* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Networking
Survey
Document related concepts
Net neutrality law wikipedia , lookup
Wireless security wikipedia , lookup
Distributed firewall wikipedia , lookup
Deep packet inspection wikipedia , lookup
Internet protocol suite wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Computer network wikipedia , lookup
Airborne Networking wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Network tap wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
UniPro protocol stack wikipedia , lookup
Transcript
INTRODUCTION TO
COMPUTER NETWORKS
Computer Centre
Indian Institute of Technology Kanpur
Kanpur INDIA
Course Content
Course Content
Lecture 1: Overview of the Course and Network
Fundamentals: 2 Hour
Lecture 2: OSI Model& TCP/IP Model : 2 Hour
Lecture 3: Physical Media (Copper, Fiber Optic and
Wireless) : 2 Hour
Lab 1: IIT Kanpur Datacenter Visit: 2 Hour
Lecture 4: UTP & Fiber Cabling: 2 Hour
Lecture 5: LAN Technologies (Ethernet, Fast
Ethernet, Gigabit Ethernet, Wireless LAN) : 2 Hour
Lab 2: Demo and Practice of UTP & Fiber Cabling: 2
Hour
Lecture 6: LAN Technologies (contd.) : 2 Hour
Course Content
Course Content
Lecture 7: WAN Technologies (Dialup, Leased Line,
ISDN, ADSL, Cable Modem, VSAT) : 2 Hour
Lab 3: Demo and Practice of Ethernet & Wireless
LAN Setup : 2 Hour
Lecture 8: WAN Technologies (contd.) : 2 Hour
Lecture 9: Internet Protocol (IP) and IP Addressing:
2 Hour
Lab 4: Demo and Practice of Setting up Subnets and
IP Address Assignment : 2 Hour
Lecture 10: Routing, VLAN, TCP and UDP: 2 Hour
Lecture 11: SNMP, Natting, Firewall and VPN: 2 Hour
Lecture 12: Internet and Internet Applications (DNS,
Email, Web..): 2 Hour
Course Content
Course Content
Lecture 13: Cisco Basics: 2 Hour
Lecture 14: Cisco Switch and Router Configuration :
2 Hour
Lab 5: Demo and Practice of Cisco Switch
Configuration : 2 Hour
Lab 6: Demo and Practice of Cisco Router
Configuration : 2 Hour
Lecture 15: DNS & Web Server Setup on Linux : 2
Hour
Lab 7: Demo and Practice of DNS and Web Server
Setup : 2 Hour
Lecture 16: Enterprise Network Implementation: 2
Hour
Course Content
Course Content
Lecture 17: Mail Server, Proxy Server & Firewall
Setup on Linux : 2 Hour
Lab 8: Demo and Practice of Mail Server , Proxy
Server and Firewall Setup : 2 Hour
Books
References
Andrew S. Tanenbaum, Computer Network, PrenticeHall
Doughlas
Internet
E.
Comer,
Computer
Networks
and
http://www.cisco.com/public/support/tac/documenta
tion.html
http://www.redhat.com/docs
http://home.iitk.ac.in/~navi/sidbinetworkcourse
Grading
Grading Guidelines
Two Exams: 40% each
Lab Assignments: 20%
Minimum 80% attendance and minimum 60% marks
are necessary to clear the course.
Introduction to Computer Networks
INTRODUCTION TO COMPUTER
NETWORKS
Introduction to Computer Networks
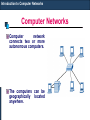
Computer Networks
Computer
network
connects two or more
autonomous computers.
The computers can be
geographically located
anywhere.
Introduction to Computer Networks
LAN, MAN & WAN
Network in small geographical Area (Room, Building
or a Campus) is called LAN (Local Area Network)
Network in a City is call MAN (Metropolitan Area
Network)
Network spread geographically (Country or across
Globe) is called WAN (Wide Area Network)
Introduction to Computer Networks
Applications of Networks
Resource Sharing
Hardware (computing resources, disks, printers)
Software (application software)
Information Sharing
Easy accessibility from anywhere (files, databases)
Search Capability (WWW)
Communication
Email
Message broadcast
Remote computing
Distributed processing (GRID Computing)
Introduction to Computer Networks
Network Topology
The network topology
defines the way in
which
computers,
printers,
and
other
devices are connected.
A network topology
describes the layout of
the wire and devices as
well as the paths used
by data transmissions.
Introduction to Computer Networks
Bus Topology
Commonly referred to
as a linear bus, all the
devices on a bus
topology are connected
by one single cable.
Introduction to Computer Networks
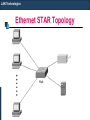
Star & Tree Topology
The star topology is the most
commonly used architecture in
Ethernet LANs.
When
installed,
the
star
topology resembles spokes in
a bicycle wheel.
Larger networks use the
extended star topology also
called tree topology. When
used with network devices that
filter frames or packets, like
bridges, switches, and routers,
this
topology
significantly
reduces the traffic on the wires
by sending packets only to the
wires of the destination host.
Introduction to Computer Networks
Ring Topology
A frame travels around the ring,
stopping at each node. If a node
wants to transmit data, it adds the
data as well as the destination
address to the frame.
The frame then continues around
the ring until it finds the
destination node, which takes the
data out of the frame.
Single ring – All the devices on
the network share a single cable
Dual ring – The dual ring topology
allows data to be sent in both
directions.
Introduction to Computer Networks
Mesh Topology
The mesh topology
connects all devices
(nodes) to each other
for redundancy and
fault tolerance.
It is used in WANs to
interconnect LANs and
for
mission
critical
networks like those
used by banks and
financial institutions.
Implementing the mesh
topology is expensive
and difficult.
Introduction to Computer Networks
Network Components
Physical Media
Interconnecting Devices
Computers
Networking Software
Applications
Introduction to Computer Networks
Networking Media
Networking media can
be defined simply as
the means by which
signals (data) are sent
from one computer to
another (either by cable
or wireless means).
Introduction to Computer Networks
Networking Devices
HUB, Switches, Routers,
Wireless Access Points,
Modems etc.
Introduction to Computer Networks
Computers: Clients and Servers
In
a
client/server
network arrangement,
network services are
located in a dedicated
computer whose only
function is to respond
to the requests of
clients.
The server contains the
file, print, application,
security, and other
services in a central
computer
that
is
continuously available
to respond to client
requests.
Introduction to Computer Networks
Networking Protocol: TCP/IP
Introduction to Computer Networks
Applications
E-mail
Searchable Data (Web Sites)
E-Commerce
News Groups
Internet Telephony (VoIP)
Video Conferencing
Chat Groups
Instant Messengers
Internet Radio
OSI Model
OSI MODEL
OSI Model
Communication Architecture
Strategy for connecting host computers and other
communicating equipment.
Defines necessary elements for data communication
between devices.
A communication architecture, therefore, defines a
standard for the communicating hosts.
A programmer formats data in a manner defined by
the communication architecture and passes it on to
the communication software.
Separating communication functions adds flexibility,
for example, we do not need to modify the entire
host software to include more communication
devices.
OSI Model
Layer Architecture
Layer architecture simplifies the network design.
It is easy to debug network applications in a layered
architecture network.
The network management is easier due to the
layered architecture.
Network layers follow a set of rules, called protocol.
The protocol defines the format of the data being
exchanged, and the control and timing for the
handshake between layers.
OSI Model
Open Systems Interconnection
(OSI) Model
International
standard
organization
(ISO)
established a committee in 1977 to develop an
architecture for computer communication.
Open Systems Interconnection
model is the result of this effort.
(OSI)
reference
In 1984, the Open Systems Interconnection (OSI)
reference model was approved as an international
standard for communications architecture.
Term “open” denotes the ability to connect any two
systems which conform to the reference model and
associated standards.
OSI Model
OSI Reference Model
The OSI model is now considered the primary
Architectural
model
for
inter-computer
communications.
The OSI model describes how information or data
makes its way from application programmes (such
as spreadsheets) through a network medium (such
as wire) to another application programme located
on another network.
The OSI reference model divides the problem of
moving information between computers over a
network medium into SEVEN smaller and more
manageable problems .
This separation into smaller more manageable
functions is known as layering.
OSI Model
OSI Reference Model: 7 Layers
OSI Model
OSI: A Layered Network Model
The process of breaking up the functions or tasks of
networking into layers reduces complexity.
Each layer provides a service to the layer above it in
the protocol specification.
Each layer communicates with the same layer’s
software or hardware on other computers.
The lower 4 layers (transport, network, data link and
physical —Layers 4, 3, 2, and 1) are concerned with
the flow of data from end to end through the network.
The upper four layers of the OSI model (application,
presentation and session—Layers 7, 6 and 5) are
orientated more toward services to the applications.
Data is Encapsulated with the necessary protocol
information as it moves down the layers before
network transit.
