* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Security - NYU Stern School of Business
Survey
Document related concepts
Next-Generation Secure Computing Base wikipedia , lookup
Wireless security wikipedia , lookup
Security-focused operating system wikipedia , lookup
Password strength wikipedia , lookup
Computer security wikipedia , lookup
Antivirus software wikipedia , lookup
Access control wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Trusted Computing wikipedia , lookup
Computer virus wikipedia , lookup
Mobile security wikipedia , lookup
Transcript
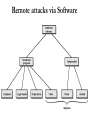
Security Requirements • Confidentiality – Requires information in a computer system only be accessible for reading by authorized parties • Integrity – Assets can be modified by authorized parties only • Availability – Assets be available to authorized parties • Authenticity – Requires that a computer system be able to verify the identity of a user Threats • Confidentiality • Interception – Unauthorized access – wiretapping • Integrity • Modification – Change or Delete: Data, Messages, Programs • Availability • Interruption – Hardware destruction – Disable File Management • Authenticity • Fabrication – Create data, messages ... What it there to protect? • Hardware – Accidental and deliberate damage – Tapping of Network lines – Overload of networks • Software – Threats include deletion, alteration, damage • Data – Involves files – Security concerns for availability, secrecy, and integrity – Stealing of classified information Protection • • • • • • Limit Sharing Limit Communication Encryption of data Control access Electronic Signatures Intrusion detection Examples of Protection • File systems – Access control defined by user – Most system files are not accessible for user • Access control – OS provides access control via Login and Password • User privileges – different user have different status (NT user groups) • Clean Memory Partitioning • Systematic backups Sharing • Sharing is the source of all evil! • No sharing: Separation in time or place • Share all or share nothing – Owner of an object declares it public or private • Share via access limitation – Operating system checks the permissibility of each access by a specific user/process to a specific object – Operating system acts as the guard Memory issues • Bound registers for processes access to RAM • Delete vs. erase – If you delete a file it is not really gone – OS only “forgot” that it was there – You can still retrieve the content • If you really want to erase thing: – Reformat the device(not always possible) – Delete files and save useless things until drive is full – Beware when your sell you used computer, there may be traces of sensitive information Message encryption: Artistic Math • Encode content x y=F(x,k1) and send y • Receiver decodes the content with a function x=D(x,k2) • Public key & private: 2 different keys are used (PGP) • Secrete Key: k1=k2, D=F-1 ! Illusion of safety • You can only read content if you know k2 • Simple letter replacement (Midterm) – has about 4*10^26 possibilities but easy to guess Electronic Signatures • Became very important recently due to ecommerce • Example: You sent and email to buy a stock • stock crashes 1 hour later, you deny ever having sent the email • Legal issue: How to prove the authenticity of electronic documents • Similar to encryption: You calculate a complex function from the message text, decode it using your private and append it Access Control Authentication • Login – Requires both a user identifier (ID) and a password – Only admit known and matching ID and password • User based or computer based • Problems: – Users can reveal their password to others either intentionally or accidentally – Hackers are skillful at guessing passwords – ID/password file can be obtained (hard to decode) ID Provides Security • Determines whether the user is authorized to gain access to a system • Determines the privileges accorded to the user – Guest or anonymous accounts have mover limited privileges than others • ID is used for discretionary access control – A user may grant permission to files to others by ID Intrusion Techniques • Steal Id and Password • Circumvent access control – Use a Trojan horse to bypass restrictions on access Techniques for Learning Passwords • Try default password used with standard accounts shipped with computer • Exhaustively try all short passwords license plates • Try words in dictionary or a list of likely passwords • Collect information about users and use these items as passwords – address, names, relatives, SSN, phone numbers • In a study 86% of password could be guessed Techniques for Stealing Passwords • Tap the line between a remote user and the host system • Watch user during login • Intercept emails that contain passwords Password Selection Strategies • Computer generated passwords :-( – Hard to remember, user write them down • Reactive password checking strategy :-( – System periodically runs password cracker to find guessable passwords – System cancels passwords that are guessed and notifies user – Consumes resources to do this, can be to late! • Proactive password checker :-) – The system checks at the time of selection if the password is allowable Types of Attacks • Intrusion – Somebody unauthorized manages to log into your system • Remote Attack – Somebody changes the behavior of your computer without being logged in Intrusion Prevention • Firewalls around network • Limit the access type: – telnet, ftp, http, ssh, rsh …. • Limit access location – allow access only from designated machines – Machine ID: IP address Intrusion Detection • Assume the behavior of the intruder differs from the legitimate user • Statistical anomaly detection – Collect data related to the behavior of legitimate users over a period of time – Statistical tests are used to determine if the behavior is not legitimate behavior • Rule-based detection – Rules are developed to detect deviation form previous usage pattern – Expert system searches for suspicious behavior Intrusion Detection Data Collection • Audit record – Native audit records • All operating systems include