* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download ECPE 5984 - Virginia Alliance for Secure Computing and Networking
Survey
Document related concepts
Computer network wikipedia , lookup
Internet protocol suite wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Computer security wikipedia , lookup
Wireless security wikipedia , lookup
Airborne Networking wikipedia , lookup
Deep packet inspection wikipedia , lookup
Network tap wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Transcript
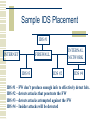
Network Intrusion Detection Systems Randy Marchany VA Tech Computing Center Blacksburg, VA 24060 [email protected] FAQ Information These notes come from the Network Intrusion Detection Systems FAQ by Robert Graham ([email protected] http://www.robertgraham.com/pubs/netw ork-intrusion-detection.html Introduction Intrusion – an attempt to compromise or misuse a computer system or network. Network Intrusion Detection System (NIDS) monitors packets on the network wire and attempts to discover if hackers are attempting to break into a system or cause a DOS. NIDS can run on the target or independent system. Introduction Network NIDS monitor many machines. System Integrity Verifiers (SIV) monitor system files to detect trojan versions of system binaries. It may log the attempt as it occurs. Log File Monitors (LFM) monitor log files generated by network services. Introduction Deception Systems aka honeypots, flytraps contain pseudo-services that emulate well-known holes in an attempt to trap hackers. Intruders – outsiders or insiders How do Intruders Get In? Physical Intrusion – console passwords, disk removal, etc. System Intrusion – hacker has a low privilege account on the system and uses a tool that exploits a weakness to gain system privilege. Remote Intrusion – gains access via a remote service on the system. Vulnerability Types Race Conditions – 2 programs accessing the same data at the same time. Software bugs – Buffer Overflows Unexpected Combinations – input is meaningless at 1 level but not at another. Unhandled Input – what happens when input doesn’t match specifications. System Configuration Default – vendor shipped configurations Lazy – sysadmins too lazy to tighten the system. Hole Creation – most programs can run in non-secure mode. Trust Relationships – one system trusts another. R-commands are an example. Password Cracking Trivial – names of people, places, things Dictionary – Unix Crack or NT/L0pht password cracking programs Brute Force – programs that try all possible combinations of characters. Sniffers & Design Flaws Shared Medium – base ethernet Server – sniffer runs on the server. Works on switched nets. Remote – SNMP based TCP/IP Protocol Flaws – smurf, synflood, IP spoofing. IP allows data to be changed anytime. IPSEC is a fix. System Flaws – Windows, Unix How Do They Get Passwords? Clear Text Passwords Encrypted Sniffing Replay Attack – the intruders don’t decrypt the passwords. They use the encrypted form to login the systems. Password file stealing Observation/Social Engineering – piece of paper attack Intrusion Steps Outside Reconnaissance – whois, DNS, WWW, FTP Inside Reconnaissance – ping sweep, inverse mapping, port scanning, rpcinfo, showmount, snmpwalk. Exploit – exploiting vulnerabilities discovered earlier. Intrusion Steps Foothold – gained entrance into the machine and now starts to hide the evidence. Install rootkits, trojans. Profit – taking advantage of the entry, the hacker now goes after the real target – information, $$, credit card info, etc. Joyride – systems used in a relay attack. Common WWW Exploits CGI – passing data to the command shell via shell metacharacters, using hidden variables, phf. WWW server IIS/RDP - ../../../../ attack to get files from the server. Alternate data streams ( Win95 names). Common WWW Exploits URL – fields can cause buffer overflows as it’s parsed in the HTTP header, displayed on the screen or saved in the cache history. Old IE bug would execute .LNK or .URL commands. HTTP headers can be used to exploit bugs because some fields are passed to functions that expect only certain information. Common WWW Exploits HTML – MIME-type overflow in Netscape Communicator’s <EMBED> command. Javascript – usually tries to exploit the “file upload” function by generating a filename and automatically hidden the SUBMIT button. Many fixes for this but equal # of circumventions. Common WWW Exploits Frames – part of JavaScript or Java hack (hiding web bugs). Hackers include link to valid site that uses frames then replace some of those frames with bad www pages. Java – normal Java applets have no access to the local system but sometimes they’d be more useful if they did have local access. Active X – works purely on trust model and runs in native mode. Buffer Overflows & DNS Attacks DNS – extra long DNS name is sent to the server. DNS names are limited to 256 bytes. RPC – statd, ttdbserverd, cmsd, snmpXdmid DNS Cache Poisoning – Every DNS packet contains a Question/Answer section. Vulnerable servers will believe and cache Answer you provide. Common Reconnaissance Scans and DOS Attacks Ping Sweeps TCP/UDP Scans OS identification Account Scans Ping of Death SYN Flood Land DDoS How Do NIDS Detect Intrusions? Anomaly detection – measures a baseline of stats like CPU utilization, disk activity, user logins, file activity. NIDS triggers when a deviation from this baseline occurs. Signature recognition – pattern matching attack probes. Uses large databases to detect the attack. Antiviral software uses this. Works only for known attacks. Matching Signatures with Incoming Traffic NIDS consists of special TCP/IP stack that reassembles datagrams and TCP streams. It uses: Protocol Stack Verification – search for protocol violations (SYN/FIN, etc.) Application Protocol Verification New Event Creation – log all application layer protocols for later correlation. NIDS Detect the Attack Firewall reconfiguration to block IP address. Chime – “Danger, Will Robinson!” alarm. Email or page admins. SNMP trap – send trap datagram to console. Syslog – record it in NT Event log or Unix syslog Save Evidence. Launch Program to handle the event. Terminate the TCP connection by sending a FIN. Other Countermeasures Firewalls – should be considered as the LAST line of defense. Authentication – password policies, single signon, removing cleartext protocols. VPN – secure connection for remote access. However, they decrease corporate security because both ends of the pipe are wide open. Where to locate IDS Network hosts Network Perimeter WAN/LAN Backbone Server farms Need to be on low-bandwidth nets to keep up with traffic. Fitting IDS with Security Framework Put firewalls between networks with different security requirements. Use scanners to check for exploits. Set host policy to conform with standards. Use NIDS to see what is actually happening. Use Host based IDS to flag intrusions. Create effective IRP. Implementing IDS OS – enable logging/auditing features Services – build/enable security in WWW servers, Email Servers, DB servers. NIDS – install in appropriate places. Firewalls – enable detection facilities. Install SNMP traps (Openview, Tivoli) Some NIDS Products BlackIce Defender (Network Ice) CyberCop Monitor (Network Associates) RealSecure (ISS) NetRanger (WheelGroup/Cisco) eTrust Intrusion Detection (CA) NetProwler (Axent) Centrax (CyberSafe) NFR (Network Flight Recorder) Dragon (Security Wizards) Network Grep System Based on raw packet capture and searching for patterns using a ‘grep’ tool. Extract the suspect string and compare to attack database. Libpcap ( library for packet capture) is the library used by Unix-based IDS. Feed output from libpcap to grep filters. Network Grep System Advantage – easy to update. Largest DB of signatures, fastest time-to-market for detecting attack scripts. Disadvantage – they detect the fewest # of serious intrusions. Example: scanning for default BO passwords. Can set off false positives. Network Grep System Advantages – system based on protocol analysis result in fewer false positives. Able to fully diagnose a problem. Example: BO PING is harmless. BO compromise is more serious. Sample IDS Placement IDS #1 INTERNET INTERNAL NETWORK FIREWALL IDS #3 IDS #2 IDS #4 IDS #1 – FW don’t produce enough info to effectively detect hits. IDS #2 – detects attacks that penetrate the FW IDS #3 – detects attacks attempted against the FW IDS #4 – Insider attacks will be detected Attacks Against the NIDS Blind the sensor with high traffic rates. Blind the event storage. Use decoy scans to fill up log space. DOS Packet Fragmentation Slow Scan Coordinated low-bandwidth attacks Attacks Against the NIDS Address spoofing Pattern Change Ptacek’s Paper on NIDS evasion. Questions to ask IDS Vendors How Much? What do signature updates cost? What traffic level blinds the IDS? How easy to evade? How scalable is it? How many signatures does it support? What IR features are included?