* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download HSARPA Cyber Security R&D
Post-quantum cryptography wikipedia , lookup
Next-Generation Secure Computing Base wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Citizen Lab wikipedia , lookup
Deep packet inspection wikipedia , lookup
Unix security wikipedia , lookup
Wireless security wikipedia , lookup
Airport security wikipedia , lookup
Distributed firewall wikipedia , lookup
Secure multi-party computation wikipedia , lookup
Security printing wikipedia , lookup
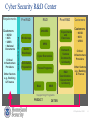
Computer and network surveillance wikipedia , lookup
Mobile security wikipedia , lookup
Security-focused operating system wikipedia , lookup
Cyberterrorism wikipedia , lookup
International cybercrime wikipedia , lookup
Cybercrime countermeasures wikipedia , lookup
Cyber-security regulation wikipedia , lookup
Cyberwarfare wikipedia , lookup
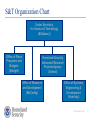
Dept. of Homeland Security Science & Technology Directorate Priorities in Security Research Funding ACM CCS Washington, DC October 26, 2004 Douglas Maughan, Ph.D. Program Manager, HSARPA [email protected] 202-254-6145 / 202-360-3170 Presentation Agenda DHS Overview Cyber Security R&D Overview Cyber Security R&D Activities National Strategy to Secure Cyberspace Secure Domain Name System (DNSSEC) Secure Protocols for the Routing Infrastructure DHS / NSF Cyber Security Testbed Large-scale Network Security Datasets Cyber Economic Assessment studies “New” Activities 23 September 2004 2 General DHS Organization Secretary (Ridge) & Deputy Secretary (Loy) Management (Hale) Border & Transportation Security (Hutchinson) Emergency Preparedness & Emergency Response (Brown) • Coast Guard • Secret Service • Citizenship & Immigration & Ombuds • Civil Rights and Civil Liberties • Legislative Affairs • General Counsel • Inspector General • State & Local Coordination • Private Sector Coordination • International Affairs • National Capital Region Coordination • Counter-narcotics • Small and Disadvantaged Business • Privacy Officer • Chief of Staff Information Analysis & Infrastructure Protection (Libutti) Science & Technology (McQueary) 23 September 2004 3 Border and Transportation Security (BTS) Mission: Securing our nation's air, land, and sea borders is a difficult yet critical task. The United States has 5,525 miles of border with Canada and 1,989 miles with Mexico. Our maritime border includes 95,000 miles of shoreline. Each year, more than 500 million people cross the borders into the U.S., some 330 million of whom are non-citizens. CBP – Customs and Border Protection ICE – Immigrations and Customs Enforcement TSA – Transportation Security Administration APHIS – Animal and Plant Health Inspection Service ODP – Office for Domestic Preparedness 23 September 2004 4 Emergency Preparedness & Response Mission: Ensure that our nation is prepared for catastrophes whether natural disasters or terrorist assaults. Not only will the EP&R Directorate coordinate with first responders, it will oversee the federal government's national response and recovery strategy. FEMA – Federal Emergency Management Agency NIRT – Nuclear Incident Response Teams DES – Domestic Emergency Support NDPO – National Domestic Preparedness Office 23 September 2004 5 Information Analysis and Infrastructure Protection (IAIP) Mission: Ensure the capability to identify and assess current and future threats to the homeland, map those threats against our vulnerabilities, issue timely warnings and take preventive and protective action to secure the national infrastructures. NCSD – National Cyber Security Division NCS – National Communications System PSD – Physical Security Division ICD – Infrastructure Coordination Division Our main internal DHS customers 23 September 2004 6 Science and Technology (S&T) Mission Conduct, stimulate, and enable research, development, test, evaluation and timely transition of homeland security capabilities to federal, state and local operational end-users. 23 September 2004 7 S&T Organization Chart Under Secretary for Science & Technology (McQueary) Office of Plans Programs and Budgets (Albright) Homeland Security Advanced Research Projects Agency (Oxford) Office of Research and Development (McCarthy) Office of Systems Engineering & Development (Kubricky) 23 September 2004 8 Crosscutting Portfolio Areas Chemical Biological Radiological Nuclear High Explosives Cyber Security USSS Paul Mahon, Ptfl Mgr 23 September 2004 9 Execution Science and Technology Directorate Office of Research and Development • • • Homeland Security Advanced Research Projects Agency Systems Engineering & Development Centers Fellowships Scholarships Stewardship of an enduring capability Innovation, Adaptation, & Revolution Development Engineering, Production, & Deployment 23 September 2004 10 Legacy of HSARPA Name How is it different from DARPA? Differences 85-90% of funds for identified DHS requirements 10-15% of funds for revolutionary research Breakthroughs, New technologies and systems These percentages likely to change over time, but we need to meet today’s requirements 23 September 2004 11 Presentation Agenda DHS Overview Cyber Security R&D Overview Cyber Security R&D Activities National Strategy to Secure Cyberspace Secure Domain Name System (DNSSEC) Secure Protocols