still necessary. 85 eigrp stub connected eigrp stub connected Router B will advertise only 10.1.2.0/24 to Router A. Notice that although 10.1.3.0/24 is also a connected network. It is not advertised to Router A because there is not a network 10.1.3.0 0.0.0.255 command, and connected routes are not redistributed. 86 eigrp stub summary Router B will advertise only 10.1.2.0/23, the summary route that is configured on the router, to Router A. eigrp stub summary 87 eigrp stub static eigrp stub static Router B will advertise only 10.1.4.0/24, the static route that is configured on the router, to Router A. (Note that the redistribute static command is configured on Router B.) 88 eigrp stub receive-only Router B will not advertise anything to Router A. eigrp stub receive-only 89 eigrp stub redistributed Router B will advertise only 10.1.4.0/24, the redistributed static route, to Router A. eigrp stub redistributed 90 Graceful Shutdown Goodbye message feature, is designed to improve EIGRP network convergence. Router B is being reconfigured (EIGRP process shutdown). Router A would normally have to wait for its hold timer to expire before it would discover the change and react to it. Packets sent during this time would be lost. 91 Graceful Shutdown Graceful shutdown - A goodbye message is broadcast when an EIGRP routing process is shut down, to inform adjacent peers about the impending topology change. Sends a Hello packet with K values all equal to 255 EIGRP peers will synchronize and recalculate neighbor relationships immediately instead of waiting for the hold timer expired. 92 CIS 185 Advanced Routing Protocols EIGRP Part 2 Rick Graziani Cabrillo College [email protected] Fall 2011