* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Internet Topology
Survey
Document related concepts
Zero-configuration networking wikipedia , lookup
Backpressure routing wikipedia , lookup
Internet protocol suite wikipedia , lookup
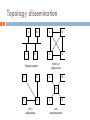
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Serial digital interface wikipedia , lookup
Computer network wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Network tap wikipedia , lookup
IEEE 802.1aq wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Multiprotocol Label Switching wikipedia , lookup
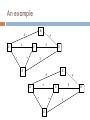
Airborne Networking wikipedia , lookup
Transcript
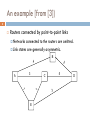
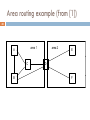
1 LINK STATE ROUTING PROTOCOLS Dr. Rocky K. C. Chang 22 November 2010 Link state approach 2 In the DV approach, each router discovers the network topology through the distance vectors received from its neighbors. In the LS approach, each router discovers the network topology through link state advertisements (LSAs). Each router is responsible for discovering its neighbors and the states of the links between them, and informs other routers. Upon receiving all the link states, a router can form a local view of the entire network. An example [from [3]) 3 Routers connected by point-to-point links Networks connected to the routers are omitted. Link states are generally asymmetric. B 4 2 3 A 1 E 5 C 1 3 D After exchanging LSAs with neighbors (from [1]) 4 For router A B Link A 4 4 A Link B 4 C 3 E 1 3 1 E Link A 1 C Link A 3 After receiving all LSAs (from [1]) 5 After the protocol converges, the routers’ link state databases are identical. B Link A 4 D 2 4 A Link B 4 C 3 E 1 2 C Link A 3 D 5 E 1 3 1 E Link A 1 C 1 D 3 1 5 3 D Link B 2 C 5 E 3 Link state routing protocols 6 Therefore, there are two main parts in a link state routing protocol. (Topology dissemination) Construct and maintain a consistent link state database in all routers. (Route computation) Each router computes minimum-cost paths to all destinations in the network. Topology dissemination 7 Neighbor discovery Use Hello protocols to discover neighbors and to elect a designated router on a shared medium. Bringing up adjacencies in a point-to-point network A set of protocols (database description, link state request/update) to synchronize the link state databases of the two routers On a shared medium, a designated router forms adjacency with other routers, and responsible for advertising the link states. Topology dissemination 8 A C B D A B C D N(N-1)/2 adjacencies Shared medium A B A B LAN C D (N-1) adjacencies C D Link advertisements Link state advertisements 9 A link-state router generates a link state advertisement (LSA) when discovering a new neighbor router, or the cost of the link to an existing neighbor changes (including link failure). The LSA describes the latest changes in the network topology and must be transmitted to all other routers as soon as possible. Dissemination cannot be based on the routing information. Why not? An example 10 If B fails, A needs to update the link state for A->B. But the spanning tree computed based on the original topology does not reach all nodes. A B Reliable flooding protocol 11 The advertising router floods an LSA to all other interfaces. Other routers forward the LSA to all interfaces except the one that the LSA is received. To ensure reliability, all LSAs are positiveacknowledged. A checksum is used to detect data corruption of an LSA, which covers the entire LSA except for some mutable fields. The checksum is used both when the LSA is flooded and kept in the router’s database. Packet storm prevention 12 To prevent packet storms from occurring, use some information to differentiate new LSAs from old LSAs. Each router must keep the latest LSAs. LSAs that are not newer are discarded. Differentiating between new and old LSAs Timestamps with local and global meanings (stamped by the advertising router). A combination of sequence number (SN) and age. LSAs’ sequence numbers and ages 13 A new LSA is indicated by a larger SN (the advertising router increments the SN for every LSA it sends). The age and other information may also be used when the SNs are identical. Design of the sequence numbering Circular SN space (SN wraparounds) Linear SN space (no SN wraparounds). Linear sequence number space 14 The SN starts from some value, say 0 (this initial value may be negative). The SN space should be large enough, say 32-bit SN space. When attempting to increment the SN beyond the largest SN, Prematurely age the LSA and reflooding it. After receiving ACKs from all neighbor routers, send the LSA with the initial SN. LSA messages 15 To recap, an LSA message must minimally include the following information Some identification information of the advertising router Link state type and its value Age, sequence number, and checksum Route computation 16 Given the network topology, each router computes minimum-cost paths from itself to other destinations (a spanning tree). Use any efficient single-source, shortest-path algorithms, such as Dijskstra’s algorithm. The link state can be based on any type of service (TOS), such as delay, reliability, etc. Compute routes for different TOS, and equal-cost paths for load balancing. The computed routes can be used in source routing or hop-by-hop routing. An example 17 B 4 2 3 5 1 1 C D 3 B E 4 2 3 A 1 E 5 C 1 A 3 D The optimality principle 18 If router E is on the optimal path from router A to router D, then the optimal path from router E to router D also falls along the same path. Given that the link state databases are identical in all routers, each local forwarding decision gives a globally optimal path. If the link state databases are not identical, can the routers forward packets on an optimal path? Area routing 19 To make the link state routing more scalable, some routers and their networks may be grouped into the same area. Intra-area routing is essentially a separate copy of the link state routing protocol. Inter-area routing relies on area border routers that have routing info in more than one area. E.g., Router D “summarizes” the routing information in area 2 and floods it to the area 1, and vice versa. Area routing example (from [1]) 20 area 1 A C B area 2 E D F Link and router failures 21 When a link fails, the routers on both side send updated LSAs for this link to age the LSAs in other routers. To cater for router failures, each LSA is associated with an age (determined by the advertising router). Each router periodically sends out its LSAs even though they are not changed, e.g., every half-an-hour. An aged LSA will also be sent out to other routers to age the LSAs in other routers. Initial sequence number 22 If a router boots up (after failure), it needs to know the latest SNs for its LSAs. One solution is to use a distinct initial sequence number to start with. Let NO be the oldest SN (2**31 + 1 in OSPF). When the router boots up, its sends LSAs with SN = NO. When other routers received LSAs with SN = NO, they inform this router of the latest SNs. Network partitions 23 Link/router failures could partition a network. After the partition is healed, the link state databases in the two previously partitioned networks may not be consistent. After the network partition, router B is unaware of the failure of link E-G. After the link C-F is restored, router B may forward packets to router E via router G. Whenever a failed link is restored, bringing up adjacency is performed. Network partition example (from [1]) 24 A E 3 2 1 B C D F G H Open shortest path first protocol 25 OSPF is an implementation of the link state approach. OSPF calculates separate routes for each TOS. When several equal-cost routes to a destination exist, traffic is distributed equally among them. The cost of a route is described by a single dimensionless metric. OSPF allows sets of networks to be grouped together, i.e., areas. The topology of an area is hidden from outside. Open shortest path first protocol 26 OSPF