* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download My final presentation
Survey
Document related concepts
Extensible Storage Engine wikipedia , lookup
Entity–attribute–value model wikipedia , lookup
Relational algebra wikipedia , lookup
Tandem Computers wikipedia , lookup
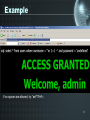
Concurrency control wikipedia , lookup
Oracle Database wikipedia , lookup
Ingres (database) wikipedia , lookup
Microsoft Access wikipedia , lookup
Team Foundation Server wikipedia , lookup
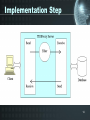
Microsoft Jet Database Engine wikipedia , lookup
Database model wikipedia , lookup
Clusterpoint wikipedia , lookup
Relational model wikipedia , lookup
Open Database Connectivity wikipedia , lookup
Transcript
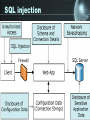
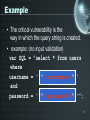
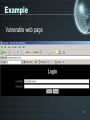
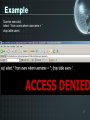
Analysis of SQL injection prevention using a filtering proxy server By: David Rowe Supervisor: Barry Irwin Presentation Outline • • • • • • Problem statement Motivation (example) Implementation Results Concluding remarks Questions 2 SQL injection • SQL Injection is a method by which the parameters of a Web-based application are modified in order to change the SQL statements that are passed to a database. • An attacker is able to insert a series of SQL statements into a 'query' by manipulating data input. 3 SQL injection 4 Example • The critical vulnerability is the way in which the query string is created. • example: (no input validation) var SQL = "select * from users where username = ' "+ username +" ' and password = ' "+ password +" '"; 5 Example Vulnerable web page 6 Example Queries executed: select * from users where username = “ drop table users 7 Example 8 Example If no spaces are allowed, try: 'or/**/1=1-- 9 SQL injection types • Redirecting and reshaping a query involves inserting SQL commands into the query being sent to the database. The commands allow a direct attack on the database. • Error message based SQL injection makes use of the database error messages returned to the client. The messages provide clues as to the database type and structure as well as the query structure. • Blind SQL injection which involves a lot of guesswork and thus requires a larger investment in time. The attacker tries many combinations of attack and makes the next attack attempt based on their interpretation of the resulting html page output. 10 Classes of SQL injection • Inband uses the existing connection to the database to manipulate the database. An example of this would be to use the data returned in a well formed web page or an error message. • Out of band requires a new channel to be opened between the client and the application. This usually requires the database to connect out to the client using email, http or a database connection. • Inference does not require any data transfer at all but uses properties such as web server response time or web server response codes. 11 Project Goals • Analyse the structure of SQL query commands • Build a parser that will check allowable patterns of SQL statements • Create a proxy server that will filter SQL commands. • Prevent a SQL injection attack to a database using this proxy server. • Prove that SQL injection can be prevented using the filter developed to work on the proxy server. 12 SQL injection 13 Implementation Step 14 Implementation Step 15 Results • Analyse the structure of SQL query commands • Build a filter that will check allowable patterns of SQL statements • Create a proxy server that will filter SQL commands. • Prevent a SQL injection attack to a database using this proxy server. • Prove that SQL injection can be prevented using the filter developed to work on the proxy server. 16 Results • Working proxy server – Extracts the SQL from a TDS query packet – Prevents SQL injection attacks • • • • White list - principle of least privilege Black list - disallow Gray list - possibly harmful Regex list - input validation – Logs • Extracted SQL queries • Halted SQL – Alerts • DBA via UDP 17 Results Average web transaction processing time - Hons08 30 Time (ms)/query 25 20 Select 15 Insert 10 5 0 Direct Proxy - No filter Proxy - Filter Query Scenario 18 Results Average web transaction processing time - Netserv 30 25 Time (ms)/query 20 Select 15 Insert 10 5 0 Direct Proxy - No filter Proxy - Filter Query scenario 19 Conclusion • Advantages – Independent of flaws in application coding and database privileges – Can operate on a separate server with real time analysis – Another layer of protection • Disadvantages – False positives also filtered out too – Won’t work if data is encrypted 20 Questions 21