* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Document
IEEE 802.1aq wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Distributed firewall wikipedia , lookup
Deep packet inspection wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Computer network wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Network tap wikipedia , lookup
Airborne Networking wikipedia , lookup
Internet protocol suite wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Virtual LAN wikipedia , lookup
UniPro protocol stack wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
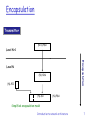
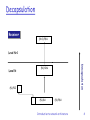
Departamento de Tecnología Electrónica Some of these slides are copyrighted by: Chapter 1 Introduction to network architecture Computer Networking: A Top Down Approach 5th edition. Jim Kurose, Keith Ross Addison-Wesley, April 2009. Introduction to network architecture 1 Chapter 1: Introduction to network architecture Chapter goals: Remembering networking basic concepts that are key for the subject. o o o o OSI Model and TCP/IP architecture Transport layer concepts Network layer concepts Data link layer concepts Introducing Virtual Local Area Networks (VLAN) Introduction to network architecture 2 Chapter 1: Introduction to network architecture 1.1 OSI Model. TCP/IP Architecture 1.2. Transport layer 1.3. Network layer 1.4. Data link layer 1.5 Virtual Local Area Network, VLANs Introduction to network architecture 3 Chapter 1: Introduction to network architecture 1.1 OSI Model. TCP/IP Architecture 1.2. Transport layer 1.3. Network layer 1.4. Data link layer 1.5 Virtual Local Area Network, VLANs Introduction to network architecture 4 TCP/IP Architecture application: supporting network applications FTP, SMTP, HTTP transport: process-process data transfer TCP, UDP network: addressing and routing of datagrams from source to destination IP, routing protocols data link: data transfer between application A_PDU message transport T_PDU segment network R_PDU Datagram/ packet data link E_PDU frame physical neighboring network elements PPP, Ethernet physical: bits “on the wire” Introduction to network architecture 5 OSI Model presentation: allow applications to interpret meaning of data, e.g., encryption, compression, machinespecific conventions session: synchronization, checkpointing, recovery of data exchange Internet stack “missing” these layers! these services, if needed, must be implemented in application Introduction to network architecture application presentation session transport network link physical 6 Encapsulation Transmitter (N+1)-PDU Level N+1 Encapsulation Level N (N)-SDU (N)-PCI (N)-DU (N)-PDU Simplified encapsulation model Introduction to network architecture 7 Decapsulation Receiver (N+1)-PDU Level N+1 Decapsulation Level N (N)-SDU (N)-PCI (N)-DU (N)-PDU Introduction to network architecture 8 Example of layer architecture: Internet Source application transport network data link physical Example: Two hosts connected by a router. Destination message segment M Ht M Ht M datagram M M Hr Ht He Hr Ht M frame Hrn Ht He H r H t Hr Ht Nota M Hx = X_PCI M = A_PCI(Ha) + User data (UD) Example UD: e_mail subject/body Text of a WhatsApp message M application transport network data link physical Mnetwork data link He physical Hr Ht M router Introduction to network architecture Phy medium 9 Multiplexion more than one transport protocol available to apps FTP Internet: TCP and UDP HTTP SMTP DNS TFTP Application How do we identify the client protocol? TCP & UDP: Port field. IP: Protocol field Ethernet: Ethertype field TCP UDP IP Link layer (LLC & MAC) Transport Network (Type/length) IEEE 802.3 (MAC) uses LLC (IEEE 802.2) IEEE 802.2: DSAP y SSAP SNAP may be used together with IEEE 802.2 to identify with Ethertype Physical Layer Introduction to network architecture 10 Multiplexion. Example (I) Introduction to network architecture 11 Multiplexion. Example (II) Data link Message H Introduction to network architecture C Data 12 Multiplexion. Example (III) Data link Network Message H Data H Introduction to network architecture E Data 13 Multiplexion. Example (IV) Data link Network Transport H Data H Introduction to network architecture Data 14 Chapter 1: Introduction to network architecture 1.1 OSI Model. TCP/IP Architecture 1.2. Transport layer 1.3. Network layer 1.4. Data link layer 1.5 Virtual Local Area Network, VLANs Introduction to network architecture 15 Transport services and protocols provide logical communication between app processes running on different hosts transport protocols run in end systems breaks app messages into segments, passes to network layer Host A Network Host B Introduction to network architecture 16 Internet transport-layer protocols more than one transport protocol available to apps Internet: TCP and UDP TCP UDP Connection- oriented Non-connectionoriented Reliable Unreliable Segment grouping Unfragmented messages Rcv orders segments User datagram ACKs and timers No ACKs Flow control No flow control Congestion control No congestion control Introduction to network architecture 17 Internet transport-layer protocols Port: identifies