IMSL® MATH LIBRARY Special Functions
... S_GAMDF/D_GAMDF (the root is “GAMDF ,” for “Gamma distribution function”) and S_POIDF/D_POIDF (the root is “POIDF,” for “Poisson distribution function”). The precision specific names of the IMSL routines that return or accept the type complex data begin with the letter “C_” or “Z_” for complex or do ...
... S_GAMDF/D_GAMDF (the root is “GAMDF ,” for “Gamma distribution function”) and S_POIDF/D_POIDF (the root is “POIDF,” for “Poisson distribution function”). The precision specific names of the IMSL routines that return or accept the type complex data begin with the letter “C_” or “Z_” for complex or do ...
1. Introduction - Université de Sherbrooke
... unrestricted parameter space <, and the constructions of least favourable sequence of priors for both problems are isomorphic, leading to the same minimax values. In contrast, the restriction to a compact interval θ ∈ [a, b] is quite different and lowers the minimax risk (see Example C below in Sect ...
... unrestricted parameter space <, and the constructions of least favourable sequence of priors for both problems are isomorphic, leading to the same minimax values. In contrast, the restriction to a compact interval θ ∈ [a, b] is quite different and lowers the minimax risk (see Example C below in Sect ...
Ranking Arguments With Compensation
... weakens its target. Think about a committee which recruits young researchers. Once an argument against a candidate is given, even if this argument is attacked, the initial argument is still considered by the members of the committee (but with a lower strength). Consequently, one attack does not nece ...
... weakens its target. Think about a committee which recruits young researchers. Once an argument against a candidate is given, even if this argument is attacked, the initial argument is still considered by the members of the committee (but with a lower strength). Consequently, one attack does not nece ...
Computing Mean, Variance and Standard Deviation
... Since u and v receive values from and return values to the outside of Sort(), they are declared with INTENT(INOUT). Note that w is not declared with any INTENT since it is not a formal argument. In this subroutine, if u is greater than v, they are not in order and the three assignment statements exc ...
... Since u and v receive values from and return values to the outside of Sort(), they are declared with INTENT(INOUT). Note that w is not declared with any INTENT since it is not a formal argument. In this subroutine, if u is greater than v, they are not in order and the three assignment statements exc ...
n - QMplus
... mathematical functions are included in the palettes; the rest you have to type yourself. The rules for using functions in Maple are much the same as in mathematics: the name of the function must be followed immediately by an opening parenthesis, zero or more values separated by commas, and a closing ...
... mathematical functions are included in the palettes; the rest you have to type yourself. The rules for using functions in Maple are much the same as in mathematics: the name of the function must be followed immediately by an opening parenthesis, zero or more values separated by commas, and a closing ...
pass-by-reference - Emory`s Math Department
... The Pass-by-reference mechanism - the agreement (cont.) For the called method: • First, the called method uses the reference (= address) stored in the parameter variables to locate the actual parameter • Once the actual parameter have been located, the called method can subsequently obtain the info ...
... The Pass-by-reference mechanism - the agreement (cont.) For the called method: • First, the called method uses the reference (= address) stored in the parameter variables to locate the actual parameter • Once the actual parameter have been located, the called method can subsequently obtain the info ...
Examples - Department of Computer and Information Science
... printf(“Triangular number %d is %d\n”, 10, calculate_triangular_number(10)); printf(“Triangular number %d is %d\n”, 20, calculate_triangular_number(20)); printf(“Triangular number %d is %d\n”, 50, calculate_triangular_number(50)); return 0; ...
... printf(“Triangular number %d is %d\n”, 10, calculate_triangular_number(10)); printf(“Triangular number %d is %d\n”, 20, calculate_triangular_number(20)); printf(“Triangular number %d is %d\n”, 50, calculate_triangular_number(50)); return 0; ...
Scripting Languages
... • Call models from your scripts – Instead of rewriting a model as a script, reference the model’s toolbox and call it as a tool ...
... • Call models from your scripts – Instead of rewriting a model as a script, reference the model’s toolbox and call it as a tool ...
CALL Statement
... Subroutine subprograms have many features in common with function subprograms: They are program units designed to perform particular tasks under the control of some other program unit. The have the same basic form: each consists of a heading, a specification part, an execution part, and an END state ...
... Subroutine subprograms have many features in common with function subprograms: They are program units designed to perform particular tasks under the control of some other program unit. The have the same basic form: each consists of a heading, a specification part, an execution part, and an END state ...
Overview of Leda Programming Language
... Leda was developed in the early 1990's by Timothy A. Budd an associate professor at Oregon State University Corvallis. The attempt to define a language that would support multiple programming paradigms was inspired by Budd's excitement about OOP and other innovations occuring in the study of program ...
... Leda was developed in the early 1990's by Timothy A. Budd an associate professor at Oregon State University Corvallis. The attempt to define a language that would support multiple programming paradigms was inspired by Budd's excitement about OOP and other innovations occuring in the study of program ...
Change log for Magma V2.20-6 - Magma Computational Algebra
... Some anomalous behaviour in the hashing of number field elements and order elements has been fixed. This manifested in poor performance in some algorithms. Corrections have been made to the real precision used in computing the LLL (basis) of an order. Insufficient precision lead to a result which ...
... Some anomalous behaviour in the hashing of number field elements and order elements has been fixed. This manifested in poor performance in some algorithms. Corrections have been made to the real precision used in computing the LLL (basis) of an order. Insufficient precision lead to a result which ...