OSI Model
Physical Layer
Provides physical interface for transmission of
information.
Defines rules by which bits are passed from one
system to another on a physical communication
medium.
Covers all - mechanical, electrical, functional and
procedural - aspects for physical communication.
Such characteristics as voltage levels, timing of
voltage changes, physical data rates, maximum
transmission distances, physical connectors, and
other similar attributes are defined by physical layer
specifications.
OSI Model
Data Link Layer
Data link layer attempts to provide reliable
communication over the physical layer interface.
Breaks the outgoing data into frames and
reassemble the received frames.
Create and detect frame boundaries.
Handle errors by implementing an acknowledgement
and retransmission scheme.
Implement flow control.
Supports points-to-point as well as broadcast
communication.
Supports simplex, half-duplex or full-duplex
communication.
OSI Model
Network Layer
Implements routing of frames (packets) through the
network.
Defines the most optimum path the packet should
take from the source to the destination
Defines logical addressing so that any endpoint can
be identified.
Handles congestion in the network.
Facilitates interconnection between heterogeneous
networks (Internetworking).
The network layer also defines how to fragment a
packet into smaller packets to accommodate
different media.
OSI Model
Transport Layer
Purpose of this layer is to provide a reliable
mechanism for the exchange of data between two
processes in different computers.
Ensures that the data units are delivered error free.
Ensures that data units are delivered in sequence.
Ensures that there is no loss or duplication of data
units.
Provides connectionless or connection oriented
service.
Provides for the connection management.
Multiplex multiple connection over a single channel.
OSI Model
Session Layer
Session layer provides mechanism for controlling the
dialogue between the two end systems. It defines how to
start, control and end conversations (called sessions)
between applications.
This layer requests for a logical connection to be
established on an end-user’s request.
Any necessary log-on or password validation is also
handled by this layer.
Session layer is also responsible for terminating the
connection.
This layer provides services like dialogue discipline
which can be full duplex or half duplex.
Session layer can also provide check-pointing
mechanism such that if a failure of some sort occurs
between checkpoints, all data can be retransmitted from
the last checkpoint.
OSI Model
Presentation Layer
Presentation layer defines the format in which the
data is to be exchanged between the two
communicating entities.
Also handles data compression and data encryption
(cryptography).
OSI Model
Application Layer
Application layer interacts with application
programs and is the highest level of OSI model.
Application layer contains management functions to
support distributed applications.
Examples of application layer are applications such
as file transfer, electronic mail, remote login etc.
OSI Model
OSI in Action
A message begins at the top
application layer and moves down
the OSI layers to the bottom
physical layer.
As the message descends, each
successive OSI model layer adds a
header to it.
A
header
is
layer-specific
information that basically explains
what functions the layer carried
out.
Conversely, at the receiving end,
headers are striped from the
message as it travels up the
corresponding layers.
TCP/IP Model
TCP/IP MODEL
TCP/IP Model
OSI & TCP/IP Models
TCP/IP Model
TCP/IP Model
Application Layer
Application programs using the network
Transport Layer (TCP/UDP)
Management of end-to-end message transmission,
error detection and error correction
Network Layer (IP)
Handling of datagrams : routing and congestion
Data Link Layer
Management of cost effective and reliable data delivery,
access to physical networks
Physical Layer
Physical Media
Physical Media
PHYSICAL MEDIA
Physical Media
Physical Media
Physical Media
Physical Media
Copper
Coaxial Cable - Thick or Thin
Unshielded Twisted Pair - CAT 3,4,5,5e&6
Optical Fiber
Multimode
Singlemode
Wireless
Short Range
Medium Range (Line of Sight)
Satellite
Physical Media
Copper Media: Coaxial Cable
Coaxial cable is a coppercored cable surrounded
by a heavy shielding and
is used to connect
computers in a network.
Outer conductor shields
the inner conductor from
picking up stray signal
from the air.
High bandwidth but lossy
channel.
Repeater is used to
regenerate the weakened
signals.
Category
Impedance
Use
RG-59
75 W
Cable TV
RG-58
50 W
Thin
Ethernet
RG-11
50 W
Thick
Ethernet
Physical Media
Copper Media: Twisted Pair
Twisted-pair is a type of
cabling that is used for
telephone communications
and most modern Ethernet
networks.
A pair of wires forms a
circuit that can transmit
data. The pairs are twisted
to
provide
protection
against crosstalk, the noise
generated by adjacent pairs.
There are two basic types,
shielded twisted-pair (STP)
and unshielded twisted-pair
(UTP).
Physical Media
Shielded Twisted Pair (STP)
Physical Media
Unshielded Twisted Pair (UTP)
Physical Media
Unshielded Twisted Pair (UTP)
Consists of 4 pairs (8 wires) of
insulated copper wires typically
about 1 mm thick.
The wires are twisted together in a
helical form.
Twisting reduces the interference
between pairs of wires.
High bandwidth and High attenuation
channel.
Flexible and cheap cable.
Category rating based on number of
twists per inch and the material used
CAT 3, CAT 4, CAT 5, Enhanced CAT
5 and now CAT 6.
Physical Media
Categories of UTP
UTP comes in several categories that are based on
the number of twists in the wires, the diameter of the
wires and the material used in the wires.
Category 3 is the wiring used primarily for telephone
connections.
Category 5e and Category 6 are currently the most
common Ethernet cables used.
Physical Media
Categories of UTP: CAT 3
Bandwidth 16 Mhz
11.5 dB Attenuation
100 ohms Impedance
Used in voice applications and 10baseT (10Mbps)
Ethernet
Physical Media
Categories of UTP: CAT 4
20 MHz Bandwidth
7.5 dB Attenuation
100 ohms Impedance
Used in 10baseT (10Mbps) Ethernet
Physical Media
Categories of UTP: CAT 5
100 MHz Bandwidth
24.0 dB Attenuation
100 ohms Impedance
Used for high-speed data transmission
Used in 10BaseT (10 Mbps) Ethernet & Fast Ethernet
(100 Mbps)
Physical Media
Categories of UTP: CAT 5e
150 MHz Bandwidth
24.0 dB Attenuation
100 ohms Impedance
Transmits high-speed data
Used in Fast Ethernet (100 Mbps), Gigabit Ethernet
(1000 Mbps) & 155 Mbps ATM
Physical Media
Categories of UTP: CAT 6
250 MHz Bandwidth
19.8 dB Attenuation
100 ohms Impedance
Transmits high-speed data
Used in Gigabit Ethernet (1000 Mbps) & 10 Gig
Ethernet (10000 Mbps)
Physical Media
Fiber Media
Optical fibers use light
to send information
through the optical
medium.
It uses the principal of
total internal reflection.
Modulated
light
transmissions are used
to transmit the signal.
Physical Media
Total Internal Reflection
Physical Media
Fiber Media
Light travels through the optical media by the way of
total internal reflection.
Modulation scheme used is intensity modulation.
Two types of Fiber media :
Multimode
Singlemode
Multimode Fiber can support less bandwidth than
Singlemode Fiber.
Singlemode Fiber has a very small core and carry
only one beam of light. It can support Gbps data
rates over > 100 Km without using repeaters.
Physical Media
Single and Multimode Fiber
Single-mode fiber
Carries light pulses
along single path
Uses
Laser
Light
Source
Multimode fiber
Many pulses of light
generated by LED
travel
at
different
angles
Physical Media
Fiber Media
The bandwidth of the fiber is limited due to the
dispersion effect.
Distance Bandwidth product of a fiber is almost a
constant.
Fiber optic cables consist of multiple fibers packed
inside protective covering.
62.5/125 µm (850/1310 nm) multimode fiber
50/125 µm (850/1310 nm) multimode fiber
10 µm (1310 nm) single-mode fiber
Physical Media
Fiber-Optic Cable
Contains one or several
glass fibers at its core
Surrounding the fibers is
a layer called cladding
Physical Media
Fiber Optic Cable
FO Cable may have 1 to
over 1000 fibers
Physical Media
Wireless Media
Very useful in difficult
terrain where cable
laying is not possible.
Provides mobility to
communication nodes.
Right of way and cable
laying costs can be
reduced.
Susceptible to rain,
atmospheric variations
and
Objects
in
transmission path.
