* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download IP Classes - La Salle University
Dynamic Host Configuration Protocol wikipedia , lookup
IEEE 802.1aq wikipedia , lookup
Network tap wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Computer network wikipedia , lookup
Distributed firewall wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Airborne Networking wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
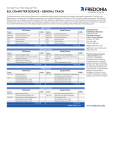
IP Addresses Based Computer Networks and Internets (Comer) CSIT 220 (Blum) 1 IP Layer Recall that starting at the IP layer, TCP/IP provided a logical homogeneity (software) that could mask any underlying physical heterogeneity (hardware). Moreover, the IP layer was responsible for delivering the messages from source to destination. CSIT 220 (Blum) 2 Intranet Businesses liked the services (HTTP, FTP, SMTP, telnet, etc.) offered by the TCP/IP model but they did not necessarily want to be connected to the Internet, so they started setting up intranets. An intranet is a set-up like the Internet (having browsers, email, etc.) but not connected to the outside world. CSIT 220 (Blum) 3 Intranet (cont.) With “tunneling”, companies can send private messages through the public network, using the public network with special encryption/decryption and other security safeguards to connect one part of their intranet to another. Allows a public transmission line to be used as part of a private network. If a public line is used as part of a private network, that network is called a Virtual Private Network CSIT 220 (Blum) 4 Intranet (Cont.) Typically, larger enterprises allow users within their intranet to access the public Internet through firewall servers that have the ability to screen messages in both directions so that company security is maintained. When part of an intranet is made accessible to customers, partners, suppliers, or others outside the company, that part becomes part of an extranet. CSIT 220 (Blum) 5 Extranet A private network that uses TCP/IP and the public telecommunication system to securely share part of a business's information with suppliers, vendors, customers, etc. The required security and privacy are gained by using firewall server management, the issuance and use of digital certificates or other means of user authentication, encryption of messages, and the use of virtual private networks (VPN) that tunnel through the public network. CSIT 220 (Blum) 6 Tunneling Tunneling works by adding another protocol, such as Microsoft’s Point-to-Point Tunneling Protocol (PPTP) or Cisco’s or Layer Two Forwarding (L2F). This new protocol is embedded in the TCP/IP packets. This allows organizations to use the Internet to transmit data across a virtual private network (VPN). CSIT 220 (Blum) 7 IP Address The logical (and thus software) destination is denoted by an IP Address. The IP Address provides homogeneity over diverse networks. The IP Address allows a host to change hardware (and thus hardware address) and yet still be found at the software level. Also IP Addresses are assigned in a more logical manner, which can facilitate routing. CSIT 220 (Blum) 8 Prefix/Suffix The routing is facilitated by the fact that an IP Address is hierarchical. It consists of two parts: The first part of the address (starting on the left) is known as the prefix and it identifies the host’s network (the group of computers it belongs to). The second part of the address is known as the suffix and it identifies the individual computer (node) within the above specified network. CSIT 220 (Blum) 9 IP Addressing Scheme In IP(v4) each host is assigned a unique 32-bit number which is the address for the host. To transmit on a TCP/IP internet, a host must know its own IP address as well as that of the destination. We’ll qualify the above statement later. CSIT 220 (Blum) 10 Dotted Decimal Notation Each 8-bit section (known as a byte or octet) of the 32-bit number [IP(v4)] is expressed as a decimal value with periods between them. The combination of eight bits can be in 256=28 states, which are expressed as the numbers 0 through 255. The range of valid addresses which can be assigned is 0.0.0.0 to 255.255.255.255, which barring various reserved addresses is 4,294,967,296=232 The La Salle network is 139.84.0.0 , the computer www.lasalle.edu is 139.84.10.250 CSIT 220 (Blum) 11 Uniqueness Each computer on an internet (or on the Internet) must have a unique address. Two hosts on the same internet can have different network portions and the same node portion. Two hosts on the same internet can have the same network portion and different node portions. Two hosts on the same internet can have different network portions and different node portions. CSIT 220 (Blum) 12 Address Classes The IP address is not divided into equal halves with one half for the network portion, the other for the node potion The addressing scheme tries to accommodate for the fact that Some networks (not many) will contain a vast number of hosts While other networks (very many) will contain a more modest number of hosts Thus the IP Class system was developed. CSIT 220 (Blum) 13 The IP Class System Originally the IP(v4) Addresses were broken into 5 classes: A through E. The dividing line between network portion and node portion of the IP address differed from class to class. The first four bits on the left identify the class to which an address belongs. A, B and C are the primary classes for the addressing, D and E were reserved. CSIT 220 (Blum) 14 