* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Wireless Optimization for Java RMI
Extensible Authentication Protocol wikipedia , lookup
Distributed operating system wikipedia , lookup
Server Message Block wikipedia , lookup
Dynamic Host Configuration Protocol wikipedia , lookup
Internet protocol suite wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Wireless security wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Hypertext Transfer Protocol wikipedia , lookup
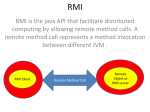
Middleware for Nomadic Computing Stefano Campadello Presentation Outline • Nomadic Computing issues • • • • Communication Issues Mobility Issues Device Issues Security Issues • Middleware for Distributed Computing • • • WAP Java RMI Corba Presentation Outline • Enhancing the Middleware • • • Dolmen Nomadic RMI Wireless CORBA • Conclusions Nomadic Computing What’s it? Nomadic Computing ”The essence of a nomadic environment is to automatically adjust all aspects of user’s computing, communications, and storage functionality in a transparent and integrated fashion” – L. Kleinrock, 1997 Anytime, Anywhere • A user wants to: • • • • use her laptop during a flight and upload her work once disembarked follow financial information independently from the location and time instantiate a communication during a disaster recovery mission access the Internet or Intranet services while on the move. The Challenges in Mobile Computing Communication Issues • Low Bandwidth • • sending long files requires long time: the chance of experiencing network failures is high a graphical user interface can act in a bizarre way • High bandwidth variability • Bandwidth can increase/decrease four orders of magnitude depending on local conditions (connected/wireless). Ex: videoconference • Disconnection • • File system can lock up for a remote server to allow access After reconnections conflicts are possible Mobility Issues • Address Migration • • Physical location != network address To communicate with a mobile computer is necessary to know its most recent address • Location-dependent information • • Some information depend on location, as local printers or local currency. In a mobile environment these information cannot be stored statically and they must be found dynamically Devices Issues • Power limitation • • • Energy supply is a bottleneck for mobile devices Bigger batteries => more weight The user wants long-lasting AND light devices • User Interface and Display Issues • • • • Size constrains force to use small user interface Small display size makes access to remote service difficult Input devices must be redesign (keyboard -> pen-based recognition) Hand-writing and sound recognition Security Issues • • • • • • Identification Certification Privacy Insecure channels Insecure devices (can be stolen) ... Middleware for Distributed Computing Middleware for Distributed Computing • Remote Procedure Call (RPC) • • • • 1976. Provides communication across a network between programs written in a high-level language Using procedure calls mechanism is easier than building a communication paradigm It presumes the existence of TCP/IP or UDP Its use is in decline: not implemented in object oriented programming languages • Java RMI • • 1998. Same concept implemented in Java. More later... Remote Procedure Call (RPC) Client program Service daemon Machine B RPC Call Invoke service Call service Machine A Service executes RPC returns requested completed return reply Program continues Middleware for Distributed Computing • Wireless Application Protocol • • Designed for Nomadic devices It provides Internet access for phones and small PDAs WAP - Architecture WAP – Architecture WAP – Architecture 2.0 Middleware for Distributed Computing • OMG CORBA • • • • 1989. Provides interoperability between objects in a heterogeneous, distributed environment Interfaces specified in OMG IDL Not suited for wireless networks, since it requires reliable communication Not suited for mobile device, since the terminal cannot change its point-of-presence • Microsoft COM and DCOM • • COM allows binary interoperability between distributed objetcs NOT platform independent and proprietary protocols OMG CORBA – Architecture Interface Repository Client IDL Compiler OBJ Implementation Repository Object (Servant) in args operation() REF out args + return IDL SKEL DII ORB CORE IDL STUBS DSI ORB INTERFACE Object Adapter GIOP/IIOP Enhancing the Nomadic Layers Nomadic Computing - Layered APPLICATIONS MIDDLEWARE (IIOP/RMI/ACTIVE-X) TRANSPORT LAYER (TCP/IP) RADIO LINK Improving Long Thin Networks • Slow Start and Congesting Avoidance • the system assumes the network is congested while packets are dropped for corruption • Delayed ACKs • the dimension of the sender’s window depends on the number of ACKs it receives. Adaptation is slow • Three-way Handshake • data transfer is possible only after the handshake is completed. Long latency makes short transactions unattractive • Lenght of TCP/IP headers Improving TCP over Wireless • Solutions: • • • • • • modify or eliminate slow start Use larger initial windows Count the data acknowlegde not the number of ACK Change the spacingbetween ACKs Compress headers or compress IP payload SNOOP (Berkeley) • Split connection approach, but maintaining end-to-end semantic • retransmission of lost packets only locally • suppression of duplicate ACKs from receiver to sender Improving Client-Server Paradigm • Satyanarayanan [1996]: • Extremes of adaptation: laissez-fair and applicationtransparent Improving Client-Server Paradigm Application-aware (collaboration) Laissez-faire (no system support) Application-transparent (no changes to applications) Enhancing the Communication Layer • Example: Coda File System Applications Mobile File Server File System APIs Mobile File System APIs File System Proxy Mobile Host Fixed Network Mowgli Project Monads • Adaptation agents for Nomadic Application. • The