Physical Media
Wireless Media
Indoor : 10 – 50m : BlueTooth, WLAN
Short range Outdoor : 50 – 200m: WLAN
Mid Range Outdoor : 200m – 5 Km : GSM, CDMA,
WLAN Point-to-Point, Wi-Max
Long Range Outdoor : 5 Km – 100 Km : Microwave
Point-to-Point
Long Distance Communication : Across Continents :
Satellite Communication
Physical Media
Frequency Bands
Band
Range
Propagatio
n
Application
VLF
3–30 KHz
Ground
Long-range radio navigation
LF
30–300 KHz
Ground
Radio beacons and
navigational locators
MF
300 KHz–3 MHz
Sky
AM radio
HF
3–30 MHz
Sky
Citizens band (CB),
ship/aircraft communication
VHF
30–300 MHz
Sky and
line-of-sight
VHF TV,
FM radio
UHF
300 MHz–3 GHz
Line-ofsight
UHF TV, cellular phones,
paging, satellite
SHF
3–30 GHz
Line-ofsight
Satellite communication
EHF
30–300 GHz
Line-ofsight
Long-range radio navigation
Physical Media
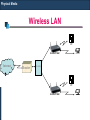
Wireless LAN
PC
Access Point
Internet
Router
Switch
PC
Access Point
Physical Media
Terrestrial Microwave
Microwaves do not
follow the curvature of
earth
Line-of-Sight
transmission
Height
allows
the
signal to travel farther
Two frequencies for
two
way
communication
Repeater is used to
increase the distance
Hop-by-Hop
Physical Media
Satellite Communication
Cabling
UTP AND FIBER CABLING
Cabling
Structured Cabling Infrastructure
Mounted and permanent
Allows patching
Comfort that infrastructure
is OK
Components:
Information Outlet with Face
Plate
Patch Panel
UTP Cable
Patch Cord
Cabling
I/O & Faceplates
Faceplate mounts on or
in wall or in raceway
Single
or
Dual
Information Outlet (I/O)
Provide
network
connectivity
to
the
Hosts through a Patch
Cord
Cabling
Patch Panel
Termination
punchdown in back
Patch cord plugin in
front
Cabling
Patch Cord & UTP Connectors
Cabling
Color Codes
Data Tx: 1 & 2
Data Rx: 3 & 6
Crossover
13
26
PoE +VDC: 4 & 5
PoE -VDC: 7 & 8
Cabling
Cutting, Striping & Crimping Tools
Make your own patch cords
Cuts and strips pairs
RJ45 end crimped onto ends
of wire
Cabling
Punching Tool
Terminates wires to back
of patch panels and in
Information Outlets
Cabling
Making Cables
Cabling
Wire Testing Equipment
Test wire for correct
termination of 8 wires
Test
for
capabilities
speed
Cabling
Cabling Rules
Try to avoid running cables parallel to power cables.
Do not bend cables to less than four times the diameter of the
cable.
If you bundle a group of cables together with cable ties (zip
ties), do not over-cinch them. You should be able to turn the tie
with fingers.
Keep cables away from devices which can introduce noise into
them. Here's a short list: copy machines, electric heaters,
speakers, printers, TV sets, fluorescent lights, copiers, welding
machines, microwave ovens, telephones, fans, elevators,
motors, electric ovens, dryers, washing machines, and shop
equipment.
Avoid stretching UTP cables (tension when pulling cables
should not exceed 25 LBS).
Do not run UTP cable outside of a building. It presents a very
dangerous lightning hazard!
Do not use a stapler to secure UTP cables. Use telephone
wire/RJ6 coaxial wire hangers which are available at most
hardware stores.
Cabling
Fiber Optic Cabling Infrastructure
Components:
Fiber Cable
Fiber Pigtail
Fiber Connectors
LIU
Coupler
Fiber Patch Cord
Cabling
Fiber Optic Connectors
Terminates the fibers
Connects to other fibers
or
transmission
equipment
Cabling
Fiber Patch Cords & Pigtails
Ends
are
typically
either SC or ST
Pigtails
have
connectors on only one
side and Patch Cords
have it on both sides.
Pigtails are spliced to
the fiber to terminate
the fiber
Patch Cord connects
switches to the Fiber
cable
Cabling
LIU & Couplers
Cabling
Fiber Optic Installation –
Outside Plant
Cabling
Fiber Optic Installation –
Outside Plant
Fiber is blown in HDPE
Pipes, 1 m deep.
The HDPE pipes is
covered with sand and
brick lining
Fiber
Roles
are
typically 2 Km. Fiber
cables
are
spliced
using Jointers
Faults like fiber cut are
located using OTDR
(Optical Time Domain
Reflectometer)
LAN Technologies
LAN TECHNOLOGIES
LAN Technologies
Technology Options
Ethernet
Fast Ethernet
Gigabit Ethernet
10 Gig Ethernet
WLAN
LAN Technologies
Media Access
Ethernet and
technologies
Wi-Fi
are
both
“multi-access”
Broadcast medium, shared by many hosts
Simultaneous transmissions will result in collisions
Media Access Control (MAC) protocol required
Rules on how to share medium
The Data Link Layer is divided into two Part MAC
Media Access Control) Sublayer and LLC (Logic
Link Control) Sublayer
LAN Technologies
802.3 Ethernet
Carrier-sense multiple
detection (CSMA/CD).
CS = carrier sense
MA = multiple access
CD = collision detection
access
with
collision
Base Ethernet standard is 10 Mbps.
100Mbps, 1Gbps, 10Gbps standards came later
LAN Technologies
Ethernet CSMA/CD
CSMA/CD (carrier sense multiple access with
collision detection) media access protocol is used.
Data is transmitted in the form of packets.
Sense channel prior to actual packet transmission.
Transmit packet only if channel is sensed idle;
else, defer the transmission until channel becomes
idle.
After packet transmission is started, the node
monitors its own transmission to see if the packet
has experienced a collision.
If the packet is observed to be undergoing a
collision, the transmission is aborted and the
packet is retransmitted after a random interval of
time using Binary Exponential Backoff algorithm.
LAN Technologies
Ethernet Address
End nodes are identified by their Ethernet
Addresses (MAC Address or Hardware Address)
which is a unique 6 Byte address.
MAC Address is represented in Hexa Decimal format
e.g 00:05:5D:FE:10:0A
The first 3 bytes identify a vendor (also called prefix)
and the last 3 bytes are unique for every host or
device
LAN Technologies
Ethernet Frame Structure
Preamble:
7 bytes with pattern 10101010 followed by one byte
with pattern 10101011
Used to synchronize receiver, sender clock rates
Addresses: 6 bytes, frame is received by all adapters
on a LAN and dropped if address does not match
Length: 2 bytes, length of Data field
CRC: 4 bytes generated using CR-32, checked at
receiver, if error is detected, the frame is simply dropped
Data Payload: Maximum 1500 bytes, minimum 46 bytes
If data is less than 46 bytes, pad with zeros to 46
bytes
Length
LAN Technologies
Ethernet
10 Base 5 (Thicknet) (Bus Topology)
10 Base 2 (Thinnet) (Bus Topology)
10 Base T (UTP) (Star/Tree Topology)
10 Base FL (Fiber) (Star/Tree Topology)
LAN Technologies
Ethernet BUS Topology
Repeater
LAN Technologies
Ethernet STAR Topology
Hub
LAN Technologies
Ethernet
Physical Media :10 Base5
10 Base2
10 BaseT
10 BaseFL
-
Thick Co-axial Cable with Bus Topology
Thin Co-axial Cable with Bus Topology
UTP Cat 3/5 with Tree Topology
Multimode/Singlemode Fiber with Tree
Topology
Maximum Segment Length
10 Base5
10 Base2
10 BaseT
- 500 m with at most 4 repeaters (Use Bridge to extend
the network)
- 185 m with at most 4 repeaters (Use Bridge to extend
the network)
- 100 m with at most 4 hubs (Use Switch to extend the
network)
LAN Technologies
Fast Ethernet
100 Mbps bandwidth
Uses same CSMA/CD media access protocol and
packet format as in Ethernet.
100BaseTX (UTP) and 100BaseFX (Fiber) standards
Physical media :100 BaseTX
- UTP Cat 5e
100 BaseFX - Multimode / Singlemode Fiber
Full Duplex/Half Duplex operations.
LAN Technologies
Fast Ethernet
Provision for Auto-Negotiation of media speed:
10 Mbps or 100Mbps (popularly available for copper
media only).
Maximum Segment Length
100 Base TX - 100 m
100 Base FX - 2 Km (Multimode Fiber)
100 Base FX - 20 km (Singlemode Fiber)
LAN Technologies
Gigabit Ethernet
1 Gbps bandwidth.
Uses same CSMA/CD media access protocol as in
Ethernet and is backward compatible (10/100/100
modules are available).
1000BaseT (UTP), 1000BaseSX (Multimode Fiber)
and 1000BaseLX (Multimode/Singlemode Fiber)
standards.
Maximum Segment Length
1000 Base T
- 100m (Cat 5e/6)
1000 Base SX - 275 m (Multimode Fiber)
1000 Base LX - 512 m (Multimode Fiber)
1000 Base LX - 20 Km (Singlemode Fiber)
1000 Base LH - 80 Km (Singlemode Fiber)
LAN Technologies
10 Gig Ethernet
10 Gbps bandwidth.
Uses same CSMA/CD media access protocol as in
Ethernet.
