* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Network layer
Distributed firewall wikipedia , lookup
IEEE 802.1aq wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
TCP congestion control wikipedia , lookup
Network tap wikipedia , lookup
Computer network wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Deep packet inspection wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Airborne Networking wikipedia , lookup
Quality of service wikipedia , lookup
Routing in delay-tolerant networking wikipedia , lookup
Internet protocol suite wikipedia , lookup
UniPro protocol stack wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
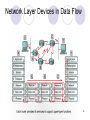
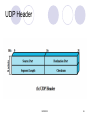
NETE0510 Network and Protocol Architecture Supakorn Kungpisdan NETE0510 1 Outline Requirements Network Architecture Performance NETE0510 2 Links, Nodes, and Clouds NETE0510 3 Switched Network NETE0510 4 Switched Network (cont’d) Circuit-switched network: telephone system Establish a dedicated circuit across a sequence of links Packet-switched network: data network Store-and-forward Packet or message Efficiency of circuit-switched VS packet-switched networks Cloud: any type of network e.g. point-to-point, multiple access, switched NETE0510 5 Internetwork A set of independence networks are interconnected to form an internetwork NETE0510 6 Internetwork (cont’d) Internet VS internet Router or gateway: a node connecting to two or more networks Address: a byte string that identifies a node; used to distinguish a node from others Routing A process of determining systematically how to forward messages toward the destination node based on its address NETE0510 7 Unicast, Multicast, Broadcast Unicast: a source node sends a message to a single destination node Broadcast: a source node sends a message to all the nodes on the network Multicast: a source node sends a message to some subset of nodes Network: two or more nodes connected by a physical link, or Two or more networks connected by a node A large message is divided into packets Why? NETE0510 8 Cost-effective Resource Sharing Efficiency How do all the hosts that want to communicate at the same time share the network? Multiplexing : a system resource is shared among multiple users Analogous to time sharing computer: CPU is shared among multiple job Multiplexing Techniques Synchronous Time-Division Multiplexing (STDM) Frequency-Division Multiplexing (FDM) Same concept as TV transmission Statistical Multiplexing Share physical link only when more than one node transmit data at the same time Transmit data on demand rater than during a predetermined time slot NETE0510 9 Multiplexing NETE0510 10 Switch Multiplexing Packets NETE0510 11 Switch Multiplexing Packets (cont’d) Switch makes decision on a packet-by-packet basis FIFO Round robin STDM Quality of Service (QoS) Congestion Switch receives packets faster than the share link can accommodate need a buffer Running out of buffer packet loss NETE0510 12 Additional Benefits of Statistical Multiplexing Cost effective for multiple users to share network resources Define the packet as the granularity with which the links of the network are allocated to different flows Decide the flow with per packet basis Fairly allocating capacity to different flows Dealing with congestion when it occurs NETE0510 13 Support for Common Services Network supports application-level processes to communicate with each other Viewed as logical “channel” NETE0510 14 Support for Common Services (cont’d) What functionality the channels should provide to application programs? Delivery guarantee? In-order delivery? Secure from eavesdropping? Etc. NETE0510 15 Identifying Common Communication Patterns Two general types of channels Request/reply channel Used in file transfer and digital library apps Need security/privacy protection Message stream channel Used in video-on-demand and videoconferencing apps No 100% delivery guarantee, but in-order Unicast/multicast/broadcast NETE0510 16 Reliability 3 classes of failures Bit errors or burst errors Occurred from outside forces e.g. lightning strikes, power surges, and microwave ovens Rare 1/106-107 bits on copper-based cable and 1/1012-1014 bits on optical fiber Packet errors Packet loss because there are bit errors Congestion Software error e.g. forward packet to the wrong link Node and link errors Physical link is cut, computer crashes by software, power failure Need time to fix Need to understand application’s requirements and recognize limitations of underlying technology Semantic gap: the gap between that application expects and what the underlying technology can provide NETE0510 17 Outline Requirements Network Architecture Performance NETE0510 18 Network Architecture A network must provide general, cost-effective, fair, and robust connectivity among a large number of computers Network architecture: a general blueprint that guide design and implementation of networks OSI and Internet (TCP/IP) architecture NETE0510 19 Layering and Protocols When the system gets complex, abstraction is needed Abstraction leads to layering Start by services offered by the underlying hardware and then add a sequence of layers of services The services provided at the higher layers are implemented in terms of the ones provided by the low layers NETE0510 20 Layering NETE0510 21 Protocols Protocols: abstract objectives that make up the layers of a network system Protocol provides a communication service that higherlevel objects use to exchange messages Each protocol defines two different interfaces: Service interface to other objects on the same computer Peer interface to another computer Indirect communications: protocol in each layer passes a message to lower layer-protocol which in turn deliver the message to its peer Multiple protocols provide a different communication service Protocol graph: a suite of protocol that make up a network system NETE0510 22 Protocols (cont’d) NETE0510 