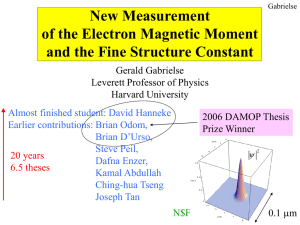
PDF
... where Hint acts on the Hilbert spaces of more than one subsystem. Two situations are possible: either Hint does not introduce any entanglement in the initial state of the system or Hint builds up entanglement among subsystems. In the first case, no correlations among the subsystems are created so th ...
... where Hint acts on the Hilbert spaces of more than one subsystem. Two situations are possible: either Hint does not introduce any entanglement in the initial state of the system or Hint builds up entanglement among subsystems. In the first case, no correlations among the subsystems are created so th ...
III. Paradoxes in Special Relativity
... point for the General Theory of Relativity and is a key ingredient of Quantum Field Theory. Yet many of its predictions are counter-intuitive. These counter-intuitive predictions produce paradoxes that are not readily explained; yet experimental results have verified the predictions of Special Relat ...
... point for the General Theory of Relativity and is a key ingredient of Quantum Field Theory. Yet many of its predictions are counter-intuitive. These counter-intuitive predictions produce paradoxes that are not readily explained; yet experimental results have verified the predictions of Special Relat ...
Strongly coupled gauge theory - CLASSE Cornell
... After spontaneous symmetry breaking of scalar field φ, it take the vacuum expectation value v every, the fermion also get a mass and become massive(mφ = gv) and the Hamiltonian of fermions come in pairs ±E with |E| ≥ m, ”electrons” and ”holenons” with positive and negative energy separately. The chi ...
... After spontaneous symmetry breaking of scalar field φ, it take the vacuum expectation value v every, the fermion also get a mass and become massive(mφ = gv) and the Hamiltonian of fermions come in pairs ±E with |E| ≥ m, ”electrons” and ”holenons” with positive and negative energy separately. The chi ...
Quantum Computing: The Risk to Existing Encryption Methods
... technology before it is compromised. Second, it would be unknown which data was secure. As will be discussed in this paper, most quantum-based attacks could be interceptions, meaning that it is possible that a message between two legitimate parties could be read without alerting either one. This wou ...
... technology before it is compromised. Second, it would be unknown which data was secure. As will be discussed in this paper, most quantum-based attacks could be interceptions, meaning that it is possible that a message between two legitimate parties could be read without alerting either one. This wou ...
An introduction to the concept of symmetry - Pierre
... This equation corresponds to the most general equation giving finite and stable observable predictions concerning all know particles, and which satisfies a set of fundamental symmetries: It must be invariant under space translation, time translation, rotations and Lorentz transformation The la ...
... This equation corresponds to the most general equation giving finite and stable observable predictions concerning all know particles, and which satisfies a set of fundamental symmetries: It must be invariant under space translation, time translation, rotations and Lorentz transformation The la ...
Probabilistic instantaneous quantum computation
... qubits 1 and 2. In (1/4) n cases the whole state of qubits 3 is projected onto the state resulting from the correct input and she does not have to perform any additional transformation on qubits 3. In the remaining 1⫺(1/4) n cases, the result of the engineer’s Bell-state analysis will not be the rig ...
... qubits 1 and 2. In (1/4) n cases the whole state of qubits 3 is projected onto the state resulting from the correct input and she does not have to perform any additional transformation on qubits 3. In the remaining 1⫺(1/4) n cases, the result of the engineer’s Bell-state analysis will not be the rig ...
The Copenhagen interpretation, and pragmatism1 Willem M. de
... I will restrict myself to the mature form of Bohr’s correspondence principle, developed after the mathematical formalism of quantum mechanics had largely been established (referred to in [3] as the strong form of correspondence, so as to distinguish it from the weak form requiring existence of a cla ...
... I will restrict myself to the mature form of Bohr’s correspondence principle, developed after the mathematical formalism of quantum mechanics had largely been established (referred to in [3] as the strong form of correspondence, so as to distinguish it from the weak form requiring existence of a cla ...
Computability and physical theories - UCSB Physics
... cannot be solved in this way. From this theorem, one shows unsolvability of a variety of other problems, including that of finding rational approximations to certain real numbers. These are called the noncomputable numbers. We briefly summarize this subject below. 3 We begin with a few ground rules. ...
... cannot be solved in this way. From this theorem, one shows unsolvability of a variety of other problems, including that of finding rational approximations to certain real numbers. These are called the noncomputable numbers. We briefly summarize this subject below. 3 We begin with a few ground rules. ...
Document
... Mystery remains: Of the many possibilities for combining quarks with colour into colourless hadrons, only two configurations were found, till now… ...
... Mystery remains: Of the many possibilities for combining quarks with colour into colourless hadrons, only two configurations were found, till now… ...