Propositioned for Metro-Ethernet
Maximum Segment Length
1000 Base-T
- Not available
10GBase-LR
- 10 Km (Singlemode Fiber)
10GBase-ER
- 40 Km (Singlemode Fiber)
LAN Technologies
802.11 Wireless LAN
Desktop
with PCI 802.11 LAN card
Network
connectivity
to the
legacy
wired LAN
Access Point
Laptop
with PCMCIA 802.11 LAN card
Provides network connectivity over wireless media
An Access Point (AP) is installed to act as Bridge
between Wireless and Wired Network
The AP is connected to wired network and is
equipped with antennae to provide wireless
connectivity
LAN Technologies
802.11 Wireless LAN
Range ( Distance between Access Point and WLAN
client) depends on structural hindrances and RF
gain of the antenna at the Access Point
To service larger areas, multiple APs may be
installed with a 20-30% overlap
A client is always associated with one AP and when
the client moves closer to another AP, it associates
with the new AP (Hand-Off)
Three flavors:
802.11b
802.11a
802.11g
LAN Technologies
Multiple Access with Collision
Avoidance (MACA)
other node in
sender’s range
sender
RTS
receiver
other node in
receiver’s range
CTS
data
ACK
Before every data transmission
Sender sends a Request to Send (RTS) frame
containing the length of the transmission
Receiver respond with a Clear to Send (CTS) frame
Sender sends data
Receiver sends an ACK; now another sender can
send data
When sender doesn’t get a CTS back, it assumes
collision
LAN Technologies
WLAN : 802.11b
The most popular 802.11 standard currently in
deployment.
Supports 1, 2, 5.5 and 11 Mbps data rates in the 2.4
GHz ISM (Industrial-Scientific-Medical) band
LAN Technologies
WLAN : 802.11a
Operates in the 5 GHz UNII (Unlicensed National
Information Infrastructure) band
Incompatible with devices operating in 2.4GHz
Supports Data rates up to 54 Mbps.
LAN Technologies
WLAN : 802.11g
Supports data rates as high as 54 Mbps on the 2.4
GHz band
Provides backward
equipment
compatibility
with
802.11b
Repeater, HUB, Bridge & Switch
REPEATER, HUB, BRIDGE AND
SWITCH
Repeater, Hub, Bridge & Switch
Repeater
A repeater receives a signal, regenerates it, and
passes it on.
It can regenerate and retime network signals at the
bit level to allow them to travel a longer distance on
the media.
It operates at Physical Layer of OSI
The Four Repeater Rule for 10-Mbps Ethernet should
be used as a standard when extending LAN
segments.
This rule states that no more than four repeaters can
be used between hosts on a LAN.
This rule is used to limit latency added to frame
travel by each repeater.
Repeater, Hub, Bridge & Switch
Hub
Hubs are used to connect
multiple nodes to a single
physical
device,
which
connects to the network.
Hubs are actually multiport
repeaters.
Using a hub changes the
network topology from a
linear bus, to a star.
With hubs, data arriving over
the cables to a hub port is
electrically repeated on all
the other ports connected to
the same network segment,
except for the port on which
the data was sent.
Repeater, Hub, Bridge & Switch
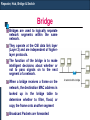
Bridge
Bridges are used to logically separate
network segments within the same
network.
They operate at the OSI data link layer
(Layer 2) and are independent of higherlayer protocols.
The function of the bridge is to make
intelligent decisions about whether or
not to pass signals on to the next
segment of a network.
When a bridge receives a frame on the
network, the destination MAC address is
looked up in the bridge table to
determine whether to filter, flood, or
copy the frame onto another segment
Broadcast Packets are forwarded
Repeater, Hub, Bridge & Switch
Switch
Switches are Multiport Bridges.
Switches provide a unique network segment on each
port, thereby separating collision domains.
Today, network designers are replacing hubs in their
wiring closets with switches to increase their network
performance and bandwidth while protecting their
existing wiring investments.
Like bridges, switches learn certain information about
the data packets that are received from various
computers on the network.
Switches use this information to build forwarding
tables to determine the destination of data being sent
by one computer to another computer on the network.
Repeater, Hub, Bridge & Switch
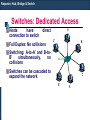
Switches: Dedicated Access
Hosts
have
connection to switch
A
direct
Full Duplex: No collisions
Switching: A-to-A’ and B-toB’
simultaneously,
no
collisions
C’
B
switch
Switches can be cascaded to
expand the network
C
B’
A’
WAN Technologies
WAN TECHNOLOGIES
WAN Technologies
Technology Options
Dial-up
Leased Line
ISDN
X.25
Frame Relay
ATM
DSL
Cable Modem
Microwave Point-to-Point Link
VSAT
WAN Technologies
Dial-up
Uses POTS (Plain Old Telephone System)
Provides a low cost need based access.
Bandwidth 33.6 /56 Kbps.
On the Customer End: Modem is connected to a
Telephone Line
On the Service Provider End: Remote Access Server
(RAS) is connected to Telephone Lines (33.6 Kbps
connectivity) or E1/R2 Line (56 Kbps connectivity)
RAS provide dialin connectivity, authentication and
metering.
Achievable bandwidth depends on the line quality.
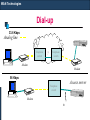
WAN Technologies
Dial-up
WAN Technologies
Dial-up
RAS
WAN Technologies
Dial-up
33.6 Kbps
Analog line
Telephone
switch
?
Telephone
switch
Modem
Modem
56 Kbps
Access server
Telephone
switch
Modem
E1
WAN Technologies
Leased Line
Used to provide point-to-point dedicated network
connectivity.
Analog leased line can provide maximum bandwidth
of 9.6 Kbps.
Digital leased lines can provide bandwidths :
64 Kbps, 2 Mbps (E1), 8 Mbps (E2), 34 Mbps (E3) ...
WAN Technologies
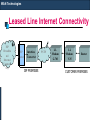
Leased Line Internet Connectivity
ISP
Broadba
nd
Internet
Connecti
vity
ISP
Router
Interface
Converter
ISP PREMISES
PSTN
LL
Modem
G.703
LL
Modem
V.35
Router
CUSTOMER PREMISES
WAN Technologies
ISDN
Another alternative to using
analog telephones lines to
establish a connection is ISDN.
Speed is one advantage ISDN
has
over
telephone
line
connections.
ISDN network is a switched
digital network consisting of
ISDN Switches.
Each node in the network is
identified by hierarchical ISDN
address which is of 15 digits.
ISDN user accesses network
through a set of standard
interfaces provided by ISDN
User Interfaces.
WAN Technologies
ISDN
Two types of user access are defined
Basic Access - Consists of two 64Kbps user channels
(B channel) and one 16Kbps signally channel (D channel)
providing service at 144 Kbps.
Primary access - Consists of thirty 64Kbps user
channels (B channels) and a 64 Kbps signally channel (D
channel) providing service at 2.048Mbps (One 64 Kbps
channel is used for Framing and Synchronization).
B
Basic
Information 128 Kbps
(Voice & Data)
B
D
Signaling 16Kbps
B
Primary
B
D
Information 1920 Kbps
Voice & Data
Signaling 64 Kbps
WAN Technologies
ISDN
ISDN devices
TE1
4W
S/T interface
TE2
NT1
2W
U interface
TA
Devices
NT1 - Interface Converter
TE1 - ISDN devices
TE2 – Non ISDN Devices (need TA)
TA - Terminal Adapter (ISDN Modem)
WAN Technologies
X.25
Packet switched
switches.
Network
consisting
of
X.25
X.25 is a connection oriented protocol (Virtual
Circuits).
End nodes are identified by an X .25 address.
Typical bandwidth offered is 2.4/9.6 kbps.
IP networks interface with X .25 through IP- X.25
routers.
WAN Technologies
X.25 and Virtual Circuits
WAN Technologies
Frame Relay
Designed to be more efficient than X.25
Developed before ATM
Call control carried in separate logical connection
No hop by hop error or flow control
End to end flow and error control (if used) are done
by higher layer
Single user data frame sent from source to
destination and ACK (from higher layer) sent back
Two type of Virtual Circuits defined
Permanent virtual circuits (PVCs)
Switched virtual circuits (SVCs)
WAN Technologies
ATM
Small fixed size packets of 53 bytes, called cells, are
used for transferring information.
Each cell has 5 bytes of header and 48 bytes of
payload for user information.
Connection oriented protocol.
A virtual Circuit is established between the
communicating nodes before data transfer takes
place.
Can be seamlessly used in LANs and WANs.
Almost unlimited scalability.
Provides quality of service guaranties.
