* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download IEEE 802.11 based WLANs
Survey
Document related concepts
Power over Ethernet wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Airborne Networking wikipedia , lookup
Computer network wikipedia , lookup
Network tap wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Deep packet inspection wikipedia , lookup
IEEE 802.1aq wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Cellular network wikipedia , lookup
Wireless security wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Transcript
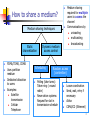
IEEE 802.11 Wireless Local Area Networks (WLANs) 802.11 WLANs - Outline 801.11 bands and layers Link layer Media access layer frames and headers CSMA/CA Physical layer frames modulation Frequency hopping Direct sequence Infrared Security Implementation 2 How to share a medium? Medium sharing techniques Static channelization FDMA,TDMA, CDMA Uses partition medium Dedicated allocation to users Examples: Satellite transmission Cellular Telephone Dynamic medium access control Scheduling Medium sharing required for multiple users to access the channel Communications by unicasting multicasting broadcasting Random access (contention) Polling (take turns): Token ring (=round robin) Reservation systems: Request for slot in transmission schedule Loose coordination Send, wait, retry if necessary Aloha CSMA/CD (Ethernet) 3 MAC Techniques - overview Contention Medium is free for all A node senses the free medium and occupies it as long as data packet requires it Example: Ethernet (CSMA/CD), IEEE 802.3 Token ring gives everybody a turn reservation time depends on token holding time (set by network operator) for heavy loaded networks Example: Token Ring/IEEE 802.5, Token Bus/IEEE 802.4, FDDI Reservation (long term) link reservation for multiple packets Example: schedule a time slot: GSM using TDMA 4 How ring-network works A node functions as a repeater A only destination copies frame to it, C A all other nodes have to discarded B transmits frame the frame addressed to A Unidirectional link A B C C ignores frame A C A A copies frame B A A B C A B C absorbs returning frame 5 Token ring A ring consists of a single or dual (FDDI) cable in the shape of a loop. Ring reservation supervised by rotating token. Each station is only connected to each of its two nearest neighbors. Data in the form of packets passes around the ring from one station to another in uni-directional way. Advantages : (1) Access method supports heavy load without degradation of performance because the medium is not shared. (2) Several packets can simultaneous circulate between different pairs of stations. Disadvantages: (1) Complex management (2) Re-initialization of the ring whenever a failure occurs 6 How bus-network works In a bus network, one node’s transmission traverses the entire network and is received and examined by every node. The access method can be : (1) Contention scheme : multiple nodes attempt to access bus; only one node succeed at a time (e.g. CSMA/CD in Ethernet) (2) Round robin scheme : a token is passed between nodes; node holding the token can use the bus (e.g.Token bus) Advantages: (1) Simple access method C D A B (2) Easy to add or remove D stations term term Disadvantages: (1) Poor efficiency with high network load (2) Relatively insecure, due to 7 the shared medium term: terminator impedance Selecting a Medium Access Control Applications: What type of traffic? Voice streams? Steady traffic, low delay/jitter Data? Short messages? Web page downloads? Enterprise or consumer market? Reliability, cost Scale: How much traffic can be carried? How many users can be supported? Examples: Design MAC to provide wireless DSL-equivalent access for rural communities Design MAC to provide Wireless-LAN-equivalent access to mobile users (user in car travelling at 130 km/hr) 8 Wireless LAN standard requirements Wireless channel is unreliable error control security/secrecy Stations movable and may be operated while