* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download ppt - Purdue University :: Computer Science
Survey
Document related concepts
Process management (computing) wikipedia , lookup
Library (computing) wikipedia , lookup
Berkeley Software Distribution wikipedia , lookup
MTS system architecture wikipedia , lookup
Commodore DOS wikipedia , lookup
Plan 9 from Bell Labs wikipedia , lookup
Computer file wikipedia , lookup
File locking wikipedia , lookup
Burroughs MCP wikipedia , lookup
Transcript
CS252: Systems Programming
Ninghui Li
Based on Slides by Prof. Gustavo Rodriguez-Rivera
Topic 7: Unix Systems Overview
What is an Operating System
An Operating System (OS) is a layer of software
that sits in between the hardware and the user
programs.
Resource sharing: OS as Referee
Sharing among processes, users, etc
resource allocation, allocate processors, memory,
network bandwidth, disk space, etc.
Isolation: error in one application should not disrupt
another
Communication:
What is an Operating System
Masking Limitations: OS as Illusionist
Virtualization: provide an application with the illusion
of resources that are not physically present
E.g., illusion of dedicated processor, memory over
whole address space
Provides a convenient and flexible programming
environment than the underlying hardware
What is an Operating System
Providing Common Services: OS as Glue
Provide a set of common, standard services to
applications to simplify and standardize their design
File system hides details of storage
Network socket abstraction hides details of network
communication
GUI, devices, sensors, etc.
What is an Operating System
Window System – Graphical use interface
Standard Programs – Programs such as a web
browser, task manager, editors, compilers etc.
Common Libraries – Libraries common to all
programs running in the computer such as math
library, string library, window library, c library
etc.
It has to do all of the above in a secure and
reliable manner.
A Tour of UNIX
We will start by describing the UNIX operating system
(OS).
Understanding one instance of an Operating System will
help us understand other OSs such as Windows, Mac OS,
Linux etc.
UNIX is an operating system created in 1969 by Ken
Thompson, Dennis Ritchie, Brian Kernighan, and others at
AT&T Bell Labs.
UNIX was a successor of another OS called MULTICS
(Multiplexed Information and Computing Service) that
was more innovative but it had many problems.
UNIX was smaller, faster, and more reliable than
MULTICS.
A Tour of UNIX
UNIX was initially created to support typesetting
(edition of documents).
By having the programmers being the users
themselves of the OS (eat your own food), UNIX
became the robust, practical system that we know
today.
UNIX was written in “C” (95%) and assembly
language (5%).
This allowed UNIX to be ported to other machines
besides Digital Equipment (DEC)’s PDP11.
BSD UNIX
UNIX was a success in the universities.
Universities wanted to modify the UNIX sources
for experimentation do Berkeley created its own
version of UNIX called BSD-UNIX.
POSIX (Portable Operating System Interface) is
an organization that created the POSIX UNIX
standard to unify the different flavors of UNIX.
Sockets, FTP, Mail etc came from BSD UNIX.
Linux
GNU Project (1984, Richard Stallman)
Create “free” UNIX implementation
Produced GNU C compilers, and other programs
Lacks a kernel
Linux (1991, Linus Torvalds, kernel on 386)
Inspired by Minix (a POSIX-compliant OS
initially created by Andrew S. Tanenbaum for
educational purposes.
Other developers quickly joined
The UNIX File System
UNIX File System
UNIX has a hierarchical File System
Important directories
/ - Root Directory
/etc OS Configuration files
/etc/passwd – User information
/etc/groups – Group information
/etc/inetd.conf – Configuration of Internet Services (deamons)
/etc/rc.*/ - OS initialization scripts for different services.
Daemons – Programs running in the background
implementing a service. (Servers).
UNIX File System
/dev – List of devices attached to the computer
/usr – Libraries and tools
/usr/bin – Application programs such as grep, ls et
/usr/lib – Libraries used by the application programs
/usr/include – Include files (.h) for the libraries
/home – Home directories
Users
UNIX was designed as a multiuser system.
In a standalone machine, the database of users is in /etc/passwd .
When networked information system (NIS) is used,
$ ypcat passwd | grep ninghui
ninghui:##ninghui:116:116:,,,:/homes/ninghui:/usr/loca
l/bin/bash
Each line has the format:
login_name:passwordinfo:userid:groupid:,,,:homedir:shell
x indicates that the hashed password is stored elsewhere
(/etc/shadow)
userid: Every user has a different “USER ID” that is a
number that identifies the user uniquely in the system.