application Port numbers: http://www.iana.org/assignments/port- numbers Application protocol Port numbers Transport protocol FTP 20, 21 TCP Telnet 23 TCP SMTP 25 TCP DNS 53 UDP (TCP (*)) TFTP 69 UDP HTTP 80 TCP POP3 110 TCP RIP 520 UDP Introduction to network architecture 18 UDP_PDU 32 bits T_PCI T_UD Header (T_PCI) has only 4 fields. Lenght is in bytes and deals with the whole T_PDU, including the header. Source port Dest port length checksum App level data (message) UDP T_PDU format Introduction to network architecture 19 TCP: Overview point-to-point: one sender, one receiver reliable, in-order byte stream: no “message boundaries” pipelined: TCP congestion and flow control set window size send & receive buffers socket door application writes data application reads data TCP send buffer TCP receive buffer RFCs: 793, 1122, 1323, 2018, 2581 full duplex data: bi-directional data flow in same connection MSS: maximum segment size connection-oriented: handshaking (exchange of control msgs) init’s sender, receiver state before data exchange flow controlled: sender will not socket door overwhelm receiver segment Introduction to network architecture 20 TCP segment structure 32 bits URG: urgent data (generally not used) ACK: ACK # valid PSH: push data now (generally not used) RST, SYN, FIN: connection estab (setup, teardown commands) Internet checksum (as in UDP) source port # dest port # sequence number acknowledgement number head not UA P R S F len used checksum Receive window Urg data pnter Options (variable length) counting by bytes of data (not segments!) # bytes rcvr willing to accept application data (variable length) Introduction to network architecture 21 TCP seq. #’s and ACKs Host A Host B Client starts active open Server is in passive open, starts connection and confirms client open Client confirms server open Connection established Introduction to network architecture time 22 Chapter 1: Introduction to network architecture 1.1 OSI Model. TCP/IP Architecture 1.2. Transport layer 1.3. Network layer 1.4. Data link layer 1.5 Virtual Local Area Network, VLANs Introduction to network architecture 23 Network layer Network layer functions: •Packet routing •Logical addressing •Multiplexion •Packet segmentation (fragmentation) Adressing: Network & Host Network Host -Network address: Used by the router -Host address: used by a determined host Which route? Introduction to network architecture 24 IPv4 protocol IP addressing Most used network layer protocol 32-bit address Network Host Network part Host part Network and host parts are determined by the subnet mask. First x bits are set to 1 and define the number of bits of the network part. Last 32-x bits are set to 0 and define the number of bits of the host part Introduction to network architecture 25 IPv4 special addresses Addresses Meaning Use 0.0.0.0/32 The own host inside the own network As source address if a host does not know its IP address 10.0.0.0/8 172.16.0.0/12 192.168.0.0/16 Private addresses IP connectivity, but no access to the Internet 127.0.0.0/8 Loopback inteface Ip use without access to the physical medium. 169.254.0.0/16 Autoconfiguration A host does not have an IP address, neither manually nor by means of a DHCP server 224.0.0.0/4 Multicast IP Multicast (D class) 240.0.0.0/4 Reserved For the use of IANA (E class) 255.255.255.255 Limited broadcast Broadcast destination for the network Introduction to network architecture 26 IP_PDU format (datagram/packet) IP protocol version number header length (bytes) “type” of data max number remaining hops (decremented at each router) upper layer protocol to deliver payload to how much overhead with TCP? 20 bytes of TCP 20 bytes of IP = 40 bytes + app layer overhead 32 bits type of ver head. len service length fragment 16-bit identifier flgs offset upper time to header layer live checksum total datagram length (bytes) for fragmentation/ reassembly 32 bit source IP address 32 bit destination IP address Options (if any) data (variable length, typically a TCP or UDP segment) Introduction to network architecture E.g. timestamp, record route taken, specify list of routers to visit. 27 Routing table (host) Host IP addr? Subnet mask? Network Id.? MAC address? Default gateway? Gateway for 10.10.63.20? Gateway for 150.214.141.120? MAC for 10.10.63.255? Introduction to network architecture 28 Routing table (router) RT Router 1 RT Router 2 Network Subnet mask Next hop Interface Network Subnet mask Next hop Interface 192.1.1.0 255.255.255.224 - E0 192.1.1.0 255.255.255.224 192.1.4.2 E0 192.1.2.0 255.255.255.192 192.1.4.1 E1 192.1.2.0 255.255.255.192 - E1 192.1.3.0 255.255.255.128 - E2 192.1.3.0 255.255.255.128 192.1.4.2 E0 192.1.4.0 255.255.255.0 - E1 192.1.4.0 255.255.255.0 - E0 192.1.1.2 E0 NETWORK 1 E1 192.1.3.1 Router 2 192.1.4.2 192.1.1.1 E2 192.1.4.1 NETWORK 2 192.1.2.1 … 192.1.2.3 192.1.1.31 … 192.1.3.2 E1 E0 NETWORK 3 … 192.1.1.3 192.1.2.2 Router 1 192.1.3.127 192.1.2.63 When receiving a packet, the router makes the AND operation between IP dest addr and the different subnet masks in the routing table. Finally, it sends the packet for the interface pointed out by the routing