moved addressing and association procedures interconnections (roaming) Wireless channel is also the reason why access method for 802.11 is called as CSMA/CA and not CSMA/CD (Collisions can not be avoided) CSMA/CA: Carrier Sense Multiple Access/Collision Avoidance CSMA/CD: Carrier Sense Multiple Access/Collision Detection 9 IEEE 802.11 defines physical (PHY), logical link (LLC) and media access control (MAC) layers for wireless local area networks 802.11 networks can work as Network basic service set (BSS) LLC MAC extended service set (ESS) FHSS DSSS IR PHY BSS can also be used in ad-hoc networking 802.xx IEEE 802.11 Architecture DS, ESS LLC: Logical Link Control Layer MAC: Medium Access Control Layer PHY: Physical Layer FHSS: Frequency hopping SS DSSS: Direct sequence SS SS: Spread spectrum IR: Infrared light BSS: Basic Service Set ESS: Extended Service Set AP: Access Point DS: Distribution System ad-hoc network 10 BSS and ESS Defined Basic Service Set (BSS) Basic (independent) service set (BSS) Extended service set (ESS) Group of stations that coordinate their access using a given instance of MAC Located in a Basic Service Area (BSA) Stations in BSS can communicate with each other Distinct collocated BSS’s can coexist Extended Service Set (ESS) Multiple BSSs interconnected by Distribution System (DS) Each BSS is like a cell and stations in BSS communicate with an Access Point (AP). Gateway operation: Portals attached to DS provide access to Internet BSSs may overlap, be physically disjoint, or they may be collocated (one BSS may use several antennas) 11 IEEE 802-series of LAN standards 802 standards free to download from http://standards.ieee.org /getieee802/portfolio.html hub stations hub stations hub stations hub router server Demand priority: A round-robin (see token rings-later) arbitration method to provide LAN access based on message priority level DQDB: Distributed queue dual buss, see PSTN lecture 2 12 The IEEE 802.11 and supporting LAN Standards IEEE 802.2 Logical Link Control (LLC) OSI Layer 2 (data link) MAC IEEE 802.3 IEEE 802.4 IEEE 802.5 IEEE 802.11 Carrier Token Token Wireless Sense Bus Ring a b g bus star PHY OSI Layer 1 (physical) ring See also IEEE LAN/MAN Standards Committee Web site http://www.ieee802.org/ 13 802.11 WLAN technologies IEEE 802.11 standards and rates IEEE 802.11 (1997) 1 Mbps and 2 Mbps (2.4 GHz band ) [FH, DS] IEEE 802.11b (1999) 11 Mbps (2.4 GHz band) = Wi-Fi [QPSK] IEEE 802.11a (1999) 6, 9, 12, 18, 24, 36, 48, 54 Mbps (5 GHz band) [OFDM] IEEE 802.11g (2001 ... 2003) up to 54 Mbps (2.4 GHz) backward compatible to 802.11b [OFDM] IEEE 802.11 networks work on license free Industrial, Science, Medicine (ISM) bands: 26 MHz 902 EIRP power in Finland 928 83.5 MHz 2400 2484 100 mW 200 MHz 5150 5350 255 MHz 5470 200 mW indoors only 5725 f/MHz 1W EIRP: Effective Isotropically Radiated Power - radiated power measured immediately after antenna Equipment technical requirements for radio frequency usage defined in ETS 300 328 14 Other WLAN technologies High performance LAN or HiperLAN (ETSI-BRAN EN 300 652) in the 5 GHz ISM version 1 up to 24 Mbps version 2 up to 54 Mbps HiperLAN provides also QoS for data, video, voice and images Bluetooth range up to 100 meters only (cable replacement tech.) Bluetooth Special Interest Group (SIG) Operates at max of 740 kbps at 2.4 GHz ISM band Applies fast frequency hopping 1600 hops/second Can have serious interference with 802.11 2.4 GHz range network 15 IEEE 802.11 Mobility Standard defines the following mobility types: No-transition: no movement or moving within a local BSS BSS-transition: station movies from one BSS in one ESS to another BSS within the same ESS ESS-transition: station moves from a BSS in one ESS to a BSS in a different ESS (continuos roaming not supported) Especially: 802.11 don’t support roaming with GSM! - Address to destination mapping - seamless integration of multiple BSS ESS 1 ESS 2 16 802.11 Logical architecture 802.xx LLC provides addressing and data link control MAC provides