WAN Technologies
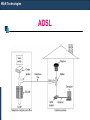
Digital Subscriber Line (DSL)
Digital Subscriber Line (DSL) uses the Ordinary
Telephone line and is an always-on technology. This
means there is no need to dial up each time to
connect to the Internet.
Because DSL is highly dependent upon noise levels,
a subscriber cannot be any more than 5.5 kilometers
(2-3 miles) from the DSL Exchange
Service can be symmetric, in which downstream and
upstream speeds are identical, or asymmetric in
which downstream speed is faster than upstream
speed.
DSL comes in several varieties:
Asymmetric DSL (ADSL)
High Data Rate DSL (HDSL)
Symmetric DSL (SDSL)
Very High Data Rate DSL (VDSL)
WAN Technologies
ADSL
WAN Technologies
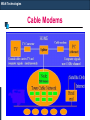
Cable Modems
The cable modem connects a
computer to the cable company
network through the same coaxial
cabling that feeds cable TV (CATV)
signals to a television set.
Uses Cable Modem at Home End
and
CMTS
(Cable
Modem
Termination System) at Head End.
Characteristics:
Shared bandwidth technology
10 Mbps to 30 Mbps downstream
128Kbps-3 Mbps upstream
Maximum Distance from provider to
customer site: 30 miles
WAN Technologies
Cable Modems
WAN Technologies
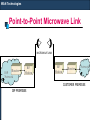
Point-to-Point Microwave Link
MICROWAVE LINK
Router
ISP
Network
RF
Modem
RF
Modem
Router
Network
CUSTOMER PREMISES
ISP PREMISES
WAN Technologies
Point-to-Point Microwave Link
Typically 80-100 MHz Band or 5 GHz Radio Link
band
2.4 GHz WiFi links are becoming popular
Requires Line of Sight
WAN Technologies
VSAT
Very Small Aperture Terminal (VSAT) provide
communication between two nodes through a
powerful Earth station called a Hub.
If two terminals want to communicate, they send
their messages to the satellite, which sends it to the
Hub and the Hub then broadcasts the message
through the satellite.
Typical
Bandwidth
9.6/19.2/32/64/128/256/512 Kbps.
offered
is
Operating modes are TDM/TDMA, SCPC PAMA &
DAMA
WAN Technologies
VSAT
Each satellite sends and receives
over two bands
Uplink: From the earth to the
satellite
Downlink: From the satellite to
the earth
Satellite frequency bands
Band
Downlink
C
3.7-4.2 GHz
Ku
11.7-12.2 GHz
Uplink
5.925-6.425 GHz
14-14.5 GHz
Ku-band based networks, are
used primarily in Europe and
North America and utilize the
smaller sizes of VSAT antennas.
C-band, used extensively in Asia,
Africa and Latin America, require
larger antenna.
Internet Protocol
INTERNET PROTOCOL
Internet Protocol
IP as a Routed Protocol
IP
is
a
connectionless,
unreliable, best-effort delivery
protocol.
IP accepts whatever data is
passed down to it from the
upper layers and forwards the
data in the form of IP Packets.
All the nodes are identified
using an IP address.
Packets are delivered from the
source to the destination using
IP address
Internet Protocol
Packet Propagation
Internet Protocol
IP Address
IP address is for the INTERFACE of a host. Multiple
interfaces mean multiple IP addresses, i.e., routers.
32 bit IP address in dotted-decimal notation for ease
of reading, i.e., 193.140.195.66
Address 0.0.0.0, 127.0.0.1
carries special meaning.
and
255.255.255.255
IP address is divided into a network number and a
host number.
Also bits in Network or Host Address cannot be all
0 or 1.
Internet Protocol
IP Address
Internet Protocol
IP Address
Internet Protocol
IP Address
Class A : Address begins with bit 0. It has 8 bit
network number (range 0.0.0.0-to-127.255.255.255),
24 bit host number.
Class B : Address begins with bits 10. It has 16 bit
network
number
(range
128.0.0.0-to191.255.255.255), 16 bit host number.
Class C : Address begins with bits 110. It has 24 bit
network
number
(range
192.0.0.0-to223.255.255.255), 8 bit host number.
Class D : Begins with 1110, multicast addresses
(224.0.0.0-to-239.255.255.255)
Class E : Begins with 11110, unused
Internet Protocol
Subnet Mask
Consider IP address = 192.168.2.25
First few bits (left to right) identify network/subnet
Remaining bits identify host/interface
Number of subnet bits is called subnet mask, e.g.
Subnet IP Address range is 192.168.2.0
192.168.2.255 or Mask = 255.255.255.0
–
Subnet IP Address range is 192.168.2.0
192.168.2.15 or Mask = 255.255.255.240
–
Internet Protocol
IP Address, Subnet Mask and
Gateway
IP Address and Subnet Mask define the Subnet
For Example IP address 172.31.1.0 and Subnet Mask
of 255.255.240.0 means that the subnet address
ranges from 172.31.0.0 to 172.31.15.255
Another notation is 172.31.1.0/28
The first Address is the Network Address and the
last Address is the Broadcast Address. They are
reserved and cannot be assigned to any node.
The Gateway Address is the Address of the router
where the packet should be sent in case the
destination host does not belong to the same
subnet
Internet Protocol
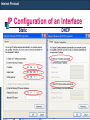
IP Configuration of an Interface
Static
DHCP
Internet Protocol
ARP
ARP (Address Resolution Protocol) is used in
Ethernet Networks to find the MAC address of a
node given its IP address.
Source node (say 192.168.2.32) sends broadcast
message (ARP Request) on its subnet asking ``Who
is 192.168.2.33’’.
All computers on subnet receive this request
Destination responds (ARP Reply) since it has
192.168.2.33
Provides its MAC address in response
Internet Protocol
IPv6
Internet Protocol Version 4 is the most popular
protocol in use today, although there are some
questions about its capability to serve the Internet
community much longer.
IPv4 was finished in the 1970s and has started to
show its age.
The main issue surrounding IPv4 is addressing—or,
the lack of addressing—because many experts
believe that we are nearly out of the four billion
addresses available in IPv4.
Although this seems like a very large number of
addresses, multiple large blocks are given to
government agencies and large organizations.
IPv6 could be the solution to many problems posed
by IPv4
Internet Protocol
IPv6
IPv6 uses 128 bit address instead of 32 bit address.
The IPv6 addresses are being distributed and are
supposed to be used based on geographical
location.
Routing
ROUTING
Routing
Router
A router is a device that determines the next
network point to which a packet should be
forwarded toward its destination
Allow different networks to communicate with each
other
A router creates and maintain a table of the
available routes and their conditions and uses this
information to determine the best route for a given
packet.
A packet will travel through a number of network
points with routers before arriving at its destination.
There can be multiple routes defined. The route with
a lower weight/metric will be tried first.
Routing
Routing
Routing
Routing Protocols
Static Routing
Dynamic Routing
IGP (Interior Gateway
Autonomous System
Protocol):
Route
data
within
an
RIP (Routing Information Protocol)
RIP-2 (RIP Version 2)
OSPF (Open Shortest Path First)
IGRP (Interior Gateway Routing Protocol)
EIGRP (Enhanced Interior Gateway Routing Protocol)
IS-IS
EGP
(Exterior Gateway Protocol):
Autonomous Systems
BGP (Border Gateway Protocol)
Route
data
between
Internetworking Devices
Internetworking Devices
Device
Description
Hub
Hubs are used to connect multiple users to a single physical device,
which connects to the network. Hubs and concentrators act as
repeaters by regenerating the signal as it passes through them.
Bridge
Bridges are used to logically separate network segments within the
same network. They operate at the OSI data link layer (Layer 2) and
are independent of higher-layer protocols.
Switch
Switches are similar to bridges but usually have more ports.
Switches provide a unique network segment on each port, thereby
separating collision domains. Today, network designers are replacing
hubs in their wiring closets with switches to increase their network
performance and bandwidth while protecting their existing wiring
investments.
Router
Routers separate broadcast domains and are used to connect
different networks. Routers direct network traffic based on the
destination network layer address (Layer 3) rather than the
workstation data link layer or MAC address.
VLAN
VLAN
VLAN
VLANs
VLANs (Virtual LAN) enable network managers to
group users logically (based on functions, project
teams or applications) rather than by physical
location.
Traffic can only be routed between VLANs.
VLANs provide the segmentation traditionally
provided by physical routers in LAN configuration.
VLAN
VLANs and Inter VLAN Routing
VLAN
Advantages of Using VLANs
Broadcast Control— Just as switches physically
isolate collision domains for attached hosts and only
forward traffic out a particular port, VLANs provide
logical bridging domains that confine broadcast and
multicast traffic to the VLANs.
Security— If you do not allow routing in a VLAN, no
users outside of that VLAN can communicate with the
users in the VLAN and vice versa. This extreme level of
security can be highly desirable for certain projects and
applications.