table. Introduction to network architecture 29 Difference between logical addresses (IP) and physical addresses (MAC) Host Y 150.214.141.19 00:1C:27:18:00:01 Host A 142.128.1.11 00:1C:27:56:34:AA Router 142.128.1.1 150.214.141.1 12:34:56:78:90:AB Source IP addr 142.128.1.11 Dest IP addr Source MAC addr 150.214.141.19 00:1C:27:56:34:AA IP packet Dest MAC addr 12:34:56:78:90:AB Source IP addr 142.128.1.11 Dest IP addr Source MAC addr Dest MAC addr 150.214.141.19 12:34:56:78:90:AB 00:1C:27:18:00:01 IP packet Introduction to network architecture 30 Socket A process sends/recieves messages by/from its socket A socket is identified by: IP address. Port number. Port number examples: HTTP: port 80 DNS: port 53 Introduction to network architecture 31 Chapter 1: Introduction to network architecture 1.1 OSI Model. TCP/IP Architecture 1.2. Transport layer 1.3. Network layer 1.4. Data link layer 1.5 Virtual Local Area Network, VLANs Introduction to network architecture 32 LAN (Local Area Network) Local Area Networks are the most used network technology. They allow the connection between hosts and routers inside a broadcast domain. Most used LAN standards are: 802.3, Ethernet. 802.11, WI-FI (WLAN, Wireless LAN). Data link layer is divided into two sublevels: o LLC (Link Layer Control). Its functions are flow control and error correction. o MAC (Medium Access Control). Foer frame synchronism, error detection, medium access control, and physical addressing. Implmented in NIC (Network Interface Card) up to MAC sublevel. OSI LAN Data link LLC MAC Physical Introduction to network architecture 33 MAC addresses Size -> 48 bits. Example: 1B:03:F2:45:78:25 There are three types of MAC addresses: Unicast: To send DL_PDUs to an only destination. All the network interfaces have a default factory MAC address. Broadcast: As a destination, it is used to send DL_PDUs to ALL the hosts in a broadcast domain (FF:FF:FF:FF:FF:FF). Multicast: As a destination, it is used to send DL_PDUs to SOME of the hosts in a broadcast domain . Configurable. The least significant bit in the first byte of the MAC address is set to 1. IEEE manages unicast factory MAC addresses. Every manufacturer has a range of MAC addresses (to assure MAC addresses are unique) It is possible to change them. Introduction to network architecture 34 Standards LAN/MAN standards Introduction to network architecture 35 MAC_PDU (frame) 1 byte Preamble (8 bytes) Dest MAC address (6 bytes) Source MAC address (6 bytes) Length/Type (2 bytes) MAC_UD (46-1500 bytes) Trailer CRC (4 bytes) 7 bytes with 10101010. 1 byte (the last one) con 10101011. •<=1500 meaning length: - number of bytes for MAC_UD - Sublevel LLC is present. •>=1536 meaning type: Multiplexion and demultiplexion Data corresponding to the upper layer, generally IP, ARP or LLC. If MAC_UD size is below 46 bytes, there is a trailer of bytes set to 0. Note MTU for Ethernet is 1500 bytes Introduction to network architecture 36 Chapter 1: Introduction to network architecture 1.1 OSI Model. TCP/IP Architecture 1.2. Transport layer 1.3. Network layer 1.4. Data link layer 1.5 Virtual Local Area Network, VLANs Introduction to network architecture 37 VLAN Introduction: Hierarchic topology for institutional modern LANs Every working group has its own switched LAN Switched LANs may be interconnected by a hierarchy of switches. S4 S1 S2 A B S3 C F D E I G H Introduction to network architecture 38 VLAN Disadvantages: Traffic is not isolated Broadcast traffic Traffic must be limited for security and confidentiality reasons Inefficient use of switches User management Introduction to network architecture 39 VLAN VLAN: Port-based VLAN A Switch ports are divided into groups Every group constitutes a VLAN Every VLAN is a broadcast domain User management -> Change in switch configuration B C D G E F H I Introduction to network architecture 40 VLAN VLAN: How is information between groups sent? A Connect switch port to an external router Configure that port as a member of both groups Logical configuration -> Separate switches connected by a router Habitually, manufacturers include VLAN and router in an only device B C D G E F H I Introduction to network architecture 41 VLAN VLAN: Different location A Members of the same group in different buildings Several switches needed Connecting group ports between switches -> Non scalable B D E C GIntroduction to network architecture I H F 42 VLAN VLAN: Different location VLAN Trunking Trunk port belongs to all VLANs Destination VLAN? 802.1Q frame format Trunk link A B D E G C I Introduction to network architecture H F 43 VLAN IEEE 802.1Q: IEEE 802.3 (Ethernet) Preamble Dest addr Source addr Type Data CRC IEEE 802.1Q Preamble Dest addr Source TPID TCI Type Data addr New CRC Tag Control Information Tag Protocol Identifier Introduction to network architecture 44 VLAN VLAN: MAC-based VLAN The network administrator creates VLAN groups based on MAC address ranges. Switch port is connected to the VLAN that corresponds to the associated host’s MAC address. IP-based VLAN Based on IPv4 or IPv6 addresses Based on network protocols (Appletalk, IPX, TCP/IP) Introduction to network architecture 45