* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download IPv4 and IPv6
Survey
Document related concepts
TCP congestion control wikipedia , lookup
Point-to-Point Protocol over Ethernet wikipedia , lookup
Serial digital interface wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Multiprotocol Label Switching wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Internet protocol suite wikipedia , lookup
SIP extensions for the IP Multimedia Subsystem wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Deep packet inspection wikipedia , lookup
Transcript
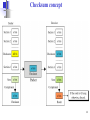
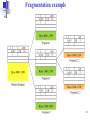
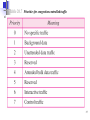
Internet Protocol/ Network Layer 1 Position of IP in TCP/IP protocol suite 2 Internet Protocol (IP) a) The IP is the host-to-host network layer delivery protocol for Internet. b) IP is a connectionless datagram protocol for packet switching network. c) Best effort delivery service: meaning that IP provides no error control or flow control. d) IP uses only an error detection mechanism (Chechsum) and discards the packet if it is corrupted. e) IP does its best to deliver a packet to its destination, but with no guarantees. Needs to rely on TCP layer for reliable delivery. 3 Internet Protocol (IP) IP connectionless network-layer protocol. IP is based on datagram routing. IP is unreliable !! IP has a two-level (at least, traditionally) hierarchical addressing mechanism. Routing in IP is a mixture of hierarchical, distance vector and link state routing algorithms. 4 Datagram • Packets in the IP layer are called Datagrams. • A datagram is a variable-length packet consisting of header and data: • Header: 20 to 60 bytes in length containing essential information for routing and addressing • It is customary to display/show the header in 4-byte sections. • VER: defines the IP version (IPv4). • HLEN: variable-length header; x4 to give it’s the actual length in bytes • Total length: of IP datagram in bytes; • Data length = Total length – header length • Time to live: to control max no. of hops visited by a datagram by count decrement. • Protocol: specifies final dest. protocol to which IP datagram should be delivered; TCP, UDP, ICMP, IGMP • Checksum: covers only header field for testing & debug5 IP datagram Differentiate Service types defines the class of datagram for quality-of-service purpose. E.g. min. delay, max. throughput, max. reliability, min. cost. (Not look into detail). Options: upto 40 bytes long, used for testing and debugging. 6 IP datagram Do not fragment ! IP Header Length in terms of 4-bit words ! More fragments Pointer to this offsetting fragment position in the datagram. Total Length of the IP packet in terms of number of bytes. Datagram-ID. Useful in Fragmentation. Identifies each datagram from others. When a datagram is fragmented, all fragments of a datagram must have the same unique Identification number. The ID number helps destination in reassembling the datagram. 7 Protocol field: 6 1 2 17 89 This field defines the higher level protocol (transport-layer) that uses the services of IP-layer. An IP datagram can encapsulate data from several higher-level protocols such as: TCP=6, UDP=17, ICMP=1, IGMP=2, OSPF=89. This field specifies the final destination protocol to which the IP datagram should be delivered. Since IP multiplexes and demultiplexes data from different higher level protocols, the value of this field helps in the demultiplexing process when the datagram arrives at its final destination. 8 Example 1 An IP packet has arrived with the first 8 bits (leftmost) as shown: 01000010 The receiver discards the packet. Why? Solution There is an error in this packet. The 4 left-most bits (0100) show the version, which is correct. The next 4 bits (0010) show the header length, which means (2 4 = 8), which is wrong. The minimum number of bytes in the header must be 20. The packet has been corrupted in transmission. Note that only HLEN field uses (x4) to get the header length 9 Example 2 In an IP packet, the value of HLEN is 1000 in binary. How many bytes of options are being carried by this packet? Solution The HLEN field value is 8, which means the total number of bytes in the header is 8 4 or 32 bytes. The first 20 bytes are the main header, the next 12 bytes are the options. 