* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Smart card presentat..
Power MOSFET wikipedia , lookup
Opto-isolator wikipedia , lookup
Immunity-aware programming wikipedia , lookup
Oscilloscope history wikipedia , lookup
Digital electronics wikipedia , lookup
Index of electronics articles wikipedia , lookup
Transistor–transistor logic wikipedia , lookup
Standby power wikipedia , lookup
Time-to-digital converter wikipedia , lookup
Flexible electronics wikipedia , lookup
Power electronics wikipedia , lookup
Audio power wikipedia , lookup
Valve audio amplifier technical specification wikipedia , lookup
Valve RF amplifier wikipedia , lookup
Radio transmitter design wikipedia , lookup
Integrated circuit wikipedia , lookup
Rectiverter wikipedia , lookup
Captain Power and the Soldiers of the Future wikipedia , lookup
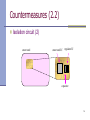
Smart card security Speaker: 陳 育 麟 Advisor: 陳 中 平 教授 1 Outline Introduction of SCAs Cryptographic Algorithms Measurements Hamming Weight Simple Power Attack (SPA) Differential Power Attack (DPA) Countermeasures My Countermeasure: EPS Conclusion for EPS 2 Introduction of SCAs Side channel attacks (SCAs) Security ICs are vulnerable to Side-Channel Attacks (SCAs). SCAs find the secret key by monitoring the power consumption, timing information, or electromagnetic radiation that is leaked by the switching behavior of digital CMOS gates, rather than theoretical weaknesses in the algorithms. Side-channel Information: • Power consumption • Electromagnetic radiation • Timing … Input message Cryptographic processing (Encrypt / Decrypt) Our focus Output message Secret keys 3 Introduction of SCAs (cont’) What kinds of SCAs? 1. Differential Fault Analysis (DFA) - Biham-Shamir (1997) 2.Timing Attacks - Kocher (1996) 3. Simple Power Analysis (SPA) - Kocher, Jaffe, Jun (1998) 4. Differential Power Analysis (DPA) - Kocher, Jaffe, Jun (1998) Not very accurate! Very accurate! 4 Cryptographic Algorithms Data Encryption Standard (DES) Advanced Encryption Standard (AES) RSA Elliptic curve … These cryptographic algorithms can be implemented by either software programming or specific hardware circuit. 5 Measurements Tools Destructive Measurement Non-destructive Measurement 6 Measurements (cont’) Tools Voltage probe Oscilloscope Current probe 7 Measurements (1) Destructive Measurement A small resistor (e.g., 50Ω) is inserted in series with Vdd or GND. oscilloscope voltage probe Vdd R IC decoupling capacitor VR output GND 8 Measurements (2) Non-destructive Measurement We need not modify the original circuit. oscilloscope current probe Vdd IC decoupling capacitor GND IVdd output IGND 9 Hamming Weight Hamming Weight vs. Power Consumption Suggest that this curve is the power consumption profile of XOR. Voltage or Current 10 Simple Power Attack (SPA) Directly interpret the power consumption rotate add conditional branch 1,2,3 … 2nd 16 3rd Different microprocessor instructions consume different power. Thus, the power consumption profiles are different. ROTATE X1 ROTATE X2 11 Differential Power Attack (DPA) Use extra statistical methods X X Y Y , Y X Cov( X , Y ) E[( X X )(Y Y )] ( X , Y ) Cov( X * , Y * ) Cov Cov( X , Y ) XY 12 Countermeasures Power Consumption Balancing INST1 INST2 INST3 INST4 consume (μW) 10 11 11.5 12 compensate (μW) 2 1 0.5 0 total (μW) 12 12 12 12 Table 1. This technique is suitable to logic-level synthesis, but its performance is limit. 13 Countermeasures (1) Addition of Noise To make the power consumption profile blur! sw oscillator C random digits DAC VCO C sw 2C Pdynamic f sw random digits 4C Pdynamic CL Not resistant to DPA attack! Not a complete solution! Related patent: US 6,327,661 To guarantee the efficiency of these two methods, the frequency of the random digit generation might be several time higher than the frequency of the system clock, and the magnitude of the noise might be a lot larger than the original system. Thus, the power consumption is very high. By the way, the area overhead is too high. 14 Countermeasures (2.1) Isolation circuit (1) Use an RC low-pass filter to blur the power consumption. But … “…Of course, the finite rds and capacitive coupling from drain to gate of MP1 limit the extent of the isolation…,” the paper said. Therefore … Not blurred enough! Not power efficient! Patrick Rakers, Larry Connell, Tim Collins, D Russell “Secure Contactless Smartcard ASIC with DPA Protection”, IEEE Journal of Solid-State Circuits, 2001. 