* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download MIS 4850 Systems Security
Survey
Document related concepts
Computer network wikipedia , lookup
Wireless security wikipedia , lookup
Network tap wikipedia , lookup
Parallel port wikipedia , lookup
Deep packet inspection wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Dynamic Host Configuration Protocol wikipedia , lookup
Remote Desktop Services wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
TCP congestion control wikipedia , lookup
Internet protocol suite wikipedia , lookup
Distributed firewall wikipedia , lookup
Transcript
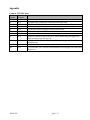
MIS 4850 Systems Security Understanding Firewalls Operation Exhibit 1 Figure 1: Access Control List (ACL) for INGRESS Filtering at a border firewall Trusted network 60.47.3.1 60.47.3.5 Untrusted network Firewall 60.47.3.2 60.47.3.9 1 2 3 4 5 6 7 8 9 10 11 12 If Source IP Address = 10.*.*.*, DENY [Private IP Address Range] If Source IP Address = 172.16.*.* to 172.31.*.*, DENY [Private IP Address Range] If Source IP Address = 192.168.*.*, DENY [Private IP Address Range] If source IP address = 60.47.*.*, DENY [internal address range] If TCP SYN=1 AND FIN=1, DENY [crafted attack packet] If Destination IP Address = 60.47.3.9 AND TCP Destination Port = 80 or 443, PASS If TCP SYN = 1 and ACK = 0, DENY [Attempt to open connection from the outside] If TCP Destination Port = 20, DENY If TCP Destination Port = 135 Through 139, DENY If TCP destination port = 513, DENY [UNIX rlogin without password] If UDP Destination Port = 69, DENY [Trivial FTP; no login necessary] DENY ALL The following questions are not related. 1. In Figure 1, some of the rules are redundant given the final Deny All. What are the redundant rules? Explain. ________________________________________________________________________ ________________________________________________________________________ ________________________________________________________________________ 2. What would be the downside of leaving redundant rules, like the ones that could be taken care of by the final Deny All, in the ACL? a. Leaving them could make the firewall pass some attack messages. b. Leaving them would add some burden on the firewall in terms of more processing time. c. None of the above 3. As the network administrator in charge of configuring the company’s firewall, you have to change the ACL in Figure 1 to add a rule that permits incoming requests to a particular computer (IP address 60.47.3.4) that hosts DNS service. (Note: the Appendix contains a list of TCP/UDP ports for common services). a. Write down the rule: _____________________________________________________ b. Where should that rule be inserted? Why? _____________________________________ 769859138 Page 1 / 5 4. What would be the possible consequences of making the rule you created when answering Question 3 (above) the very first rule of the ACL? a. This may decrease the likelihood of being attacked b. This may allow an attacker using IP spoofing with a Class A IP address in the private range to get to the corporate web server. c. This may allow an attacker using IP spoofing with a Class A IP address in the private range to get to target the DNS server. d. None of the above 5. As the network administrator in charge of configuring the company’s firewall, you have to change the ACL in Figure 1 to add a rule that allows packet destined to a an internal secured web server (HTTPS) that has IP address 60.47.3.7 to pass. (Note: the Appendix contains a list of TCP/UDP ports for common services). a. Write down the rule: ___________________________________________________ b. Where the rule should be inserted in the ACL? ______________________________ 6. As the network administrator in charge of configuring the company’s firewall, you have to change the ACL in Figure 1 to add a rule that says all SMTP traffic should pass through an SMTP application proxy which IP address is 60.47.3.10. a. Write down the rule: ___________________________________________________ b. Where the rule should be inserted in the ACL? ______________________________ 7. Which of the following would Rule 1 help prevent? a. Attacks initiated by any trusted network’s legitimate user targeting hosts in the trusted network or in the untrusted network. b. Attacks initiated by any outsider targeting hosts in the untrusted network. c. Attacks initiated by any outsider targeting hosts in the trusted network. d. None of the above. The following questions do not refer to the exhibit above. 