* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download 07-IPheader
Piggybacking (Internet access) wikipedia , lookup
Network tap wikipedia , lookup
TCP congestion control wikipedia , lookup
Airborne Networking wikipedia , lookup
Point-to-Point Protocol over Ethernet wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Computer network wikipedia , lookup
Distributed firewall wikipedia , lookup
Multiprotocol Label Switching wikipedia , lookup
SIP extensions for the IP Multimedia Subsystem wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Internet protocol suite wikipedia , lookup
Deep packet inspection wikipedia , lookup
Zero-configuration networking wikipedia , lookup
UniPro protocol stack wikipedia , lookup
Routing in delay-tolerant networking wikipedia , lookup
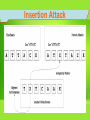
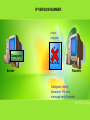
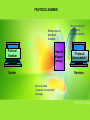
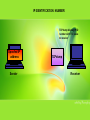
Examining IP Header Fields There are 2 types of attack towards Network Intrusion Detection System (NIDS): • Insertion Attacks - Where an attacker forces an NIDS to read information that isn’t valid, confusing it about what’s actually happening. • Evasion Attacks - When attackers slips entire packet past the NIDS by making them look invalid when they aren’t. Insertion Attack Evasion Attack INSERTION ATTACKS Attacker would to send Attacker send three packet the packet R E W T to which is R , O , and EWT obscure NIDS EO W RT Confuse about NIDS sees Ractually O E W T, but what’s Victim happening, host sees R E W T. NIDS accepted the packet O EVASION ATTACKS Attacker would to send the packet E WAttacker T to send two packet which is R, and E W T obscure NIDS E WRT Attacker slips entire packet past the NIDS by making them look invalid when they aren’t. Packet R NIDS sees E W T, but Victim host sees R E W T. 5 ways to examine IP header fields either being attack or not : 1. IP Version Number • There are two IP version numbers currently in use. There are IPv4 and IPv6. IPv4 is the most common and pervasive version number thus far. IPv6 is not yet in wide use in user networks. • The IP version field must be validated by a receiving host (receiver) and if not valid, the datagram is discarded and no error message is sent to the sending host (sender). • RFC 1121 protocol states that the datagram must be silently discarded if an invalid value is discovered. • Using IP version number, it is rather difficult to detect insertion attack unless the attacker is on the same network as the NIDS. IP VERSION NUMBER Invalid datagram Datagram Sender IP Version Number (RFC 1121 PROTOCOL) Receiver Datagram silently discarded. No error message sent to sender Cont.. 2. Protocol Number • Protocol number use the later version of network mapper (nmap) to scan a host for listening protocols. • This is done using the –sO option. • The target host is scanned for all 256 possibilities of protocols. Protocols are deemed listening when no Internet Control Message Protocol (ICMP) “protocol unreachable” message is returned. Cont.. 2. Protocol Number • There is a flaw in the logic use by nmap to discern listening protocols: • Nmap assumes that the absence of an ICMP “protocol unreachable” message means that the protocol is listening. Yet, conditions such as the scanned site blocking outbound ICMP messages prevent the nmap scanner from getting these messages. • Dropped packets, that might also cause the loss of packets and falsely influence nmap. Cont.. 2. Protocol Number The author of nmap tried to mitigate the flaws by: Nmap sends duplicate packets for each protocol to deal with the problem of packet loss by using Differentiated Services Byte and The Don’t Fragment (DF) Flag. If nmap get no ICMP “protocol unreachable” message back, it doesn’t assume all protocols are listening. Instead, it wisely assumes that the traffic is being “filtered” and reports this. PROTOCOL NUMBER Nmap scan a protocol number Protocol Number Network Mapper (nmap) Sender Receiver doesn’t support the protocol number “Protocol Unreachable” Receiver Receiver send “protocol unreachable” message Cont.. 3. IP Numbers • IP numbers are 32-bit fields. The source IP number is located in the 12th through 15th bytes offset of the IP header; the destination IP number is located in the 16th through 19th bytes offset of the IP header. • If users see an IP number entering their network that purports to be from their network, there is a misconfiguration problem with a host. Most likely, someone has crafted this packet and is spoofing an IP address in their range. Cont.. 3. IP Numbers • Users also should never see source IPs coming from the loopback address 127.0.0.1(identifies the local host), nor should not see any source IPs that fall in the Internet Assigned Numbers Authority (IANA) reserved private network numbers defined in RFC 1918. These address intended use is for local internal networks only. • The method use to prevent these problems: • – A packet-filtering device should shun this traffic. – Use decoy or spoofed source IP’s as a smokescreen. Users shouldn’t allow traffic with a broadcast destination IP address into or out of your network. Such destination addresses are typically used to quickly map other networks or use them as Smurf amplification sites. Cont.. 4. IP Identification Number • The IP identification value is found in bytes 4 and 5 offset of the IP header. For each new datagram that a host sends, it must generate a unique IP ID number. This value is normally incremented by 1, although some use an increment of 256, for each new datagram sent by the host. • The range for IP ID values is 1 through 65,535 because this is a 16bit field. When the maximum value of 65,535 is reached, it should wrap around and start again. Cont.. 4. IP Identification Number • If users see different “alleged” source IPs sending traffic to their network and that IPs appear to have a chronology of incrementing IP ID numbers, it is possible that the source IP are being spoofed. • The –vv option of TCPdump can be used to display the IP ID number along with the time-to-live (TTL) value. – Time-to-Live (TTL) - Number of hops/links which the packet may be routed over, decremented by most routers - used to prevent accidental routing loops IP Checksum IP IDENTIFICATION NUMBER TCPdump display IP ID number with TTL value to receiver Spoofed IP address Sender TCPdump Receiver Cont.. 4. IP Checksum • Checksums are used to ensure that data has not gotten corrupted from source to destination. • The IP checksum is found in the 10th and 11th bytes offset of the IP header. • The algorithm used for TCP/IP is to divide the data that being checksummed into 16-bit fields. Each 16-bit field has a 1’s complement operation done on it and all of these 1’s complement values are added. The final value is considered to be the checksum. Cont.. 4. IP Checksum • The IP checksum is validated by each router through which it passes from source to destination and finally is validated by the destination host as well. • Is the computed checksum does not agree with the one found in the datagram, the datagram is discarded silently. • The IP checksum is examined and recomputed for each hop on the way from source to destination. Intermediate routers validate the IP checksum, and if it is correct, the TTL value is decremented by 1. The IP header checksum must be recomputed to reflect this change in the IP header. The end