* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Lecture 1 - Intro
Survey
Document related concepts
Remote Desktop Services wikipedia , lookup
Wireless security wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Wake-on-LAN wikipedia , lookup
TCP congestion control wikipedia , lookup
Distributed firewall wikipedia , lookup
Computer network wikipedia , lookup
Network tap wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Deep packet inspection wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Airborne Networking wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Internet protocol suite wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Transcript
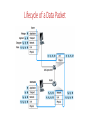
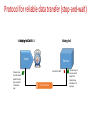
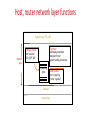
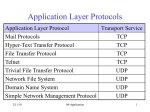
Modern Communication Networks Amr El Mougy [email protected] C7.207 Course Objectives 1. Strengthen your foundation of networking 2. Build your knowledge of the latest advances in networks 3. Introduce the concept of intelligence in networks 4. Empower your research skills Grading Policy Final 40% Research Reports 40% Mid-term 20% Course Outline 1. Overview of the basics of networking 2. Taxonomy of the types of networks 3. Advanced networking tools 4. Intelligence in networking (context-awareness and ubiquitous computing) 5. Advanced topics: • Software-defined networks • Cloud computing • Internet of Things • Social networks • Big data • Security and privacy Important Note • These slides are not meant to be comprehensive lecture notes! They are only remarks and pointers. The material presented here is not sufficient for studying for the course • Your main sources for studying are: • Research papers • your own lecture notes Internet Access Mobile network PC Global ISP server wireless laptop cellular handheld Home network Regional ISP Institutional network access points wired links router 1-8 Introduction 2 Internet Traffic • Global IP traffic will reach 1.1 Zettabytes per year by 2016, or 88.4 exabytes per month • An increase of 5 –fold over the last 5 years • An increase of 3 folds is expected by 2019 • Wireless and mobile traffic makes up 54% of global traffic • By 2019, two thirds of global traffic will be generated by non-PC devices (welcome to the IoT) Protocol Stack Lifecycle of a Data Packet Home Networks to/from cable headend Cable/ DSL modem router/ firewall Ethernet wireless laptops wireless access point Application Layer Creating a network app Write programs that • run on (different) end systems • communicate over network • e.g., web server software communicates with browser software application transport network data link physical No need to write software for network-core devices • Network-core devices do not run user applications • applications on end systems allows for rapid app development, propagation Application Architectures • Client-server • Peer-to-peer (P2P) • Hybrid of client-server and P2P application transport network data link physical application transport network data link physical What transport service does an app need? Data loss • some apps (e.g., audio) can tolerate some loss • other apps (e.g., file transfer, telnet) require 100% reliable data transfer Timing • some apps (e.g., Internet telephony, interactive games) require low delay to be “effective” Throughput • some apps (e.g., multimedia) require minimum amount of throughput to be “effective” • other apps (“elastic apps”) make use of whatever throughput they get Security • Encryption, data integrity, … Transport service requirements of common apps Application Data loss Throughput Time Sensitive file transfer e-mail Web documents real-time audio/video no loss no loss no loss loss-tolerant no no no yes, 100’s msec stored audio/video interactive games instant messaging loss-tolerant loss-tolerant no loss elastic elastic elastic audio: 5kbps-1Mbps video:10kbps-5Mbps same as above few kbps up elastic yes, few secs yes, 100’s msec yes and no Example of Application Protocols HTTP: hypertext transfer protocol • Web’s application layer protocol • client/server model • client: browser that requests, receives, “displays” Web objects • server: Web server sends objects in response to requests PC running Explorer Server running Apache Web server Mac running Navigator HTTP Messages request line (GET, POST, HEAD commands) Request Message GET /somedir/page.html HTTP/1.1 Host: www.someschool.edu User-agent: Mozilla/4.0 header Connection: close lines Accept-language:fr Carriage return, line feed indicates end of message status line (protocol, status code, status phrase) Response Message data, e.g., requested HTML file header lines (extra carriage return, line feed) HTTP/1.1 200 OK Connection close Date: Thu, 06 Aug 1998 12:00:15 GMT Server: Apache/1.3.0 (Unix) Last-Modified: Mon, 22 Jun 1998 …... Content-Length: 6821 Content-Type: text/html data data data data data ... Domain Name System (DNS) Root DNS Servers com DNS servers yahoo.com DNS servers amazon.com DNS servers org DNS servers pbs.org DNS servers edu DNS servers poly.edu umass.edu DNS servers DNS servers Client wants IP for www.amazon.com; 1st approx: • client queries a root server to find com DNS server • client queries com DNS server to get amazon.com DNS server • client queries amazon.com DNS server to get IP address for www.amazon.com root DNS server DNS name resolution example 2 • Host at cis.poly.edu wants IP address for gaia.cs.umass.edu 3 TLD DNS server 4 5 iterated query: contacted server replies with name of server to contact “I don’t know this name, but ask this server” local DNS server dns.poly.edu 1 8 7 6 authoritative DNS server dns.cs.umass.edu requesting host cis.poly.edu gaia.cs.umass.edu Transport Layer Transport vs. network layer • network layer: logical communication between hosts • transport layer: logical communication between processes • relies on, enhances, network layer services Household analogy: 12 kids sending letters to 12 kids • processes = kids • app messages = letters in envelopes • hosts = houses • transport protocol = Ann and Bill • network-layer