* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download F5 User’s Group
Survey
Document related concepts
Wireless security wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Computer security wikipedia , lookup
Dynamic Host Configuration Protocol wikipedia , lookup
Net neutrality law wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Remote Desktop Services wikipedia , lookup
Cross-site scripting wikipedia , lookup
Deep packet inspection wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Distributed firewall wikipedia , lookup
Transcript
F5 User’s Group
2
Welcome!
Please introduce yourself
Name
Title
Company
Your role
Introductions
Name
Title
Company
Role
Requests (optional)
• Application
• Network
• Security
Requests? (optional)
IT agility. Your way.
3
F5 User’s Group Meeting June 12th, 2013
NEW Agenda
F5 Technology Update—What’s new in 11.4
Application Acceleration Manager
Centralized Policy Matching
VMWare View Proxy
VXLAN Gateway & NVGRE Gateway
Programmable Infrastructure
JavaScript and CSS Minification
DNS Recap
New Platforms
F5’s role at Interop
By the way…
FLOWJAM
Lunch
Roundtable discussion
11.0 was released
in August 2011
WHAT’S NEW IN VERSION 11.4
Brian Deitch, FSE
Jon Bartlett, FSE
5
What is Application Acceleration Manager?
• Web Accelerator Manager
• WAN Optimization Manager
• Web Accelerator will optimize your web applications and
decreases page load time anywhere from 10 to 90%
• WAN Optimization Manager will optimize network traffic
and reduce latency
What happens if I already own WA or WOM?
• You will be licensed as AAM with 11.4
• Since WA and WOM are AAM, you get both features
6
What is Centralized Policy Matching?
• Policy matching framework enables creation of flexible L7
policies:
• Centralized policy matching across BIG-IP modules
• Protocol-neutral matching for HTTP and other L7/L4
protocols
• Replaces HTTP class in v11.4
BIG-IP
Local Traffic
Manager
BIG-IP
Application
Acceleration
Manager
BIG-IP
Application
Security
Manager
Centralized Policy Matching
7
Old
HTTP Class
New
Centralized Policy
8
VMWare View Proxy-PCoIP Support
What does this really mean?
• Customizable TCP/IP Stack
• PCoIP Decryption and re-encryption
• Elimination of Secure Gateway Servers
9
Typical VMWare View Deployment
Client
DMZ
Router
BIG-IP LTM
Secure Gateway Servers
PCoIP
CORP
Connection Servers:
VMWare View
10
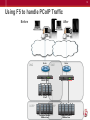
Using F5 to handle PCoIP Traffic
Before
After
Client
DMZ
Router
Client
DMZ
BIG-IP LTM
Router
BIG-IP LTM + APM
Secure Gateway Servers
PCoIP
CORP
CORP
Connection Servers:
VMWare View
Connection Servers:
VMWare View
11
VXLAN Functionality
What does this really mean?
• Simplify the Expansion of Virtual Networks
• Apply Services across
Heterogeneous Networks
for Optimized Performance
• Improve Application
Mobility and Business
Continuity
12
Configuring VXLAN from the CLI
create net vlan vxlancontrol { interfaces add { 1.1} mtu 1550 }
create net self myvtep { address 10.1.1.1/32 vlan vxlancontrol }
create net tunnels tunnel vxlan5000 { local-address 10.1.1.1 remoteaddress 239.0.0.1 profile vxlan key 5000 }
create net vlan legacy5000 { interfaces add { 1.2 } }
create net vlan-group vxlan5000-bridge { members add { legacy5000
vxlan5000 } }
create net self vxlan5000-defroute { address 11.1.1.254/32 vlan
vxlan5000-bridge }
13
NVGRE Functionality
• Gateway between multiple Microsoft Hyper-V enabled
virtual networks
• NVGRE Gateway plugin available for Microsoft’s
System Center Virtual Machine Manager on DevCentral
Video: http://goo.gl/jQKvE
Download: http://goo.gl/LfJd5
14
What is Programmable Infrastructure?
Programmable infrastructure improves IT agility to
deliver your applications faster and with higher
predictability.
Extensibility
Management Plane
Data Plane
Control Plane
15
Programmable Infrastructure
Unleashing TMOS Programmability
iRules
Intercept, inspect,
transform, direct and
make decisions based
on inbound and
outbound application
traffic.
iApps
Define and tie all
related application
availability, security
and optimization
services to the
application. Deploy
these services with
optimum,
application-specific
configurations in
only a few minutes.
iControl
Realize new levels of
automation and
configuration
management with F5’s
web services–enabled
open.
iCall
Automate tasks to
improve
operations by
monitoring for
events and
executing scripts
to resolve issues
quickly and
predictable.
What’s New
iRule Procedures
Build a library of
functionality that can be
re-used, controlled and
managed in a consistent
way
Generic iApps
Leverage application
service objects to
provide a logical
container and context
to your application
without the need for
deployment
templates.
iControl REST
REST provides a
modern lightweight API
standard for
integration preferred
Control Plane
Automation
Automate BIG-IP
to dynamically
respond to events
and perform BIGIP configuration
actions.