accounting software that collects information on user activity – Detection-specific audit records • Collection facility can be implemented that generates audit records containing only that information required by the intrusion detection system • Very common for Web services – I can tell exactly what you did on blackboard Remote attacks via Software 2 Types of Malicious Programs • Those that need a host program – Fragments of programs that cannot exist independently of some application program, utility, or system program • Independent – Self-contained programs that can be scheduled and run by the operating system Trojan Horse • Useful program that contains hidden code that when invoked performs some unwanted or harmful function • Can be used to accomplish functions indirectly that an unauthorized user could not accomplish directly – User may set file permission so everyone has access – can do anything the user could do • Example: new exciting freeware game • Does not need illegal access Login Spoofing • Setup a screen that looks exactly like login • New user comes and tries to login • Program reads in login information and mails is to intruder • Login fails, user thinks he misspelled and logs in again Logic Bomb • Code embedded in a legitimate program that is set to “explode” when certain conditions are met – Presence or absence of certain files – Particular day of the week – Particular user running application • Example: An employee had a program that checked whether his name appeared on payroll – After he was fired the bomb went off and destroyed important software – Potential of blackmail Worms • Use network connections to spread form system to system • Electronic mail facility – A worm mails a copy of itself to other systems • Remote execution capability – A worm executes a copy of itself on another system • Remote log-in capability – A worm logs on to a remote system as a user and then uses commands to copy itself from one system to the other Zombie • Program that secretly takes over another Internetattached computer • It uses that computer to launch attacks that are difficult to trace to the zombie’s creator • Typical Windows NT problem: Recent case that attacked the White House server Viruses • Program that can “infect” other programs by modifying them – Modification includes copy of virus program – The infected program can infect other programs Virus Stages • Dormant phase – Virus is idle • Propagation phase – Virus places an identical copy of itself into other programs or into certain system areas on the disk Virus Stages • Triggering phase – Virus is activated to perform the function for which it was intended – Caused by a variety of system events • Execution phase – Function is performed Types of Viruses • Parasitic – Attaches itself to executable files and replicates – When the infected program is executed, it looks for other executables to infect • Memory-resident – Lodges in main memory as part of a resident system program – Once in memory, it infects every program that executes Types of Viruses • Boot sector – Infects boot record – Spreads when system is booted from the disk containing the virus • Stealth – Designed to hide itself form detection by antivirus software – May use compression Types of Viruses • Polymorphic – Mutates with every infection, making detection by the “signature” of the virus impossible – Mutation engine creates a random encryption key to encrypt the remainder of the virus • The key is stored with the virus Macro Viruses • A macro is an executable program embedded in a word processing document or other type of file • Autoexecuting macros in Word – Autoexecute • Executes when Word is started – Automacro • Executes when defined event occurs such as opening or closing a document – Command macro • Executed when user invokes a command (e.g., File Save) • Dominantly Windows problem E-mail Virus: Windows Issue • Activated when recipient opens the e-mail attachment • Activated by open an e-mail that contains the virus • Uses Visual Basic scripting language • Propagates itself to all of the e-mail addresses known to the infected host • Protection: Use email program that has very limited privileges (Beware Outlook and Explorer) Antivirus Approaches • • • • Detection Identification Removal Your antivirus program from yesterday is useless for today’s virus! • Stern approach: Every time the user logs in to his machine the computer downloads the most current version of antivirus software from the network How does Antivirus software work? • Virus signature scanner – Scan target code looking for known viruses • CPU emulator – Instructions in an executable file are interpreted by the emulator rather than the processor Internet Attacks • One way to attack internet services is to create an overload for the server • Most server have a capacity that reflects normal use requirements • Tojan horse or worms get distributed onto many machines • At a specific time all infected machines start sending requests to the same server • Server goes down • Big problem for online brokerage with time sensitive information Comparison UNIX to WINDOWS • UNIX: targeted by access attacks since it is a – – – – Multi-user environment High degree of sharing Constant network access Sophisticated OS: hard to write malicious programs • WINDOWS: targeted by remote attacks – Singly user environment – Less sophisticated OS: easier to write malicious programs – Switched off most of the time (used to be) Security Design Principles • Public system design – It creates a false illusion if you think nobody knows you architecture • Default: no access • Repetitive checks for current authority – User might have forgotten to lock out, timeout • Give the least privileges possible • Security should be build in the lowest levels of the system, security as add-on does not work well Summary • There is no safe system! • Business decision – How do I enforce save behavior from employees – Security is very expensive – Security get more expensive, the more flexibility , communication and sharing I allow – Separate physical network for sensitive data – Hire an ex-hacker to break into my system to test security