Performance— You can assign users that require highperformance or isolated networking to separate VLANs.
TCP/UDP
TCP/UDP
TCP/UDP
TCP/UDP
Transport Layer Protocol
TCP is connection Oriented (uses checksum and
acknowledgment)
UDP is Connectionless
Both use the concept of Connection Port Number
(16 Bit Source Port Number and Destination Port
Number)
Standard Applications have standard Port Numbers
(Email 25, Telnet 23, FTP 20 & 21, SSH 22)
Natting
NATTING
Natting
Private vs Public IP Addresses
Whatever connects directly into Internet must have
public (globally unique) IP address
There is a shortage of public IPv4 address
So Private IP addresses can be used within a
private network
Three address ranges are reserved for private
usage
10.0.0.0/8
172.16.0.0/16 to 172.31.0.0/16
192.168.0.0/24 to 192.168.255.0/24
A private IP is mapped to a Public IP, when the
machine has to access the Internet
Natting
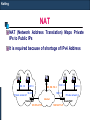
NAT
NAT (Network Address Translation) Maps Private
IPs to Public IPs
It is required because of shortage of IPv4 Address
H1
H3
H2
10.0.1.2
10.0.1.3
Private network 1
H5
213.168.112.3
10.0.1.1
H4
10.0.1.2
10.0.1.1
10.0.1.3
Private network 2
Internet
Router/NAT
128.195.4.119
Router/NAT
128.143.71.21
Natting
NAT
Static NAT : Maps unique Private IP to unique
Public IP
Dynamic NAT : Maps Multiple Private IP to a Pool of
Public IPs (Port Address Translation : Maps a
Public IP and Port Number to a service in Private IP)
Source = 128.143.71.21
Source port = 3200
Source = 10.0.1.2
Source port = 2001
Private address: 10.0.1.2
H1
Private network
Private address: 10.0.1.3
H2
Source = 10.0.1.3
Source port = 1090
128.143.71.21
Internet
NAT
Source = 128.143.71.21
Destination = 4444
SNMP
SNMP
SNMP
Simple Network Management
Protocol
SNMP is a framework that
provides
facilities
for
managing and monitoring
network resources on the
Internet.
Components of SNMP:
SNMP agents
SNMP managers
Management
Information
Bases (MIBs)
SNMP protocol itself
SNMP agent
SNMP
manager
SNMP
protocol
messages
SNMP agent
SNMP agent
SNMP
SNMP
SNMP is based on the
manager/agent
model
consisting of a manager, an
agent,
a
database
of
management
information,
called as MIB.
The manager provides the
interface between the human
network manager and the
management system.
The agent provides the
interface
between
the
manager and the physical
device(s) being managed.
SNMP
SNMP
SNMP uses five basic messages (GET, GET-NEXT, GETRESPONSE, SET, and TRAP) to communicate between the
manager and the agent.
The GET and GET-NEXT messages allow the manager to
request information for a specific variable. The agent, upon
receiving a GET or GET-NEXT message, will issue a GETRESPONSE message to the manager with either the
information requested or an error indication as to why the
request cannot be processed.
A SET message allows the manager to request a change be
made to the value of a specific variable in the case of an alarm
remote that will operate a relay. The agent will then respond
with a GET-RESPONSE message indicating the change has
been made or an error indication as to why the change cannot
be made.
The TRAP message allows the agent to spontaneously inform
the manager of an ‘important’ event.
VPN
VPN
VPN
VPN
VPN is a private connection between two systems
or networks over a shared or public network
(typically Internet).
VPN technology lets an organization securely
extend its network services over the Internet to
remote users, branch offices, and partner
companies.
In other words, VPN turns the Internet into a
simulated private WAN.
VPN is very appealing since the Internet has a
global presence, and its use is now standard
practice for most users and organizations.
VPN
VPN
VPN
How VPN Works
To use the Internet as a private Wide Area Network,
organizations may have to address two issues :
First, networks often communicate using a variety of
protocols, such as IPX and NetBEUI, but the Internet
can only handle TCP/IP traffic. So VPN may need to
provide a way to pass non-TCP/IP protocols from
one network to another.
Second data packets traveling the Internet are
transported in clear text. Therefore, anyone who can
see Internet traffic can also read the data contained
in the packets. This is a problem if companies want
to use the Internet to pass important, confidential
business information.
VPN
How VPN Works
VPN overcome these obstacles by using a strategy
called Tunneling. Instead of packets crossing the
Internet out in the open, data packets are fist
encrypted for security, and then encapsulated in an
IP packet by the VPN and tunneled through the
Internet.
The VPN tunnel initiator on the source network
communicates with a VPN tunnel terminator on the
destination network. The two agree upon an
encryption scheme, and the tunnel initiator
encrypts the packet for security.
VPN
Advantages of Using VPN
VPN technology provides many benefits. Perhaps
the biggest selling point for VPN is cost savings.
One can avoid having to purchase expensive leased
lines to branch offices or partner companies. On
another cost-related note, you can evade having to
invest in additional WAN equipment and instead
leverage your existing Internet installation.
Another benefit of VPN is that it is an ideal way to
handle mobile users.
Enterprise Network
ENTERPRISE NETWORK
IMPLEMENTATION
Enterprise Network
Small Office Network
Use Unmanaged 10/100 Switches
Use Enhanced Cat 5 Pathcords
Enterprise Network
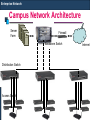
Campus Network Architecture
Server
Farm
Firewall
Backbone Switch
Distribution Switch
Access Switch
Internet
Enterprise Network
Campus Network Architecture
Uses Three Tier Switching Architecture (Popularly known as
Cisco’s Switching Architecture)
Backbone Switch
Layer 3/4 Chassis based switch
Multiple 100Fx or 1000SX/LX or 10GLX/LH ports for
connectivity to Distribution switches
Multiple 10/100/1000 ports for connectivity to Servers
Distribution Switch
Layer 2/3 Managed Fixed configuration switch
1/2 100Fx or 1000Sx/Lx or 10GLX/LH ports for connectivity to
the Backbone switch
Multiple 10/100 or 10/100/1000 ports for connectivity to the
Access switches
Access Switch
Layer2 Managed/Unmanaged Fixed configuration switch
Multiple 10/100 or 10/100/1000 ports for desktop connectivity
Enterprise Network
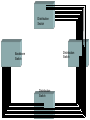
Campus Network Cabling
Campus backbone cabling—This is typically single- or
multimode cable that interconnects the central campus
Backbone Switch with each of the building Distribution
Switches. Typically Ring Architecture is used to connect the
Backbone switch to the Distribution switch to provide
redundant routes.
Building backbone cabling—This is typically Category 5e
or 6 UTP cable that interconnects the building distributor with
each of the floor distributors in the building.
Horizontal cabling—This is predominantly Category 5e or 6
UTP cabling.
Distribution
Switch
Backbone
Switch
Distribution
Switch
Distribution
Switch
Distribution
Switch
Distribution
Switch
Backbone
Switch
Distribution
Switch
Distribution
Switch
Distribution
Switch
Backbone
Switch
Distribution
Switch
Enterprise Network
Campus Network
The residential connectivity can be provided on
Ethernet/Dial-up/ADSL.
The Internet connectivity can be provided on leased
line.
Enterprise Network
Enterprise WAN Architecture
A typical scenario will have Corporate Headquarter
connected to Remote Offices (Branch Offices, Retail
Counters etc.)
The Remote offices would be interconnected to the
corporate office through
A dedicated network implemented over Leased-Lines and/or IPLC
(International Private Leased Circuit) (Microsoft, IBM, Cisco, Infosys
etc.)
A dedicated network implemented over VSAT (Banks’ ATM
Network, Reserve Bank network, BSE Online Trading, NSE Online
Trading etc.)
VPNs on the Internet (Asian Paint Supplier Network, Bajaj Auto Retail
Network etc.)
A mix of above technologies
The backup links may provided through
Redundant route through an alternate leased line
Dial backup on ISDN (The Head Office has a PRI connectivity and
the Remote offices have BRI connectivity)
Enterprise Network
Enterprise WAN Architecture
The Disaster Recovery site would be connected
through multiple links to the main site
VoIP infrastructure may be available (A Call Manager
will be placed at the Head Office and VoIP phones
would be available in all the offices)
The NOC (Network Operation Center) may be at the
Head Quarter (Infosys) or at a remote site (Reliance,
Microsoft)
The NOC maintains, monitors and manages the
network and application servers.