10 Example 3 In an IP packet, the value of HLEN is 516 (or 0101) and the value of the total length field is 002816 (or 00101000). How many bytes of data are being carried by this packet? Solution The HLEN value is 5, which means the total number of bytes in the header is 5 4 or 20 bytes (no options). The total length is 28(hex) = 40 bytes, which means the packet is carrying 20 bytes of data. Data length = total length – header length = (40-20) = 20. Only HLEN field uses (x4) to get header length 11 Example 4 An IP packet has arrived with the first few hexadecimal digits as shown below: 45000028000100000102................... How many hops can this packet travel before being dropped? The data belong to what upper layer protocol? Solution To find the time-to-live field, we should skip 8 bytes (16 hexadecimal digits). 4 bits (binary) = 1 bit (hex); 1 byte = 8 bits binary = 2 bits (hex) The time-to-live field is the ninth byte, which is 01. This means the packet can travel only one hop. The protocol field is the next byte (02), which means that the upper layer protocol 12 is IGMP. Checksum To create the checksum the sender does the following: 1. The packet is divided into k sections, each of n bits. 2. All sections are added together using one’s complement arithmetic. 3. The final result is complemented to make the checksum. 13 Checksum concept 14 Checksum in one’s complement arithmetic The checksum in the IP covers only the header, not the data. At sender side, the initial checksum = 0000 0000, then the checksum is carried out by summing up all the fields and applying one’s compliment arithmetic to it to obtain the checksum value before it sends out the IP datagram. At receiver side, same procedure of checksum is carried out. The final value of the result must be 0000 0000, otherwise it will be seen as error and discarded. 15 Decimal value representation 00000000 00000000 Example of checksum calculation in binary 16 Example of checksum calculation in hexadecimal 17 Fragmentation a) A datagram can travel through different networks. b) Each router decapsulates the IP datagram from the frame it receives, process it and then encapsulates it in another frame. c) The format and size of the received frame depend on the protocol used by the physical network through which the frame has just travelled. d) The format and size of the sent frame depend on the protocol used by the physical network through which the frame is going to travel. e) E.g.: if a router connects an Ethernet and ATM networks, it receives a frame in the Ethernet format and sends a frame in the ATM formats. f) Fragmentation is the process of slitting the data into smaller chucks of data (fragment) at the lower layer defined by its maximum transfer size, and add the header to each of these smaller chucks of fragment. g) To make the IP independent of the physical network, the packagers decided to make the max length of IP datagram = largest maximum transfer unit (MTU) defined so far as 65535 bytes. 18 Maximum Transfer Unit (MTU) Each data-link layer protocol has its own frame format. One of the fields defined in the format is the maximum size of the data field. In other words, when a datagram is encapsulated in a frame, the total size of the datagram must be less then this maximum size. When a datagram is fragmented, each fragment has its own header with most of fields repeated, but some changed. A fragmented datagram may itself be fragmented if it encounters a network 19 with even smaller MTU. (Possible several fragmentation b4 final destination). Fragmentation a) A datagram can be fragmented by the source host or any router in the path. b) The reassembly of the datagram, however, is done only by the destination host because each fragment becomes an independent datagram. c) Whereas the fragmented datagram can travel through different routes, and we can never control or guarantee which route a fragmented datagram may take d) All the fragments belonging to the same datagram should arrive at the destination host. So it is logical to do the reassembly at the final destination. 20 Fragmentation The fields that are related to fragmentation and reassembly of an IP datagram are: the identification, flags and fragmentation offset fields. Identification: this field identifies a datagram originating from the source host. When a datagram is fragmented, the value in the ID field is copied into all fragments. This help the reassembly process at destination host. Flags: This is a 3-bit field; 1st is reserved, 2nd is do not fragment bit and 3rd is more fragment bit: if ‘1’ meaning not the last fragment and more fragment after this one; if ‘0’ meaning is the last fragment or only fragment. Fragmentation Offset: The 13-bit field shows the relative position of this fragment with respect to the whole datagram. It is the offset of the data in the original datagram measured in units of 8 bytes. 