* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Firewalls: An Effective Solution for Internet Security
Survey
Document related concepts
Airport security wikipedia , lookup
Cyberwarfare wikipedia , lookup
Information security wikipedia , lookup
Cyber-security regulation wikipedia , lookup
Network tap wikipedia , lookup
Security-focused operating system wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Wireless security wikipedia , lookup
Deep packet inspection wikipedia , lookup
Mobile security wikipedia , lookup
Computer security wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Unix security wikipedia , lookup
Transcript
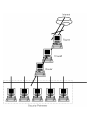
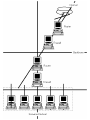
Previous screen 83-10-40 Firewalls: An Effective Solution for Internet Security E. Eugene Schultz Payoff Firewalls are an effective method of reducing the possibility of network intrusion by attackers. The key to successful firewall implementation is the selection of the appropriate system and regular maintenance. Introduction The Internet has presented a new, complex set of challenges that even the most sophisticated technical experts have not been able to solve adequately. Achieving adequate security is one of the foremost of these challenges. The major security threats that the Internet community faces are described in this article. It also explains how firewall— potentially one of the most effective solutions for Internet security—can address these threats, and it presents some practical advice for obtaining the maximum advantages of using firewalls. Internet Security Threats The vastness and openness that characterizes the Internet presents an extremely challenging problem—security. Although many claims about the number and cost of Internet-related intrusions are available, valid, credible statistics about the magnitude of this problem will not be available until scientific research is conducted. Exacerbating this dilemma is that most corporations that experience intrusions from the Internet and other sources do not want to make these incidents known for fear of public relations damage and, worse yet, many organizations fail to even detect most intrusions. Sources, such as Carnegie Mellon University's Computer Emergency Response Team, however, suggest that the number of Internet-related intrusions each year is very high and that the number of intrusions reported to CERT (which is one of dozens of incident response teams) is only the tip of the iceberg. No credible statistics concerning the total amount of financial loss resulting from securityrelated intrusions are available, but, judging by the amount of money corporations and government agencies are spending to implement Internet and other security controls, the cost must be extremely high. Many types of Internet security threats exist. One of the most serious methods is Internet protocol (IP) spoofing. In this type of attack, a perpetrator fabricates packet that bear the address of origination of a client host and sends these packets to the server for this client. The server acknowledges receiving these packets by returning packets with a certain sequence number. If the attacker can guess this packet sequence number and incorporate it into another set of fabricated packets that are then sent back to the server, the server can be tricked into setting up a connection with a fraudulent client. The intruder can subsequently use attack methods, such as use of trusted host relationships to intrude into the server machine. A similar threat is domain name service (DNS) spoofing. In this type of attack, an intruder subverts a host within a network, and sets up this machine to function as an apparently legitimate name server. The host then provides bogus data about host identities and certain network services, enabling the intruder to break into other hosts within the network. Session hijacking is another Internet security threat. The major tasks for the attacker who wants to hijack an ongoing session between remote hosts are locating an existing Previous screen connection between two hosts and fabricating packets that bear the address of the host from which the connection has originated. By sending these packets to the destination host, the originating host's connection is dropped, and the attacker picks up the connection. Another Internet security threat is network snooping, in which attackers install programs that copy packets traversing network segments. The attackers periodically inspect files that contain the data from the captured packets to discover critical log-on information, particularly user IDs and passwords for remote systems. Attackers subsequently connect to the systems for which they possess the correct log-on information and log on with no trouble. Attackers targeting networks operated by Internet service providers (ISPs) have made this problem especially serious, because so much information travels these networks. These attacks demonstrate just how vulnerable network infrastructures are; successfully attacking networks at key points, where router, firewalls, and server machines are located, is generally the most efficient way to gain information allowing unauthorized access to multitudes of host machines within a network. A significant proportion of attacks exploit security exposures in programs that provide important network services. Examples of these programs include sendmail, Network File System (NFS), and Network Information Service(NIS). These exposures allow intruders to gain access to remote hosts and to manipulate services supported by these hosts or even to obtain superuser access. Of increasing concern is the susceptibility of World Wide Web(WWW) services and the hosts that house these services to successful attack. The ability of intruders to exploit vulnerabilities in the hypertext transfer protocol(HTTP) and in Java, a programming language used to write WWW applications, seems to be growing at an alarming rate. Until a short time ago, most intruders have attempted to cover up indications of their activity, often by installing programs that selectively eliminated data from system logs. These also avoided causing system crashes or causing massive slowdowns or disruption. However, a significant proportion of the perpetrator community has apparently shifted its strategy by increasingly perpetrating denial-of-service attacks. For example, many types of hosts crash or perform a core dump when they are sent a packet internet groper or ping packet that exceeds a specified size limit or when they are flooded with synchronize (SYN) packets that initiate host-to-host connections. (Packet internet groper, or ping, is a service used to determine whether a host on a network is up and running.) These