key work is ”prediction” through learning Addressing the Mobility Issues • Mobile IP Enhancing The Middleware Layer Nomadic RMI Remote Method Invocation • RMI protocol interface lets Java objects on different hosts communicate with each other in a transparent way • Clients can invoke methods of a remote object as if they were local methods • Preserve the object oriented paradigm in distributed computing Java RMI - Layers Logical Path Server Program Client Program Skeleton (JDK 1.1) Stub Remote Reference Layer Remote Reference Layer Transport Layer The Internet Transport Layer Java RMI - Protocol Server Virtual Machine Client Virtual Machine Client Client Object Object Registry Registry 2 3 Server Server 1 Remote Remote Object Object 6 8 Stub Stub 5 4 7 Skeleton Skeleton Java RMI in a Nutshell Client Server Lookup(): where is Hello? Registry Registry Hello is here Client Client Send the me stub Stub-server Server-stub Here is the stub DGC messages invokeMethod() Stub “ReturnValue” Server Server Java RMI in a Nutshell Client Server Lookup(): where is Hello? Registry Registry Hello is here Client Client Send the me stub Stub-server Server-stub Here is the stub DGC messages invokeMethod() Stub “ReturnValue” Server Server “Hello World” Example Client TCP 2 Registry TCP 1 Header ProtocolAck, EPId EPId, Lookup() ServerRef Header ProtocolAck, EPId EPId, dirty() Lease Ping Ping Ack Parallel Parallel DGCAck Ping Ping Ack sayHello() “Hello World” ... clean() clean result Server Data traffic analysis 55 (6%) 41 (4%) 831 (85%) 52 (5%) Server and Registry to Client (bytes) 276 (42%) 37 (6%) 305 (46%) 40 (6%) 331 (20%) 78 (5%) 1136 (69%) 92 (6%) 979 (100%) 658 (100%) 1637 (100%) Client to Server and Registry (bytes) Registry Lookup Invocation Data DGC Data Protocol Overhead Total Total (bytes) RMI Optimization • Maintain compatibility with Java RMI specifications • Avoid redundancy in communication protocol • Use compression and caching to minimize data transmission Java RMI Optimization • Protocol • Use of Mediators to minimize the exchange of data through the wireless link. • Data Communication • Optimized Communication: Compress and Optimize data communication • Class Loading • If possible, avoid to download stubs Protocol Optimization • The idea is to de-couple the connection between the client and the server using mediators. Mobile Node Access Node Naming Client RMIAgent RMIProxy Wireless Link Optimized RMI Mobile Node FakeStub FakeStubs Access Node Registry Registry Agent Agent Proxy Proxy Server Server Cache Cache Monads Monads Registry Registry Client Client Client Client Registry Registry Server Server Optimized RMI Mobile Node FakeStub FakeStubs Access Node Registry Registry Agent Agent Proxy Proxy Server Server Cache Cache Monads Monads Registry Registry Client Client Client Client Registry Registry Server Server Optimized Remote Invocation Client Client RMI RMI Agent Agent Registry Registry RMI RMI Proxy Proxy Header Protocol Ack Lookup() In cache? lookup Lookup() ServerRef InternalRef AgentRef Header Protocol Cache and mark for sync dirty() First? Lease Ack Header dirty() count[ref]++ Protocol Ack Lease DGCAck Header Protocol Ack DGCAck sayHello () sayHello() sayHello () “Hello World” “Hello World” “Hello World” ... clean() Last? clean() clean result clean result clean() clean result Server Server Comparison between RMI and RMI Java RMI Optimized RMI Improvement Registry Invocation 7.1 sec 1.7 sec Remote Invocation 1.3 sec 0.6 sec 8.4 sec 2.3 sec 417% 216% 365% Total Test Arrangements • Operating Systems • • Clients: • Windows98 • Linux (Red Hat 6.1, kernel 2.2.14) Server • Windows NT (SP 6) • Linux (Red Hat 6.1, kernel 2.2.14) Test Arrangements • Java Virtual Machine • Sun JDK 1.2.2 (Linux and Windows) • Wireless communication • GSM HSCSD (5 configurations) • Benchmark Suite • KaRMI from University of Karlsruhe Lookup Results (windows) Lookup Differences Invocation Results Image Uplink (Linux) Invocation Results Two-way Text uplink Nomadic RMI • The previous solution does not support mobility • If the connection between mobile host and RMI Agent is interrupted the system is in an unstable state • RMI (Nomadic RMI) Protocol addresses this problem • It allows Handover between different access points Nomadic RMI Enhancing The Middleware Layer Wireless CORBA Issues of CORBA in Nomadic Environment • IIOP servers are not expected to change their transport connection endpoint • IIOP and the transport connections are supposed to be reliable • It is not possible to change network interface during an IIOP connection • Connections are expected to enjoy high bandwidth Wireless CORBA – Architecture Home domain Home Location Agent Terminal Bridge Terminal Domain Access Bridge Access Bridge GIOP tunnel Visited domain Access Bridge Access Bridge wCORBA Framework • Mobile IOR • • Identifies the terminal on which the target object resides And its Access Bridge • Home Location Agent • Keeps track of the current location of the terminal • Access Bridge • End-point of the GIOP tunnel in the network side • Terminal Bridge • GIOP tunnel wCORBA Framework • Terminal Bridge • End-point of the GIOP tunnel on the terminal side • GIOP tunnel • Is the means to transmit GIOP messages between the Terminal Bridge and the Access Bridge Wireless CORBA - GIOP Tunneling Protocol CORBA invocations Object Object GIOP messages GIOP GTP GIOP GTP msgs GTP GTP adaptation layer GTP adaptation layer transport transport Terminal ORB Access Bridge ORB IIOP TCP IIOP messages IIOP TCP TCP byte stream peer ORB Wireless CORBA – Handoff old AB TB new AB HLA start_handoff HandoffTunnelRequest transport_address_request Establishment of transport connectivity EstablishTunnelRequest location_upadte EstablishTunnelReply ArrivingTerminalNotification HandoffTunnelReply handoff_completed ReleaseTunnelRequest ReleaseTunnelReply HandoffNotification notify other ABs DepartingTerminalNotification report_handoff_status