Sample Writing
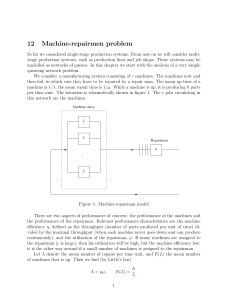
... In other words, we now have a concept of what the worst-case scenario for the number of steps in Euclid’s algorithm looks like. For example, imagine that, for some reason, we want to find the greatest common divisor of two integers that have 5 and 3 digits, respectively. Because of Lame´’s Theorem, ...
... In other words, we now have a concept of what the worst-case scenario for the number of steps in Euclid’s algorithm looks like. For example, imagine that, for some reason, we want to find the greatest common divisor of two integers that have 5 and 3 digits, respectively. Because of Lame´’s Theorem, ...
Research Summary - McGill University
... of knowledge can be essential to an autonomous agent for efficient decision making. Predictive State Representation, PSR, has been developed to provide a maintainable, self-verifiable and learnable representation of the knowledge of the world. I was very much intrigued by the PSR work, and started w ...
... of knowledge can be essential to an autonomous agent for efficient decision making. Predictive State Representation, PSR, has been developed to provide a maintainable, self-verifiable and learnable representation of the knowledge of the world. I was very much intrigued by the PSR work, and started w ...
A Generalized Algorithm for Flow Table Optimization
... We allow the programmer to break a single flow table into multiple sub-tables. To do so, we first create the FDD for the input table, then convert all edges to the desired predicate type. Finally, we run BFS from each node at which we’d like a new table, to a depth equal to the number of fields in t ...
... We allow the programmer to break a single flow table into multiple sub-tables. To do so, we first create the FDD for the input table, then convert all edges to the desired predicate type. Finally, we run BFS from each node at which we’d like a new table, to a depth equal to the number of fields in t ...
nscan4 (PDF, 316 KiB)
... integers. The same fact was proved by Adleman and Odlyzko [1] under the assumption of several deep and unproved hypotheses from number theory. The generalization of our result to algebraic number fields and to polynomials in several variables is the subject of future publications. ...
... integers. The same fact was proved by Adleman and Odlyzko [1] under the assumption of several deep and unproved hypotheses from number theory. The generalization of our result to algebraic number fields and to polynomials in several variables is the subject of future publications. ...
Godel incompleteness
... Gödel's incompleteness theorems are very “dangerous” (yes, mostly to Hilbert's ideas), which makes them interesting, and therefore popular... but also misinterpreted! First of all, the theorem does not say that every axiomatic system is necessarily incomplete: for example, absolute geometry with th ...
... Gödel's incompleteness theorems are very “dangerous” (yes, mostly to Hilbert's ideas), which makes them interesting, and therefore popular... but also misinterpreted! First of all, the theorem does not say that every axiomatic system is necessarily incomplete: for example, absolute geometry with th ...
IOSR Journal of Computer Engineering (IOSR-JCE)
... Table 1 is the comparison results among DGA and SGA. Nbest denotes the number of times an optimal solution was found. Nmax,Nmean and Nsd denote the maximum, average convergence and standard deviation generations needed to find the optimal solutions, respectively. From the comparison results, we can ...
... Table 1 is the comparison results among DGA and SGA. Nbest denotes the number of times an optimal solution was found. Nmax,Nmean and Nsd denote the maximum, average convergence and standard deviation generations needed to find the optimal solutions, respectively. From the comparison results, we can ...
Predictive Job Scheduling in a Connection Limited System using
... Genetic Algorithm application level scheduling algorithm generates the initial population, evaluates each individual’s fitness, and performs genetic operations on the Individuals with high fitness such copying, crossover and mutation, to generate a new population. The genetic process continues with ...
... Genetic Algorithm application level scheduling algorithm generates the initial population, evaluates each individual’s fitness, and performs genetic operations on the Individuals with high fitness such copying, crossover and mutation, to generate a new population. The genetic process continues with ...
Predictive Job Scheduling in a Connection Limited System using
... Genetic Algorithm application level scheduling algorithm generates the initial population, evaluates each individual’s fitness, and performs genetic operations on the Individuals with high fitness such copying, crossover and mutation, to generate a new population. The genetic process continues with ...
... Genetic Algorithm application level scheduling algorithm generates the initial population, evaluates each individual’s fitness, and performs genetic operations on the Individuals with high fitness such copying, crossover and mutation, to generate a new population. The genetic process continues with ...
fundamentals of algorithms
... • Build solution to recurrence from bottom up. Write an algorithm that starts with base cases and works its way up to the final solution. Dynamic programming algorithms need to store the results of intermediate sub-problems. This is often but not always done with some kind of table. We will now cove ...
... • Build solution to recurrence from bottom up. Write an algorithm that starts with base cases and works its way up to the final solution. Dynamic programming algorithms need to store the results of intermediate sub-problems. This is often but not always done with some kind of table. We will now cove ...
WHAT IS AN ALGORITHM?
... and zeros, which make up a binary code. A sample instruction might be 100111000 01100110 Second-generation language- These are also called assembly languages and are characterized by abbreviated words, called mnemonics. A sample code might be ‘Add 12,8’ ...
... and zeros, which make up a binary code. A sample instruction might be 100111000 01100110 Second-generation language- These are also called assembly languages and are characterized by abbreviated words, called mnemonics. A sample code might be ‘Add 12,8’ ...
WHAT IS AN ALGORITHM?
... and zeros, which make up a binary code. A sample instruction might be 100111000 01100110 Second-generation language- These are also called assembly languages and are characterized by abbreviated words, called mnemonics. A sample code might be ‘Add 12,8’ ...
... and zeros, which make up a binary code. A sample instruction might be 100111000 01100110 Second-generation language- These are also called assembly languages and are characterized by abbreviated words, called mnemonics. A sample code might be ‘Add 12,8’ ...
The Multiple Knapsack Problem Approached by a Binary Differential
... to handle binary problems, in particular the 0-1 MKP. The BDE algorithm was first applied in [10] for the 0-1 MKP and the results obtained were promising. BDE consists in applying simple operators (crossover and bit-flip mutation) in candidate solutions represented as binary strings. In this work se ...
... to handle binary problems, in particular the 0-1 MKP. The BDE algorithm was first applied in [10] for the 0-1 MKP and the results obtained were promising. BDE consists in applying simple operators (crossover and bit-flip mutation) in candidate solutions represented as binary strings. In this work se ...