8. Create an ACL (i.e. write down the rules) for Ingress Filtering in a case where the only messages allowed are those coming from external web servers or external email servers. (Note: the Appendix contains a list of TCP/UDP ports for common services). ________________________________________________________________________ ________________________________________________________________________ ________________________________________________________________________ ________________________________________________________________________ 9. Create an ACL (i.e. write down the rules) for Egress Filtering in a case where the only messages allowed are those destined to internal web servers or internal email servers. (Note: the Appendix contains a list of TCP/UDP ports for common services). ________________________________________________________________________ ________________________________________________________________________ ________________________________________________________________________ ________________________________________________________________________ 769859138 Page 2 / 5 Exhibit 2 Figure 2: Access Control List (ACL) for EGRESS Filtering at a border firewall Trusted network 60.47.3.1 60.47.3.5 Untrusted network Firewall 60.47.3.2 60.47.3.9 1 2 3 4 5 6 7 If Source IP Address = 10.*.*.*, DENY [Private IP Address Range] If Source IP Address = 172.16.*.* to 172.31.*.*, DENY [Private IP Address Range] If Source IP Address = 192.168.*.*, DENY [Private IP Address Range] If source IP address NOT = 60.47.*.*, DENY [not in internal address range] If ICMP Type = 8, PASS [allow outgoing echo messages] If Protocol = ICMP, DENY [drop all other outgoing ICMP messages] If TCP RST=1, DENY [do not allow outgoing resets; used in host scanning] 8 9 10 11 12 13 If source IP address = 60.47.3.9 AND TCP source port = 80 OR 443, PASS [public webserver] If TCP source port = 0 through 49151, DENY [well-known and registered ports] If UDP source port = 0 through 49151, DENY [well-known and registered ports] If TCP source port = 49152 through 65536, PASS [allow outgoing client connections] If UDP source port = 49152 through 65536, PASS [allow outgoing client connections] DENY ALL The following questions are not related one to another. 10. What rules prevent any host that provides service (other than web service) to respond to any external host? ________________________________________________________________________ ________________________________________________________________________ 11. Are rules 9 and 10 necessary? Why? ____________________________________________ 12. As the network administrator in charge of configuring the company’s firewall, you have to change the ACL in Figure 2 to add a rule that allows DNS response from the DNS server with IP address 60.47.3.4 to pass. (Note: the Appendix contains a list of TCP/UDP ports for common services). a. Write down the rule: ___________________________________________________ b. Where the rule should be inserted in the ACL? ______________________________ 13. As the network administrator in charge of configuring the company’s firewall, you have to change the ACL in Figure 2 to add a rule that allows packets from the internal secured web server (HTTPS) with IP address 60.47.3.7 to pass. (Note: the Appendix contains a list of TCP/UDP ports for common services). a. Write down the rule: ___________________________________________________ b. Where the rule should be inserted in the ACL? ______________________________ 769859138 Page 3 / 5 Exhibit 3 Internal Firewall Screening Router Firewall Internet Internet 172.18.9.x Subnet Demilitarized Zone (DMZ) Main Border Firewall Host Firewall Host Host Firewall Firewall Marketing Accounting Email Client on Server on Server on 172.18.5.x 172.18.7.x 172.18.6.x Subnet Subnet Subnet Public Webserver 60.47.3.9 SMTP Application Proxy Server 60.47.3.10 External DNS Server 60.47.3.4 HTTP Application Proxy Server 60.47.3.1 14. Name the host that will filter incoming and outgoing emails to make sure that they are safe:___________________________. Provide its IP address: ___________________ 15. NAT is usually implemented on firewalls or routers to hide the actual IP addresses of hosts to outsiders for security reasons. In the firewall architecture shown in Exhibit 3, what host should not be protected by NAT? (Circle all correct answers) a. The Marketing Client b. The Accounting server c. The public web server d. The external DNS server e. The SMTP proxy server 769859138 Page 4 / 5 Appendix Common TCP/UDP ports Port Primary Application Number Protocol 20 TCP FTP Data Traffic 21 TCP FTP Supervisory Connection. Passwords sent in the clear 22 TCP SSH (Secure Shell). Used for secure logins and file transfers (sftp) 23 TCP Telnet. Passwords sent in the clear 25 TCP Used for SMTP email transfer between email servers 53 TCP/UDP Domain Name System (DNS) 69 UDP Trivial File Transfer Protocol (TFTP). No login necessary 80 TCP Hypertext Transfer Protocol (HTTP). Used for transferring web pages b/w clients and non secure web servers. 110 TCP POP3 (Post Office Protocol Ver. 3). Used for retrieving emails b/w clients and mailservers 137-139 TCP NETBIOS service for P2P file sharing in older versions of Windows 443 TCP HTTP over SSL/TLS. Used for secured transfer of web pages b/w clients and web servers. 769859138 Page 5 / 5