for the Routing Infrastructure DHS / NSF Cyber Security Testbed Large-scale Network Security Datasets Cyber Economic Assessment studies “New” Activities 23 September 2004 12 Cyber Security R&D Portfolio: Scope The Internet serves a significant underlying role in many of the Nation’s critical infrastructures Adversaries face asymmetric offensive / defensive capabilities with respect to traditional warfare Makes cyberspace an appealing battleground Cyberspace provides the ability to exploit weaknesses in our critical infrastructures Communications, monitoring, operations and business systems Provides a fulcrum for leveraging physical attacks The most significant cyber threats to the nation are very different from “script-kiddies” or virus writers DHS S&T focus is on those threats and issues that warrant national-level concerns 23 September 2004 13 Cyber Security R&D Center Requirements Pre R&D R&D Customers Critical Infrastructure Providers DNSSEC Prioritize requirements • NCSD • NCS • USSS • National Documents Post R&D Experiments and Exercises Workshops Customers Customers • NCSD • NCS • USSS SPRI Sector Roadmaps Solicitation Preparation Cyber Economics Outreach – Venture Community & Industry Future Programs Other Sectors e.g., Banking & Finance BAA SBIR R&D Coordination Government & Industry Critical Infrastructure Providers Other Sectors e.g., Banking & Finance Supporting Programs PREDICT DETER 23 September 2004 14 Post Research Activities Experiments U.S. / Canada Secure Blackberry Experiment 3 phase homeland security deployment activity Includes industry participants from both countries Oil and Gas Sector Sector workshop in late July Expected to lead to technology pilot deployments Department of Treasury FS ISAC, FSSCC, Numerous sector participants Technology pilot organization in process 23 September 2004 15 Post Research Activities (continued) Exercises National Exercise Plan (managed by DHS ODP) National Cyber Security Exercise as part of NEP Several regional cyber security tabletop exercises Others U.S. NORTHCOM Unified Defense 05 / TOPOFF 3 CWID 2005 (originally known as JWID) 23 September 2004 16 DHS S&T Commercial Outreach Strategy Assist commercial companies in providing cyber security technology to DHS and other government agencies Assist DHS S&T-funded researchers in transferring cyber security technology to larger, established security technology companies Partner with the venture capital community to transfer technology to existing portfolio companies, or to create new ventures We will work with the VCs to: Focus on bringing innovation to the marketplace Accelerate development and deployment Provide orders-of-magnitude leverage of DHS R&D funding Government We will partner with the VCs, not compete with them Work with many VCs and portfolio companies Provide liaison and bridge activities We do not invest for equity Established Commercial Companies DHS Researchers Emerging Commercial Companies 23 September 2004 17 Presentation Agenda DHS Overview Cyber Security R&D Overview Cyber Security R&D Activities National Strategy to Secure Cyberspace Secure Domain Name System (DNSSEC) Secure Protocols for the Routing Infrastructure DHS / NSF Cyber Security Testbed Large-scale Network Security Datasets Cyber Economic Assessment studies “New” Activities 23 September 2004 18 Domain Name System and Security Critical Internet infrastructure component Virtually DNS database maps: Name to IP address (for example: www.isi.edu = 128.9.176.32) And every Internet application uses the DNS many other mappings (mail servers, IPv6, reverse…) DNS threats identified in early 1990s DNSSEC Cryptographic signatures in the DNS Assures integrity of results returned from DNS queries Protects against tampering in caches and during transmission End-system checks the chain of signatures up to the root 23 September 2004 19 Activities To Date Formation of ad-hoc government and industry “steering committee” Two workshops in early and late May May: Amsterdam – as part of the RIPE agenda 23 May: San Fran – affiliated with NANOG Attendees included: DNS software developers, DNS root operators (U.S. and International), government network operators, and numerous other stakeholders 3 Initial R&D Funding – NIST, industry Future Activities Pilot deployments of DNSSEC on .us and .gov network 23 September 2004 20 Secure Protocols for the Routing Infrastructure (SPRI) BGP is the routing protocol that connects ISPs and subscriber networks together to form the Internet BGP does not forward subscriber traffic, but it determines the paths subscriber traffic follows The BGP architecture makes it highly vulnerable to human errors and malicious attacks against Links between routers The routers themselves Management stations that control routers Working with industry to develop solutions for our current routing security problems and future technologies 23 September 2004 21 DHS / NSF Cyber Security Testbed “Justification and Requirements for a National DDOS Defense Technology Evaluation Facility”, July 2002 We still lack large-scale deployment of security technology sufficient to protect our vital infrastructures Recent investment in research on cyber security technologies by government agencies (NSF, DARPA, armed services) and industry. One important reason is the lack of an experimental