* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Chapter 4 : TCP/IP and OSI
Survey
Document related concepts
Wake-on-LAN wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Network tap wikipedia , lookup
Zero-configuration networking wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Computer network wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Deep packet inspection wikipedia , lookup
Airborne Networking wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
TCP congestion control wikipedia , lookup
Routing in delay-tolerant networking wikipedia , lookup
UniPro protocol stack wikipedia , lookup
Internet protocol suite wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Transcript
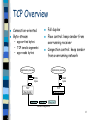
TCP/IP Network and OSI Model 1 What is a Protocol? Allows entities (i.e. application programs) from different systems to communicate Shared conventions for communicating information are called protocols Includes syntax, semantics, and timing 2 Why Use Protocol Architecture? Data communications requires complex procedures – Sender identifies data path/receiver – Systems negotiate preparedness – Applications negotiate preparedness – Translation of file formats For all tasks to occur, high level of cooperation is required 3 Three-Layer Model Distributed data communications involves three primary components: – Networks – Computers – Applications Three corresponding layers – Network access layer – Transport layer – Application layer 4 Protocol “Layers” Networks are complex! many “pieces”: – hosts – routers – links of various media – applications – protocols – hardware, software Question: Is there any hope of organizing structure of network? Or at least our discussion of networks?0 5 Organization of air travel ticket (purchase) ticket (complain) baggage (check) baggage (claim) gates (load) gates (unload) runway takeoff runway landing airplane routing airplane routing airplane routing a series of steps 6 Organization of air travel: a different view ticket (purchase) ticket (complain) baggage (check) baggage (claim) gates (load) gates (unload) runway takeoff runway landing airplane routing airplane routing airplane routing Layers: each layer implements a service – via its own internal-layer actions – relying on services provided by layer below 7 Layered air travel: services Counter-to-counter delivery of person+bags baggage-claim-to-baggage-claim delivery people transfer: loading gate to arrival gate runway-to-runway delivery of plane airplane routing from source to destination 8 ticket (purchase) ticket (complain) baggage (check) baggage (claim) gates (load) gates (unload) runway takeoff runway landing airplane routing airplane routing arriving airport Departing airport Distributed implementation of layer functionality intermediate air traffic sites airplane routing airplane routing airplane routing 9 Why layering? Dealing with complex systems: explicit structure allows identification, relationship of complex system’s pieces – layered reference model for discussion modularization eases maintenance, updating of system – change of implementation of layer’s service transparent to rest of system – e.g., change in gate procedure doesn’t affect rest of system 10 layering considered harmful? Internet protocol stack application: supporting network applications – ftp, smtp, http transport: host-host data transfer – tcp, udp network: routing of datagrams from source to destination – ip, routing protocols link: data transfer between neighboring network elements application transport network link physical – ppp, ethernet physical: bits “on the wire” 11 TCP/IP Transmission Control Protocol/Internet Protocol Developed by DARPA No official protocol standard Can identify five layers Application Host-to-Host (transport) Internet Network Access Physical 12 TCP Overview Full duplex – app writes bytes – TCP sends segments – app reads bytes Flow control: keep sender from overrunning receiver Congestion control: keep sender from overrunning network Application process Application process Write bytes … Connection-oriented Byte-stream … TCP Send buffer Segment Read bytes TCP Receive buffer Segment … Segment Transmit segments 13 TCP: Overview point-to-point: RFCs: 793, 1122, 1323, 2018, 2581 – one sender, one receiver – bi-directional data flow in same connection – MSS: maximum segment size reliable, in-order byte steam: – no “message boundaries” pipelined: send & receive buffers socket door application writes data application reads data TCP send buffer TCP receive buffer segment connection-oriented: – handshaking (exchange of control msgs) init’s sender, receiver state before data exchange – TCP congestion and flow control set window size full duplex data: socket door flow controlled: – sender will not overwhelm receiver 14 TCP segment structure 32 bits URG: urgent data (generally not used) ACK: ACK # valid PSH: push data now (generally not used) RST, SYN, FIN: connection estab (setup, teardown commands) Internet checksum (as in UDP) source port # dest port # sequence number acknowledgement number head not UA P R S F len used checksum rcvr window size ptr urgent data Options (variable length) counting by bytes of data (not segments!) # bytes rcvr willing to accept application data (variable length) 15 TCP Segment (TCP PDU) Source port (16 bits) Destination port (16 bits) Sequence number (32 bits) Acknowledgment