Reserved Class Class D is used for multicasting. Class D addresses begin with the first four bits 1110. If a set of hosts uses multicasting, they agree to share the multicast address. When a message is transmitted to the multicast address, each host in the group makes a copy. Class E is reserved for future use. Class E addresses begin with the first four bits 1111. CSIT 220 (Blum) 15 Fig. 18.1 CSIT 220 (Blum) 16 Class A Class A is self-identified by the leftmost bit being a 0. Class A uses the first octet from the left to identify the network and the rest to identity the nodes. It has 7 bits (first octet minus first bit used to indicate class A) to identify networks, so there can be 128 = 27 Class A networks. It has 24 bits (the last three octets) to identify nodes, so there can be 16777216=224 nodes on a Class A network (almost). CSIT 220 (Blum) 17 Reserved Addresses Actually the node addresses consisting of all 1’s and all 0’s are reserved, so the number of Class A nodes is actually 16,777,214=224 – 2 All 0’s (in the suffix) is reserved to refer to the network itself. All 1’s (in the suffix) is used to broadcast on the network. CSIT 220 (Blum) 18 Class B Class B is self-identified by the first two bits being a 10. Class B uses the first two octets from the left to identify the network and the rest to identity the nodes It has 14 bits (first two octet minus first two bits used to indicate class B) to identify networks, so there can be 16384 = 214 Class B networks. It has 16 bits (the last two octets) to identify nodes, so there can be 65534=216 –2 nodes on a Class B network. CSIT 220 (Blum) 19 Class C Class C is self-identified by the first three bits being a 110. Class C uses the first three octets from the left to identify the network and the remaining one to identity the nodes. It has 21 bits (first three octet minus first three bits used to indicate class C) to identify networks, so there can be 2097152 = 221 Class C networks. It has 8 bits (the last octet) to identify nodes, so there can be 254 =28 –2 nodes on a Class C network. CSIT 220 (Blum) 20 Fig. 18.5 These are all off by 2 because it is neglected by node addresses (suffixes) reserved for the network and broadcasting CSIT 220 (Blum) 21 Computing Address Class In Class A, the first octet starts with a 0, thus the smallest number is 0 0 0 0 0 0 0 And the largest number (in Class A) is 0 0 1 1 1 1 1 1 1 So in decimal-dot notation, Class A addresses start with a number between 0 and 127 CSIT 220 (Blum) 22 CSIT 220 (Blum) 23 Computing Address Class In Class B, the first octet starts with a 10, thus the smallest number is 1 0 0 0 0 0 0 0 And the largest number is 1 0 1 1 1 1 1 1 So in decimal-dot notation, Class B addresses start with a number between 128 and 191 www.lasalle.edu (139.84.10.250) is Class B CSIT 220 (Blum) 24 CSIT 220 (Blum) 25 Computing Address Class In Class C, the first octet starts with a 110, thus the smallest number is 1 0 0 0 0 0 0 1 1 1 And the largest number is 1 1 1 0 1 1 So in decimal-dot notation, Class C addresses start with a number between 192 and 223 CSIT 220 (Blum) 26 CSIT 220 (Blum) 27 Determining class from first four bits CSIT 220 (Blum) 28 subnet A Class B network (like LaSalle’s) can have 65534 hosts. To manage traffic within the network, it is useful to break the network into subnetworks (subnets). On TCP/IP networks, subnets are defined as all devices whose IP addresses have the same prefix. But Class B has a two-octet prefix, so wouldn’t all 65534 of the hosts be on the same subnet? CSIT 220 (Blum) 29 Subnet mask Dividing a network into subnets is useful for both security and performance reasons. The division of the prefix and suffix portions was made more flexible by using subnet masks. In addition to setting an IP address, one also sets a subnet mask which specifies which portion of the address is used to identify the network and which portion is used to identify the hosts within a network. The 1’s in the subnet mask correspond to the network part, the 0’s correspond to the host part. CSIT 220 (Blum) 30 Subnet mask By convention, the bits for the network address are all set to 1 It would also work if the bits were set exactly the same as in the network address (prefix). A typical subnet mask looks like 11111111.11111111.11110000.0000000 0. One extracts the subnet address by performing a bitwise AND operation on the mask and the IP address. See previous lecture (c362_f03_13.ppt) for example. CSIT 220 (Blum) 31 CIDR The use of subnet masking instead of classes sometimes goes by the name Classless Inter-Domain Routing (CIDR). CSIT 220 (Blum) 32 Address Authority IP addresses must be unique. The network portion (prefix) is assigned by an external agency. The host portion (suffix) is assigned by the network administrator. Initially the external assigning was done by InterNIC. CSIT 220 (Blum) 33 InterNIC A collaborative project between AT&T and Network Solutions, Inc. (NSI) supported by the National Science Foundation. The distribution of IP addresses was taken over, but InterNIC still maintains a database (directory) of IP addresses, domain names, etc. It also performs some outreach and educational services. CSIT 220 (Blum) 34 IANA ICANN The responsibility for overseeing IP distribution was first taken over by IANA (Internet Assigned Number Authority) and then by ICANN (Internet Corporation of Assigned Names and Numbers). The Internet Service Providers (ISP) control blocks of addresses assigned to them. They divide them up and lease them to various