* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Lecture 1
Survey
Document related concepts
Multiprotocol Label Switching wikipedia , lookup
Backpressure routing wikipedia , lookup
IEEE 802.1aq wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Computer network wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Network tap wikipedia , lookup
Distributed firewall wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Wake-on-LAN wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Airborne Networking wikipedia , lookup
Deep packet inspection wikipedia , lookup
Transcript
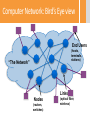
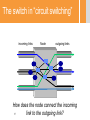
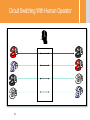
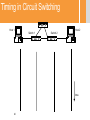
Introduction to Communication Networks –67594 Dr. Michael Schapira Rothberg A413 [email protected] Some of the slides were taken from Prof. Scott Shenker, UC Berkeley Administrative • Lectures on Sundays 10:00-11:45 (Michael) • Tutorials on Tuesdays and Thursdays 14:00-15:45 (Nir) • Tutorials are important! – Repeating material that was taught in the lectures – Introducing new subjects that complements the subjects in class. – Teaching mathematical material that will be needed both for lectures and homeworks. Homeworks and Grading • Four assignments: 30% – Mandatory – Each assignments 7.5% – Need average grade>54 to pass • Final exam: 70% – Depending on the number of assignments we end up with – Need grade>54 to pass Course Books • Computer Networking: A Top Down Approach (5th or 6th Edition) – J. Kurose, K. Ross • Computer Networks: A System approach (5th Edition) – L. L. Peterson, B. S. Davie • Network Algorithmics: An Interdisciplinary Approach to Designing Fast Networked Devices. G. Varghese, 2004. What Will You Learn? • Key concepts in networking – Different ways to route? – What is congestion control? • Domain-specific knowledge: how the Internet works – What does an IP packet look like? – How can a single typo bring down a third of the Internet? 5 Why is Networking Fascinating? • The Internet has had a tremendous impact • The Internet changed the networking paradigm • The design of the Internet presents interesting intellectual challenges • Many of these intellectual challenges remain unsolved 6 Impact • Internet changed the way we gather information – Web, search engines • Internet changed the way we relate to each other – Email, facebook, twitter • Which would you choose? – Computers without the Internet (standalone PCs) – Internet without computers (or really old ones) 7 Intellectual Challenges • Connecting two computers is easy – So why is designing the Internet hard? • Internet must cope with unprecedented scale, diversity and dynamic range – More about this later in lecture…. 8 Unsolved challenges • Security – Security of infrastructure – Security of users • Availability – Internet is very resilient – But availability is not sufficient for critical infrastructures • Evolution – It is too hard to change the Internet architecture 9 Quote from John Day (Internet Pioneer) There is a tendency in our field to believe that everything we currently use is a paragon of engineering, rather than a snapshot of our understanding at the time. We build great myths of spin about how what we have done is the only way to do it to the point that our universities now teach the flaws to students (and professors and textbook authors) who don't know better. 10 Computer Network’s Ultimate Goal Transmitting data between end-users Computer Network: Bird’s Eye view End Users (hosts, terminals, stations) “The Network” Links Nodes (routers, switches) (optical fiber, wireless) Networks Come at Different Sizes Internet: 2,038,600,000 Users (2010), 4.99M in Israel 13 Small Home/Office Network Diversity of End Users • • • • • • • • • • • • Cell phones Supercomputer clusters Tablets Televisions Gaming consoles Web cams Automobiles Sensing devices Picture frames Security systems Power grid …… 14 Diversity of Network Devices Links Interfaces Fibers Ethernet card Nodes Large router Wireless card Coaxial Cable Telephone switch 15 Diversity of (Application) Requirements • • • • • • • • Size of transfers Bidirectionality (or not) Latency sensitive (or not) Tolerance of jitter (or not) Tolerance of packet drop (or not) Need for reliability (or not) Multicast (or not) ….. 