enables the flexible configuration of IP subnets. Each route distributed by OSPF has a destination and mask. Two different subnets of the same IP network number may have different sizes. All OSPF protocol exchanges are authenticated. Externally derived routing data is passed transparently throughout the OSPF network. An OSPF network example 27 A cost is associated with the output side of each router interface. Three kinds of nodes: Router (transit) Network (transit), e.g., N8 and N9 Stub network (nontransit), e.g., N1 and N2 N3, 6, 8, 9 are broadcast networks. RT5 and RT7 are AS border routers. N12-N14 are external networks, and the routes to N12 are advertised by both RT5 and RT7. 28 + | 3+---+ N12 N14 N1|--|RT1|\ 1 \ N13 / | +---+ \ 8\ |8/8 + \ ____ \|/ / \ 1+---+8 8+---+6 * N3 *---|RT4|------|RT5|--------+ \____/ +---+ +---+ | + / | |7 | | 3+---+ / | | | N2|--|RT2|/1 |1 |6 | | +---+ +---+8 6+---+ | + |RT3|--------------|RT6| | +---+ +---+ | |2 Ia|7 | | | | +---------+ | | N4 | | | | | | N11 | | +---------+ | | | | | N12 |3 | |6 2/ +---+ | +---+/ |RT9| | |RT7|---N15 +---+ | +---+ 9 |1 + | |1 _|__ | Ib|5 __|_ / \ 1+----+2 | 3+----+1 / \ * N9 *------|RT11|----|---|RT10|---* N6 * \____/ +----+ | +----+ \____/ | | | |1 + |1 +--+ 10+----+ N8 +---+ |H1|-----|RT12| |RT8| +--+SLIP +----+ +---+ |2 |4 | | +---------+ +--------+ N10 N7 **FROM** * * T O * * 29 |RT|RT|RT|RT|RT|RT|RT|RT|RT|RT|RT|RT| |1 |2 |3 |4 |5 |6 |7 |8 |9 |10|11|12|N3|N6|N8|N9| ----- --------------------------------------------RT1| | | | | | | | | | | | |0 | | | | RT2| | | | | | | | | | | | |0 | | | | RT3| | | | | |6 | | | | | | |0 | | | | RT4| | | | |8 | | | | | | | |0 | | | | RT5| | | |8 | |6 |6 | | | | | | | | | | RT6| | |8 | |7 | | | | |5 | | | | | | | RT7| | | | |6 | | | | | | | | |0 | | | RT8| | | | | | | | | | | | | |0 | | | RT9| | | | | | | | | | | | | | | |0 | RT10| | | | | |7 | | | | | | | |0 |0 | | RT11| | | | | | | | | | | | | | |0 |0 | RT12| | | | | | | | | | | | | | | |0 | N1|3 | | | | | | | | | | | | | | | | N2| |3 | | | | | | | | | | | | | | | N3|1 |1 |1 |1 | | | | | | | | | | | | | N4| | |2 | | | | | | | | | | | | | | N6| | | | | | |1 |1 | |1 | | | | | | | N7| | | | | | | |4 | | | | | | | | | N8| | | | | | | | | |3 |2 | | | | | | N9| | | | | | | | |1 | |1 |1 | | | | | N10| | | | | | | | | | | |2 | | | | | N11| | | | | | | | |3 | | | | | | | | N12| | | | |8 | |2 | | | | | | | | | | N13| | | | |8 | | | | | | | | | | | | N14| | | | |8 | | | | | | | | | | | | N15| | | | | | |9 | | | | | | | | | | H1| | | | | | | | | | | |10| | | | | Link state representations: routers and LANs 30 **FROM** * * T O * * |RT12|N9|N10|H1| -------------------RT12| | | | | N9|1 | | | | N10|2 | | | | H1|10 | | | | RT12's router links advertisement **FROM** * * T O * * |RT9|RT11|RT12|N9| ---------------------RT9| | | |0 | RT11| | | |0 | RT12| | | |0 | N9| | | | | N9's network links advertisement Shortest-path tree rooted at RT6 31 Links without labels have costs of 0, e.g., N3 to R1, 2, 4. RT6 has a link to address Ib (destination) and another link to RT10 (transit). Numbered vs unnumbered point-to-point links RT10 uses RT7 to reach external network N12. RT6 to address Ia (destination)? Only the next hop to the destination is used in the IP forwarding. 32 RT6(origin) RT5 o------------o-----------o Ib /|\ 6 |\ 7 8/8|8\ | \ / | \ | \ o | o 6 | \7 N12 o N14 | \ N13 2 | \ N4 o-----o RT3 \ / \ 5 1/ RT10 o-------o Ia / |\ RT4 o-----o N3 3| \1 /| | \ N6 RT7 / | N8 o o---------o / | | | /| RT2 o o RT1 | | 2/ |9 / | | |RT8 / | /3 |3 RT11 o o o o / | | | N12 N15 N2 o o N1 1| |4 | | N9 o o N7 /| / | N11 RT9 / |RT12 o--------o-------o o--------o H1 3 | 10 |2 | o N10 R6’s forwarding table for internal destinations 33 Destination Next Hop Distance __________________________________ N1 RT3 10 N2 RT3 10 N3 RT3 7 N4 RT3 8 Ib * 7 Ia RT10 12 N6 RT10 8 N7 RT10 12 N8 RT10 10 N9 RT10 11 N10 RT10 13 N11 RT10 14 H1 RT10 21 R6’s forwarding table for external destinations 34 Destination Next Hop Distance __________________________________ N12 RT10 10 N13 RT5 14 N14 RT5 