* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download A threat can be any person, object, or event that, if realized, could
Survey
Document related concepts
Computer and network surveillance wikipedia , lookup
Deep packet inspection wikipedia , lookup
Distributed firewall wikipedia , lookup
Authentication wikipedia , lookup
Security and safety features new to Windows Vista wikipedia , lookup
Security-focused operating system wikipedia , lookup
Access control wikipedia , lookup
Computer security wikipedia , lookup
Unix security wikipedia , lookup
Mobile security wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Transcript
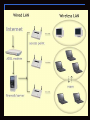
Privacy In Wireless Networks Priyanka Kadiyala Introduction A network consists of 2 or more computers that are linked in order to share resources. They may be linked through cables, telephone lines or radio waves. Wired & Wireless networks Local Area Network The Institute of Electrical and Electronic Engineers (IEEE) has defined a LAN as “a datacomm system allowing a number of independent devices to communicate directly with each other, within a moderately sized geographic area over a physical communications channel of moderate rates”. Distributed File Storing, Remote Computing, Messaging. Security & Privacy Of A Network Security – Protection of networks and their services from unauthorized modification, destruction, or disclosure. Privacy – Protecting confidential details of a person or a network. Threats & vulnerabilities effect security of a network, which in turn, implies that the privacy of the network becomes insecure. Privacy Security Threats A threat can be any person, object, or event that, if realized, could potentially cause damage to the LAN. Threats can be malicious, such as the intentional modification of sensitive information, or can be accidental, such as an error in a calculation, or the accidental deletion of a file. Vulnerabilities Vulnerabilities are weaknesses in a LAN that can be exploited by a threat. For example, unauthorized access (the threat) to the LAN could occur by an outsider guessing an obvious password. Reducing or eliminating the vulnerabilities of the LAN can reduce or eliminate the risk of threats to the LAN. Security Concerns in a LAN Distributed File Storing – Inadequate protection mechanisms on the local workstation. For example, a personal computer (PC) may provide minimal or no protection of the information stored on it. A user that copies a file from the server to the local drive on the PC loses the protection afforded the file when it was stored on the server. Remote Computing - Concerns Remote computing must be controlled so that only authorized users may access remote components and remote applications. The inability to authenticate can lead to unauthorized users being granted access to remote servers and applications. Topologies & Protocols - Concerns The topologies and protocols used today demand that messages be made available to many nodes in reaching the desired destination. This is much cheaper and easier to maintain than providing a direct physical path from every machine to every machine. Threats - active and passive wiretapping. Passive wiretapping includes not only information release but also traffic analysis. Active wiretapping includes message stream modifications (including modification, delay, duplication, deletion or counterfeiting). Other concerns Other LAN security problems include -inadequate LAN management and security policies, lack of training for proper LAN usage and security, inadequate protection mechanisms in the workstation environment, and inadequate protection during transmission. Inadequately protected email can easily be captured, and perhaps altered and retransmitted, effecting both the confidentiality and integrity of the message. Wireless networks Wireless devices use Radio Frequency (RF) to facilitate communication. Various types of wireless communication solutions use different frequencies, mostly regulated by governments. 802.11 and Bluetooth operate in the 2.4Ghz band. Wide Area Networks (WANs) using GPRS, GSM, etc. Local Area Networking (LANs) using 802.11b. Personal Area Networking (PANs) using Bluetooth. WLAN Medium range. Around 150-200ft. Can be extended using directional antenna, repeaters,etc. Benefits –Removes need for cabling infrastructure. –Rapid deployment. How does it work? –Clients ‘associate’ to ‘Access Points’ (AP’s) – Infrastructure Mode. –Clients form peer-to-peer network -‘Ad-Hoc’ Mode. Bluetooth PAN Short range (around 10m or 30 feet). Short range cable replacement technology, used to transmit both voice and data. Gadget oriented. IEEE 802.11 Standard Defines the physical layers and the MAC sublayers for the wireless LANs. Frequency Hopping Spread Spectrum Radio, Direct Sequence Spread Spectrum Radio and Baseband Infrared. Data rate - 2 Mbps ; 2400 - 2483.5 MHz frequency band. Two authentication schemes: Open System Authentication and Shared Key