16 Computer Network vs. Distributed System • Computer network is the infrastructure and technologies needed to transmit data between hosts • Distributed system is the set of hosts using the computer network The network itself does not produce data (except control data to manage the network) Properties of Links • Delay (sometimes also called latency) – Propagation time for data sent along the link – Corresponds to the “length” of the link • Bandwidth (capacity) – Amount of data sent (or received) per unit time – Corresponds to the “width” of the link • Bandwidth-delay product: (BDP) – Amount of data that can be “in flight” at any time – Propagation delay × bits/time = total bits in link bandwidth 18 delay x bandwidth delay Throughput • Fraction of time link is busy transmitting – Often denoted by ρ – Also, called the utilization of the link • Ratio of arrival rate to bandwidth – Arrival: A bits/sec on average – Bandwidth: B bits/sec – Throughput = A/B 19 Speed of Light • Question: how long does it take light to travel from Jerusalem to New York? • Answer: – Distance Jerusalem New York: 9,164 km (great circle) – Traveling 300,000 km/s: 30.55 msec 20 Latency • Propagation Delay – Depends on distance, medium speed (e.g., 2/3 speed of light) • Transmission Time – Depends on the bandwidth of the link and line-card properties • Queuing Delay – Congestion within the network (competition) – Will be discussed later… • Either one-way, round-trip (depends on context) Examples - Single Link Bandwidth-Delay (BDP) Transmission Times Same city over slow link: – Bwdth~100mbps – Delay~.1msec – BDP ~ 10000bits ~ 1.25MBytes Cross-country over fast link: – Bwdth~10Gbps – Delay~10msec – BDP ~ 108bits ~ 12.5GBytes • 1500 byte packet over 14.4k modem: ~1 sec • 1500 byte packet over 10Gbps link: ~10-6sec 22 Examples – End to End • Question: how long does it take an Internet “packet” to travel from Jerusalem to New York? • Answer: – For sure 30.55 msec – Depends on: • The route the packet takes (could be circuitous!) • The propagation speed of the links the packet traverses – E.g., in optical fiber light propagates at about 2/3 C • The transmission rate (bandwidth) of the links (bits/sec) – and thus the size of the packet • Number of hops traversed (store-and-forward delay) • The “competition” for bandwidth the packet encounters (congestion). It may have to sit & wait in router queues. – In practice this boils down to 70 msec • Within Israel 10 msec 23 Dynamic Range of All Properties… • Round-trip times (delay/latency) from 10secs to seconds – 5 orders of magnitude • Data rates (bandwidth) from kbps to 100 Gbps – 8 orders of magnitude • Queueing delays in the network vary from 0 to seconds • ….. 24 Latency and Implications to Networking • Question: how many cycles does your PC execute before it can possibly get a reply to a message it sent to a New York web server? • Answer: – Round trip takes 140 msec – PC runs at (say) 3 GHz – 3,000,000,000 cycles/sec*0.14 sec = 420,000,000 cycles = Forever! – Communication feedback is always dated – Communication fundamentally asynchronous • Same even between machines that are directly connected (via a local area network or LAN)? – 0.2 ms = 200 sec = 600,000 cycles – Still a loooong time … and asynchronous Network Topologies Objective: Connectivity between each pair of end-users Network Topologies Objective: Connectivity between each pair of end-users Clique • Pros: Each pair of hosts has direct link. No competition on resources. • Cons: EXPENSIVE! (except in small networks) Network Topologies Objective: Connectivity between each pair of end-users Tree Pros: Very cheap, only N links required for N hosts. Cons: 1. Failure-prone (what happened if a single link fails?) 2.Coordination/Congestion resolution mechanisms are needed. Network Topologies Objective: Connectivity between each pair of end-users • In practice, most networks has some topology in between, trading off resilience and cost. • Some networks has a known topology – E.g. Telephony, local area networks, data centers • Other networks’ topology is not known – Each node only knows its neighbors – Learning the entire network is too time- and resourceconsuming – All control is done in a distributed manner Ad hoc Deployment • Can’t assume carefully managed deployment – Network must work without planning – Topologies are changed and are not regular – “Network of Networks” 30 More things to consider: Failures • Consider communication that uses 50 components – Assume each work correctly 99% of the time – What is likelihood communication fails? • Answer: success requires that they all function, so failure probability = 1 - (.99)50 ≈ 39.5% • Even if nodes are 99.9% reliable, failure probability is still close to 5%... • Must design the system to expect failure! 