denial-of-service attacks make up an increasing proportion of observed Internet attacks. They represent a particularly serious threat, because many organizations require continuity of computing and networking operations to maintain their business operations. Not to be overlooked is another type of security threat called social engineering. Social engineering is fabricating a story to trick users, system administrators, or help desk personnel into providing information required to access systems. Intruders usually solicit password for user accounts, but information about the network infrastructure and the identity of individual hosts can also be the target of social engineering attacks. Internet Security Controls As previously mentioned, Internet security threats pose a challenge because of their diversity and severity. An added complication is an abundance of potential solutions. Encryption Encryption is a process of using an algorithm to transform cleartext information into text that cannot be read without the proper key. Encryption protects information stored in host machines and transmitted over networks. It is also useful in authentication users to hosts or networks. Although encryption is an effective solution, its usefulness is limited by the difficulty in managing encryption keys (i.e., of assigning keys to users and recovering Previous screen keys if they are lost or forgotten), laws limiting the export and use of encryption, and the lack of adherence to encryption standards by many vendors. One-Time Passwords Using one-time passwords is another way in which to challenge security threats. Onetime passwords captured while in transit over networks become worthless, because each password can only be used once. A captured password has already been used by the legitimate user who has initiated a remote log-on session by the time that the captured password can be employed. Nevertheless, one-time passwords address only a relatively small proportion of the total range of Internet security threats. They do not, for example, protect against IP spoofing or exploitation of vulnerabilities in programs. Installing fixes for vulnerabilities in all hosts within an Internet-capable network does not provide an entirely suitable solution because of the cost of labor, and, over the last few years, vulnerabilities have surfaced at a rate far faster than that at which fixes have become available. Firewalls Although no single Internet security control measure is perfect, the firewall has, in many respects, proved more useful overall than most other controls. Simply, a firewall is a security barrier between two networks that screens traffic coming in and out of the gate of one network to accept or reject connections and service requests according to a set of rules. If configured properly, it addresses a large number of threats that originate from outside a network without introducing any significant security liabilities. Because most organizations are unable to install every patch that CERT advisories describe, these organizations can nevertheless protect hosts within their networks against external attacks that exploit vulnerabilities by installing a firewall that prevents users from outside of the network from reaching the vulnerable programs in the first place. A more sophisticated firewall also controls how any connection between a host external to a network and an internal host occurs. Moreover, an effective firewall hides information, such as names and addresses of hosts within the network, as well as the topology of the network, which it is employed to protect. Firewalls can defend against attacks on hosts (including spoofing attacks), application protocols, and applications. In addition, firewalls provide a central method for administering security on a network and for logging incoming and outgoing traffic to allow for accountability of user actions and for triggering incident response activity if unauthorized activity occurs. Firewalls are typically placed at gateways to networks to create a security perimeter, as shown in Exhibit 1, primarily to protect an internal network from threats originating from an external one (particularly from the Internet). This scheme is successful to the degree that the security perimeter is not accessible through unprotected avenues of access. The firewall acts as a choke component for security purposes. Exhibit 1 displays routers that are located in front and in back of the firewall. The first router (shown above the firewall) is an external one used initially to route incoming traffic, to direct outgoing traffic to external networks, and to broadcast information that enables other network routers(as well as the router on the other side of the firewall) to know how to reach the host network. The other internal router (shown below the firewall) sends incoming packets to their destination within the internal network, directs outgoing packets to the external router, and broadcasts information on how to reach the internal network and the external router. This belt-andsuspenders configuration further boosts security by preventing the broadcast of information about the internal network outside of the network that the firewall protects. An attacker finding this information can learn IP addresses, subnets, servers, and other information, Previous screen which is useful in perpetrating attacks against the network. Hiding information about the internal network is much more difficult if the gate has only one router. A Typical Gate-Based Firewall Architecture Another way in which firewalls are deployed (though less frequently) is within an internal network—at the entrance to a subnet within a network—rather than at the gateway to the entire network. The purpose of this configuration(shown in Exhibit 2)is to segregate a subnetwork (a screened subnet) from the internal network at large, a wise strategy if the subnet has tighter security requirements than the rest of the security perimeter. This type of deployment more carefully controls access to data and services within a subnet than is otherwise allowed within the network. The gate-based firewall, for example, may allow file transfer protocol (FTP) access to an internal network from external sources. However, if a subnet contains hosts that store information, such as lease bid data or salary data, allowing FTP access to this subnet is less advisable. Setting up the subnet as a screened subnet may provide suitable security control, that is, the internal firewall that provides security screening for the subnet is configured to deny all FTP access, regardless of whether the access requests originated from outside or inside the network. A Screened Subnet Simply having a firewall, no matter how it is designed and implemented, does