number (32 bits) Window (16 bits) Checksum (16 bits) Urgent Pointer (16 bits) Options (variable) Data Offset (4 bits) Reserved (6 bits) Flags (6 bits) : URG, ACK, PSH, RST, SYN, FIN 16 TCP/IP Physical Layer Physical interface between a DTE (e.g. computer or terminal) and a transmission medium Specifies: – Characteristics of medium – Nature of signals – Data rate 17 TCP/IP Network Access Exchange of data between end system and network Address of host and destination Prioritization of transmission Software at this layer depends on network (e.g. X.25 vs. Ethernet) Segregation means that no other software needs to be concerned about net specifics 18 Network Access Layer Concerned with exchange of data between computer and network Includes addressing, routing, prioritizing, etc Different networks require different software at this layer Example: X.25 standard for network access procedures on packet-switching networks 19 TCP/IP Internet Layer An Internet is an interconnection of two or more networks Internet layer handles tasks similar to network access layer, but between networks rather than between nodes on a network Uses IP for addressing and routing across networks Implemented in workstations and routers 20 TCP/IP Transport Layer Also called host-to-host layer Reliable exchange of data between applications Uses TCP protocols for transmission 21 Transport Layer Concerned with reliable transfer of information between applications Independent of the nature of the application Includes aspects like flow control and error checking 22 TCP/IP Application Layer Logic needed to support variety of applications Each type of application (file transfer, remote access) requires different software on this layer 23 TCP/IP Applications SMTP (Simple Mail Transfer Protocol) – Basic e-mail facility, transferring messages among hosts FTP (File Transfer Protocol) – Sends files from one system to another on user command Telnet – Remote login capability, allowing a user to emulate a terminal on the remote system 24 TCP & UDP Most TCP/IP applications use TCP for transport layer TCP provides a connection (logical association) between two entities to regulate flow check errors UDP (User Datagram Protocol) does not maintain a connection, and therefore does not guarantee delivery, preserve sequences, or protect against duplication 25 UDP: User Datagram Protocol [RFC 768] “no frills,” “bare bones” Internet transport protocol “best effort” service, UDP segments may be: – lost – delivered out of order to app connectionless: – no handshaking between UDP sender, receiver – each UDP segment handled independently of others Why is there a UDP? no connection establishment (which can add delay) simple: no connection state at sender, receiver small segment header no congestion control: UDP can blast away as fast as desired 26 UDP: more often used for streaming multimedia apps – loss tolerant – rate sensitive other UDP uses (why?): Length, in bytes of UDP segment, including header – DNS – SNMP reliable transfer over UDP: add reliability at application layer – application-specific error recover! 32 bits source port # dest port # length checksum Application data (message) UDP segment format 27 Addressing Each computer on a network requires a unique address on that network Each application requires a unique address within the computer to allow support for multiple applications (service access points, or SAP) 28 IPv4 Header Version (4 bits) Internet header length (4 bits) Type of Service (8 bits) Total Length (16 bits) Identification (16 bits) Flags (3 bits) Fragment Offset (13 bits) Time to Live (8 bits) Protocol (8 bits Header Checksum (16 bits) Source Address ( 32 bits) Destination Address (32 bits) Options (variable) Padding (variable) 29 IP and IPv6 IP provides for 32-bit source and destination addresses IPv6 (1996 standard) provides for 128-bit addresses Migraqtion to IPv6 will be a very slow process 30 Data Transmission Application layer creates data block Transport layer appends header to create PDU (protocol data unit) – Destination SAP, Sequence #, Error-Detection Code Network layer appends another header – Destination computer, facilities (e.g. “priority”) 31 Standardized Protocol Architectures Vendors like standards because they make their products more marketable Customers like standards because they enable products from different vendors to interoperate Two protocol standards are well-known: – TCP/IP: widely implemented – OSI: well-known, less used, still useful for modeling/conceptualizing 32 Routers Equipment used to interconnect independent networks Several essential functions – Provide a link between networks – Provide routing and delivery of data between processes on systems from different networks – Provide the above functions without requiring modification of the attached networks 33 Router Issues Addressing schemes Maximum packet size Interfaces Reliability 34 Internetworking Interconnected networks, usually implies TCP/IP Can appear to users as a single large network The global Internet is the largest example, but intranets and extranets are also examples 35 IP Internet Network 1 (Ethernet) Concatenation of Networks H2 H1 H7 R3 H8 H3 Network 4 (point-to-point) Network 2 (Ethernet) R1 R2 H4 Network 3 (FDDI) Protocol Stack H5 H6 H1 H8 TCP R1 IP IP ETH R2 ETH R3 IP FDDI FDDI IP PPP PPP TCP IP ETH ETH 36 Internetworking Protocols 37 Question ??? 38