User ID 0 means root user
Users
ninghui:##ninghui:116:116:,,,:/homes/ninghui:/usr/lo
cal/bin/bash
login_name:x:userid:groupid:,,:homedir:shell
:groupid:
:,,,: Optionally other info
:homedir: Home directory of the user. The directory
where the user’s files are under
:shell: The login shell.
Users
Commands for users
adduser – Adds a new user
passwd – Change password.
There exist a special user called “root” with
special privileges.
Only root can modify files anywhere in the
system.
To login as root (superuser) use the command
“su”.
Only root can add users or reset passwords.
Groups
A “group” represents a group of users.
A user can belong to several groups.
The file /etc/group describes the different
groups in the system.
Yellow Pages
In some systems the password and group files is
stored in a server called “Yellow Pages” that
makes the management easier.
If your UNIX system uses yellow pages the group
and database are in a server. Use “ypcat”
ypcat group | grep cs252
cs252:*:10174:cs252,grr,ninghui,choi293,geh,jind,li2490,math
ewc,mishra63,svelagap,wang2842,hays1,cphrampu,fieldn
Also the passwd file can be in Yellow Pages:
File Systems
The storage can be classified from fastest to
slowest in the following
Information stored in microchips
(1) Registers (2) Cache (3) RAM
(4) Flash Memory and Solid State Drive (SSD)
Information stored on other physical medium
(5) Hard Disk Drives (HDD), electromagnetic
(6) CD/DVD, optical
(7) Tape
Remote: Network storage
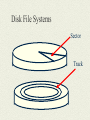
Disk File Systems on Hard Drive
Disk
The disk is an electromagnetic and
mechanical device that is used to store
information permanently.
The disk is divided into sectors, tracks and
blocks
Disk File Systems
Sector
Track
Disk File Systems
Block
A Block is the intersection between a sector
and a track
Disk File Systems
A head needs to be moved to read data from
another track.
Disks when formatted are divided into
sectors, tracks and blocks.
Disks are logically divided into partitions.
A partition is a group of blocks.
Each partition is a different file system.
UNIX Disk File System
Partition 1
Boot Super
Block Block
Partition 2
Inode List
Partition 3
Data Blocks
Disk File System
Each partition is divided into:
Boot Block – Has a piece of code that jumps to the OS
for loading.
Superblock – Contain information about the number of
data blocks in the partition, number of inodes, bitmap
for used/free inodes, and bitmap for used/free blocks,
the inode for the root directory and other partition
information.
Inode-list – It is a list of I-nodes. An inode has
information about a file and what blocks make the file.
There is one inode for each file in the disk.
Data Blocks – Store the file data.
I-node information
• An i-node represents a file in disk. Each i-node
contains:
1.
Flag/Mode
1.
2.
Owners
1.
3.
Creation time, Access Time, Modification Time.
Size
1.
5.
Userid, Groupid
Time Stamps
1.
4.
Read, Write, Execute (for Owner/Group/All) RWX RWX RWX
Size of file in bytes
Ref. Count –
1.
2.
Reference count with the number of times the i-node appears in a
directory (hard links).
Increases every time file is added to a directory. The file the i-node
represents will be removed when the reference count reaches 0.
I-node information
The I-node also contains a block index with the
blocks that form the file.
To save space, the block index uses indices of
different levels.
This benefits small files since they form the
largest percentage of files.
Small files only uses the direct and single-indirect
blocks.
This saves in space spent in block indices.
I-node information
Direct block –
Points directly to the data blocks. There are 12 of them in the
structure
Single indirect –
Points to a block that contains a table of 256 entry's, each is
the id of a data block. There are 3 single indirect blocks.
Double indirect –
Points to a block with table of 256 entries, each of which
then points to another table of 256
Triple Indirect
Points to a block which is a table of 256 entries which then
points to another block table of 256 that points to another
block of 256 bytes.
I-node Block Index
12 direct
blocks
…
3 single indirect
blocks
1 double indirect
1 triple indirect
I-node
…
I-node information
Assume 1KB block and 256 block numbers
in each index block.
