* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Types of Encryption Algorithms
Survey
Document related concepts
Next-Generation Secure Computing Base wikipedia , lookup
Cross-site scripting wikipedia , lookup
Post-quantum cryptography wikipedia , lookup
Airport security wikipedia , lookup
Information security wikipedia , lookup
Security and safety features new to Windows Vista wikipedia , lookup
Cyber-security regulation wikipedia , lookup
Deep packet inspection wikipedia , lookup
Unix security wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Wireless security wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Security-focused operating system wikipedia , lookup
Computer security wikipedia , lookup
Mobile security wikipedia , lookup
Transcript
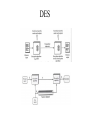
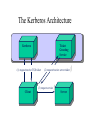
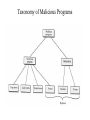
SECURITY ISSUES IN NETWORKS WITH INTERNET ACCESS PRESENTED BY Sri Vallabh Aida Janciragic Sashidhar Reddy Topics of Discussion • Principles for secure networking • Internet Vulnerabilities • Security building blocks Internet Security • Why do we need to study security in the internet? Here are some reasons … – Computer networks have lots of vulnerabilities and threats – A hacker can log into my machine remotely and destroy the information – A malicious program can wipe out data on hundreds of computers causing huge losses Principles for Secure Networking • Questions to consider – What are we trying to protect? – What operations are authorized? – What is security parameter? Principles continued… • Know the configuration of the network hardware and software • Know the vulnerabilities of the configuration • Know the threats and consider it in relation to the vulnerabilities to asses the risk • Authenticate and authorize the accessto network resources Principles Continued.. • Maintain audit logs • Have a plan to detect and respond to security incidents • Ensure individual accountability The Networks of TwoHands Corporation • TwoHands corporation develops, produces, and markets specialized gloves used in waste disposal and other safety related applications • The corporation has a Headquarters,a Research Lab,several factories and warehouses in different parts of the country Continued… • Let us discuss the five stages of development in TwoHands Networks and consider in each stage the problems associated with the network and the possible remedies Stage1:Private Networks Only Security Problems 1. Any user can access network traffic 2. Diskette drives on the client workstations 3. PCs with modem connections 4. Insufficient training to authorized users Continued… Possible Countermeasures 1. Introduction of an authentication system for each user 2. Installation of virus detection software and configuration monitors 3. Installation of temper resistant hardware 4. Security awareness training for authorized users Stage 2:Private Networks plus Read-only Web Server Security Problems 1. All the problems in stage 1 2. Denial of service attack 3. Unauthorized change to data on web server 4. Web address spoofing Continued… Possible Countermeasures 1. Use a reliable web server package 2. Keep abreast of the advisories provided by CERT(Computer Emergency Response Team), FIRST(Forum of Incident Response Teams) 3. Proper maintenance of web server Stage 3:Private Nets Plus Forms-Based WWW Server Security Problems 1. Compromise of order information 2. Spoofing of order information 3. Loss of control over the web site 4. Customer information stored on ISP host. Continued… Possible Countermeasures 1. Using a secure web server like HTTP 2. Double checking the CGI scripts 3. Customer authentication Stage 4:Internet Service through Firewall with Forms-Based WWW Server Security Problems 1. Attacks on internal systems via misconfigured firewalls 2. Importing of malicious software or exporting of sensitive information via properly configured firewall 3. Compromise of identity of correspondents 4. Back doors into internal networks Continued… Possible Countermeasures 1. Proper firewall configuration 2. Vigilant management of firewall and the website 3. Provide proper awareness of security to the internal users Stage 5:Virtual Private Networks Security Problems 1. Contamination of internal database via actions of cooperating companies 2. Service delays/denial for intranet traffic due to Internet/ISP problems 3. Compromise or delay of intranet traffic due to crypto mismanagement 4. Compromise of internal traffic patterns Continued… Possible Countermeasures 1. Using proper encryption methodology 2. Avoid same company as ISP all the sites Network Security Policy and Services • For any level of network security to be established and maintained we need to understand: • • • what assets we need to protect against what threats to what degree • identify the elements of security policies appropriate for networks construct a security policy to meet the needs of network decide on means for enforcing the policy • • Network security services • confidentiality (protection against eavesdropping) • integrity (protection against data modification) • authentication (assurance that the source of the data is accurately identified to the recipient) • non-repudiation (inability of the sender to disavow data the recipient receives) Vulnerabilities • Network • Sniffing • War Dialing • Protocol • • • • Data-link-layer security Network-layer security Transport-layer security IP origin forgery Above the application layer • System access control and authorization data structures • Malicious Software • Hidden Application Features Types of Encryption Algorithms Symmetric DES ( Digital Encryption Standard) Asymmetric RSA ( Public Key Cryptography) (Rivest Shamir Adleman) DES RSA Authentication Cryptographic Hash Functions MAC (Message Authentication Code) Digital Signatures Security in TCP/IP Protocol Stack Application Layer Encryption Session Encryption IP Layer Encryption Relative Location of Security in TCP/IP Protocol Stack SSL Protocol Operation IP Security Scenario The Kerberos Architecture Ticket Granting Service Kerberos (1) request/receive TGS ticket Client (2) request/receive server ticket (3) request service Server Intrusion Detection Network Based Network Security Monitor, Network IDS, Net Ranger, Tripwire etc… Host Based Probes of host ports, password guessing etc… Taxonomy of Malicious Programs Security Management Tools SATAN (Security Analysis Tool for Auditing Networks) ISS (Internet Security Scanner) Tiger Crack Snoop Firewall • Firewall : a method used to prevent unauthorized access to a private network Internet Trust Types of Firewalls SOCKS Firewall Protected Network Socksified user app asks SOCKS daemon for circuit Internet SOCKS daemon on firewall parses request, checks access control rules, and makes connection (proxy); copy data back in through firewall. Target of communication sends information back through SOCKS daemon, which routes it to the user desktop.