21 Fragmentation example 1st fragment last byte number 2nd fragment last byte number 3rd fragment 1st byte number last byte number This example shows a datagram with a data size of 4000 bytes fragmented into 3 parts. The bytes in the original datagram are numbered 0 to 3999. The value of offset is measured in units of 8 bytes because the length of the offset field is only 13 bits long cannot represent a sequence more than 8192. (65536/8 = 213). This force the hosts or routers that fragment datagrams to choose the size of each fragment so that the 1st byte number is divisible by 22 8. Fragmentation example 23 Example 5 A packet has arrived with an M bit value of 0. Is this the first fragment, the last fragment, or a middle fragment? Do we know if the packet was fragmented? Solution If the M bit is 0, it means that there are no more fragments; the fragment is the last one. However, we cannot say if the original packet was fragmented or not. A nonfragmented packet is considered the last fragment. 24 Example 6 A packet has arrived with an M bit value of 1. Is this the first fragment, the last fragment, or a middle fragment? Do we know if the packet was fragmented? Solution If the M bit is 1, it means that there is at least one more fragment. This fragment can be the first one or a middle one, but not the last one. We don’t know if it is the first one or a middle one; we need more information (the value of the fragmentation offset). However, we can definitely say the original packet has been fragmented because the M bit value is 1. 25 Example 7 A packet has arrived with an M bit value of 1 and a fragmentation offset value of zero. Is this the first fragment, the last fragment, or a middle fragment? Solution Because the M bit is 1, it is either the first fragment or a middle one. Because the offset value is 0, it is definitely the first fragment. 26 Example 8 A fragment packet has arrived in which the offset value is 100. What is the number of the first byte? Do we know the number of the last byte? Solution To find the number of the first byte, we multiply the offset value by 8. (100 8 = 800) This means that the first byte number is 800. We cannot determine the number of the last byte unless we know the length of the data. 27 Example 9 A fragment packet has arrived in which the offset value is 100, the value of HLEN is 5 and the value of the total length field is 100. What is the number of the first byte and the last byte? Fragment Offset Solution 1st byte number last byte number 100 The first byte number is 100 8 = 800. Given that the total length = 100 bytes & the header length = 20 bytes (5 4), hence the data length = 80 bytes in this datagram. (Data length = total length – header length = 100 – 20 = 80) If the first byte number is 800, the last byte number must 879. (= 800 + 80 – 1 ; since it started from ‘0’ not ‘1’) 28 IP components 29 Internet Protocol version 6: IPv6 30 IPv6 a) Although IPv4 was well designed, it is clear that IPv4 is becoming insufficient for the fast growing Internet and the needs: • Due to growing demand of internet usage, the use of addressing space is becoming insufficient for conventional netid & hostid two-level addressing structure in Classful addressing. • Real-time application i.e. video transmission requires minimum delay strategies and reservation of resource not provided in IPv4 • Encryption and authentication of data and security mechanism not provided in IPv4. • Limitation of flexibility and mobility supported in IPv4. b) While CIDR may buy a few years’ time, the days of IPv4 has already been numbered. c) In IPv6, the internet protocol was extensively modified to accommodate the unforeseen growth of Internet. 31 Improvement in IPv6 a) IPv6 has some advantages over IPv4: • Longer addresses than IPv4: 128 bits long > 32 bits currently in IPv4. That means a huge increase of additional 296 addressing space. • Simplification in Header: contains only 8 vital fields < 13 in IPv4. (speeds up routing process). – 5 fields becomes options. • New options: to support additional functionalities • Security: Authentication & privacy are key features of new IP • More Services: to handle special/real-time multimedia traffic. 