Direct block = 12 * 1Kb = 12Kb
Single indirect = 3 * 256 * 1Kb = 768 Kb
Double indirect = 1 * 256 * 256 * 1Kb = 64
Mb
Triple indirect = 1 * 256 * 256 * 256 * 1Kb
= 16 Gb
I-node information
Most of the files in a system are small.
This also saves disk access time since small files
need only direct blocks.
1 disk access for the I-Node
1 disk access for the datablock.
An alternative to the multi-level block index is a
linked list. Every block will contain a pointer to
the next block and so on.
Linked lists are slow for random access.
What is in a Directory?
A directory is a file that contains a list of pairs
(file name, I-node number)
Each pair is also called a hard-link
A hard-link to an i-node increases the reference
count in the i-node.
When the reference-count reaches 0, the file is
removed.
UNIX Directories
33
CS5
26
Hard Links
Hard Links cannot cross partitions, that is, a directory
cannot list an I-node of a different partition.
A hard link can also be explicitly created as follows:
ln target-file [dir/]name-link
Creates a hard link to a target-file in dir (in current directory
when dir is missing.
This does not use a new i-node. It finds the i-node
number of the target-file, increases its reference count,
and store the pair (i-node-no, name-link) in directory
In some OSs, the reference count is also incremented
when the file is open. This prevents the file from being
removed while it is in use.
Soft-Links
Directories may also contain Soft-Links. Created using
ln –s target-file name-link
A soft-link adds to the current directory a pair of the form
(file name, a new i-node number)
A new file is created, the content of the file storing targetfile, where path may be an absolute or relative path in this or another
partition.
Soft-links can point to files in different partitions.
A soft-link does not keep track of the target file.
The target file’s i-node’s reference count does not increase.
If the target file is removed, the symbolic link becomes
invalid (dangling symbolic link).
File Ownership
The Group Id and owner’s User ID are
stored as part of the file information
Also the creation, modification, and access
time are stored in the file in addition to the
file size.
The time stamps are stored in seconds after
the Epoch (0:00, January 1st, 1970).
File Permissions
The permissions of a file in UNIX are
stored in the inode in the flag bits.
Use “ls –l” to see the permissions.
-rw-rw-r--rw-------rwxrwxr-x
-rw-rw-r-drwxr-sr-x
drwxr-sr-x
1
1
1
1
10
9
grr
grr
grr
grr
grr
grr
150
975
5924
124
512
512
Aug 29 1995 calendar
Mar 25 1999 cew.el
Jul 9 10:48 chars
Jul 9 10:47 chars.c
Oct 14 1998 contools
Oct 8 1998 contools-new
Permission Bits
The permissions are grouped into three groups:
User, Group, and Others.
rwx rwx rwx
User
Group
Other
Permission Bits
To change the persmissions of a file use the
command chmod.
chmod <u|g|o><+|-><r|w|x>
Where
<u|g|o> is the owner, group or others.
<+|-> Is to add or remove permissions
<r|w|x> Are read, write, execute permissions.
Example
Permission Bits Example
Make file “hello.txt” readable and writable
by user and group but only readable by
others
chmod
chmod
chmod
chmod
u+rw hello.txt
g+rw hello.txt
o+r hello.txt
o-w hello.txt
Scripts and Executable files should have the
executable bit set to be able to execute them.
chmod ugo+x myscript.sh
Permission Bits
Also you can change the permission bits all
at once using the bit representation in octal
USER GROUP OTHERS
RWX
RWX
RWX
110
110
100
- Binary
6
6
4
- Octal digits
chmod 664 hello.c
Basic Permissions Bits on Files
(Non-directories)
Read controls reading the content of a file
i.e., the read system call
Write controls changing the content of a file
i.e., the write system call
Execute controls loading the file in memory and execute
i.e., the execve system call
Topic 10: Operating System
42
CS5
26
Directory Bit
The Directory Bit in the file flags indicates
that the file is a directory
When an file is a directory the “x” flag
determines if the file can be listed or not.
If a file has its directory with “+x” but not
readable “-r” then the file will be accessible
but it will be invisible since the directory
cannot be listed.
Permission Bits on Directories
Read bit allows one to show file names in a directory
The execution bit controls traversing a directory
does a lookup, allows one to find inode # from file name
chdir to a directory requires execution
Write + execution control creating/deleting files in the directory
Deleting a file under a directory requires no permission on the file. Having
wx permission suffices.
