Convection - Diffusion model of talking bacteria
... bacterial receptor; (3) the accumulation of a critical threshold concentration of the quorum sensing signal generates a concerted response and (4) the cellular response extends beyond physiological changes required to metabolize or detoxify the molecule. When all four criteria are met, a molecule ca ...
... bacterial receptor; (3) the accumulation of a critical threshold concentration of the quorum sensing signal generates a concerted response and (4) the cellular response extends beyond physiological changes required to metabolize or detoxify the molecule. When all four criteria are met, a molecule ca ...
Convection - Diffusion model of talking bacteria
... bacterial receptor; (3) the accumulation of a critical threshold concentration of the quorum sensing signal generates a concerted response and (4) the cellular response extends beyond physiological changes required to metabolize or detoxify the molecule. When all four criteria are met, a molecule ca ...
... bacterial receptor; (3) the accumulation of a critical threshold concentration of the quorum sensing signal generates a concerted response and (4) the cellular response extends beyond physiological changes required to metabolize or detoxify the molecule. When all four criteria are met, a molecule ca ...
MRIB Multicast Routing Information Base
... • MBGP (Multi-protocol BGP) router bgp 65051 neighbor 194.254.101.1 remote-as 1717 address family ipv4 multicast neighbor 194.254.101.1 activate exit-address-family ...
... • MBGP (Multi-protocol BGP) router bgp 65051 neighbor 194.254.101.1 remote-as 1717 address family ipv4 multicast neighbor 194.254.101.1 activate exit-address-family ...
Slide 1
... We expect to see SSM and Embedded-RP being the IPv6 solutions for multicast across multiple domains in the Internet SAP/sdr as it is today will not work, alternatives are being worked on Some argue we only need SSM This makes it very simple for the network for both IPv4 and IPv6, but adds complexity ...
... We expect to see SSM and Embedded-RP being the IPv6 solutions for multicast across multiple domains in the Internet SAP/sdr as it is today will not work, alternatives are being worked on Some argue we only need SSM This makes it very simple for the network for both IPv4 and IPv6, but adds complexity ...
Interdomain IPv6 multicast
... PIM-SM requires an RP for source discovery All routers must use the same RP and somehow know its address Initially packets from a source will be sent to the RP When a host joins a group, join messages are sent hop by hop towards the RP The RP serves as a meeting place between sources and receivers T ...
... PIM-SM requires an RP for source discovery All routers must use the same RP and somehow know its address Initially packets from a source will be sent to the RP When a host joins a group, join messages are sent hop by hop towards the RP The RP serves as a meeting place between sources and receivers T ...
Verifiable Shuffling
... on formal proofs of correctness; both shortcomings are addressed in the current version. We also make some brief comparisons with, and criticisms of some more recent publications which build on the results presented in [23]. In particular, we point out that, in contrast to other protocols, the proto ...
... on formal proofs of correctness; both shortcomings are addressed in the current version. We also make some brief comparisons with, and criticisms of some more recent publications which build on the results presented in [23]. In particular, we point out that, in contrast to other protocols, the proto ...
Introduction to Transport Layer
... layer. At the second arrival, packet 2 arrives and is stored and marked (shaded slot), but it cannot be delivered because packet 1 is missing. At the next arrival, packet 3 arrives and is marked and stored, but still none of the packets can be delivered. Only at the last arrival, when finally a copy ...
... layer. At the second arrival, packet 2 arrives and is stored and marked (shaded slot), but it cannot be delivered because packet 1 is missing. At the next arrival, packet 3 arrives and is marked and stored, but still none of the packets can be delivered. Only at the last arrival, when finally a copy ...
Adult Peripheral Parenteral Nutrition [31152] 31152 Adult Peripheral
... Reason for PERIPHERAL LINE TPN: The patient has - {RX REASON FOR TPN:5000030} ...
... Reason for PERIPHERAL LINE TPN: The patient has - {RX REASON FOR TPN:5000030} ...
Project JXTA 2.0 Super
... • Universal binding mechanism • Peer name -> DNS • All binding operations are implemented as discovery or search of one or more XML documents • Project JXTA does not specify how the search of advertisement is performed ...
... • Universal binding mechanism • Peer name -> DNS • All binding operations are implemented as discovery or search of one or more XML documents • Project JXTA does not specify how the search of advertisement is performed ...
Chapter 9
... • IP fails to deliver datagrams when: – the destination machine is temporarily or permanently disconnected from the network – the TTL reaches zero – intermediate routers are so congested that they can’t process incoming data ...
