Arrays - CIS @ Temple University
... Summary • Entire array can be passed as parameter to a method • Method return value can be an array • Partially filled array usually stores values in initial segment, use an int to track how many are used • Privacy leak caused by returning array corresponding to private instance variable JAVA: An I ...
... Summary • Entire array can be passed as parameter to a method • Method return value can be an array • Partially filled array usually stores values in initial segment, use an int to track how many are used • Privacy leak caused by returning array corresponding to private instance variable JAVA: An I ...
COP2800 * Computer Programming Using JAVA
... PICTURE CREDIT: http://users.soe.ucsc.edu/~charlie/book/notes/summary1-4/sld016.htm ...
... PICTURE CREDIT: http://users.soe.ucsc.edu/~charlie/book/notes/summary1-4/sld016.htm ...
Chapter 1
... • In the distant past, programmers wrote programs in machine language. • Programmers developed higher level programming languages to make things easier. • The first of these was assembler. • Assembler made things easier but was also processor dependent. ...
... • In the distant past, programmers wrote programs in machine language. • Programmers developed higher level programming languages to make things easier. • The first of these was assembler. • Assembler made things easier but was also processor dependent. ...
JavaHTP7e_01
... In this chapter you will learn: Basic computer hardware and software concepts. Basic object technology concepts, such as classes, objects, attributes, behaviors, encapsulation, inheritance and polymorphism. The different types of programming languages. Which programming languages are most wi ...
... In this chapter you will learn: Basic computer hardware and software concepts. Basic object technology concepts, such as classes, objects, attributes, behaviors, encapsulation, inheritance and polymorphism. The different types of programming languages. Which programming languages are most wi ...
Chapter 1
... In this chapter you will learn: Basic computer hardware and software concepts. Basic object technology concepts, such as classes, objects, attributes, behaviors, encapsulation, inheritance and polymorphism. The different types of programming languages. Which programming languages are most wi ...
... In this chapter you will learn: Basic computer hardware and software concepts. Basic object technology concepts, such as classes, objects, attributes, behaviors, encapsulation, inheritance and polymorphism. The different types of programming languages. Which programming languages are most wi ...
CSC110_Programming_1_Overview
... Aspects of a computer program that must be designed: – The logical flow of the instructions – The mathematical procedures – The layout of the programming statements – The appearance of the screens – The way information is presented to the user – The program’s “user friendliness” – Manuals, help syst ...
... Aspects of a computer program that must be designed: – The logical flow of the instructions – The mathematical procedures – The layout of the programming statements – The appearance of the screens – The way information is presented to the user – The program’s “user friendliness” – Manuals, help syst ...
Python
... • Actual code length of Python is 5-10 times shorter than equivalent C++ code • Python is sometimes referred to and used as a glue language that combines several component written in C++ To Perl: • Both share similar roots (Unix, scripting), and similar features. • Perl is harder to maintain based o ...
... • Actual code length of Python is 5-10 times shorter than equivalent C++ code • Python is sometimes referred to and used as a glue language that combines several component written in C++ To Perl: • Both share similar roots (Unix, scripting), and similar features. • Perl is harder to maintain based o ...
Document
... “Egad, I think the interpreter is the hardest to be understood of the two!” — Richard Brinsley Sheridan ...
... “Egad, I think the interpreter is the hardest to be understood of the two!” — Richard Brinsley Sheridan ...
unit 1
... Names should be chosen carefully - they play a central role in the readability of the program and is part of its documentation; they should be: ...
... Names should be chosen carefully - they play a central role in the readability of the program and is part of its documentation; they should be: ...
Chapter 1
... • In the distant past, programmers wrote programs in machine language. • Programmers developed higher level programming languages to make things easier. • The first of these was assembler. • Assembler made things easier but was also processor dependent. ...
... • In the distant past, programmers wrote programs in machine language. • Programmers developed higher level programming languages to make things easier. • The first of these was assembler. • Assembler made things easier but was also processor dependent. ...
Chapter 3 Control Methods
... Don’t use floating-point values for equality checking in a loop control. Since floating-point values are approximations, using them could result in imprecise counter values and inaccurate results. This example uses int value for data. If a floating-point type value is used for data, (data != 0) may ...
... Don’t use floating-point values for equality checking in a loop control. Since floating-point values are approximations, using them could result in imprecise counter values and inaccurate results. This example uses int value for data. If a floating-point type value is used for data, (data != 0) may ...
Java
... typically use the following building blocks: Classes and methods from class libraries, classes and methods you create yourself and classes and methods that others create and make available to you. ...