23 Example of Protocol Graph Request/Reply Message Stream NETE0510 24 Encapsulation NETE0510 25 OSI Architecture NETE0510 26 OSI Architecture (cont’d) Physical layer: handle the transmission of raw bits over a communications link Data-link layer: collect a stream of bits into a large aggregate called a frame Network layer: handle routing among nodes within a packetswitched network. Transport layer: implement a process-to-process channel Session layer: provide a name space used to tie together the potential different transport streams Presentation layer: concern with the format of data exchanged between peers Application layer: include network applications NETE0510 27 OSI Model Analogy Create document (paper + pen, pencil, etc, used for separate rooms) Translate, arrange format (dictionary, translator) Doorman, enter and leave the room Check document condition and bring document to each room (port number) living room (80), dining room (21), art studio (23) Postal address (IP address) front door , post office How to deliver document trucks, ships, planes (ID card = MAC address)) Street, ocean, air NETE0510 28 Ethernet and the OSI Model NETE0510 29 Network Layer Devices in Data Flow NETE0510 30 Internet (TCP/IP) Architecture NETE0510 31 TCP/IP Layers no official model but a working one Application layer Host-to-host, or transport layer Internet layer Network access layer Physical layer NETE0510 32 Physical Layer concerned with physical interface between computer and network concerned with issues like: characteristics of transmission medium signal levels data rates other related matters NETE0510 33 Network Access Layer exchange of data between an end system and attached network concerned with issues like : destination address provision invoking specific services like priority access to & routing data across a network link between two attached systems NETE0510 34 Internet Layer (IP) routing functions across multiple networks for systems attached to different networks using IP protocol implemented in end systems and routers routers connect two networks and relays data between them NETE0510 35 Transport Layer (TCP) common layer shared by all applications provides reliable delivery of data in same order as sent commonly uses TCP NETE0510 36 Application Layer provide support for user applications need a separate module for each type of application NETE0510 37 OSI v TCP/IP NETE0510 38 Operation of TCP and IP NETE0510 39 Addressing Requirements two levels of addressing required each host on a subnet needs a unique global network address its IP address each application on a (multi-tasking) host needs a unique address within the host known as a port NETE0510 40 Operation of TCP/IP NETE0510 41 Transmission Control Protocol (TCP) usual transport layer is (TCP) provides a reliable connection for transfer of data between applications a TCP segment is the basic protocol unit TCP tracks segments between entities for duration of each connection NETE0510 42 TCP Header NETE0510 43 User Datagram Protocol (UDP) an alternative to TCP no guaranteed delivery no preservation of sequence no protection against duplication minimum overhead adds port addressing to IP NETE0510 44 UDP Header NETE0510 45 IP Header NETE0510 46 IPv6 Header NETE0510 47 TCP/IP Applications have a number of standard TCP/IP applications such as Simple Mail Transfer Protocol (SMTP) File Transfer Protocol (FTP) Telnet NETE0510 48 Some TCP/IP Protocols NETE0510 49 Features of Internet Architecture Does not imply strict layering Free to bypass the defined transport layers and directly use IP or one of the underlying networks Hourglass shape IP serves as the focal point of the architecture – common method for exchanging packets among a wide collection of networks (According to IETF) If someone propose a new protocol to be included in the architecture, they must produce both a protocol specification and representative implementation of the specification Ensure that the protocols can be efficiently implemented NETE0510 50 Outline Requirements Network Architecture Performance NETE0510 51 Bandwidth Bandwidth: the number of bits that can be transmitted over the network in a certain period of time Bandwidth of a single physical link Bandwidth of a logical process-to-process channel At the physical level, transmitting 1 bit of data on a 1Mbps link takes 1 µs For logical process-to-process channels, bandwidth is also influenced by other factors NETE0510 52 Latency Latency: time taken a message to travel from one end of a network to the other E.g. transcontinental network has a latency of 24 ms. Round-trip Time (RTT): time taken to send a message from one end of a network to the other and back Components of latency: Speed-of-light propagation delay: 3 x 108 m/s in a vacuum, 2.3 x 108 m/s in a cable, 2 x 108 m/s in a fiber Transmission delay: time taken to transmit a unit of data Queuing delay NETE0510 53 Latency (cont’d) TotalLatency = Propagation + Transmit + Queue Propagation = Distance/SpeedOfLight Transmit = Size/Bandwidth NETE0510 54 Delay X Bandwidth Product A channel where latency is the length of the pipe and the bandwidth is diameter of the pipe Then the product gives the volume of the pipe the number of bits it holds E.g. a transcontinental channel with a one-way latency of 50 ms and a bandwidth of 45 Mbps is able to hold 50 x 103 s x 45 x 106 bps = 2.25 x 106 bits or approx 280 KB Important when constructing high performance networks because it tells how many bits the sender must transmit before the first bit arrives at the receiver. NETE0510 55 Delay X Bandwidth Product (cont’d) The sender sends 2 delay X bandwidth of data before hearing from the receiver The bits are said to be “in flight” If the receiver tells the sender to stop transmitting, it will takes up to a delay X bandwidth before the sender can respond. Takes 5.5 x 106 bits (671 KB) of data NETE0510 56 Questions? Next Lecture Introduction to Transmission Technologies NETE0510 57