14 N15 RT10 17 OSPF areas 35 OSPF uses the concept of areas to define the routing environment. An area is a logical collection of networks, identified by a 32-bit ID. All routers belonging to the same area disclose complete information about all networks within that area. There is a special area that must be defined for all OSPF domains---the backbone area (0.0.0.0). The backbone is responsible for distributing routing information between areas. Inter-area routing 36 Internal, area border, backbone, AS boundary routers Inter-area routing: from source to an area border router to a backbone path between the source and destination areas to another intra-area path to the destination The correct area border to use for exiting the source area is chosen exactly the same way as how external routers are chosen (e.g., N12). 37 ........................... . + . . | 3+---+ . N12 N14 . N1|--|RT1|\ 1 . \ N13 / . | +---+ \ . 8\ |8/8 . + \ ____ . \|/ . / \ 1+---+8 8+---+6 . * N3 *---|RT4|------|RT5|--------+ . \____/ +---+ +---+ | . + / \ . |7 | . | 3+---+ / \ . | | . N2|--|RT2|/1 1\ . |6 | . | +---+ +---+8 6+---+ | . + |RT3|------|RT6| | . +---+ +---+ | . 2/ . Ia|7 | . / . | | . +---------+ . | | .Area 1 N4 . | | ........................... | | .......................... | | . N11 . | | . +---------+ . | | . | . | | N12 . |3 . Ib|5 |6 2/ . +---+ . +----+ +---+/ . |RT9| . .........|RT10|.....|RT7|---N15. . +---+ . . +----+ +---+ 9 . . |1 . . + /3 1\ |1 . . _|__ . . | / \ __|_ . . / \ 1+----+2 |/ \ / \ . . * N9 *------|RT11|----| * N6 * . . \____/ +----+ | \____/ . . | . . | | . . |1 . . + |1 . . +--+ 10+----+ . . N8 +---+ . . |H1|-----|RT12| . . |RT8| . . +--+SLIP +----+ . . +---+ . . |2 . . |4 . . | . . | . . +---------+ . . +--------+ . . N10 . . N7 . . . .Area 2 . .Area 3 . ................................ .......................... Advertising link states into Area 1 38 Internal destinations: N1-N4 Area border routers RT3 and RT4 advertise into Area 1 the distances to all destinations external to the area. RT3 and RT4 must also advertise into Area 1 the locations of the AS boundary routers RT5 and RT7. Finally, external advertisements from RT5 and RT7 are flooded throughout the entire AS, including Area 1. **FROM** |RT|RT|RT|RT|RT|RT| |1 |2 |3 |4 |5 |7 |N3| ----- ------------------RT1| | | | | | |0 | RT2| | | | | | |0 | RT3| | | | | | |0 | * RT4| | | | | | |0 | * RT5| | |14|8 | | | | T RT7| | |20|14| | | | O N1|3 | | | | | | | * N2| |3 | | | | | | * N3|1 |1 |1 |1 | | | | N4| | |2 | | | | | Ia,Ib| | |15|22| | | | N6| | |16|15| | | | N7| | |20|19| | | | N8| | |18|18| | | | N9-N11,H1| | |19|16| | | | N12| | | | |8 |2 | | N13| | | | |8 | | | N14| | | | |8 | | | N15| | | | | |9 | | 39 Figure 7: Area 1's Database. **FROM** |RT|RT|RT|RT|RT|RT|RT |3 |4 |5 |6 |7 |10|11| -----------------------RT3| | | |6 | | | | RT4| | |8 | | | | | RT5| |8 | |6 |6 | | | RT6|8 | |7 | | |5 | | RT7| | |6 | | | | | * RT10| | | |7 | | |2 | * RT11| | | | | |3 | | T N1|4 |4 | | | | | | O N2|4 |4 | | | | | | * N3|1 |1 | | | | | | * N4|2 |3 | | | | | | Ia| | | | | |5 | | Ib| | | |7 | | | | N6| | | | |1 |1 |3 | N7| | | | |5 |5 |7 | N8| | | | |4 |3 |2 | N9-N11,H1| | | | | | |1 | N12| | |8 | |2 | | | N13| | |8 | | | | | N14| | |8 | | | | | N15| | | | |9 | | | Figure 8: The backbone's database. Summary 40 LS protocols have been deployed for intra-domain routing, such as IS-IS and OSPF. LS protocols rely on reliable mechanisms to update link states of the network in all routers. Compared with the DV approach, LS protocols are more complex to design and also more difficult to manage. While the LS approach scales better than the DV approach, the LS still cannot be used in interdomain routing. References 41 1. 2. 3. 4. 5. M. Steenstrup, Routing in Communications Networks, Prentice Hall, 1995. R. Perlman, Interconnection, Second Edition, Addison Wesley, 2000. S. Keshav, An Engineering Approach to Computer Networking, Addison Wesley, 1997. C. Huitema, Routing in the Internet, Prentice Hall PTR, Second Edition, 1999. OSPF version 2 (RFC 1583)