... typically use the following building blocks: Classes and methods from class libraries, classes and methods you create yourself and classes and methods that others create and make available to you. ...
Chapter 3 Control Methods
... To write expressions using the conditional operator (§3.5) . To display formatted output using the System.out.printf method and to format strings using the String.format method (§3.6). To know the rules governing operand evaluation order, operator precedence, and operator associativity (§§3.7- ...
... To write expressions using the conditional operator (§3.5) . To display formatted output using the System.out.printf method and to format strings using the String.format method (§3.6). To know the rules governing operand evaluation order, operator precedence, and operator associativity (§§3.7- ...
Document
... “Egad, I think the interpreter is the hardest to be understood of the two!” — Richard Brinsley Sheridan ...
... “Egad, I think the interpreter is the hardest to be understood of the two!” — Richard Brinsley Sheridan ...
Multimedia on the Web
... designed to react whenever events occur • JScript – a Microsoft version of JavaScript • C# – a Microsoft version of Java • ActiveX – an open set of technologies for integrating components on the Internet and within Microsoft applications • VBScript – an object-oriented scripting language that Micros ...
... designed to react whenever events occur • JScript – a Microsoft version of JavaScript • C# – a Microsoft version of Java • ActiveX – an open set of technologies for integrating components on the Internet and within Microsoft applications • VBScript – an object-oriented scripting language that Micros ...
Problem Solving - Welcome to Computer Science
... • Java programs are designed to be able to run on any kind of computer when downloaded from the Web. • With most languages, that would mean downloading source code for the program and having a compiler translate it into the machine code for your machine. The user would have to tell the machine to co ...
... • Java programs are designed to be able to run on any kind of computer when downloaded from the Web. • With most languages, that would mean downloading source code for the program and having a compiler translate it into the machine code for your machine. The user would have to tell the machine to co ...
Floats
... reserved word. Reserved words are used by C exclusively. Here are a few: double, char, int, do, float, if, return, sizeof, void,while, typedef, struct, switch, for, else. See the complete list in the Documents section of the course website. Rule #2: An identifier must contain only letters, digit ...
... reserved word. Reserved words are used by C exclusively. Here are a few: double, char, int, do, float, if, return, sizeof, void,while, typedef, struct, switch, for, else. See the complete list in the Documents section of the course website. Rule #2: An identifier must contain only letters, digit ...
Introduction to Computers, the Internet and the Web
... The C preprocessor obeys special commands called preprocessor directives, which indicate that certain manipulations are to be performed on the program before compilation. ©1992-2010 by Pearson Education, Inc. All Rights Reserved. ...
... The C preprocessor obeys special commands called preprocessor directives, which indicate that certain manipulations are to be performed on the program before compilation. ©1992-2010 by Pearson Education, Inc. All Rights Reserved. ...
29_Recursion_part1 - Iowa State University
... Recursive Programming • A method in Java can invoke itself; if set up that way, it is called a recursive method • The code of a recursive method must be structured to handle both the base case and the recursive case ...
... Recursive Programming • A method in Java can invoke itself; if set up that way, it is called a recursive method • The code of a recursive method must be structured to handle both the base case and the recursive case ...
Chapter 1
... Parameter passing by value Copyright © 2004 Pearson Addison-Wesley. All rights reserved. ...
... Parameter passing by value Copyright © 2004 Pearson Addison-Wesley. All rights reserved. ...
Creating a variable
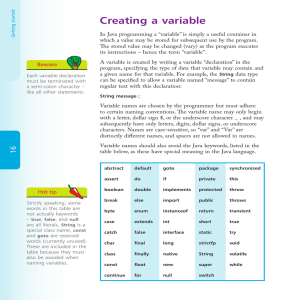
... “gear”, and names that consist of multiple words should capitalize the first letter of each subsequent word, such as “gearRatio” – the so-called “camelCase” naming convention. Once a variable has been declared, it may be assigned an initial value of the appropriate data type using the equals sign = ...
... “gear”, and names that consist of multiple words should capitalize the first letter of each subsequent word, such as “gearRatio” – the so-called “camelCase” naming convention. Once a variable has been declared, it may be assigned an initial value of the appropriate data type using the equals sign = ...
CET3640 – Lecture 7 – Ch 10 – Polymorphism Interfaces
... © Copyright 1992-2012 by Pearson Education, Inc. All Rights Reserved. ...
... © Copyright 1992-2012 by Pearson Education, Inc. All Rights Reserved. ...