* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Network Management Concepts and Practice
Survey
Document related concepts
Wireless security wikipedia , lookup
Multiprotocol Label Switching wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Distributed firewall wikipedia , lookup
Deep packet inspection wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Computer network wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Network tap wikipedia , lookup
Airborne Networking wikipedia , lookup
Internet protocol suite wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Transcript
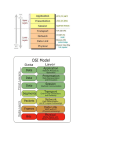
Network Management Concepts and Practice Author: J. Richard Burke Presentation by Shu-Ping Lin Outline Network Components Overview of Network Management Communication Architecture A communication architecture integrates many protocols and the software that implements them. These parts can be developed independently of one another as long as the developers adhere to the standard interfaces between them. OSI Reference Model OSI Reference Model The model does not specify how to implement the function in each layer. The functions in each layer are defined by protocol, which are implemented in software. The software in each layer provides services to the layer above it. Layering concept simplifies the development process and allows improvements of software in one layer without affecting other layers. Physical Layer This layer defines the electrical, mechanical, functional specifications for hardware that connects a device to the network. Physical layer standards would specify Connector’s size and shape Exact number of pins The signals that can be used to those pins Data Link Layer This layer specifies the procedures in order to achieve reliable point-to-point transfer of information between two devices. Data link layer can be divided into two sublayers. Logical Link Control Medium Access Control Data Link Layer (cont’d) CSMA/CD is implemented in Ethernet. CSMA means that a computer waits until there is no signal from any other computer on LAN before transmitting a message. CD reduces the probability that a collision will occur by backoff its transmission. Bridge is a typical device working on data link layer. Network Layer This layer provides the mechanisms for transporting a packet from the source networks to the destination network. Packets are messages constructed by the network layer and higher layers. A router is called a network layer device because it is controlled by protocols up to and including the network layer. Transport Layer Transport layer provides reliable and unreliable transport protocols. The reliable protocol, which is called the Transport Control Protocol (TCP), provides the mechanisms that enable end-to-end reliability. TCP accomplishes this by the use of automated acknowledgement and automated retransmissions. Transport Layer (cont’d) The unreliable transport protocol, which is called the User Datagram Protocol (UDP), places no constrains on the network. Best-effort delivery from the source device to the destination device is all that is required. UDP is used when speed is of the essence and the effort spent on ensuring reliability is not cost-effective. Session Layer The Session layer provides the mechanisms necessary to open and close multiple logical connections between processes on different PCs. These logical connections are called session. Many logical connections can use the same physical connection. Presentation Layer This layer provides a common representation of data transferred between peer application layer entities on different stations. Abstract syntax notation.one (ASN.1) format is useful for application layer. However, the layers below the presentation layer use a formant call transfer syntax. The presentation layer translates between ASN.1 and transfer syntax. Application Layer Common Application Service Elements provide service generally useful to a variety of application programs provided by vendors. Specific Application Service Elements service the additional needs of particular application programs. Frames Frame construction Application program makes a request. The request is passed to the appropriate application-layer-entity. The application-layer-entity constructs an Application layer protocol data unit (PDU). The Application layer PDU is then passed to the appropriate presentation-layerentity. This entity constructs a Presentation layer PDU. Frames (cont’d) PDUs continue to be constructed and passed to the layers below. This process continues until the Network layer PDU is received by the Data Link layer. The frame is construct in the Data Link layer. The Network Layer PDU is encapsulated in a Data Link layer header and trailer. Frames (cont’d) TCP/IP Protocol Stack Network Device Workstations Servers Repeaters Hubs Bridges Switches Routers Probes Workstations Workstations typical make use of the services of all layers of a protocol stack because they process the requests of application programs for information on servers. Server is like workstation making use of all layers of the protocol stack. Repeater Repeater amplifies the signal between segments and extends the length of a LAN. Repeaters are used on 10BASE2 and 10BASE5 LANs. Hubs A hub is a repeater with many input and output ports. Every transmission received by the hub on one port is amplified and retransmitted out of all other ports. Hub do not examine information in any field of the frame. Repeaters and hubs are consider a Physical layer device. Bridges Transparent bridge divides a LAN into segments that use the same media access control specification and it controls what traffic is passed between segments. uses bridge table to learn which devices are on which segments. Translating bridges connects networks using different MAC layer specifications. Bridges (cont’d) Errors and collisions that take place on one segment are not propagated to devices on the other segment. The use of switches rather than bridges is commonplace today. Switches A switch is a multiport bridge. Switches are typically configured to forward incoming frames to outgoing ports based on destination MAC addresses associated with those ports in the switch table. Switches also can be configured to drop frames based on MAC destination or to redirect frames to other MAC address. Switches (cont’d) Higher layers of the protocol stack are now being implemented in switches. Layer 3 switch also can function like router. Routers Router reads the Network layer header in packet to find the destination network address and then looks up the address in routing table. The routing table is a list of mappings of network addresses to ports that will get the packet to the destination networks by the best means. Routers (cont’d) Routing table Probes Probes are tools for learning about the details of the communication between devices. Probes can be placed on a network and the information they gather transferred to the Management Station fro analysis of the traffic. Outline Network Components Overview of Network Management Network Management Jobs of network management in early day Attaching PCs and server to a LAN using Network Interface Cards (NICs) Installing protocol stacks Configuring NIC I/O addresses and interrupts so as not to conflict with other NIC selections. Using Ping application to ensure that all devices on the network could communicate with one another Network Management (cont’d) Access control The manager might write a script for the server to control access to information on it. The script would provide access to drives, folders or files that use or group of users needed. Install a print server to manage the print jobs from each of the PCs. Network Management (cont’d) Network configuration If the networks were to be divided into subnets, then a bridge would be used to connect them. The manager would configure a routing table to enable connectivity according to network address, subnet address and subnet mask. Finally, installing user applications on PCs is necessary for interfacing correctly with OS. Maintenance After configuring primary network ingredients, here comes the maintenance. Network performance is not optimized, there will be software and hardware failures and network resources will change. The manager is required to make estimates of the network capacity. There was a need for minimal security. Maintenance (cont’d) New work management has divided into specialties nowadays. Administration Backing up servers Maintaining security Installing OS and applications Network engineer Be responsible for the health of the network and its availability to user. Network-Based Management As network has grown larger and more complicated, network manager needed to find more efficient way to determine and control the state of network. Some protocols could be used by network manager to remotely control devices. Simple Network Management Protocol (SNMP) Management Information Base (MIBs) Network Management Systems (NMS) Network Management Protocol Stack Management Station and Management Agent. Network Management Example Step 1 NMS calls for the service of the management process Step 2 the management process call the program the implements network management protocol. Step 3 NMP constructs a request packet to the program on the management agent. Step 4 NMP on the management agent cause the request packet to be passed to the agent process. Network Management Example (cont’d) Step 5 The agent process accesses the value of the requested variable and passes it to NMP. Step 6 NMP constructs the response packet which is sent back to the management station. Step 7 At the management station the program that implements the NMP receives the response packet. Step 8 The management process passes the requested value to the application program.