Authentication. OSA–null authentication. WEP Weaknesses Confidentiality: Prevent casual eavesdropping. Access Control: Protect access to a wireless network infrastructure. Data Integrity: Prevent tampering with transmitted messages. WEP relies on the difficulty of discovering the secret key through force. Threats to Wireless Networks When transmissions are broadcast over radio waves, interception and masquerading becomes trivial to anyone with a radio, and so there is a need to employ additional mechanisms to protect the communications. Privacy & Security threats in wireless networks can be Internal or external. Internal – Rogue access points and Incorrectly configured access points. External – Eavesdropping, Identity theft, War driving, Man-in-the-middle attacks,etc. Eavesdropping Eavesdropping is very easy in the radio environment, when one sends a message over the radio path, anyone equipped with a suitable transceiver in the range of the transmission can eavesdrop the message. Undetectable. Parking Lot Attack - Eavesdropping Transitive Trust In wired networks we can always track the wire from our computer to the next network node, but in the wireless environment there is no such way to find out with whom we are talking to. In all cases both parties of the transmission should be able to authenticate each others. The only real protection against this kind of attacks is the strong authentication mechanism of the mobiles accessing the wireless LAN. Man-In-The-Middle Attacks The attacker positions himself between the victim and the device with which the victim is trying to communicate. The attacker can impersonate the receiver with respect to the sender, and the sender with respect to the receiver, without having either of them realize that they have been attacked. An attacker can also impersonate a user. By monitoring the frame transmissions, a hacker can program a rogue radio NIC to mimic a valid one. In this way, the rogue radio NIC steals the ongoing session for which the valid user had logged into. Identity Theft Service Set Identifiers (SSIDs), static WEP authentication and Media Access Control (MAC) addresses are often used to verify that clients are authorized to connect with an AP. However, knowledgeable intruders can pick up approved SSIDs and MAC addresses to connect to a WLAN as an authorized user. Internal Threats Rogue APs - Rogue WLANs can be attached to corporate networks from authorized network users, inadvertently opening doors for intruders. Incorrectly configured APs: Radio waves broadcast by wireless base stations are relatively powerful, and residential neighbors or adjacent businesses may connect to each other's wireless networks. Many APs are initially configured to openly broadcast SSIDs of authorized users. SSIDs can be incorrectly used as passwords to verify authorised users, which allow intruders to easily steal an SSID and assume the identity of an authorized user. Wardriving An unauthorized user uses his mobile device to access a network. Incorrectly configured APs may broadcast their SSID so that any passer by with the equipment can associate and begin sharing a network’s Internet connection. IEEE 802.11i Standard Addresses the weaknesses of 802.11 data privacy by incorporating Temporal Key Integrity Protocol (TKIP), plus a sophisticated keying system that ties together the data privacy and authentication functions. Possible Solutions Activate WEP at the very least - The use of standard 802.11 WEP for networks where there is low risk of attack by actual hackers is a minimum for any security policy. Ensure only authorized people can reset the access points. Some access points will revert back to factory default settings (i.e., no security at all) when someone pushes the reset button on the access point. This makes the access point a fragile entry point for a hacker to extend their reach into the network. As a result, provide adequate physical security for the access point hardware. Properly install all access points. Don't leave access points within easy reach of a hacker who can replace a legitimate safeguarded access point with an unsecured, rogue access point that accepts access from any user. Disable access points during non-usage periods. Assign "strong" passwords to access points. Reduce propagation of radio waves outside the facility. Through the use of directional antennas, you can direct the propagation of radio waves inside the facility and reduce the "spillage" outside the perimeter. Reduces the ability for someone to jam the WLAN from outside the perimeter of the facility. Questions Why does wireless need more security? What are the impacts of such threats & vulnerabilities? What is the solution? References http://csrc.nist.gov/publications/fips/fips191/fip s191.pdf http://www.tml.tkk.fi/Opinnot/Tik110.501/1997/wireless_lan.html#Threats http://www.pentest.co.uk/documents/wlesssalford.pdf http://libproxy.library.unt.edu:2696/iel5/10753/ 33896/01615051.pdf?tp=&arnumber=161505 1&isnumber=33896 Thank you