31 More things to consider: Greed • There are greedy people out there who want to: – Steal your financial information (bank, credit card, etc.) – Use your computer for attacks • There is a thriving underground economy for compromised computers and financial information 32 More things to consider: Malice • There are malicious people out there who want to: – Bring your system down and/or steal confidential data • When attacker is a nation-state, attacks are far harder to stop – Many defensive techniques involve stopping attacks that have been seen before – But33 nation-states can use new attack vectors Summary • Modern network are very diverse • Some of the design choices directly depends on the settings – E.g., the topology • Some of the design “choices” are consequences physics – E.g., asynchronous transmissions • Some of the design choices depends on user behavior – E.g. Security issue Example: Telephone Network • Alexander Graham Bell – 1876: Demonstrates the telephone at US Centenary Exhibition in Philadelphia Telephone network uses circuit switching • Establish: source creates circuit to destination – Nodes along the path store connection info – And reserve resources for the connection – If circuit not available: “Busy signal” • Transfer: source sends data over the circuit – No destination address, since nodes know path – Continual stream of data • Teardown: source tears down circuit when done 36 The switch in “circuit switching” incoming links Node outgoing links How does the node connect the incoming link to the outgoing link? 37 Circuit Switching With Human Operator 38 “Modern” switches • Almon Brown Strowger (1839 - 1902) – 1889: Invents the “girl-less, cuss-less” telephone system -- the mechanical switching system Timing in Circuit Switching Host 1 Switch 1 Switch 2 Host 2 time 40 Timing in Circuit Switching Host 1 Circuit Establishment Switch 1 Switch 2 Host 2 propagation delay between Host 1 and Switch1 time 41 Timing in Circuit Switching Host 1 Switch 1 Switch 2 Host 2 Transmission delay Circuit Establishment propagation delay between Host 1 and Switch1 time 42 Timing in Circuit Switching Host 1 Switch 1 Switch 2 Host 2 Transmission delay Circuit Establishment propagation delay between Host 1 and Switch1 time 43 Timing in Circuit Switching Host 1 Switch 1 Switch 2 Host 2 Transmission delay Circuit Establishment propagation delay between Host 1 and Switch1 propagation delay between Host 1 and Host 2 time 44 Timing in Circuit Switching Host 1 Switch 1 Switch 2 Host 2 Transmission delay propagation delay between Host 1 and Switch1 Circuit Establishment propagation delay between Host 1 and Host 2 Transfer Information time 45 Timing in Circuit Switching Host 1 Switch 1 Switch 2 Host 2 Transmission delay propagation delay between Host 1 and Switch1 Circuit Establishment propagation delay between Host 1 and Host 2 Transfer Information time Circuit Teardown 46 Sharing a link incoming links Node outgoing links How do the black and orange circuits share the outgoing link? 47 Circuit Switching: Multiplexing a Link – Each circuit allocated certain time slots time 48 • Frequency-division – Each circuit allocated certain frequencies frequency • Time-division time Time-Division Multiplexing/Demultiplexing Frames Slots = 0 1 2 3 4 5 0 1 2 3 4 5 • Time divided into frames; frames into slots • Relative slot position inside a frame determines to which conversation data belongs – E.g., slot 0 belongs to blue conversation • Requires synchronization between sender and receiver • Need to dynamically bind a slot to a conversation • If a conversation does not use its circuit capacity is lost! 49 Strengths of phone system • Predictable performance – Known delays – No drops • Easy to reason about • Supports a crucial service What about weaknesses? 50 Weakness #1: Not resilient to failure • Any failure along the path prevents transmission • Entire transmission has to be restarted • “All or nothing” delivery model 51 Weakness #2: Wastes bandwidth • Consider a network application with: – Peak bandwidth P – Average bandwidth A • How much does the network have to reserve for the application to work? – The peak bandwidth • What is the resulting level of utilization (average throughput)? – Ratio of A/P 52 Smooth vs Bursty Applications • Some applications have relatively small P/A ratios – Voice might have a ratio of 3:1 or so • Data applications tend to be rather bursty – Ratios of 100 or greater are common • Circuit switching too inefficient for bursty apps • Generally: – Don’t care about factors of two in performance – But when it gets to several orders of magnitude…. Weakness #3: Designed Tied to App • Design revolves around the requirements of voice • Not general feature of circuit switching – But definitely part of the telephone network design 54 Weakness #4: Setup Time • Every connection requires round-trip time to set up – Slows down short transfers 55 How to overcome these problems? • Paul Baran, “On Distributed Communications” (1964) – Distributed control – Message blocks (packets) – Store-and-forward delivery • Analyzed by Kleinrock – Statical multiplexing 56 Taxonomy of Communication Networks • Communication networks can be classified based on the way in which the nodes exchange information: Communication Network 57 Taxonomy of Communication Networks • Communication networks can be classified based on the way in which the nodes exchange information: Communication Network Broadcast Communication Network 58 Broadcast Communication Networks • Information