SINGULAR PERTURBATIONS FOR DIFFERENCE
... there is a "boundary layer" only at the right end point, regardless of the sign of the coefficient ak in (1.1) (this discrepancy will be explained in § 5). In fact, the initial value problem for the difference equation (1.1) together with Y0 = a and Yx = ß is unstable with no boundary layer, while t ...
... there is a "boundary layer" only at the right end point, regardless of the sign of the coefficient ak in (1.1) (this discrepancy will be explained in § 5). In fact, the initial value problem for the difference equation (1.1) together with Y0 = a and Yx = ß is unstable with no boundary layer, while t ...
Minds may be computers but.. - Cognitive Science Department
... to create products, that are valued within one or more cultural settings” and Pinker (1997) has defined it as “the ability to attain goals in the face of obstacles by means of decisions based on rational (truth-obeying) rules.” And although he may have meant it as a joke, Boring’s (1923) definition ...
... to create products, that are valued within one or more cultural settings” and Pinker (1997) has defined it as “the ability to attain goals in the face of obstacles by means of decisions based on rational (truth-obeying) rules.” And although he may have meant it as a joke, Boring’s (1923) definition ...
Coursera – University of Washington
... This course is not a MATLAB tutorial. It is an introductory programming course that uses MATLAB to illustrate general concepts in computer science and programming. Students who successfully complete this course will become familiar with general concepts in computer science, gain an understanding of ...
... This course is not a MATLAB tutorial. It is an introductory programming course that uses MATLAB to illustrate general concepts in computer science and programming. Students who successfully complete this course will become familiar with general concepts in computer science, gain an understanding of ...
SoV - UCSD CSE
... We seek to separate the two types of mutations. Identifying mutations under selection is important for identifying the genetic basis of ...
... We seek to separate the two types of mutations. Identifying mutations under selection is important for identifying the genetic basis of ...
Exact solutions of discrete master equations in terms of continued
... In recent years, the concept of master equations has attracted wide attention. These equations play a major role in the description of systems which do not behave in a deterministic way, but display statistical fluctuations of the system variables. In many cases, e.g. if particle or occupation numbe ...
... In recent years, the concept of master equations has attracted wide attention. These equations play a major role in the description of systems which do not behave in a deterministic way, but display statistical fluctuations of the system variables. In many cases, e.g. if particle or occupation numbe ...
An Algorithm for Fast Convergence in Training Neural Networks
... of the network increases, it should be clear that the training would entail costly hardware due to the exponential growth in the computational complexity. ...
... of the network increases, it should be clear that the training would entail costly hardware due to the exponential growth in the computational complexity. ...
Evolutionary Optimization of Radial Basis Function Classifiers for
... chemical applications [60]. Typically, these publications focus on one particular application problem. Hence, the universality of methods does not become clear. Besides that, most of the publications do not set out the repeatability of results even if a stochastic optimization algorithm is applied. ...
... chemical applications [60]. Typically, these publications focus on one particular application problem. Hence, the universality of methods does not become clear. Besides that, most of the publications do not set out the repeatability of results even if a stochastic optimization algorithm is applied. ...
Algorithm Selection for Combinatorial Search Problems: A Survey
... approaches for solving similar kinds of problem instances. In some scenarios, a new algorithm is clearly superior to previous approaches. In the majority of cases however, a new approach will improve over the current state of the art for only some problem instances. This may be because it employs a ...
... approaches for solving similar kinds of problem instances. In some scenarios, a new algorithm is clearly superior to previous approaches. In the majority of cases however, a new approach will improve over the current state of the art for only some problem instances. This may be because it employs a ...
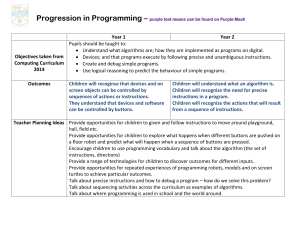
Outcomes Children will recoginse that devices and on screen
... of actions for a Zebra Crossing, a light house, lights and a foundation for the Town Hall during the day and the night, and bridge lights. These can be linked to models such as a fairground wheel where these are available. Use the Espresso Computer Modelling module to manage water at home and then t ...
... of actions for a Zebra Crossing, a light house, lights and a foundation for the Town Hall during the day and the night, and bridge lights. These can be linked to models such as a fairground wheel where these are available. Use the Espresso Computer Modelling module to manage water at home and then t ...
A Study on Swarm Intelligence Techniques in Intrusion Detection
... At the same time it decreases for all other terms (evaporation). Among the discovered rules the best one is selected and augmented to the discovered rules. This is done iteratively until a large base of rules is constructed which can be later on used in test sets as criteria for classifying network ...
... At the same time it decreases for all other terms (evaporation). Among the discovered rules the best one is selected and augmented to the discovered rules. This is done iteratively until a large base of rules is constructed which can be later on used in test sets as criteria for classifying network ...
Genetic algorithm

In the field of artificial intelligence, a genetic algorithm (GA) is a search heuristic that mimics the process of natural selection. This heuristic (also sometimes called a metaheuristic) is routinely used to generate useful solutions to optimization and search problems. Genetic algorithms belong to the larger class of evolutionary algorithms (EA), which generate solutions to optimization problems using techniques inspired by natural evolution, such as inheritance, mutation, selection, and crossover.