Physics 610: Quantum Optics
... notes and some problems will be drawn from Loudon’s texts “The Quantum Theory of Light”, now in its third edition, and from other texts listed below. Also, some use will be made of Eberly and Allen’s short treatise on the two-level atom, and of other now-classic texts. Some classes will include prob ...
... notes and some problems will be drawn from Loudon’s texts “The Quantum Theory of Light”, now in its third edition, and from other texts listed below. Also, some use will be made of Eberly and Allen’s short treatise on the two-level atom, and of other now-classic texts. Some classes will include prob ...
Wave
... Fortunately, the strange rules of quantum physics affect only very small objects, such as individual atoms and electrons. As soon as we have a macroscopic object consisting of many atoms, an experiment becomes more predictable. Typically, a macroscopic object consists of 1024 atoms (Avogadro’s numb ...
... Fortunately, the strange rules of quantum physics affect only very small objects, such as individual atoms and electrons. As soon as we have a macroscopic object consisting of many atoms, an experiment becomes more predictable. Typically, a macroscopic object consists of 1024 atoms (Avogadro’s numb ...
Single and Entangled Photon Sources
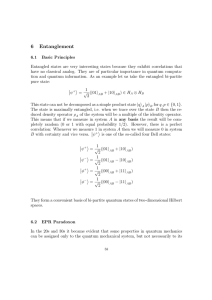
... entangled pair, the other member at any subsequent time regardless of distance is found to have the appropriate correlated value. Quantum entanglement first came about as a criticism to quantum mechanics by Albert Einstein, Boris Podolsky, and Nathan Rosen in a paper describing the EPR paradox. This ...
... entangled pair, the other member at any subsequent time regardless of distance is found to have the appropriate correlated value. Quantum entanglement first came about as a criticism to quantum mechanics by Albert Einstein, Boris Podolsky, and Nathan Rosen in a paper describing the EPR paradox. This ...
An Introduction to: Coherent and Squeezed states
... • Coherent and squeezed states are basic elements of modern day quantum optics. • Consequently, this seminar also provided an introduction to continuous variable quantum optics. • An understading of these states is crucial in order to understand other more striking states such as a quantum optical ...
... • Coherent and squeezed states are basic elements of modern day quantum optics. • Consequently, this seminar also provided an introduction to continuous variable quantum optics. • An understading of these states is crucial in order to understand other more striking states such as a quantum optical ...
ppt - ICTS
... BPP (Bounded-Error Probabilistic PolynomialTime): Class of problems solvable efficiently with use of randomness Note: It’s generally believed that BPP=P BQP (Bounded-Error Quantum Polynomial-Time): Class of problems solvable efficiently by a quantum computer ...
... BPP (Bounded-Error Probabilistic PolynomialTime): Class of problems solvable efficiently with use of randomness Note: It’s generally believed that BPP=P BQP (Bounded-Error Quantum Polynomial-Time): Class of problems solvable efficiently by a quantum computer ...
Another version - Scott Aaronson
... Also for first time, can prove “abstract” version of scheme (involving a classical oracle) is unconditionally secure Same construction yields the first private-key scheme that’s provably “interactively secure” ...
... Also for first time, can prove “abstract” version of scheme (involving a classical oracle) is unconditionally secure Same construction yields the first private-key scheme that’s provably “interactively secure” ...
Abstract
... that it is not continuous but atomistic, not absolute but relative, not classical but quantized. In the ensuing century his heuristic hypotheses were con rmed as facts. They de ne what might be called the \atomic world view." Today we stand on the threshold of a new era: the information age. Far fro ...
... that it is not continuous but atomistic, not absolute but relative, not classical but quantized. In the ensuing century his heuristic hypotheses were con rmed as facts. They de ne what might be called the \atomic world view." Today we stand on the threshold of a new era: the information age. Far fro ...
S. Mayboroda:
... The property of the localization of the eigenfunctions in rough domains or rough materials permeates acoustics, quantum physics, elasticity, to name just a few. Localization on fractal domains was used for noise abatement walls which up to date hold world efficiency record. Anderson localization of ...
... The property of the localization of the eigenfunctions in rough domains or rough materials permeates acoustics, quantum physics, elasticity, to name just a few. Localization on fractal domains was used for noise abatement walls which up to date hold world efficiency record. Anderson localization of ...
Quantum key distribution
Quantum key distribution (QKD) uses quantum mechanics to guarantee secure communication. It enables two parties to produce a shared random secret key known only to them, which can then be used to encrypt and decrypt messages. It is often incorrectly called quantum cryptography, as it is the most well known example of the group of quantum cryptographic tasks.An important and unique property of quantum key distribution is the ability of the two communicating users to detect the presence of any third party trying to gain knowledge of the key. This results from a fundamental aspect of quantum mechanics: the process of measuring a quantum system in general disturbs the system. A third party trying to eavesdrop on the key must in some way measure it, thus introducing detectable anomalies. By using quantum superpositions or quantum entanglement and transmitting information in quantum states, a communication system can be implemented which detects eavesdropping. If the level of eavesdropping is below a certain threshold, a key can be produced that is guaranteed to be secure (i.e. the eavesdropper has no information about it), otherwise no secure key is possible and communication is aborted.The security of encryption that uses quantum key distribution relies on the foundations of quantum mechanics, in contrast to traditional public key cryptography which relies on the computational difficulty of certain mathematical functions, and cannot provide any indication of eavesdropping at any point in the communication process, or any mathematical proof as to the actual complexity of reversing the one-way functions used. QKD has provable security based on information theory, and forward secrecy.Quantum key distribution is only used to produce and distribute a key, not to transmit any message data. This key can then be used with any chosen encryption algorithm to encrypt (and decrypt) a message, which can then be transmitted over a standard communication channel. The algorithm most commonly associated with QKD is the one-time pad, as it is provably secure when used with a secret, random key. In real world situations, it is often also used with encryption using symmetric key algorithms like the Advanced Encryption Standard algorithm. In the case of QKD this comparison is based on the assumption of perfect single-photon sources and detectors, that cannot be easily implemented.