Network access to wireless medium LLC CSMA/CA MAC Priority based access (802.12) FHSS DSSS IR PHY joining the network authentication & privacy Services Station service: Authentication, privacy, MSDU* delivery Distributed system: Association**, participates to data distribution Three physical layers (PHY) FHSS: Frequency Hopping Spread Spectrum (SS) CSMA/CA: Carrier Sense Multiple Access DSSS: Direct Sequence SS with Collision Avoidance LLC: Logical Link Control Layer IR: Infrared transmission *MSDU: MAC service data unit ** with an access point in ESS or BSS MAC: Medium Access Control Layer PHY: Physical Layer FH: Frequency hopping DS: Direct sequence IR: Infrared light 17 802.11 DSSS DSSS-transmitter Supports 1 and 2 Mbps data transport, uses BPSK and QPSK modulation Uses 11 chips Barker code for spreading - 10.4 dB processing gain Defines 14 overlapping channels, each having 22 MHz channel bandwidth, from 2.401 to 2.483 GHz Power limits 1000mW in US, 100mW in EU, 200mW in Japan Immune to narrow-band interference, cheaper hardware PPDU:Baseband Data Frame Unit, BPSK: Binary Phase Shift Keying, QPSK: Quadrature PSK DSSS: Direct Sequence Spread Spectrum, PN:Pseudo Noise 18 802.11 FHSS Supports 1 and 2 Mbps data transport and applies two level - GFSK modulation* (Gaussian Frequency Shift Keying) 79 channels from 2.402 to 2.480 GHz ( in U.S. and most of EU countries) with 1 MHz channel space 78 hopping sequences with minimum 6 MHz hopping space, each sequence uses every 79 frequency elements once Minimum hopping rate 2.5 hops/second Tolerance to multi-path, narrow band interference, security Low speed, small range due to FCC TX power regulation (10mW) * f f c f , f nom 160 kHz 19 26 MHz 802.11a 902 928 83.5 MHz 2400 2484 200 MHz 5150 5350 255 MHz 5470 5725 f/MHz Operates at 5 GHz band Supports multi-rate 6 Mbps, 9 Mbps,… up to 54 Mbps Uses Orthogonal Frequency Division Multiplexing (OFDM) with 52 subcarriers, 4 us symbols (0.8 us guard interval) Applies inverse discrete Fourier transform (IFFT) to combine multicarrier signals to single time domain symbol 20 IEEE 802.11a rates and modulation formats Data Rate Coded bits per Code bits per Data bits per sub-carrier OFDM symbol OFDM symbol 1/2 1 48 24 BPSK 3/4 1 48 36 12 QPSK 1/2 2 96 48 18 QPSK 3/4 2 96 72 24 16QAM 1/2 4 192 96 36 16QAM 3/4 4 192 144 48 64QAM 2/3 6 288 192 54 64QAM 3/4 6 288 216 Modulation Coding Rate 6 BPSK 9 (Mbps) 21 IEEE 802.3 Media Access Control (MAC) Carrier-sense multiple access protocol with collision avoidance (CSMA/CA) DIFS: Distributed Inter-Frame Spacing SIFS: Short Inter-Frame Spacing ack: Acknowledgement 22 Other ARQ - Techniques forward channel ARQ-system: TX-buffer RX-buffer return channel ack. of erroneous frame correct pre-error frames correct post-error frames ‘corrected’ frame acknowledgment ack. of error received n-1 frames send due to RX-TX propagation delay TX-buffer TX-buffer re-send only the erroneous frame RX-buffer (after reordering) n frames to be re-send Selective repeat RX-buffer Go-back-n - also some correct frames re-send - small receiver buffer size enough - no reordering in RX - reordering required in TX -- large buffer required in in TXTX a large buffer required Stop-and-wait - for each packet wait for ack. - if negative ack received, re-send packet - inefficient if long propagation delays 23 MAC frame NOTE: This frame structure is common for all data send by a 802.11 station control info (WEP, data type as management, control, data ...) next frame duration frame ordering info for RX -Basic service identification* -source/destination address -transmitting station -receiving station *BSSID: a six-byte address typical for a particular access point (network administrator sets) CRC: Cyclic Redundancy Check WEP: Wired Equivalent Privacy frame specific, variable length frame check sequence (CRC) 24 Logical Link Control Layer (LLC) Specified by ISO/IEC 8802-2 (ANSI/IEEE 802.2) purpose: exchange data between users across LAN using 802-based MAC controlled link provides