... • IP fails to deliver datagrams when: – the destination machine is temporarily or permanently disconnected from the network – the TTL reaches zero – intermediate routers are so congested that they can’t process incoming data ...
PowerPoint 프레젠테이션
... potentially large group, with only one copy of the packet stream result in significant traffic reduction, maximizing the use of network bandwidth. unicast applications can use TCP or UDP at the transport layer, multicast applications use UDP. For this reason, the application layer must provide ...
... potentially large group, with only one copy of the packet stream result in significant traffic reduction, maximizing the use of network bandwidth. unicast applications can use TCP or UDP at the transport layer, multicast applications use UDP. For this reason, the application layer must provide ...
(IP) Multicast
... functions suitable for applications transmitting real-time data, such as audio, video or simulation data, over multicast or unicast network services. ...
... functions suitable for applications transmitting real-time data, such as audio, video or simulation data, over multicast or unicast network services. ...
Transmission Control Protocol (TCP)
... Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) are the major protocols operating at Transport Layer. Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) operate very differently and you can choose Transmission Control Protocol (TCP) or User Datagram Protocol (U ...
... Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) are the major protocols operating at Transport Layer. Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) operate very differently and you can choose Transmission Control Protocol (TCP) or User Datagram Protocol (U ...
CUSTOMER_CODE SMUDE DIVISION_CODE SMUDE
... exchanges network management information between a network management console and network devices such as routers, bridges and servers. ...
... exchanges network management information between a network management console and network devices such as routers, bridges and servers. ...
draft-gu-ppsp-tracker-protocol-02
... • Less signaling traffic • Also some “reasonable” tech on network coding using hybrid pullpush mode ...
... • Less signaling traffic • Also some “reasonable” tech on network coding using hybrid pullpush mode ...
Constraints on Automated Key Management for Routing Protocols
... • If something goes wrong with routing (or with security), there has to be a way to recover • If the routing protocol depends upon AKM, then AKM can’t depend upon the routing protocol – For OSPF & IS-IS, AKM **must** only operate between directly attached devices, using link layer – You can’t depend ...
... • If something goes wrong with routing (or with security), there has to be a way to recover • If the routing protocol depends upon AKM, then AKM can’t depend upon the routing protocol – For OSPF & IS-IS, AKM **must** only operate between directly attached devices, using link layer – You can’t depend ...
The View-Update Problem
... View Processing create view PresSuite as select * from Room where NrBeds = 2 select * from PresSuite p natural join Reservation s where Cost > 85 and ArrivalDate = “10 May” = select * from (select * from Room where NrBeds = 2) p natural join Reservation s where Cost > 85 and ArrivalDate = “10 May” ...
... View Processing create view PresSuite as select * from Room where NrBeds = 2 select * from PresSuite p natural join Reservation s where Cost > 85 and ArrivalDate = “10 May” = select * from (select * from Room where NrBeds = 2) p natural join Reservation s where Cost > 85 and ArrivalDate = “10 May” ...
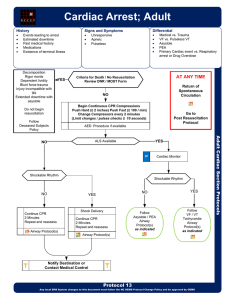
Cardiac Arrest
... Uterine Displacement moving uterus to the patient’s left side. IV/IO access preferably above diaphragm. Defibrillation is safe at all energy levels. · Consider mechanical CPR (compression) device if available. · Refer to Dialysis / Renal Failure protocol caveats when faced with dialysis / renal fail ...
... Uterine Displacement moving uterus to the patient’s left side. IV/IO access preferably above diaphragm. Defibrillation is safe at all energy levels. · Consider mechanical CPR (compression) device if available. · Refer to Dialysis / Renal Failure protocol caveats when faced with dialysis / renal fail ...
Bilevel programming, pricing problems and Stackelberg games
... A bilevel optimization problem consists in an optimization problem in which some of the constraints specify that a subset of variables must be an optimal solution to another optimization problem. This paradigm is particularly appropriate to model competition between agents, a leader and a follower, ...
... A bilevel optimization problem consists in an optimization problem in which some of the constraints specify that a subset of variables must be an optimal solution to another optimization problem. This paradigm is particularly appropriate to model competition between agents, a leader and a follower, ...




![Adult Peripheral Parenteral Nutrition [31152] 31152 Adult Peripheral](http://s1.studyres.com/store/data/008026131_1-d48ced12e0c1aec6da28b090ad0e5917-300x300.png)