* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Week One
Survey
Document related concepts
Asynchronous Transfer Mode wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Network tap wikipedia , lookup
Computer network wikipedia , lookup
Airborne Networking wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Communication protocol wikipedia , lookup
Deep packet inspection wikipedia , lookup
Internet protocol suite wikipedia , lookup
UniPro protocol stack wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Transcript
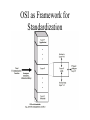
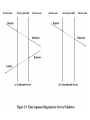
Data Communications Architecture Models What is a Protocol? • For two entities to communicate successfully, they must “speak the same language”. • What is communicated, how it is communicated, and when it is communicated must conform to some mutually acceptable conventions. • These conventions are referred to as a protocol. Key Elements of a Protocol • Syntax – Data formats – Signal levels • Semantics – Control information for coordination – Error handling • Timing – Speed matching – Sequencing Protocol Architecture • Task of communication broken up into modules • For example file transfer could use three modules – File transfer application – Communication service module – Network access module Simplified File Transfer Architecture A Three Layer Model • Application Layer • Transport Layer • Network Access Layer Application Layer • Support for different user applications • e.g. e-mail, file transfer Transport Layer • Reliable data exchange • Independent of network being used • Independent of application Network Access Layer • Exchange of data between the computer and the network • Sending computer provides address of destination • May invoke levels of service • Dependent on type of network used (LAN, packet switched etc.) Addressing Requirements • Two levels of addressing required • Each computer needs unique network address • Each application on a (multi-tasking) computer needs a unique address within the computer – The service access point or SAP Protocols in Simplified Architecture Protocol Data Units (PDU) • At each layer, protocols are used to communicate • Control information is added to user data at each layer • Transport layer may fragment user data • Each fragment has a transport header added – Destination SAP – Sequence number – Error detection code • This gives a transport protocol data unit Network PDU • Adds network header – network address for destination computer – Facilities requests Operation of a Protocol Architecture TCP/IP Protocol Architecture • Developed by the US Defense Advanced Research Project Agency (DARPA) for its packet switched network (ARPANET) • Used by the global Internet • No official model but a working one. – – – – – Application layer Host to host or transport layer Internet layer Network access layer Physical layer TCP/IP Protocol Suite • Dominant commercial protocol architecture • Specified and extensively used before OSI • Developed by research funded US Department of Defense • Used by the Internet Physical Layer • Physical interface between data transmission device (e.g. computer) and transmission medium or network • Characteristics of transmission medium • Signal levels • Data rates • etc. Network Access Layer • Exchange of data between end system and network • Destination address provision • Invoking services like priority Internet Layer (IP) • Systems may be attached to different networks • Routing functions across multiple networks • Implemented in end systems and routers Transport Layer (TCP) • Reliable delivery of data • Ordering of delivery Application Layer • Support for user applications • e.g. http, SMTP TCP/IP Protocol Architecture Model Some Protocols in TCP/IP Suite OSI Model • Open Systems Interconnection • Developed by the International Organization for Standardization (ISO) • Seven layers • A theoretical system delivered too late! • TCP/IP is the de facto standard OSI - The Model • A layer model • Each layer performs a subset of the required communication functions • Each layer relies on the next lower layer to perform more primitive functions • Each layer provides services to the next higher layer • Changes in one layer should not require changes in other layers OSI as Framework for Standardization OSI Layers • • • • • • • Application Presentation Session Transport Network Data Link Physical The OSI Environment OSI v TCP/IP Standards • Required to allow for interoperability between equipment • Advantages – Ensures a large market for equipment and software – Allows products from different vendors to communicate • Disadvantages – Freeze technology – May be multiple standards for the same thing Standards Organizations • • • • • Internet Society ISO ITU-T (formally CCITT) IEEE ANSI Functions of Standards • • • • • • • • • Encapsulation Segmentation and reassembly Connection control Ordered delivery Flow control Error control Addressing Multiplexing Transmission services Encapsulation • Addition of control information to data – Address information – Error-detecting code – Protocol control Segmentation (Fragmentation) • • • • Data blocks are of bounded size Application layer messages may be large Network packets may be smaller Splitting larger blocks into smaller ones is segmentation (or fragmentation in TCP/IP) – ATM blocks (cells) are 53 octets long – Ethernet blocks (frames) are up to 1526 octets long • Checkpoints and restart/recovery Why Fragment? • Advantages – – – – More efficient error control More equitable access to network facilities Shorter delays Smaller buffers needed • Disadvantages – Overheads – Increased interrupts at receiver – More processing time Connection Control • • • • • Connection Establishment Data transfer Connection termination May be connection interruption and recovery Sequence numbers used for – Ordered delivery – Flow control – Error control Connection Oriented Data Transfer Ordered Delivery • PDUs may traverse different paths through network • PDUs may arrive out of order • Sequentially number PDUs to allow for ordering Flow Control • • • • Done by receiving entity Limit amount or rate of data Stop and wait Credit systems – Sliding window • Needed at application as well as network layers Error Control • Guard against loss or damage • Error detection – – – – Sender inserts error detecting bits Receiver checks these bits If OK, acknowledge If error, discard packet • Retransmission – If no acknowledge in given time, re-transmit • Performed at various levels Addressing • • • • Addressing level Addressing scope Connection identifiers Addressing mode • Let’s look at two of these in more detail Addressing level • Level in architecture at which entity is named • Unique address for each end system (computer) and router • Network level address – IP or internet address (TCP/IP) – Network service access point or NSAP (OSI) • Process within the system – Port number (TCP/IP) – Service access point or SAP (OSI) Address Concepts Addressing Mode • Usually an address refers to a single system – Unicast address – Sent to one machine or person • May address all entities within a domain – Broadcast – Sent to all machines or users • May address a subset of the entities in a domain – Multicast – Sent to some machines or a group of users Multiplexing • Supporting multiple connections on one machine • Mapping of multiple connections at one level to a single connection at another – Carrying a number of connections on one fiber optic cable – Aggregating or bonding ISDN lines to gain bandwidth Transmission Services • Priority – e.g. control messages • Quality of service – Minimum acceptable throughput – Maximum acceptable delay • Security – Access restrictions Review Questions • • • • What are the layers of the TCP/IP model? What are the layers of the OSI model? What is meant by encapsulation? Trace an FTP command as it moves down through the layers, across the medium, and up the layers on the receiving side.