addressing and data link control (routing) independent of topology, medium, and chosen MAC access method Data to higher level protocols Info: carries user data Supervisory: carries flow/error control Unnumbered: carries protocol control data Source SAP LLC’s functionalities LLC’s protocol data unit (PDU) SAP: service access point 25 Logical Link Control Layer Services A Unacknowledged connectionless service no error or flow control - no ack-signal usage unicast (individual), multicast, broadcast addressing higher levels take care or reliability - thus fast for instance for TCP B Connection oriented service supports unicast only error and flow control for lost/damaged data packets by cyclic redundancy check (CRC) C Acknowledged connectionless service ack-signal used error and flow control by stop-and-wait ARQ faster setup than for B 26 A TCP/IP packet in 802.11 TPC/IP sends data packet Control header LLC constructs PDU by adding a control header SAP (service access point) MAC frame with new control fields Traffic to the target BSS / ESS *BDU: protocol data unit MAC lines up packets using carrier sense multiple access (802.3 CSMA) PHY layer transmits packet using a modulation method (DSSS, OFDM, IR, FHSS) 27 Authentication and privacy Goal: to prevent unauthorized access & eavesdropping Realized by authentication service prior access Open system authentication station wanting to authenticate sends authentication management frame - receiving station sends back frame for successful authentication Shared key authentication (included in WEP*) Secret, shared key received by all stations by a separate, 802.11 independent channel Stations authenticate by a shared knowledge of the key properties WEP’s privacy (blocking out eavesdropping) is based on ciphering: *WEP: Wired Equivalent Privacy 28 Vertical handovers Vertical handovers deal with communication between different systems targeting to seamless communications: 802 and global roaming (GSM, UMTS) 802 and Internet distribution (ADSL) 802 and home networking (Bluetooth) Users can route traffic to different interfaces based on their price, security, bandwidth, etc. requirements Current (Cellular) operators are in a (very) good position to extend their service offerings beyond a single wireless network (subscriptions incl. several access methods, e.g. 2.5/3G, WLAN, xDSL, etc.). For more information search Google with ‘6WINIT’ 29 Simultaneous Multiple Access (“SIMA”) SIMA=Ability to use simultaneously multiple network interfaces: Route different traffic flows through different interfaces in parallel Access and network selection could be based on user profiles/policies Dynamic operation (possibly hidden from the end-user) Scope of mobility (Homogeneous vs. Heterogeneous environments): micro-mobility, intra-domain mobility (Horizontal handovers) macro-mobility, inter-domain/global mobility (Vertical handovers) 30 WLAN Network Planning Network planning target Maximize system performance with limited resource Including coverage throughput capacity interference roaming security, etc. Planning process Requirements for project management personnel Site investigation Computer-aided planning practice Testing and verifying planning 31 Base station location planning tools NPS/indoor (Nokia Network, Finland) Indoor radio planning designed originally for GSM/DCS Support three models One slop model Multi-wall model Enhanced Multi-wall model System parameters can be adjusted and optimized by field measurement Graphical planning of interface and coverage view 32 Field measurements Measurement targets: power levels - throughput - error rate Laptop or PDA Utility come with radio card HW (i.e. Lucent client manager) Supports channel scan, station search Indicate signal level, SNR, transport rate Advanced tools: detailed protocol data flows Special designed for field measurement Support PHY and MAC protocol analysis Integrated with network planning tools Examples Procycle™ from Softbit, Oulu, Finland SitePlaner™ from WirelessValley, American 33 