* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Lecture Notes - Computer Science & Engineering
Distributed firewall wikipedia , lookup
Wireless security wikipedia , lookup
Cross-site scripting wikipedia , lookup
Deep packet inspection wikipedia , lookup
Cyberwarfare wikipedia , lookup
Cyber-security regulation wikipedia , lookup
Security-focused operating system wikipedia , lookup
Medical privacy wikipedia , lookup
Mobile security wikipedia , lookup
Denial-of-service attack wikipedia , lookup
Information privacy law wikipedia , lookup
Information security wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
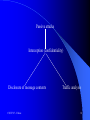
Cyberattack wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Computer security wikipedia , lookup
Social engineering (security) wikipedia , lookup
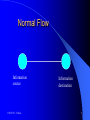
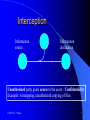
CSCE 727 Cyber Attacks and Risk Management Attack Sophistication vs. Intruder’s Technical Knowledge From: http://people.ubuntu.com/~duanedesign/SurvivabilityandInformationAssuranceCurriculum/01survive/01survive.html CSCE 727 - Farkas 2 Reading Required: Denning Chapter 8, 9, 14 Hutchins et al, Intelligence-Driven Computer Network Defense Informed by Analysis of Adversary Campaigns and Intrusion Kill Chains, White paper,http://www.lockheedmartin.com/content/dam/lockheed/data/corporate/d ocuments/LM-White-Paper-Intel-Driven-Defense.pdf Interesting Reading: DHS repairing internal security operations, Homeland Security News Wire, April 9, 2014, http://www.homelandsecuritynewswire.com/seworld20140409dhs-repairing-internal-security-operations Student develops new way to detect hackers, Homeland Security News Wire, April 9, 2014, http://www.homelandsecuritynewswire.com/dr20140409student-develops-new-way-to-detect-hackers Measuring smartphone malware infection rates, Homeland Security News Wire, April 9, 2014, http://www.homelandsecuritynewswire.com/dr20140409measuring-smartphone-malware-infection-rates CSCE 727 - Farkas 3 Attack Internet Engineering Task Force: RFC 2828: “ An assault on system security that derives from an intelligent threat, i.e., an intelligent act that is a deliberate attempt (especially in the sense of a method or technique) to evade security services and violate the security policy of the system.” CSCE 727 - Farkas 4 Normal Flow Information source CSCE 727 - Farkas Information destination 5 Interruption Information source Information destination Asset is destroyed of becomes unavailable - Availability Example: destruction of hardware, cutting communication line, disabling file management system, etc. CSCE 727 - Farkas 6 Interception Information source Information destination Unauthorized party gains access to the asset – Confidentiality Example: wiretapping, unauthorized copying of files CSCE 727 - Farkas 7 Modification Information source Information destination Unauthorized party tampers with the asset – Integrity Example: changing values of data, altering programs, modify content of a message, etc. CSCE 727 - Farkas 8 Fabrication Information source Information destination Unauthorized party insets counterfeit object into the system – Authenticity Example: insertion of offending messages, addition of records to a file, etc. CSCE 727 - Farkas 9 Phases of Attack Improve detection by examining which “phase” an intruder’s behavior is identified Attack phases: – Intelligence gathering: attacker observes the system to determine vulnerabilities – Planning: attacker decide what resource to attack (usually least defended component) – Attack: attacker carries out the plan – Inside the system: Hiding: attacker covers tracks of attack Future attacks: attacker installs backdoors for future entry points CSCE 727 - Farkas 10 Passive Attack “Attempts to learn or make use of information from the system but does not affect system resources” (RFC 2828) Sniffer CSCE 727 - Farkas 11 Sniffers All machines on a network can “hear” ongoing traffic A machine will respond only to data addressed specifically to it Network interface: “promiscuous mode” – able to capture all frames transmitted on the local area network segment CSCE 727 - Farkas 12 Risks of Sniffers Serious security threat Capture confidential information – Authentication information – Private data Capture network traffic information CSCE 727 - Farkas 13 Network Sniffing Tools Used for network analysis and troubleshooting SecTools.Org: Top 125 Network Security Tools, http://sectools.org/tag/sniffers/ Free, open source sniffers Multiplatform support (user needs superuser privilege, education: drop privilege) #1: Wireshark: GUI interface #9: tcpdump: command line CSCE 727 - Farkas 14 Wireshark Examines data from a live network or from a capture file on disk GUI interface for editing and visualization – Green: TCP traffic, dark blue: DNS traffic, light blue: UDP traffic, black: TCP packets with problems Has remotely exploitable security holes How to Use Wireshark to Capture, Filter and Inspect Packets, http://www.howtogeek.com/104278/how-touse-wireshark-to-capture-filter-and-inspect-packets/ CSCE 727 - Farkas 15 Passive attacks Interception (confidentiality) Disclosure of message contents CSCE 727 - Farkas Traffic analysis 16 Disclosure of message content Intruder is able to interpret and extract information being transmitted Highest risk:authentication information – Can be used to compromise additional system resources CSCE 727 - Farkas 17 Traffic Analysis Intruder is not able to interpret and extract the transmitted information Intruder is able to derive (infer) information from the traffic characteristics CSCE 727 - Farkas 18 Protection Against Passive Attacks Shield confidential data from sniffers: cryptography Disturb traffic pattern: – Traffic padding – Onion routing Detect and eliminate sniffers CSCE 727 - Farkas 19 Detection of Sniffer Tools Difficult to detect: passive programs Tools: – Promisc – Linux – cmp – SunOS 4.x: detects promiscuous mode – AntiSniff (L0pht Heavy Industries, Inc. ): remotely detects computers that are packet sniffing, regardless of the OS Interesting read: S. Truth, How to Test for Sniffing Vulnerabilities, http://web.securityinnovation.com/appsecweekly/blog/bid/63274/How-to-Test-for-SniffingVulnerabilities CSCE 727 - Farkas 20 Tor Online anonymity Free software and an open network Platforms: Windows, Mac, Linux/Unix, and Android Defend against traffic analysis Download site: https://www.torproject.org/ CSCE 727 - Farkas 21 Tor Tor network: a group of volunteer-operated servers Privacy: user connections through a series of virtual tunnels using the Tor network Censorship circumvention tool: allowing users to reach otherwise blocked destinations or content CSCE 727 - Farkas 22 How Tor works? Source: https://www.torproject.org/about/overview. html.en Cryptographically hide connection between communicating partners CSCE 727 - Farkas 23 Source: The Tor Project, https://www.torproject.org/ CSCE 727 - Farkas 24 Source: The Tor Project, https://www.torproject.org/ CSCE 727 - Farkas 25 Source: The Tor Project, https://www.torproject.org/ CSCE 727 - Farkas 26 Risk of Tor? False sense of privacy Legal risk of Tor relay operators? Bad guys use Tor, too! Interesting reading: – EFF: 7 Things You Should Know About Tor, 2014, https://www.eff.org/deeplinks/2014/07/7-things-you-shouldknow-about-tor – B. Schneier: Has Tor Been Compromised?, 2013, https://www.schneier.com/blog/archives/2013/08/has_tor_be en_co.html CSCE 727 - Farkas 27 Active attacks “Attempts to alter system resources of affect their operation” (Internet Enginering Task Force, RFC 2828) CSCE 727 - Farkas 28 Active attacks Interruption DOS, DDOS (availability) Modification (integrity) Replay (Authentication) Masquarade (Authentication) CSCE 727 - Farkas Fabrication (integrity) 29 Protection against DoS, DDoS Hard to provide full protection Some of the attacks can be prevented – Filter out incoming traffic with local IP address as source – Avoid established state until confirmation of client’s identity Internet trace back: determine the source of an attack CSCE 727 - Farkas 30 Degradation of Service Do not completely block service just reduce the quality of service CSCE 727 - Farkas 31 Intrusion Control It is better to prevent something than to plan for loss. Problem: Misuse happens! CSCE 727 - Farkas 32 Need: Intrusion Prevention: protect system resources Intrusion Detection: (second line of defense) identify misuse Intrusion Recovery: cost effective recovery models CSCE 727 - Farkas 33 Intrusion Prevention First line of defense Techniques: cryptography, identification, authentication, authorization, access control, security filters, etc. Not good enough (prevention, reconstructions) CSCE 727 - Farkas 34 Intrusion Detection System (IDS) Looks for specific patterns (attack signatures or abnormal usage) that indicate malicious or suspicious intent Second line of defense against both internal and external threats See recommended reading! CSCE 727 - Farkas 35 Intrusion Detection Systems Deter intruders Catch intruders Prevent threats to fully occur (real-time