infrastructure and rigorous scientific methodologies for developing and testing next-generation defensive cyber security technology The goal is to create, operate, and support a researcher-andvendor-neutral experimental infrastructure that is open to a wide community of users and produce scientifically rigorous testing frameworks and methodologies to support the development and demonstration of next-generation cyber defense technologies 23 September 2004 22 Architectural Plan Construct a homogeneous emulation cluster based upon University of Utah’s Emulab Implement network services – DNS, BGP Add containment, security, and usability features to the software Add (controlled) hardware heterogeneity Connect to other government and industry testbeds (once we have our act together) 23 September 2004 23 DETER Testbed Architecture User Internet Ethernet Bridge with Firewall ‘User’ Server User files Control DB 'Gatekeeper' 'Boss' Server Image fills this entire area User Acct & Data logging External VLAN Web/DB/SNMP, switch mgmt Boss VLAN Users VLAN Router (OR originates at the upper left corner of the area with Firewall … outlined and is sized to the full width or height of this bounding box.) Control Hardware VLAN Node Serial Line Server Control Network VLAN Power Serial Line Server 64 @100bT Control ports PC PC PC Power 160Controller 64 x 4 @1000bT Data ports Switch Control Interface Programmable Patch Panel (VLAN switch) DETER Project – Feb 04 23 September 2004 24 DETER Testbed Status Developed Draft Policy and Procedures Experiment Definition Experiment Review Board Security Isolation Argument Architecture Design Report ISI and UCB Node Operational Held first set of Experiments June 8, 2004 Workshop held yesterday In conjunction with ACM CCS in Washington, DC Open to entire research community 23 September 2004 25 A Protected REpository for Defense of Infrastructure against Cyber Threats PREDICT Program Objective “To advance the state of the research and commercial development (of network security ‘products’) we need to produce datasets for information security testing and evaluation of maturing networking technologies.” Rationale / Background / Historical: Researchers with insufficient access to data unable to adequately test their research prototypes Government technology decision-makers with no data to evaluate competing “products” Bottom Line: Improve the quality of defensive cyber security technologies 23 September 2004 26 Activities To Date Industry Workshop (Feb. 11-12, 2004) Begin the dialogue between HSARPA and industry as it pertains to the cyber security research agenda Discuss existing data collection activities and how they could be leveraged to accomplish the goals of this program Discuss data sharing issues (e.g., technical, legal, policy, privacy) that limit opportunities today and develop a plan for navigating forward Develop a process by which “data” can be “regularly” collected and shared with the network security research community 23 September 2004 27 Workshop Attendees (Feb. 11-12, 2004) AOL UUNET Verio XO Communications Akamai Arbor Networks Riverhead Networks System Detection Cisco Packet Clearing House Symantec USC-ISI UC San Diego Univ. of Washington BBN Technologies CERT/CC LBNL Internet2 CAIDA Merit Networks Citigroup Cooley, LLC (Lawyer) 23 September 2004 28 Data Collection Activities Classes of data that are interesting, people want collected, and seem reasonable to collect Netflow traces – headers and full packet (context dependent) Critical infrastructure – BGP and DNS data Topology data IDS / firewall logs Performance data Network management data (i.e., SNMP) VoIP (1400 IP-phone network) Blackhole Monitor traffic Packet 23 September 2004 29 Trusted Access Repository Process PREDICT Coordination Center (Government-funded, Externally hosted) Institutional Sponsorship Data Providers Data Listing Researchers Data Hosting Sites Proposal Review Process Accepted Proposals MOU / MOA 23 September 2004 30 Sample Datasets that will be available University of Michigan University of Washington Wisconsin Advanced Internet Lab – Netflow, iSink logs, IDS logs XO Communications Performance data, NetFlow data, and routing protocol data from the Abilene network University of Wisconsin Host-based forensic data and honeypot data Internet 2 Dark address space monitoring, honeypot monitoring, BGP Beacon routing data, and routing protocol sensors, MichNet routing protocol data and Netflow data Netflow and routing protocol logs Packet Clearing House BGP routing dataset and VoIP measurement data 23 September 2004 31 Sample Datasets (continued) CAIDA Internet Software Consortium (ISC) Packet traces from Internet Business Exchange (IBX) point Los Nettos - LA regional network provider Packet traces from OC48 operational network Equinix DNS packet traces from F-root Verio Topology measurement data, Network Telescope data Full packet headers, NetFlow data, SNMP data, and standard logs DNS root server data. Los Nettos hosts both the B and L root servers Internet topology data based on the SCAN topology-mapping project LBNL Anonymized enterprise traffic from internal LBNL networks 23 September 2004 32 PREDICT – Proposed Timeline Sep 1- Oct 30: Working groups complete actions identified at last PI meeting Data Schema WG Application Process WG All MOU/MOAs in