32 IPv4 datagram Totally remove bcs fixed 40 bytes header is used Replaced by Hop limit in IPv6 Replaced by Flow label in IPv6 Taken out bcs Next header in IPv6 tells what follows the last IP header (e.g. a UDP or TCP) All replaced by functions in both Next header & payload extension header: fragmentation in IPv6 Replaced by payload length in IPv6 Totally removed bcs calculating this greatly reduce performances. Data-link and Transport layer have their own checksum for 33 better support of reliability, Format of an IPv6 datagram 32 bits Base Header: Occupies 40 bytes Payload: Extension header + Data from upper layer Occupies up to 65535 bytes 34 IPv6 packet field a) VER: IP version; 4 for IPv4 and 6 for IPv6 b) PRI: priority field defines priority of packets w.r.t. traffic congestion; 0-7: for packets that can slow down in event of congestion; 8-15 for real-time traffic with constant sending rate – Audio & Video. c) Flow label: (~ Service in IPv4) Special handling for a particular flow of data; pseudo-connection btw source and dest. for reserved bandwidth and stringent delay requirement. (Still experimental). d) Payload length: tells how many payload bytes follow the 40-bytes header; excluding the count for header based – 40 bytes not included e) Next header: 8-bit field defines the subsequent headers that follow the base header to allow extension; either optional extension headers used by IP or header for an upper-layer protocol, e.g. UDP & TCP. f) Hop limit: serves the same purpose as the TtL in IPv4. g) Source and Destination address field: both occupy 16 bytes (128 bits) h) Extension Headers: 6 extension headers which is optional in IPv4. 35 Comparison between IPv4 and IPv6 packet headers 36 Table 20.7 Priorities for congestion-controlled traffic 37 Table 20.8 Priorities for noncongestion-controlled traffic 38 IPv6 datagram 39 Extension header format 40 Table 20.6 Next header codes for IPv6 41 Extension header types Miscellaneous info for routers Full or partial route to follow Manage datagram fragment Verification of sender’s ID Info about encrypted contents Additional info for destination Same concept of fragmentation as IPv4. However, in IPv6, only original source can fragment the packet using a path MTU discovery method to find the smallest MTU supported by any network on the path. If not, then fragment to a size of 576 bytes, the 42 minimum size of MTU required for each network connected to Internet. Table 20.10 Comparison between IPv4 options and IPv6 extension headers 43 Hop-by-hop option header format Used for information that all routers along the path must examine. Start by telling what kind of header come next and then the length and size of datagram. 44 Source routing 45 Source routing example 46 Fragmentation 47 Authentication Provide a mechanism for the receiver to confirm and be sure of the sender 48 Encrypted security payload When sender and receiver wish to communicate securely. 49 IPv6 address IPv4 4 bytes 32 bits 50 Abbreviated address 51 Abbreviated address with consecutive zeros Two or more groups of 16 zeros can be replaced by a pair of colons 52 CIDR address 53 Transition from IPv4 to IPv6 a) Because of huge number of systems on the Internet, the transition from IPv4 to IPv6 cannot happen suddenly. b) It will take considerable amount of time before every system in the Internet can move from IPv4 to IPv6 c) The transition should be a smooth process to prevent any problems due to their differences. d) 3 transition strategies: • Dual stack • Tunnelling • Header translation 54 Three transition strategies 55 Dual stack A station should simultaneously run both IPv4 & IPv6 protocols until all Internet uses IPv6. To determine which version to use, the source host queries the DNS and send whichever version of IP packet the DNS returns. 56 Tunneling Tunnelling is a strategy used when two hosts using IPv6 want to connect with each other when the packet must pass through a region that uses IPv4. To pass thru the region, packet must have an IPv4 address. So, the IPv6 packet is encapsulate in an IPv4 packet when it enters the region, and IPv6 leaves its capsule when it exits the region. 57 Header translation Header translation is necessary when majority of the Internet has moved to IPv6 but some systems still use IPv4. The sender wants to use IPv6 but the receiver does not understand IPv6. Tunnelling does not work because packet must be in the IPv4 format to be understood by the receiver. In this case, the header format must be changed totally through header translation to down-convert from IPv6 to IPv4 header. 58 Table 20.11 Header translation 59 Further Reading 1- “Computer Networks”, Andrew Tanenbaum, 4th Ed. to learn more about the generic network layer. 2- “Internetworking with TCP/IP vol.1”, Douglas Comer, 4th Ed., provides a detailed and comprehensive presentation of TCP/IP. 3- “Data Communications and Networking”, Behrouz Forouzan, 4th Ed., Copyright Information : Some figures used in this presentation have been either directly copied or adapted from several books. 60