IDS) Improve prevention techniques IDS deployment, customisation and management is generally not trivial See required reading! CSCE 727 - Farkas 36 Audit-Based Intrusion Detection Profiles, Rules, etc. Audit Data Intrusion Detection System Decision CSCE 727 - Farkas Need: • Audit data • Ability to characterize behavior 37 Audit Data Format, granularity and completeness depend on the collecting tool Examples – – – – System tools collect data (login, mail) Additional collection of low system level “Sniffers” as network probes Application auditing Honey Net Needed for – Establishing guilt of attackers – Detecting suspicious user activities CSCE 727 - Farkas 38 Audit Data Accuracy Collection method – System architecture and collection point – Software and hardware used for collection Storage method – Protection of audit data Sharing – Transmission protection and correctness – Availability CSCE 727 - Farkas 39 IDS Categories 1. 2. 3. 4. 5. Time of data analysis Real-time v.s. off-the-line IDS Location where audit data was gathered Host-based v.s. network-based v.s. hybrid Technique used for analysis Rule-based v.s. statistic-based Location of analysis Centralized, distributed, network-based Pattern IDS looking for Misuse v.s. anomaly-based v.s. hybrid CSCE 727 - Farkas 40 Intrusion Recovery Actions to avoid further loss from intrusion Terminate intrusion and protect against reoccurrence Law enforcement Enhance defensive security Reconstructive methods based on: – Time period of intrusion – Changes made by legitimate users during the effected period – Regular backups, audit trail based detection of effected components, semantic based recovery, minimal rollback for recovery. CSCE 727 - Farkas 41 What is “Survivability”? To decide whether a computer system is “survivable”, you must first decide what “survivable” means. CSCE 727 - Farkas 42 Risk Assessment Threats RISK Vulnerabilities Consequences 43 Real Cost of Cyber Attack Damage of the target may not reflect the real amount of damage Services may rely on the attacked service, causing a cascading and escalating damage Need: support for decision makers to – Evaluate risk and consequences of cyber attacks – Support methods to prevent, deter, and mitigate consequences of attacks 44 Risk Management Framework (Business Context) Understand Business Context Identify Business and Technical Risks Carry Out Fixes and Validate Synthesize and Rank Risks Define Risk Mitigation Strategy Measurement and Reporting 45 Understand the Business Context “Who cares?” Identify business goals, priorities and circumstances, e.g., – – – – Increasing revenue Meeting service-level agreements Reducing development cost Generating high return investment Identify software risk to consider 46 Identify Business and Technical Risks “Why should business care?” Business risk – Direct threat – Indirect threat Consequences – – – – Financial loss Loss of reputation Violation of customer or regulatory constraints Liability Tying technical risks to the business context in a meaningful way 47 Synthesize and Rank the Risks “What should be done first?” Prioritization of identified risks based on business goals Allocating resources Risk metrics: – – – – Risk likelihood Risk impact Risk severity Number of emerging risks 48 Define the Risk Mitigation Strategy “How to mitigate risks?” Available technology and resources Constrained by the business context: what can the organization afford, integrate, and understand Need validation techniques 49 Carry Out Fixes and Validate Perform actions defined in the previous stage Measure “completeness” against the risk mitigation strategy – Progress against risk – Remaining risks – Assurance of mechanisms Testing 50 Measuring and Reporting Continuous and consistent identification and storage of risk information over time Maintain risk information at all stages of risk management Establish measurements, e.g., – Number of risks, severity of risks, cost of mitigation, etc. 51 Assets-Threat Model (1) Threats compromise assets Threats have a probability of occurrence and severity of effect Assets have values Assets are vulnerable to threats Threats Assets 52 Assets-Threat Model (2) Risk: expected loss from the threat against an asset R=V*P*S R risk V value of asset P probability of occurrence of threat V vulnerability of the asset to the threat 53 Risk Acceptance Certification How well the system meet the security requirements (technical) Accreditation Management’s approval of automated system (administrative) 54 Next Class: Privacy CSCE 727 - Farkas 55