protocol = postal service Internet transport layer protocols All Protocols do multiplexing/demultiplexing Reliable, in-order delivery (TCP) • congestion control • flow control • connection setup Unreliable, unordered delivery (UDP) • no-frills extension of “best-effort” IP services not available: • delay guarantees • bandwidth guarantees application transport network data link physical network data link physical network data link physical network data link physicalnetwork network data link physical data link physical network data link physical application transport network data link physical Protocol for reliable data transfer (stop-and-wait) Waiting for 1 0 1NAK 0 Waiting for for ACKCall or 0 Waiting Sender Transport Layer at sender accepts packet from App Layer and sends it to Network Layer Receiver Send ACK or NAK 0 Errors and Loss Transport Layer at receiver extracts packet from Network Layer and delivers it to App Layer TCP Flow Control • receiver side of TCP connection has a receive buffer: (currently) application TCP data IP unused buffer (in buffer) process datagrams space rwnd RcvBuffer flow control sender won’t overflow receiver’s buffer by transmitting too much, too fast app process may be slow at reading from buffer receiver: advertises unused buffer space by including rwnd value in segment header sender: limits # of unACKed bytes to rwnd • speed-matching service: matching send rate to receiving application’s drain rate • guarantees receiver’s buffer doesn’t overflow TCP Congestion Control • Sliding Window Protocol • Sender maintains a congestion window (cwnd), in addition to the receiver’s window (rwnd) advertised in ACK • Allowed-window = min(cwnd, rwnd) • If no congestion: Allowed-window = rwnd • Packet loss is interpreted as congestion occurrence: reduce congestion window size. Network Layer Two Key Network-Layer Functions • forwarding: move packets from router’s input to appropriate router output • routing: determine route taken by packets from source to dest. • routing algorithms analogy: routing: process of planning trip from source to dest forwarding: process of getting through single interchange Datagram networks • no call setup at network layer • routers: no state about end-to-end connections • no network-level concept of “connection” • packets forwarded using destination host address • packets between same source-dest pair may take different paths application transport network data link 1. Send data physical application transport 2. Receive data network data link physical Host, router network layer functions Transport layer: TCP, UDP Network layer IP protocol •addressing conventions •datagram format •packet handling conventions Routing protocols •path selection •RIP, OSPF, BGP forwarding table ICMP protocol •error reporting •router “signaling” Link layer physical layer IP addresses: how to get one? Q: How does a host get IP address? • hard-coded by system admin in a file • Windows: control-panel->network->configuration->tcp/ip->properties • UNIX: /etc/rc.config • DHCP: Dynamic Host Configuration Protocol: dynamically get address from as server • “plug-and-play” 4-32 Graph Abstraction • Graph: G = (N,E) • N: set of nodes (routers) = { u, v, w, x, y, z } • E: set of edges (links)= { (u,v), (u,x), (v,x), (v,w), (x,w), (x,y), (w,y), (w,z), (y,z) } (Links are bi-directional) • Each link is associated with a cost value (can represent delay, distance,..) • Cost of a path (x1,x2 ,….,xn ) = c(x1 ,x2) + c(x2 ,x3) +…..+ c(xn-1 ,xn ) • Routing algorithm objective: • Find path with minimum cost between sender and receiver Routing Algorithms Classification • Global • Least-cost path is calculated using complete, global knowledge about the network • All routers have complete graph (topology, costs) • “Link state” algorithms (OSPF, open shortest path first) • Decentralized • Calculations are carried out in an iterative, distributed manner. • Router knows link costs to physically connected adjacent nodes • “Distance vector” algorithms (RIP, Routing Information Protocol) 1-34 How does Data Travel? • At the Transport Layer: TCP and UDP protocols. Primary function is multiplexing and demultiplexing. TCP also establishes end-to-end logical connections • At the Network Layer (L3): IP protocols provides addressing (IP addresses are unique but dynamic) • At the Data Link Layer (L2): protocols provide access control plus MAC addressing (MAC addresses are unique and static) IP Addresses Vs. MAC Addresses • IP Address xxxxxxxx xxxxxxxx xxxxxxxx xxxxxxxx 223 191 056 008 • MAC Address xxxxxxxx xxxxxxxx xxxxxxxx xxxxxxxx xxxxxxxx xxxxxxxx 1C 22 F3 D1 42 A9 How does data travel? DNS Server 68.87.71.226 GUC 68.80.2.0/24 Bob 00:16:D3:23:63:8A ISP 68.80.0.0/13 00:22:6B:45:1F:1B 68.85.2.1 Bob wishes to retrieve a page from www.google.com Bob has just booted up the computer www.google.com 68.233.169.105 Google 68.233.160.0/19 Data Link Layer Link Layer Functions • Framing • Medium Access Control (MAC) • Reliable delivery • Flow control • Error detection and correction Medium Access Control (MAC) • Can be classified in 3 main categories: - Channel partitioning - Random Access - Taking-turns Channel Partitioning • Divides resources evenly • Eliminates collisions • Not very flexible • May waste resources if they are not needed by the device Random Access • Each node transmits at the full rate, R, of the channel • Collisions cannot be avoided • Upon collision: - Wait for random period of time - Retransmit frame ALOHA and Slotted ALOHA • ALOHA: • Slotted ALOHA: - Nodes may transmit whenever they want - All nodes are synchronized - Upon detecting a collision, either retransmit immediately or wait for one frame time - Nodes can only transmit at beginning of a slot - Upon a collision, the node will retransmit in the next slot with probability p Carrier Sense Multiple Access (CSMA) • Nodes employ carrier sensing before transmission • Collisions occur if two nodes start transmitting at the same time • Upon collision detection, nodes stop transmitting the rest of the packet • Collisions are caused by channel propagation delay Carrier Sense Multiple Access (CSMA)