develoment Public Relations WG Oct 1-Nov 15: Conduct internal PREDICT Process Pilot Nov 15- Dec 15: Conduct external PREDICT Process Pilot Dec 15-Jan 15: Modify PREDICT processes based on feedback from PREDICT pilot ~Jan 15: PREDICT goes live Working through announcement process 23 September 2004 33 Cyber Economic Assessment Studies Examination of current “cyber event” cost evaluation methods Business Case Development Understanding of costs and losses Strategies for encouraging cyber security investment Cyber Risk Prioritization 23 September 2004 34 Presentation Agenda DHS Overview Cyber Security R&D Overview Cyber Security R&D Activities National Strategy to Secure Cyberspace Secure Domain Name System (DNSSEC) Secure Protocols for the Routing Infrastructure DHS / NSF Cyber Security Testbed Large-scale Network Security Datasets Cyber Economic Assessment studies “New” Activities 23 September 2004 35 Recent SBIRs SBIR = Small Business Innovative Research CROSS-DOMAIN ATTACK CORRELATION TECHNOLOGIES Objective: Develop a system to efficiently correlate information from multiple intrusion detection systems (IDSes) about “stealthy” sources and targets of attacks in a distributed fashion across multiple environments. REAL-TIME MALICIOUS CODE IDENTIFICATION Objective: Develop technologies to detect anomalous network payloads destined for any service or port in a target machine in order to prevent the spread of destructive code through networks and applications. These technologies should focus on detecting “zero day attacks”, the first appearance of malicious code for which no known defense has been constructed. 23 September 2004 36 HSARPA Cyber Security Broad Area Announcement (BAA 04-17) A critical area of focus for DHS is the development and deployment of technologies to protect the nation’s cyber infrastructure including the Internet and other critical infrastructures that depend on computer systems for their mission. The goals of the Cyber Security Research and Development (CSRD) program are: To perform research and development (R&D) aimed at improving the security of existing deployed technologies and to ensure the security of new emerging systems; To develop new and enhanced technologies for the detection of, prevention of, and response to cyber attacks on the nation’s critical information infrastructure. To facilitate the transfer of these technologies into the national infrastructure as a matter of urgency. http://www.hsarpabaa.com 23 September 2004 37 BAA Technical Topic Areas (TTAs) System Security Engineering Vulnerability Prevention Vulnerability Discovery and Remediation Tools and techniques for analyzing software to detect security vulnerabilities Cyber Security Assessment Tools and techniques for better software development Develop methods and tools for assessing the cyber security of information systems Security of Operational Systems Security and Trustworthiness for Critical Infrastructure Protection 1) Automated security vulnerability assessments for critical infrastructure systems 2) Improvements in system robustness of critical infrastructure systems 3) Configuration and security policy management tools 4) Cross-platform and/or cross network attack correlation and aggregation 23 September 2004 38 BAA TTAs (continued) Security of Operational Systems Wireless Security Security tools/products for today’s networks Solutions and standards for next generation networks Investigative and Prevention Technologies Network Attack Tools and techniques for attack traceback Technologies Forensics to Defend against Identity Theft R&D of tools and techniques for defending against identity theft and other financial systems attacks, e.g., phishing 23 September 2004 39 BAA Program / Proposal Structure NOTE: Deployment Phase = Test, Evaluation, and Pilot deployment in DHS “customer” environments Type I (New Technologies) New technologies with an applied research phase, a development phase, and a deployment phase (optional) Type II (Prototype Technologies) More mature prototype technologies with a development phase and a deployment phase (optional) Funding not to exceed 36 months (including deployment phase) Funding not to exceed 24 months (including deployment phase) Type III (Mature Technologies) Mature technology with a deployment phase only. Funding not to exceed 12 months 23 September 2004 40 Tackling Cyber Security Challenges: Business Not as Usual Strong mission focus (avoid mission creep) Close coordination with other Federal agencies Outreach to communities outside of the Federal government Building public-private partnerships (the industrygovernment *dance* is a new tango) Strong emphasis on technology diffusion and technology transfer Migration paths to a more secure infrastructure Awareness of economic realities 23 September 2004 41 Summary DHS S&T is moving forward with an aggressive cyber security research agenda Working with industry to solve the cyber security problems of our current infrastructure DNSSEC, Working with academe and industry to improve research tools and datasets DHS/NSF Secure Routing Cyber Security Testbed, PREDICT Looking at future RDT&E agendas with the most impact for the nation SBIRs, BAA 04-17 23 September 2004 42 Douglas Maughan, Ph.D. Program Manager, HSARPA [email protected] 202-254-6145 / 202-360-3170 23 September 2004 43