slides
... The algorithm in words: 1. Divide n elements into groups of 5 2. Find median of each group (How? How long?) 3. Use Select() recursively to find median x of the n/5 medians 4. Partition the n elements around x. Let k = rank(x) 5. if (i == k) then return x if (i < k) then use Select() recursively to ...
... The algorithm in words: 1. Divide n elements into groups of 5 2. Find median of each group (How? How long?) 3. Use Select() recursively to find median x of the n/5 medians 4. Partition the n elements around x. Let k = rank(x) 5. if (i == k) then return x if (i < k) then use Select() recursively to ...
pptx - Neural Network and Machine Learning Laboratory
... – Problem has natural hierarchy with independent branches – Speed-up happens when we can find short-cuts during partition/merge that can be taken ...
... – Problem has natural hierarchy with independent branches – Speed-up happens when we can find short-cuts during partition/merge that can be taken ...
UNIT-I - WordPress.com
... Big oh is used to represent the upper bound of an algorithm’s running time, i.e. we can give largest amount of time taken by the algorithm to complete. But whereas omega notation represent the lower bound of an algorithm’s running time, i.e. we can give smallest amount of time taken by the algorit ...
... Big oh is used to represent the upper bound of an algorithm’s running time, i.e. we can give largest amount of time taken by the algorithm to complete. But whereas omega notation represent the lower bound of an algorithm’s running time, i.e. we can give smallest amount of time taken by the algorit ...
Introduction to Randomized Algorithms.
... Application of Yao’s Lemma Lemma: A lower bound on the expected number of probes required by any randomized algorithm to solve the Find-bill problem is (n + 1)/2. Proof: We assume that the bill is located in any one of the n boxes uniformly at random. We only consider deterministic algorithms that ...
... Application of Yao’s Lemma Lemma: A lower bound on the expected number of probes required by any randomized algorithm to solve the Find-bill problem is (n + 1)/2. Proof: We assume that the bill is located in any one of the n boxes uniformly at random. We only consider deterministic algorithms that ...
I p - Jad Matta
... Lemma: A lower bound on the expected number of probes required by any randomized algorithm to solve the Find-bill problem is (n + 1)/2. Proof: We assume that the bill is located in any one of the n boxes uniformly at random. We only consider deterministic algorithms that does not probe the same box ...
... Lemma: A lower bound on the expected number of probes required by any randomized algorithm to solve the Find-bill problem is (n + 1)/2. Proof: We assume that the bill is located in any one of the n boxes uniformly at random. We only consider deterministic algorithms that does not probe the same box ...
Research Summary - McGill University
... representation of the knowledge of the world. I was very much intrigued by the PSR work, and started working on incorporating PSRs into POMDP control algorithms. Since the representational power of PSRs is equivalent to the belief state representation in POMDPs, one can imagine PSR planning algorith ...
... representation of the knowledge of the world. I was very much intrigued by the PSR work, and started working on incorporating PSRs into POMDP control algorithms. Since the representational power of PSRs is equivalent to the belief state representation in POMDPs, one can imagine PSR planning algorith ...
PPT
... Input: n 2-D points P = {p1,…,pn}; pi=(xi,yi) d(pi,pj) = ( (xi-xj)2+(yi-yj)2)1/2 Output: Points p and q that are closest ...
... Input: n 2-D points P = {p1,…,pn}; pi=(xi,yi) d(pi,pj) = ( (xi-xj)2+(yi-yj)2)1/2 Output: Points p and q that are closest ...
Data Structures Lecture
... Deadlines are always final Submission guidelines must be followed. Name your submission folder in the format RollNo_Name_HW# e.g. 123_Umar_HW#3 Submissions by email will not be accepted ...
... Deadlines are always final Submission guidelines must be followed. Name your submission folder in the format RollNo_Name_HW# e.g. 123_Umar_HW#3 Submissions by email will not be accepted ...
Logarithms in running time
... Example: What is the probability two numbers to be relatively prime? ...
... Example: What is the probability two numbers to be relatively prime? ...
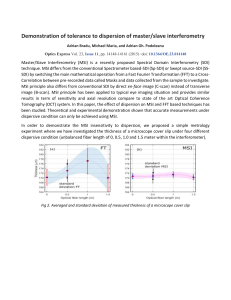
Demonstration of tolerance to dispersion of master/slave interferometry
... technique. MSI differs from the conventional Spectrometer based-SDI (Sp-SDI) or Swept source-SDI (SSSDI) by switching the main mathematical operation from a Fast Fourier Transformation (FFT) to a CrossCorrelation between pre-recorded data called Masks and data collected from the sample to investigat ...
... technique. MSI differs from the conventional Spectrometer based-SDI (Sp-SDI) or Swept source-SDI (SSSDI) by switching the main mathematical operation from a Fast Fourier Transformation (FFT) to a CrossCorrelation between pre-recorded data called Masks and data collected from the sample to investigat ...
Algorithms and Data Structures Algorithms and Data Structures
... The average-case running time of an algorithm A is the function AVTA : N → N where AVTA (n) is the average number of computation steps performed by A on an input of size n. For a genuine average–case analysis we need to know for each n the probability with which each input turns up. Usually we assum ...
... The average-case running time of an algorithm A is the function AVTA : N → N where AVTA (n) is the average number of computation steps performed by A on an input of size n. For a genuine average–case analysis we need to know for each n the probability with which each input turns up. Usually we assum ...
CUSTOMER_CODE SMUDE DIVISION_CODE SMUDE
... required to perform a step should always bound above by a constant. In some instances, count of addition of two numbers might be as one step. In such cases approximation of time efficient becomes critical. This consideration might not justify certain situations. If the numbers involved in a computat ...
... required to perform a step should always bound above by a constant. In some instances, count of addition of two numbers might be as one step. In such cases approximation of time efficient becomes critical. This consideration might not justify certain situations. If the numbers involved in a computat ...
Lecture 2 - Rabie A. Ramadan
... Suppose you are implementing a spreadsheet program, in which you must maintain a grid of cells. Some cells of the spreadsheet contain numbers, but other cells contain expressions that depend on other cells for their value. However, the expressions are not allowed to form a cycle of dependencies: for ...
... Suppose you are implementing a spreadsheet program, in which you must maintain a grid of cells. Some cells of the spreadsheet contain numbers, but other cells contain expressions that depend on other cells for their value. However, the expressions are not allowed to form a cycle of dependencies: for ...