15 Countermeasures (2.2) Isolation circuit (2) smart card smart card IC regulator IC capacitor 16 Countermeasures (2.3) Isolation circuit (3) Quoted from: US Patent: 6,510,518 (Jan, 21, 2003) “Balanced Cryptographic Computational Method and Apparatus for Leak Minimization in SmartCards and Other Cryptosystems” 17 Countermeasures (3.1) WDDL (1) WDDL stands for Wave Dynamic Differential Logic. It is based on ‘constant power consumption technique’. K. Tiri, D. Hwang, A. Hodjat, B. Lai, S. Yang, P. Schaumont, and I. Verbauwhede, “A Side-Channel Leakage Free Coprocessor IC in 0.18μm CMOS for Embedded AES-based Cryptographic and Biometric Processing”, DAC, June 2005. 18 Countermeasures (3.2) WDDL (2) WDDL / Standard CMOS: Area: 3X Power Consumption: 13.5X Speed: 0.24X Resistant to both SPA and DPA attack! The power consumption profile is completely blurred! It is an effective method! But … WDDL Standard CMOS Dynamic logic is sensitive to noise! The overheads are too high! Not an economic method! 19 Countermeasures (3.3) WDDL: Input buffers clk = 0: precharge eval pre eval clk = 0: precharge clk M1 clk = 1: evaluation pre Ofalse clk Ofalse clk = 1: evaluation I I clk I Otrue Otrue Otrue Ofalse 20 Countermeasures (3.4) SDDL: Core INV gates clk Ofalse Ifalse clk Ifalse Ofalse Otrue Itrue Core SDDL INV Gate (n-logic) Itrue Otrue Core SDDL INV Gate (p-logic) 21 Countermeasures (3.5) SDDL: Output buffers clk Ofalse Ifalse clk Ifalse Ofalse Otrue Itrue Core SDDL INV Gate (n-logic) Itrue Otrue Core SDDL INV Gate (p-logic) 22 My Countermeasure: EPS Embedded Power Supply (EPS) Technology: Charge sharing phenomenon. Dynamic regulation. Main goal: 1. Resistant to both SPA and DPA attack! 2. To make the power consumption profile completely blurred! (like ‘addition of noise’ or ‘WDDL’) 3. Area overhead: less than 10% 4. On the power consumption side, very little is increased! (not more than 5%) 5. On the performance side, very little is lost! (not more than 5%) 6. Very easy to integrate with other circuits! 23 My Countermeasure: EPS (cont’) Embedded Power Supply (EPS) The minimum supply voltage of standard CMOS logic is: VDD ENCRYPT other circuits charge pre-storing capacitor Cps (1 ~ 3) VDD, min secure circuit VDD,min Vtn | Vtp | During the encryption, the pMOS is off and the secure circuit uses the charges of the charge pre-storing capacitor to do the encryption. Thus, no side-channel information is leaked during the encryption. By institute, the charge pre-storing capacitor is very large; therefore, It needs improvement. 24 My Countermeasure: EPS (cont’) Improvement for EPS VDD system clock encrypt VEPS other circuits charge pre-storing capacitor Cps’ Vref secure circuits SMT D Q CK nQ VIPS secure clock level shifter This improvement takes more clocks to finish an encryption. However, this weakness can be avoided by using two charge pre-storing capacitor. 25 My Countermeasure: EPS (cont’) Further Improvement for EPS VDD nCH1 nCH2 VEPS other circuits Vref Cps1 nPW1 secure circuits nPW2 secure clock SMT control logic Cps2 VIPS system clock level shifter If the secure circuit is positive edge-triggered, the control logic will be negative edge-triggered. 26 Conclusion for EPS Capacitor size: Cps >> Cps’ > Cps1 = Cps2 Area overhead: less than 10% On the power consumption side, very little has been increased! On the performance side, very little has been lost! Resistant to both SPA and DPA attack. VDD nCH1 VDD ENCRYPT other circuits charge pre-storing capacitor Cps nCH2 VEPS VDD system clock encrypt (1 ~ 3) VDD, min secure circuit VEPS other circuits charge pre-storing capacitor Cps’ other circuits Vref secure circuits SMT D Q Vref Cps1 nPW1 secure circuits nPW2 SMT control logic Cps2 CK nQ VIPS secure clock secure clock VIPS system clock level shifter level shifter 27 Thank you! 28