16
iCall Examples
Local Traffic Manager
Triggered
–
Run TCP Dump on an event
–
Detect server errors and mark server down in a
pool on excessive errors
–
On Failover, generate qkview and/or ucs
–
GTM Monitor weight change - Set LTM wildcard
virtual server "VS Score" value based on the
number of available pool members of tertiarilyrelated (that is, non-default to the VIP) pool.
–
–
Re-prioritization of SharePoint nodes based on
the SharePoint -reported health value that is
delivered in an HTTP response.
Automatic qkview creation upon core dump or
unknown restart - Customers are frequently
asked to generate qkviews for support to
troubleshoot issues. To improve the chance of
repro, it would be good to have an event that
detects core dumps/ restarts and automatically
creates a qkview.
Periodic
•
Generate Config Backup
•
Pool Synchronization from DNS - use an
iApp to accept a list of host names that
will be used to populate a pool via DNS.
Detect when the results of the resolution
change and repopulate the pool to stay
synchronized.
•
Pool update on DHCP response - create
a script that takes DHCP responses and
adds the IPs to a pool.
•
Re-prioritization of SharePoint nodes
based on the SharePoint -reported health
value that is delivered in an HTTP
response.
•
Datagroup Sync with external source
Perpetual
•
Achieve application delivery optimization
and enhanced productivity without the
need to rewrite applications
17
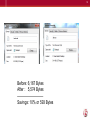
JavaScript and CSS Minification
What does this really mean?
• Reduces overall file size
• Removes whitespace
• Removes comments
18
Before: 6,167 Bytes
After : 5,574 Bytes
-------------------------Savings: 10% or 593 Bytes
19
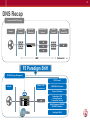
DNS Recap
Conventional DNS Thinking
Internet
External
Firewall
DNS Load
Balancing
Array of DNS
Servers
DMZ
Internal
Firewall
Hidden
Master DNS
Datacenter
F5 Paradigm Shift
F5 DNS Delivery Reimagined
DNS Firewall
Internet
Master DNS
Infrastructure
DNS DDoS Protection
Protocol Validation
Authoritative DNS
Caching Resolver
Transparent Caching
High Performance DNSSEC
DNSSEC Validation
Intelligent GSLB
20
New platforms – TMOS versions
Platform
Versions supported
F5-BIG-LTM-5000s
v11.4
F5-BIG-LTM-5200v
v11.4
F5-BIG-LTM-7000s
V11.4
F5-BIG-LTM-7200v
v11.4
F5-BIG-LTM-10200s
v11.4
21
22
23
24
F5’s Role at Interop
25
Attacking the Network
• 2 BreakingPoint Firestorms w/40 Gbits each
– Denver
– External Edge Las Vegas
•
Leveraged Capabilities
–
–
–
–
Client Simulation
Application Session Simulation
Security Attack Strike Lists
Protocol Fuzzing
26
Attacking the Network
Network Attack from the internet to all users at the show
Sourced from random spoofed locations on the
internet
Destined for the attendees
On ports identified that should be protected ie:
Microsoft file transfers, SQL and other common
vulnerabilities
Common load 33Gbits per second
F5 tech: AFM
DDoS attack to www.interop.com
Sourced from 45.0.14&15.0/24 upstream over the
100Gbit link
Destined for the Interop show’s ns server
Common load 7Gbits per second
Common requests: 3.5 Million per second
DDoS attack to www.interop.com
Sourced from 45.0.14&15.0/24 upstream over the
100Gbit link
Destined for www.interop.com
Common load 800Mbits per second
Common requests: 70k per second
Simulated bots: 30k
F5 tech: AFM & ASM
DoS attack to www.interop.com using SQL Injection
Sourced from 45.0.14&15.0/24 upstream over the
100Gbit link
Destined for www.interop.com
Common load 20Mbits per second
F5 tech: AFM & ASM
F5 tech: DNS Express
Watch the Video
http://www.youtube.com/watch?feature=player_detailpage&v=hFpVivIqx9Q#t=59s
27
Attack Mitigation Technologies
• Advanced Firewall Manager (AFM)
– Provides ACL management
– Provides DOS Vector Protection
• DNS Express
– High Speed Responder
• Application Security Module (ASM)
•
– Signature detection
– DDoS detection
iRules
– Provide custom detection and mitigation
28
By the way…
Other cool features in 11.4
•
•
•
•
•
•
•
•
ASM HP WebInspect Vulnerability Scanner Integration
AFM SIP DDoS protection
APM local user DB
APM Citrix Traffic Shaping
AAM Forward Error Correction
vCMP Flexible Allocation
Heterogeneous Failover Groups
Enhanced sFlow
• http://blog.sflow.com/2013/06/f5-big-ip-ltm-and-tmos-1140.html
• SSL Elliptic Curve Cryptography
• ProxyPass via Rewrite profiles
Thank You!
Please fill out a survey