not necessarily protect against externally originated security threats. The benefits of firewalls depend to a large degree on the type used and how it is deployed and maintained. Using Firewalls Effectively To ensure that firewalls perform their intended function, it is important to choose the appropriate firewall and to implement it correctly. Establishing a firewall policy is also a critical step in securing a system, as is regular maintenance of the entire security structure. Choosing the Right Firewall Each type of firewall offers its own set of advantages and disadvantages. Combined with the vast array of vendor firewall products and the possibility of custom-building firewall, this task can be potentially overwhelming. Establishing a set of criteria for selecting an appropriate firewall is an effective aid in narrowing down the choices. One of the most important considerations is the amount and type of security needed. For some organizations with low to moderate security needs, installing a packet-filtering firewall that blocks out only the most dangerous incoming service requests often provides the most satisfactory solution, because the cost and effort are not likely to be great. For other organizations, such as banks and insurance corporations, packet-filtering firewalls do not generally provide the granularity and control against unauthorized actions usually needed for connecting customers to services that reside within a financial or insurance corporation's network. Additional factors, such as the reputation of the vendor, the arrangements for vendor support, the verifiability of the firewall's code (i.e., to confirm that the firewall does what the vendor claims it does), the support for strong authentication, the ease of administration, the ability of the firewall to withstand direct attacks, and the quality and extent of logging and alarming capabilities should also be strong considerations in choosing a firewall. The Importance of a Firewall Policy Previous screen The discussion to this point has focused on high-level technical considerations. Although these considerations are extremely important, too often security professionals overlook other considerations that, if neglected, can render firewalls ineffective. The most important consideration in effectively using firewalls is developing a firewall policy. A firewall policy is a statement of how a firewall should work—the rules by which incoming and outgoing traffic should be allowed or rejected. A firewall policy, therefore, is a type of security requirements document for a firewall. As security needs change, firewall policies must change accordingly. Failing to create and update a firewall policy for each firewall almost inevitably results in gaps between expectations and the actual function of the firewall, resulting in uncontrolled security exposures in firewall functionality. For example, security administrators may think that all incoming HTTP requests are blocked, but the firewall may actually allow HTTP requests from certain Internet protocol (IP) addresses, leaving an unrecognized avenue of attack. An effective firewall policy should provide the basis for firewall implementation and configuration; needed changes in the way that the firewall works should always be preceded by changes in the firewall policy. An accurate, up-to-date firewall policy should also serve as the basis for evaluating and testing a firewall. Security Maintenance Many organizations that employ firewalls feel a false sense of security once the firewalls are in place. Properly designing and implementing firewalls can be difficult, costly, and time consuming. It is critical to remember, however, that firewall design and implementation are simply the beginning point of having a firewall. Firewalls that are improperly maintained soon lose their value as security control tools. One of the most important facets of firewall maintenance is updating the security policy and rules by which each firewall operates. Firewall functionality invariably must change as new services and applications are introduced in(or sometimes removed from) a network. Undertaking the task of daily inspections of firewall logs to discover attempted and possibly successful attacks on both the firewall and the internal network that it protects should be an extremely high priority. Evaluating and testing the adequacy of firewalls for unexpected access avenues to the security perimeter and vulnerabilities that lead to unauthorized access to the firewall should also be a frequent, high-priority activity. Firewall products have improved considerably over the past several years, and are likely to continue to improve. Several vendor products, for example, are not network addressable, which makes breaking into these platforms by someone who does not have physical access to them virtually impossible. At the same time, however, recognizing the limitations of firewalls and ensuring that other appropriate Internet security controls are in place is becoming increasingly important because of such problems as third-party connections to organizations' networks that bypass gate-based security mechanisms altogether. Therefore, an Internet security strategy that includes firewalls in addition to host-based security mechanisms is invariably the most appropriate direction for achieving suitable levels of Internet security. Conclusion Internet connectivity can be extremely valuable to an organization, but it involves many security risks. A firewall is a key tool in an appropriate set of security control measures to protect Internet-capable networks. Firewalls can be placed at the gateway to a network to form a security perimeter around the networks that they protect or at the entrance to subnets to screen the subnets from the rest of the internal network. Previous screen Developing an accurate and complete firewall policy is the most important step in using firewalls effectively. This policy should be modified and updated as new applications are added within the internal network protected by the firewall and new security threats emerge. Maintaining firewalls properly and regularly examining the log data that they provide are almost certainly the most neglected aspects of using firewalls. Yet, these activities are among the most important in ensuring the defenses are adequate and that incidents are quickly detected and handled. Performing regular security evaluations and testing the firewall to identify any exploitable vulnerabilities or misconfiguration are also essential activities. Establishing a regular security procedure minimizes the possibility of system penetration by an attacker. Author Biographies E. Eugene Schultz E. Eugene Schultz, PhD, is a program manager at SRI International.