transmitted by any node is received by every other node in the network – Usually only in LANs (Local Area Networks) • E.g., WiFi, Ethernet (classical, but not current) • E.g., lecture! • What problems does this raise? • Problem #1: limited range • Problem #2: coordinating access to the shared communication medium – Multiple Access Problem • Problem #3: privacy of communication 59 Taxonomy of Communication Networks • Communication networks can be classified based on the way in which the nodes exchange information: Communication Network Switched Communication Network 60 Broadcast Communication Network Taxonomy of Communication Networks • Communication networks can be classified based on the way in which the nodes exchange information: Communication Network Switched Communication Network Circuit-Switched Communication Network 61 Broadcast Communication Network Taxonomy of Communication Networks • Communication networks can be classified based on the way in which the nodes exchange information: Communication Network Switched Communication Network Circuit-Switched Communication Network 62 Broadcast Communication Network Packet-Switched Communication Network (Datagram Network) Packets / Datagrams • Payload (Body) – Data being transferred • Header – Instructions to the network for how to handle packet Header 63 Payload Datagram Packet Switching • Each packet is independently switched – Each packet header contains full destination address • No resources are pre-allocated (reserved) in advance 64 Timing of Datagram Packet Switching Host 1 Node 1 Packet 1 65 Node 2 propagation delay between Host 1 and Node 1 Host 2 Timing of Datagram Packet Switching Host 1 transmission time of Packet 1 at Host 1 66 Node 1 Packet 1 Node 2 propagation delay between Host 1 and Node 1 Host 2 Timing of Datagram Packet Switching Host 1 transmission time of Packet 1 at Host 1 Node 1 Packet 1 Host 2 Node 2 propagation delay between Host 1 and Node 1 Packet 1 processing delay of Packet 1 at Node 2 Packet 1 67 Timing of Datagram Packet Switching Host 1 transmission time of Packet 1 at Host 1 Node 1 Packet 1 Host 2 Node 2 propagation delay between Host 1 and Node 1 Packet 2 Packet 1 Packet 3 processing delay of Packet 1 at Node 2 Packet 2 Packet 3 Packet 1 Packet 2 Packet 3 68 Datagram Packet Switching Host C Host D Host A Node 1 Node 2 Node 3 Node 5 Host B Node 6 Node 4 69 Node 7 Host E Datagram Packet Switching Host C Host D Host A Node 1 Node 2 Node 3 Node 5 Host B Node 6 Node 4 70 Node 7 Host E Datagram Packet Switching Host C Host D Host A Node 1 Node 2 Node 3 Node 5 Host B Node 6 Node 4 71 Node 7 Host E Bursts • Packets arrive at the nodes in different patterns: time time – Bursty/smooth sources – Multiplexing different flows creates bursts Buffers to mitigate bursts • Due to bursts, sometime transient arrival rate is larger than transmission rate – Even if long-term arrival rate is smaller than transmission rate • One possibility: drop packets • Better approach: add buffers to save excess packets (until the bursts ends) – Even when buffers, sometimes packets are lost – Even with infinite buffers, sometimes packets are lost Basic Queueing Theory Terminology • Arrival process: how packets arrive – Average rate A – Peak rate P • Service process: transmission times – Average transmission time – For networks, function of packet size • W: average time packets wait in the queue/buffer – W for “waiting time” • L: average number of packets waiting in the queue – L for “length of queue” 74 Statistical Multiplexing Three Flows with Bursty Arrivals Data Rate 1 Time Data Rate 2 Capacity Time Data Rate 3 Time When Each Flow Gets 1/3rd of Capacity Data Rate 1 Frequent Overloading Time Data Rate 2 Time Data Rate 3 Time When Flows Share Total Capacity Time No Overloading Time Statistical multiplexing relies on the assumption that not all flows burst at the same time. Very similar to insurance, and has same failure case Time Another Take on “Stat Mux” • Assume time divided into frames – Frames divided into slots Frame • Flows generate packets during each frame Slots – Peak number of packets/frame P – Average number of packets/frame A • Single flow: must allocate P slots to avoid drops – But P might be much bigger than A – Very wasteful! • Use the “Law of Large Numbers”…. 79 Law of Large Numbers (~1713) • Consider any probability distribution – Can be highly variable, such as varying from 0 to P • Take N samples from probability distribution – In this case, one set of packets from each flow • Thm: the sum of the samples is very close to N×A – And gets percentage-wise closer as N increases • Sharing between many flows (high aggregation), means that you only need to allocate slightly more than average A slots per frame. – Sharing smooths out variations 80 So, if you were building a network…. • Which would you choose? – Circuit switched? – Packet-switched? 81