Accessing a file identified by a path name requires execution to all
directories along the path
Topic 10: Operating System
44
CS5
26
Some Examples
What permissions are needed to access a
file/directory?
read a file:
write a file:
delete a file:
rename a file:
…
/d1/d2/f3
/d1/d2/f3
/d1/d2/f3
from /d1/d2/f3 to /d1/d2/f4
File/Directory Access Control is by System Calls
e.g., open(2), stat(2), read(2), write(2), chmod(2),
opendir(2), readdir(2), readlink(2), chdir(2), …
Topic 10: Operating System
45
CS5
26
UNIX Processes
Process’ Properties
A process has the following properties:
PID: Index in process table
Command and Arguments
Environment Variables
Current Dir
Owner (User ID)
Stdin/Stdout/Stderr
Use ps or top to see process information
Process ID
Uniquely identifies the processes among all live
processes.
The initial process (init process) has ID of 0.
The OS assigns the numbers in ascending order.
The numbers wrap around when they reach the
maximum and then are reused as long as there is no
live process with the same processID.
You can programmatically get the process id with
int getpid();
Command and Arguments
Every process also has a command that is
executing (the program file or script) and 0
or more arguments.
The arguments are passed to main.
int main(int argc, char **argv);
argc contains the number of arguments
including the command name.
argv[0] contains the name of the command
Printing the Arguments
printargs.c:
int main(int argc, char **argv) {
int i;
for (i=0; i<argc; i++) {
printf(“argv[%d]=\”%s\”\n”, i, argv[i]);
}
}
gcc –o printargs printargs.c
./printargs hello world
argv[0]=“./printargs”
argv[1]=“hello”
argv[2]=“world”
Environment Variables
It is an array of strings of the form A=B that is
inherited from the parent process.
Some important variables are:
PATH=/bin:/usr/bin:. Stores the list of directories
that contain commands to execute.
USER=<login> Contains the name of the user
HOME=/homes/grr Contains the home directory.
You can add Environment variables settings in .login or
.bashrc and they will be set when starting a shell
session.
Environment Variables
To set a variable from a shell use
export A=B
Example: Add a new directory to PATH
export PATH=$PATH:/newdir
Printing Environment
To print environment from a shell type
“env”.
lore 24 % env
USER=grr
LOGNAME=grr
HOME=/homes/grr
PATH=/opt/csw/bin:/opt/csw/gcc3/bin:/p/egcs1.1b/bin:/u/u238/grr/Orbix/bin:/usr/local/gnu:/p/srg/bin
:/usr/ccs/bin:/usr/local/bin:/usr/ucb:/bin:/usr/bin:/usr
/hosts:/usr/local/X11:/usr/local/gnu:.
MAIL=/var/mail/grr
SHELL=/bin/tcsh
TZ=US/East-Indiana
…
Printing Environment from a Program
Can access environment variables through the
“char ** environ” variable in C.
environ points to an array of strings of the form
A=B and ends with a NULL entry.
extern char **environ;
int main(int argc, char **argv) {
int i=0;
while (environ[i]!=NULL) {
printf(“%s\n”,environ[i]);
i++;
}
}
Current Directory
Every process also has a current directory.
The open file operations such as open() and
fopen() will use the current directory to resolve
relative paths.
If the path does not start with “/” then a path is
relative to the current directory.
/etc/hello.c – Absolute path
hello.c – Relative path.
To change the directory use “cd dir” in a shell or
chdir(dir) inside a program
Stdin/Stdout/Stderr/Redirection
Also a process inherits from the parent a
stdin/stdout and stderr.
They are usually the keyboard and the terminal but
they can be redirected.
Example:
command < in.txt
> out.txt
2> err.txt
// redirect stdin
// redirect stdout
// redirect stderr
Redirection of stdin/stdout/stderr
command >> out
Append output of the command into out.
command > out.txt 2> err.txt
Redirect stdout and stderr.
command > out.txt 2>&1
Redirect both stderr and stdout to file out.txt
PIPES
In UNIX you can connect the output of a
command to the input of another using
PIPES.
Example:
ls –al | sort
Lists the files in sorted order.
Review
Understand the effect of redirecting and
using pipes.
Understand the concepts of I nodes,
directories, and hard and soft links
Understanding permission bits, arguments,
environments, pipes