The Data exchange between offices may be through
the servers at NOC to ensure security
Enterprise Network
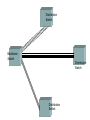
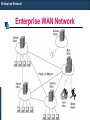
Enterprise WAN Network
Enterprise Network
Enterprise WAN Network
Enterprise Network
Enterprise WAN
Server
Farm
Corporate Head Office
Branch Office
Service Provider
Network
Branch Office
All the locations are connected through a Service Provider Network
over MPLS Backbone
Branch Office
Enterprise Network
Service Provider Networks: Reliance
Reliance Data Centers, are connected to 132 countries across 4
continents spanning US, UK, Mid-east and Asia-Pac through Flag
Telecom backbone (Reliance Infocomm 's group company) and other
undersea cable systems like Se-Me-Wea-3 and i2i and are having
public / private peering relationship with large Tier 1 ISPs and
content providers at more than 15 Internet Exchange points across
the globe. There also exists peering relationship with other popular
domestic ISPs on STM-1 bandwidth levels.
The data centers further are connected to Reliance's country wide
optic fiber based IP network with terabytes of capacity having points
of presence at more than 1100 cities. Customers' can access the
Internet by connecting to any of these 1100 PoPs using multiple
means like local dedicated leased lines, PSTN -ISDN dialup links OR
simply by using Reliance's 3G CDMA mobile services.
The Reliance Data Centers at various locations are also
interconnected through redundant fiber ring with bandwidth capacity
of STM-4 for data replication purposes for providing Disaster
Recovery services.
Enterprise Network
Service Provider Networks: Reliance
Enterprise Network
Service Provider Networks: Reliance
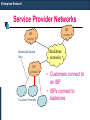
Enterprise Network
Service Provider Networks
ISP
networ
k
ISP
networ
k
Bandwidth-limited
links
ISP
network
Customer Networks
Backbone
networks
• Customers connect to
an ISP
• ISPs connect to
backbone
Enterprise Network
Service Provider Networks: FLAG
http://www.flagtelecom.com/Global_network.swf
Cisco Devices
CONFIGURING CISCO
SWITCH AND ROUTER
Cisco Devices
Cisco’s LAN Switches
Cisco Devices
Cisco’s Routers
Cisco Devices
Hardware Components
Depending on the model/series (at least)
Mother Board/Back Plane
CPU (RISC - MIPS or Motorola)
Memory
Bus
I/O interfaces/Modules
Cisco Devices
Memory Components
Flash Memory – Holds the IOS; is not
erased when the router is reloaded; is an
EEPROM
[Electrically
Erasable
Programmable
Read-Only
Memory]
created by Intel, that can be erased and
reprogrammed repeatedly through an
application of higher than normal electric
voltage
NVRAM – Non-Volatile RAM - holds
router configuration; is not erased when
router is reloaded
RAM – Holds packet buffers, ARP cache,
routing table, software and data structure
that allows the router to function; runningconfig is stored in RAM, as well as the
decompressed IOS in later router models
ROM – Starts and maintains the router
Cisco Devices
What is IOS?
Internetwork Operating System
Operating System of all Cisco Devices
A derivative of BSD UNIX
Custom built by Cisco for each platform
Pre-packaged and static. Complete IOS is upgraded.
Features available in different versions (for a price!)
GUI’s available, but 90%+ of users still prefer commandline configuration.
IOS is designed to be hardware independent.
Cisco Devices
Configuring Cisco Devices
Provides Command Line Interface (CLI) and HTTP
interface
HTTP Interface may be an extention of CLI
CLI can be accessed using Consol Port (through
Hyper Terminal) or by Telnetting the device
Cisco Devices
Configuring Cisco Devices
Two modes of Operation :
Consol
Mode
:
Only
Status
monitored
can
be
Enable
Mode
:
Configuration
can
changed and seen
be
Router> enable (disable)
Router#
Cisco Devices
CLI Commands
Exhaustive Command List
Type help or ? to see list of commands
Type command ? to see the possible command
options
Commands can be auto-completed using TAB
Up-Arrow, Down-Arrow
command history
can
be
used
Abbreviations of Commands can be used
to
see
Cisco Devices
Show Configuration
sh run : To see running configuration
sh conf : To see saved configuration
Cisco Devices
Save Configuration
wr mem
Cisco Devices
Configuration Mode
conf t
Cisco Devices
Disable or Delete the Configuration
Use “no” before the configuration line
Cisco Devices
General Commands
hostname
ip default-gateway
ip name-server
ip routing
ip route
ip multicast-routing
banner
Cisco Devices
Interface Configuration Commands
Interfaces are named by type and position; e.g.:
ethernet0, ethernet1/0,... Fastethernet0,fastethernet1/0,…
gigabitethernet0,gigabitethernet1/0
serial0, serial1 ... serial3/1
Can be abbreviated:
ethernet0 or eth0 or e0
serial0 or ser0 or s0
IP address and netmask configuration, status configuration
etc. are done using interface commands:
router#config terminal
router(config)#interface e0
router(config-if)#ip address 195.176.118.254 255.255.255.0
router(config-if)#exit
router#
Cisco Devices
Interface Commands
ip address < ip address > < netmask >
ip address < ip address > < netmask > secondary
duplex full/half/auto
speed 10/100/1000/auto
bandwidth < bandwidth in kbps >
description < interface description >
shutdown
encapsultaion hdlc/ppp
Cisco Devices
Static Routing Commands
ip route <network address> <netmask> <gateway
router address>
ip route 172.16.20.0 255.255.255.0 172.16.10.2
ip default-gateway < default gateway router address>
ip default-gateway 172.16.10.1
ip route 0.0.0.0 0.0.0.0 172.16.10.1
Cisco Devices
Backup & Restore Configuration
Copy (from cisco device to tftp server and viceversa)
copy startup-config tftp (it will ask the tftp server ip
address and destination filename)
copy tftp startup-config (it will ask the tftp server ip
address and destination filename)
Cisco Devices
Static NAT Commands
ip nat inside (on the port where you have private IP)
ip nat outside (on the port where you have public IP)
ip nat inside source static <private ip> <public ip>
(global command)
Cisco Devices
NAT Pool Commands
ip nat inside (on the port where you have private IP)
ip nat outside (on the port where you have public IP)
ip nat pool <name of the nat pool> <starting ip
address> <last ip address> <netmask of the public
ip addresses> (global command)
ip nat inside source list 1 pool <name of the nat
pool> overload (global command)
access-list 1 permit <private ip> (global command)
Cisco Devices
Diagnostic Commands
ping
traceroute
Cisco Devices
General Monitoring and
Administration Commands
reload
sh ver
sh int
Cisco Devices
Upgrading Cisco IOS
Download and install TFTP server (http://www.download.com)
Download Cisco IOS Software Image to be upgraded
Copy this image in the outbound directory of TFTP server
Establish a Console or Telnet session with the router
Use sh flash command to check that you have enough space
in flash to install the new image
Backup the existing IOS image on the TFTP server using the
command copy flash tftp (it will ask the tftp server ip address
and source and destination filename)
Copy the new IOS image from TFTP server to the flash using
the command copy tftp flash (it will ask for the tftp server ip
address and source and destination filename)
Reboot the Router
Internet Applications
INTERNET
APPLICATIONS
Internet Applications
Internet Applications
Domain Name Service
Proxy Service
Mail Service
Web Service
DNS
DNS
DNS
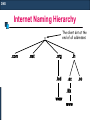
Internet Naming Hierarchy
The silent dot at the
end of all addresses
.com
.net
.org
.tcd
.in
.ac
.iitk
www
www
.co
DNS Setup
DNS Operation
A DNS server maintains the name to IP address
mapping of the domain for which it is the name server.
The DNS server for a domain is registered with the
domain registrar and the entry is maintained by the
Internet Root-Servers (13) or Country Level RootServers.
Whenever a server is queried, if doesn’t have the
answer, the root servers are contacted.
The root servers refer to the DNS server for that
domain (in case the domain is a top level domain) or
the Country Root Server (in case the domain is
country level domain).
Proxy Server
PROXY SERVER
Proxy Server
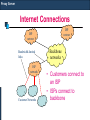
Internet Connections
ISP
networ
k
ISP
networ
k
Bandwidth-limited
links
ISP
network
Customer Networks
Backbone
networks
• Customers connect to
an ISP
• ISPs connect to
backbone
Proxy Server
Internet Connections
Cost of connections is based on bandwidth
Cost of connection is a major part of network cost
Organisations only obtain as much bandwidth as they
can afford
Many organisations in Asia-Pacific only have 64kb/s –
2Mb/s connections (as compared to their counterpart
in US and Europe who have bandwidths of 2.4 Gbps –
10 Gbps)
Proxy Server
What is a Web Proxy?
A proxy is a host which relays web access requests
from clients
Used when clients do not access the web directly
Used for security,
performance
browser
logging,
proxy
accounting
web
and
Proxy Server
What is Web Caching?
Storing copies of recently accessed web pages
Pages are delivered from the cache when requested
again
Browser caches
Proxy caches
Proxy Server
Why Cache?
