* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download sql-injection-attack-ndss
Survey
Document related concepts
Oracle Database wikipedia , lookup
Relational algebra wikipedia , lookup
Extensible Storage Engine wikipedia , lookup
Entity–attribute–value model wikipedia , lookup
Tandem Computers wikipedia , lookup
Microsoft Access wikipedia , lookup
Functional Database Model wikipedia , lookup
Ingres (database) wikipedia , lookup
Microsoft Jet Database Engine wikipedia , lookup
Clusterpoint wikipedia , lookup
Database model wikipedia , lookup
Relational model wikipedia , lookup
Open Database Connectivity wikipedia , lookup
Transcript
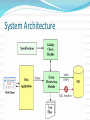
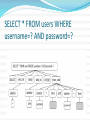
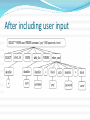
Introduction SQL Injection is a very old security attack. It first came into existence in the early 1990's ex: ”Hackers” movie hero does SQL Injection to hack into the database SQL injection is still pervasive. One of the security magzine claimed that more than a million sites are still vulnerable to SQL Injections What is SQL Injection Attack? Definition: Injecting SQL statements in to the vulnerable spots with a malicious intention It refers to one of the code injection attacks where in data provided by the user is included in a SQL query such that part of the user’s input is treated as SQL code. Most of the cyber crimes are pertaining stealing credit card numbers and stealing money using SQL Injection in the wake of this decade. Attack intents Extracting data Adding or modifying data Performing Denial-Of-Service attack Bypassing authentication Privilege escalation, etc Injection Mechanisms Injection through user inputs Injection through cookies Injection through server variables Second order injection Vulnerability The query behind such a login screen will be SELECT * FROM USERS WHERE username=‘”+usrname+”’ and password=‘”+pass+”’; If the user enters username as x’ or 1=1- - and anything as password. The statement that will be evaluated is, SELECT * FROM USERS WHERE username=‘x’ or 1=1 - -’ and password=‘anything’; This query will be true for each and every tuple of the table and the attacker will be successful in logging into the application as administrator (first user in the table). Any tautology works 1 OR 1=1 1' OR '1'='1 x' OR greg LIKE '%re%' admin' OR 1<4 admin' OR 4>2 x' OR 'select' > 's' x' OR 'select' < x' Blind SQL Injection Attack In this attack cracker/hacker tries to enter wrong data deliberately to figure out the database structure and its properties www.site.com/userid=22' or www.site.com/userid=22 or 1=1 UNION select null, null, null, null....... Denial of Service If the attacker gives input as “ ’ ; SHUTDOWN; - -” The query will be SELECT * FROM USERS WHERE username=’ ‘; SHUTDOWN; - -’ and password=‘anything’; The database gets shutdown and which will lead to a DoS attack on the web application. Evasion Techniques White space manipulation the white spaces can be replaced by tab, carriage return or line feed, which goes undetected by any firewall, IDS,etc Comment exploitation The sql style comment - - is detected by a no of applications these days, but it can be replaced by C style comment /**/. Eg UN/*comment*/ION, the sql parsing engines nowadays strip off all comments before submitting query for execution, thus evasion can be done. Encoding techniques The easiest method of defeating detection Most common encodings are URL encoding Unicode/UTF-8 Hex encoding char() function Mitigation Techniques The root cause of SQL injection vulnerabilities is insufficient input validation. The mitigation can be Defensive coding practices like Input type checking Encoding of inputs Positive pattern matching Identification of all input sources This the best way of preventing SQLIAs but its application is problematic in practice. Use static analysis and also runtime analysis Have java script to validate input at the client side Thoroughly parse all the statements that are generated at the runtime using tools like AMNESIA Praveenkumar G Hoolimath 10IT16F Introduction It is a specification based approach, specifications here are the different types of queries that the web application is expected to execute. These specifications help to build rules. The SQL queries will be intercepted and checked with these rules. The queries violating these rules will be discarded. Different phases Phase 1: Definition of specifications (using EBNF) Phase 2: Interception of SQL statements Phase 3: Lexical analysis Phase 4: Syntactical verification of SQL statements Phase 5: Forwarding valid SQL statements to the database Phase 6: Logging System Architecture Specification using EBNF SELECT * FROM User WHERE userid=‘”+username+”’ and password=‘”+pass+”’; <Query specification> := SELECT <Select List> <From Clause> <Where Clause> <Select List> := <Table Column> (<COMMA> <Table Column>)* <From Clause> := FROM <Table reference> <Where Clause> := WHERE <search condition> AND <search condition> <search condition> := <Table Column> "=" <STRING LITERAL> Salient Features It prevents all forms of SQL injection attacks Its effectiveness is independent of any particular target system, application environment, or DBMS There is no need to modify the source code of existing web applications to apply the new protection scheme to them. Vasanth Raja 10IT05F SQL PARSE TREE VALIDATION The solution is based on validation at run time. Checks the statement structure before the inclusion of the user input and after the inclusion of user input. SQL PARSE TREE VALIDATION(2) This method aims at 1) Minimizing the effort required by the programmer 2) Eliminate the possibility of the attack 3) Minimize the runtime overhead SELECT * FROM users WHERE username=? AND password=? After including user input This method is not disallowing the program from using tautologies. Eliminating tautologies is not the goal Let the tautology be there in the user input but find the structure at run time and stop the query to be fed to database engine This method allows the programmer to include the comments in the SQL statements Query structure including comments as tokens Class structure of the System Thank you