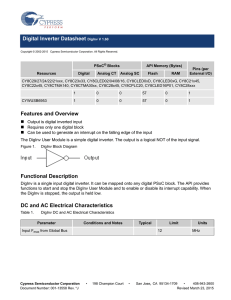
Digital Inverter Datasheet DigInv V 1.60 Features and Overview
... The Application Programming Interface (API) routines are provided as part of the user module to allow the designer to deal with the module at a higher level. This section specifies the interface to each function together with related constants provided by the “include" files. Note In this, as in all ...
... The Application Programming Interface (API) routines are provided as part of the user module to allow the designer to deal with the module at a higher level. This section specifies the interface to each function together with related constants provided by the “include" files. Note In this, as in all ...
Introduction to Programming in Python
... - input: a comma separated list of values - returns: the minimum or maximum value in the list • Click here to see a complete list of Python built-in functions. We will continue to work with some of them in later modules. ...
... - input: a comma separated list of values - returns: the minimum or maximum value in the list • Click here to see a complete list of Python built-in functions. We will continue to work with some of them in later modules. ...
explicit rules: input-output formulas
... What similarities do you see between the Now-Next rule and the Input-Output rule? Repetitive addition can be written as multiplication resulting in the coefficient in the input-output rule ...
... What similarities do you see between the Now-Next rule and the Input-Output rule? Repetitive addition can be written as multiplication resulting in the coefficient in the input-output rule ...
EXAMPLE: /* A Program to add N even positive numbers: Sum= 2+4
... 1- Main program call function ADD_Even(N, sum); and assign the returned value SUM in function to its name ADD. 2- The value of the name of the function (SUM) is assigned to variable sumx. 3- The main function will continue executing statements in sequence after the call statement. 4- Also, the input ...
... 1- Main program call function ADD_Even(N, sum); and assign the returned value SUM in function to its name ADD. 2- The value of the name of the function (SUM) is assigned to variable sumx. 3- The main function will continue executing statements in sequence after the call statement. 4- Also, the input ...
2.1 Functions and their Graphs
... input values with output values. • The set of input values is called the domain. Also called x-coordinate. • The set of output values is called the range. Also called y-coordinate. • A relation as a function provided there is exactly one output for each input. NOTE: x values do not repeat. • It is N ...
... input values with output values. • The set of input values is called the domain. Also called x-coordinate. • The set of output values is called the range. Also called y-coordinate. • A relation as a function provided there is exactly one output for each input. NOTE: x values do not repeat. • It is N ...
function - City Tech OpenLab
... • Does one thing. If it does too many things, it should be broken down into multiple functions ...
... • Does one thing. If it does too many things, it should be broken down into multiple functions ...
Notes: Evaluating Functions
... A/S: Addition/Subtraction (these two operations are of equal importance – they should be done as they appear from left to right in the expression) If everything is entered correctly, the calculator will follow order of operations. --------------------------------------------------------------------- ...
... A/S: Addition/Subtraction (these two operations are of equal importance – they should be done as they appear from left to right in the expression) If everything is entered correctly, the calculator will follow order of operations. --------------------------------------------------------------------- ...
2.1 Functions and their Graphs
... • In an equation, the input variable is called the independent variable. • The output variable is called the dependent variable and depends on the value of the input variable. • In y=2x-7 ….. X is the independent var. Y is the dependant var. • The graph of an equation in 2 variables is the collecti ...
... • In an equation, the input variable is called the independent variable. • The output variable is called the dependent variable and depends on the value of the input variable. • In y=2x-7 ….. X is the independent var. Y is the dependant var. • The graph of an equation in 2 variables is the collecti ...
Esame di Microeconomia avanzata (16 aprile 2004)
... inferior input and a normal input an increase in its price will reduce its use (either by increasing or decreasing respectively the level of output). In other words, an input is inferior ( ~ x i/y < 0) if and only if is regressive (y/ wi > 0). III) Discuss briefly the convexity of the profit fu ...
... inferior input and a normal input an increase in its price will reduce its use (either by increasing or decreasing respectively the level of output). In other words, an input is inferior ( ~ x i/y < 0) if and only if is regressive (y/ wi > 0). III) Discuss briefly the convexity of the profit fu ...
2.1 Functions and their Graphs
... • In an equation, the input variable is called the independent variable. • The output variable is called the dependent variable and depends on the value of the input variable. • In y=2x-7 ….. X is the independent var. Y is the dependant var. • The graph of an equation in 2 variables is the collecti ...
... • In an equation, the input variable is called the independent variable. • The output variable is called the dependent variable and depends on the value of the input variable. • In y=2x-7 ….. X is the independent var. Y is the dependant var. • The graph of an equation in 2 variables is the collecti ...
Chapter 8 Subroutines and Control Abstraction June 25, 2015
... the frame; less likely to see this on RISC architecture As you might surmise, compilers on CISC architectures attempt usually to make use of that complexity. ...
... the frame; less likely to see this on RISC architecture As you might surmise, compilers on CISC architectures attempt usually to make use of that complexity. ...
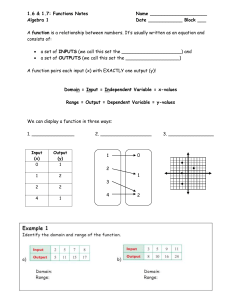
Algebra 1
... Remember: a function is a relationship between input and output values where each input is paired with exactly one output. The easiest way to determine a function: X cannot repeat! (y can) ...
... Remember: a function is a relationship between input and output values where each input is paired with exactly one output. The easiest way to determine a function: X cannot repeat! (y can) ...
Function Identification PowerPoint
... any two points lie on the same vertical line. If there are not two points on the same vertical line then the relation is a function. If there are two points on the same vertical line then the relation is NOT a function ...
... any two points lie on the same vertical line. If there are not two points on the same vertical line then the relation is a function. If there are two points on the same vertical line then the relation is NOT a function ...