Shorter response time
Reduced bandwidth requirement
Reduced load on servers
Access control and logging
Proxy Server
Popular Proxy Caches
Apache proxy
MS proxy server
WinProxy
Squid
Squid is popular because
configurable and free
Many others
it
is
powerful,
Web Server
WEB SERVER
Web Server
Web Server
HTTP (Hyper Text Transfer Protocol) is used to
transfer web pages from a Web Server to Web
Client (Browser)
Web Pages are arranged in a directory structure in
the Web Server
HTTP supports CGI (Common Gateway interface)
HTTP supports Virtual Hosting (Hosting multiple
sites on the same server)
Popular Web Servers
Apache
Windows IIS
IBM Websphere
Email
EMAIL
Email
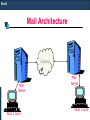
Mail Architecture
Internet
Mail
Server
Mail Client
Mail
Server
Mail Client
Email
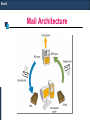
Mail Architecture
Email
Mail Architecture
Simple Mail Transfer Protocol (SMTP) is used to
transfer mail between Mail Servers over Internet
Post Office Protocol (PoP) and Interactive Mail
Access Protocol (IMAP) is used between Client and
Mail Server to retrieve mails
The mail server of a domain is identified by the MX
record of that domain
Popular Mail Servers
Sendmail/Postfix
Microsoft Exchange Server
IBM Lotus
DNS Setup
DNS CONFIGURATION
DNS Setup
DNS Configuration
named daemon is used
A DNS Server may be caching/master/slave server
The named.ca file has information of all Root
Servers.
There is a Forward Zone file and a Reverse Zone
file for every domain.
Configuration file:
/var/named/chroot/etc/named.conf
Forward Zone File:
/var/named/chroot/var/named/<forward_zone_file>
Reverse Zone File:
/var/named/chroot/var/named/<reverse_zone_file>
DNS Setup
Sample Master named.conf
zone "." {
type hint;
file "named.ca";
};
zone "0.0.127.in-addr.arpa" {
type master;
file "named.local";
allow-query {any;};
};
zone "iitk.ac.in" {
type master;
file "hosts.db";
allow-query {any;};
};
zone "95.200.203.IN-ADDR.ARPA" {
type master;
file "hosts.rev.203.200.95";
allow-query {any;};
};
zone "iitk.ernet.in" {
type slave;
file "hosts.iitk.ernet.in";
masters { 202.141.40.10; };
allow-query {any;};
DNS Setup
Sample Forward Zone File
$TTL 86400
@
IN
SOA ns1.iitk.ac.in. root.ns1.iitk.ac.in. (
200605091 ; Serial
10800 ; Refresh - 3 hours
3600 ; Retry - 1 hour
1209600 ;Expire - 1 week
43200 ) ; Minimum TTL for negative answers - 12 hours
IN
NS
ns1.iitk.ac.in.
IN
NS
ns2.iitk.ac.in.
IN
MX
5
mail0.iitk.ac.in.
IN
MX
10
mail1.iitk.ac.in.
IN
MX
20
mail2.iitk.ac.in.
$ORIGIN iitk.ac.in.
ns1
IN
A
mail0
IN
A
proxy
IN
CNAME
203.200.95.142
203.200.95.144
mail0
DNS Setup
Sample Reverse Zone File
$TTL 86400
$ORIGIN 200.203.in-addr.arpa.
95
IN
SOA ns1.iitk.ac.in. root.ns1.iitk.ac.in. (
200605091 ; Serial
10800
; Refresh - 5 minutes
3600
; Retry - 1 minute
1209600 ; Expire - 1 weeks
43200 ) ; Minimum TTL for negative answers - 12 hours
IN
NS
ns1.iitk.ac.in.
IN
NS
ns2.iitk.ac.in.
$ORIGIN 95.200.203.in-addr.arpa.
;
;
142 IN
PTR ns1.iitk.ac.in.
144 IN
PTR mail0.iitk.ac.in.
DNS Setup
Configuring Local Resolver
/etc/resolv.conf
server 127.0.0.1
DNS Setup
Test DNS
nslookup
host
dig
Test your DNS with the following DNS diagnostics
web site: dnsstuff.com
Apache Setup
APACHE SETUP
Web Server Setup
Web Server
Apache Web Server is used
Daemon is httpd (service httpd start/stop/restart)
Web Server Setup
Files used by Apache
Configuration file: /etc/httpd/conf/httpd.conf
Log files: /var/log/httpd/access_log and
/var/log/httpd/error_log
Modules /etc/httpd/modules
Default Document Root /var/www/html
Default CGI Root /var/www/cgi-bin
Web Server Setup
Apache Configuration Directives
Server Name
Min and Max Servers
Document Root
CGI Enable/Disable
User Directory
Directory Index
Mime Types
Modules
Access Restrictions
Secure Server
Virtual Hosting
Web Server Setup
Basic Settings
Change the default value for ServerName
www.<your-domain.com> in httpd.conf and put the
website content in /var/www/html
Additionally you can configure Name based Virtual
Hosting (allow more than one websites to run on
the same server)
Web Server Setup
Virtual Hosting
NameVirtualHost
*:80
<VirtualHost *:80>
ServerName server-name
DocumentRoot path-to-virtual-document-root
</VirtualHost>
<VirtualHost *:80>
ServerName server-name
DocumentRoot path-to-virtual-document-root
</VirtualHost>
Squid Setup
SQUID SETUP
Squid Setup
Obtaining Squid
Source code (in C) from www.squid-cache.org
Binary executables
Linux (comes with RedHat and others)
FreeBSD
Windows
Pre-installed in Fedora/Enterprise Linux
Squid Setup
Basic Settings
Edit the /etc/squid/squid.conf file to configure squid
Configuration options:
Disk Cache size and location
Authentication
Allowed Hosts
Any other access restrictions (sites, content, size,
time of access etc.) using ACL
service squid start/stop/restart
Squid Setup
Disc Requirements
Squid makes very heavy use of disc because of
heavy read/write in cache
Needs discs with low seek times
SCSI is better
Can spread cache over 2 or more discs
Raid not recommended
Cached data is not critical
Squid Setup
Calculating Disc Space
Recommend keeping at least 2 days worth of
objects
10 days may be better
Example:
256Kbps link loaded 10 hrs/day ~= 1GB
assume 50% cacheable - .5GB / day
2 days objects - 1GB
10 days objects - 5 GB
Squid Setup
Squid.conf Basic Configuration
cache_dir ufs /var/spool/squid/cache 100 16 256
auth_param basic program /usr/lib/squid/ncsa_auth
/etc/shadow
acl sidbiusers proxy_auth required
http_access allow sidbiusers
acl our_network src 172.28.250.0/24
http_access allow our_network
(Note: use squid –z for the first time to create the
cache directory and its subdirectories)
Sendmail Setup
SENDMAIL SETUP
Mail Server Setup
Sendmail Configuration
Daemon: sendmail
Configuration File: /etc/mail/sendmail.mc
Edit the following lines
LOCAL_DOMAIN(`localhost.localdomain')dnl
(Replace localhost.localdomain by the domain name for which
the mail server is being configured)
DAEMON_OPTIONS(`Port=smtp,Addr=127.0.0.1,
Name=MTA')dnl
(comment this line by adding dnl at the start of the line)
dnl MASQUERADE_AS(`mydomain.com')dnl
(remove dnl & replace mydomain.com by the domain name)
Sendmail Setup
Sendmail Configuration
Add the range of IP addresses of your network in
access file
(e.g. 172.31.
Relay)
Run “make –C /etc/mail” command to compile
sendmail.mc and generate sendmail.cf file.
Restart sendmail and watch for errors
Sendmail Setup
PoP & IMAP Server
PoP3 & IMAP Server can be started using dovecot
server. (service dovecot start)
Firewall
FIREWALL
Firewall
Basic Setup
Internet
Application
Web Server
Database
Firewall
Firewall
Firewall Rules
IP Address of Source (Allow from Trusted Sources)
IP Address of
Destinations)
Destination
(Allow
to
trusted
Application Port Number (Allow Mail but restrict
Telnet)
Direction of Traffic (Allow outgoing traffic but
restrict incoming traffic)
Firewall
Firewall Implementation
Hardware Firewall: Dedicated Hardware Box (Cisco
PIX, Netscreen )
Software Firewall: Installable on a Server ( )
Host OSs (Windows XP/Linux) also provide
software firewall features to protect the host
These days Firewalls provide IDS/IPS (Intrusion
Detection System/Intrusion Prevention System)
services also.
Linux Security
LINUX Firewall
Use GUI (Applications ->System Settings->
Security Level) to activate the firewall
Allow standard services and any specific port
based application
All other services and ports are blocked
Linux Security
LINUX Firewall