organizations. CSIT 220 (Blum) 35 Special IP Addresses Network Addresses: IP reserves the host (suffix) address of 0’s for a network Direct Broadcast: IP reserves the host (suffix) address of 1’s for broadcasting within the network Limited Broadcast: Used during system startup by a computer that does not know its IP address. The entire prefix and suffix are assigned all 1’s for the local network. This Computer: Used by a computer to define its address. The computer needs to send or receive packets to determine its address on the network. This happens during startup. IP reserves the address of all zeros to mean the initial host computer. CSIT 220 (Blum) 36 LoopBack Used to test network applications. Can test computer-to-computer applications using one computer by forcing a packet down through the protocol stack by using the loopback address. The application uses the loopback address to send the data to “another” application which is running on the same machine. During loopback testing, no packets leave the computer. The network prefix of 127 is reserved for loopback. Any suffix is used. (Reduces the number of Class A networks.) CSIT 220 (Blum) 37 Ping localhost CSIT 220 (Blum) 38 Berkeley Broadcast Address Form Recall TCP/IP was distributed with a version of Unix put out by Berkeley. In that version of TCP/IP, all 0’s in the suffix is used for as broadcasting (instead of all 1’s). Many people used this version, so now there are standard broadcasts and Berkeley broadcasts. CSIT 220 (Blum) 39 Routers and IP Addressing Routers are also given IP addresses, actually they are given 2 or more addresses since a router connects to more than one physical network. To make network administrator’s lives easier, they often assign the same suffix to the various router addresses. (The prefixes must of course be different.) CSIT 220 (Blum) 40 Multi-Homing Sometimes computers also have multiple IP addresses (and multiple NIC cards). If a host computer connects to multiple networks, it is called multi-homed. This may increase reliability and performance, since it is still networked if only one of the networks goes down. CSIT 220 (Blum) 41 Source/Destination Unknown In the simplest scenario, a computer must know its own IP address (the source) as well as the destination IP address. But this is not always the case. CSIT 220 (Blum) 42 Source or destination not known In some situations (when using Dynamic Host Configuration Protocol DHCP), a host does not initially know its own IP address, and it must transmit at least one message without knowing its eventual IP Address A user does not have to know the destination IP address but can use instead the domain name. Sometimes the actual destination address is hidden behind a firewall and is not known to the source. CSIT 220 (Blum) 43 DHCP Dynamic Host Configuration Protocol is a protocol for assigning IP addresses dynamically. A device’s IP address may change every time it connects to the network. It is even possible to change the address while still connected. CSIT 220 (Blum) 44 DHCP (cont.) In some situations this can simplify a network administrator’s job since he or she does not have to assign addresses manually. Many ISPs use dynamic IP addressing for dial-up users. CSIT 220 (Blum) 45 Checking for DHCP CSIT 220 (Blum) 46 Checking for DHCP CSIT 220 (Blum) 47 Checking for DHCP CSIT 220 (Blum) 48 Checking for DHCP CSIT 220 (Blum) 49 Checking for DHCP CSIT 220 (Blum) 50 Ipconfig /all CSIT 220 (Blum) 51 Domain name A user does not have to know an IP address, a user often knows a domain name which stands in for one or more IP addresses. Also a given IP may have more than one domain name. Because the Internet is based on IP addresses, not domain names, every Web server requires a Domain Name System (DNS) server to translate domain names into IP addresses. CSIT 220 (Blum) 52 TLD Every domain name has a suffix that indicates which top level domain (TLD) it belongs to. There are only a limited number of such domains. For example: gov - Government agencies edu - Educational institutions org - Organizations (nonprofit) mil - Military com - commercial business net - Network organizations ca - Canada A new set came out recently. CSIT 220 (Blum) 53 Whois (a service for looking up domain names) CSIT 220 (Blum) 54 Whois www.lasalle.edu CSIT 220 (Blum) 55 NAT If the destination address is behind a firewall, it is not known to the source. In such a case, Network Address Translation (NAT) is required. NAT allows a LAN to use one set of IP addresses for internal traffic and a second set for external traffic. A NAT box is located where the LAN meets the Internet and it makes all necessary translations. CSIT 220 (Blum) 56 NAT (Cont.) NAT serves two main purposes: Provides a type of firewall by hiding internal IP addresses. Enables a company to use more internal IP addresses. Since they're used internally only, there's no conflict with IP addresses used by other companies and organizations. CSIT 220 (Blum) 57 IP Spoofing Sometimes the source address is faked. A hacker might gain unauthorized access to computers by sending messages to a computer with a faked source IP address, masquerading as a trusted host. To engage in IP spoofing, a hacker must Discover the IP address of a trusted host. Change the packet headers so they appear to come from that host. CSIT 220 (Blum) 58 Other References http://www.whatis.com http://www.webopdeia.com http://public.pacbell.net/dedicated/cidr. html http://www.netsol.com/cgibin/whois/whois CSIT 220 (Blum) 59