Capacity planning 802.11b has usually about 6.5 Mbps rate throughput due to CSMA/CA MAC protocol PHY and MAC management overhead More user connected, less capacity offered Example of supported users in different application cases: Environment Traffic content Corporation Web, Email, File Wireless LAN transfer Branch Office All application via Network WLAN Public Access Web, Email, VPN Traffic Load Nu mber of simu ltaneous users 802.11b 802.11b 802.11 11Mbps 5.5Mbps 2Mbps 150 kbits/user 40 20 9 300 kbits/user 20 10 4 100 kbits/user 60 30 12 tunneling 34 Frequency planning 83.5 MHz 200 MHz 255 MHz 802.11b 902 928 2400 2484 5150 5350 5470 5725 f/MHz Interference from other WLAN systems or cells IEEE 802.11 operates at uncontrolled ISM band 14 channels of 802.11b are overlapping, only 3 channels are disjointed. For example Ch1, 6, 11 Throughput decreases with less channel spacing A example of frequency allocation in multi-cell network 6 5 4 Mbit/s 26 MHz 11Mb if/frag 512 2Mb if/frag 512 2Mb if/frag 2346 3 2 1 0 Offset 25MHz Offset 20MHz Offset 15MHz Offset 10MHz Offset 5MHz Offset 0MHz 35 Interference from microwave ovens Microwave oven magnetrons have central frequency at 2450~2458 MHz Burst structure of radiated radio signal, one burst will affect several 802.11 symbols 18 dBm level measured from 3 meter away from oven -> masks all WLAN signals! Solutions Use unaffected channels Keep certain distance Use RF absorber near microwave oven 100 mW 902 928 26 MHz 2400 2484 83.5 MHz indoors only 200 mW 5150 5350 200 MHz 1W 5470 5725 f/MHz 255 MHz 36 Interference from Bluetooth The received signal level from two systems are comparable at mobile side In co-existing environment, the probability of frequency collision for one 802.11 frame vary from 48% ~62% Deterioration level is relevant to many factors relative signal levels 802.11 frame length activity in Bluetooth channel Solution Co-existing protocol IEEE 802.15 (not ready) Limit the usage of BT in 802.11 network 37 WLAN benefits Mobility increases working efficiency and productivity extends the On-line period Installation on difficult-to-wire areas inside buildings road crossings Increased reliability Note: Pay attention to security! Reduced installation time cabling time and convenient to users and difficult-towire cases 38 WLAN benefits (cont.) Broadband 11 Mbps for 802.11b 54 Mbps for 802.11a/g (GSM:9.6Kbps, HCSCD:~40Kbps, GPRS:~160Kbps, 2.5G: ~340 kbps, WCDMA:up to 2Mbps) Long-term cost savings O & M cheaper that for wired nets Comes from easy maintenance, cabling cost, working efficiency and accuracy Network can be established in a new location just by moving the PCs! 39 WLAN technology challenges Date Speed IEEE 802.11b supports rates up to 11 MBps (in practice 6 Mb/s), sometimes this is not enough - far lower than 100 Mbps fast Ethernet. (… 802.11a reaches up to 54 Mb/s …) Interference Works in ISM band, shares the same frequency with microwave oven, Bluetooth, and others Security Current WEP algorithm is weak - usually not ON! Roaming No industry standard is available and propriety solution are not interoperable - especially with GSM Inter-operability Only few basic functionality are interoperable, other vendor’s features can’t be used in a mixed network 40 WLAN implementation challenges Lack of wireless networking experience for most IT engineer No well-recognized operation process on network implementation Selecting access points with ‘Best Guess’ method Unaware of interference from/to other networks Weak security policy As a result, your WLAN may have Poor performance (coverage, throughput, capacity, security) Unstable service Customer dissatisfaction 41 References [1] Jim Geier: Wireless LANs, SAMS publishing [2] A. Leon-Garcia, I. Widjaja: Communication Networks (2th ed.), Instructor’s Slide Set, McGraw-Hill [3] Kurose, Ross: Computer Networking (2th ed.), Pearson Education [4] IEEE 802 Standard [5] Raimo Vuopionperä: Background of the VHO project, TEKES-seminar (Vertical handover goes alive! ) 31.10.2003 42