* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Firewall Categorization Methods
Survey
Document related concepts
Extensible Authentication Protocol wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Internet protocol suite wikipedia , lookup
Airborne Networking wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Parallel port wikipedia , lookup
Remote Desktop Services wikipedia , lookup
Computer network wikipedia , lookup
Wireless security wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Network tap wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Deep packet inspection wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Transcript
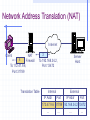
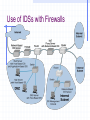
Firewall Categorization Methods Firewalls can be categorized by processing mode, development era, or intended structure Five processing modes that firewalls can be categorized by are: Packet filtering Application gateways Circuit gateways MAC layer firewalls Hybrids Firewalls Categorized by Development Generation First generation: static packet filtering firewalls Second generation: application-level firewalls or proxy servers Third generation: stateful inspection firewalls Fourth generation: dynamic packet filtering firewalls; allow only packets with particular source, destination and port addresses to enter Fifth generation: kernel proxies; specialized form working under kernel of Windows NT Packet Filters Either block or allow transmission of packets of information based on criteria such as port, IP address, and protocol Review the header, strip it off, and replace it with a new header before sending it to a specific location within the network Fundamental components of firewalls Viewing Header Contents The Use of Rules The Use of Rules Stateful Packet Filtering Dual-Homed Host Proxy Server Configuration Figure 8-3 Symmetric Encryption Example Cryptographic Algorithms Data Encryption Standard (DES): one of most popular symmetric encryption cryptosystems 64-bit block size; 56-bit key Adopted by NIST in 1976 as federal standard for encrypting non-classified information Triple DES (3DES): created to provide security far beyond DES Advanced Encryption Standard (AES): developed to replace both DES and 3DES Cryptographic Algorithms Asymmetric Encryption (public key encryption) Uses two different but related keys; either key can encrypt or decrypt message If Key A encrypts message, only Key B can decrypt Highest value when one key serves as private key and the other serves as public key Figure 8-4 Using Public Keys A Public Key Generated by PGP Network Address Translation (NAT) Used, by most firewalls, to shield a private network from outside interference Translates between private addresses inside a network and public addresses outside the network Done transparently (unnoticed by external computers) Internal IP addresses remain hidden Performed by NAT proxy servers Uses an address table to do translations Ex: a computer inside accesses a computer outside Change source IP address to its own address Change source port number to a unique number Used as an index to the original source IP address Performs reverse operations for response packets Network Address Translation (NAT) From 172.47.9.6, Port 31789 From 192.168.34.2, 1 Port 13472 2 Internet Client NAT Firewall Translation Table Server Host Internal External IP Addr Port IP Addr Port 172.47.9.6 31789 192.168.34.2 13472 … … … … Network Address Translation (NAT) Internet Client NAT 4 Firewall To 172.47.9.6, Port 31789 3 To 192.168.34.2, Port 13472 Translation Table Server Host Internal External IP Addr Port IP Addr Port 172.47.9.6 31789 192.168.34.2 13472 … … … … Tunneling Protocols Used with VPNs IPSec PPTP (Point-to-Point Tunneling Protocol) L2TP (Layer 2 Tunneling Protocol) PPP over SSL (Point-to-Point Protocol over Secure Sockets Layer) IPSec IPSec provides: Encryption of the data part of packets Authentication Encapsulation between two VPN hosts Two security methods (AH and ESP) Capability to work in two modes (transport and tunnel) PPTP Developed by Microsoft for granting VPN access to remote users over dial-up connections Uses Microsoft Point-to-Point Encryption (MPPE) to encrypt data Useful if support for older clients is needed Compatible with Network Address Translation (NAT) Replaced by L2TP L2TP Extension to PPP that enables dial-up users to establish a VPN connection to a remote access server Uses IPSec to encrypt data Incompatible with NAT but provides a higher level of encryption and authentication PPP Over SSL UNIX based method for creating VPNs Both combine existing tunnel system (PPP) with a way of encrypting data in transport (SSL) SSL Public key encryption system used to provide secure communications over the Web Detecting Unauthorized Access Intrusion Detection Systems (IDSs): Network-based IDSs Install IDS sensors on network circuits and monitor packets Reports intrusions to IDS Management Console Host-based IDSs Monitor all activity on the server as well as incoming server traffic Application-based IDSs Special form of host-based IDSs Monitor just one application, such as a Web server Techniques Used by IDSs Misuse detection Compares monitored activities with signatures of known attacks If an attack is recognized the IDS issues an alert and discards the packet Challenge: keep database current Anomaly detection Operates in stable computing environments Looks for major deviations from the “normal” parameters of network operation e.g., a large number of failed logins When detected, an alert is issued, packets discarded Problem: false alarms (valid traffic different from normal) Use of IDSs with Firewalls