Xen and the Art of Virtualization
... Each guest OS has a timer interface and is aware of both ‘real’ and ‘virtual’ time. Virtual devices are elegant and simple to access. Data is transferred using asynchronous I/O rings. An event mechanism replaces hardware interrupts for notifications. Table 1: The paravirtualized x86 interface. guest ...
... Each guest OS has a timer interface and is aware of both ‘real’ and ‘virtual’ time. Virtual devices are elegant and simple to access. Data is transferred using asynchronous I/O rings. An event mechanism replaces hardware interrupts for notifications. Table 1: The paravirtualized x86 interface. guest ...
Chapter 6
... Solution to Critical-Section Problem MUST satisfy the following three requirements: 1. Mutual Exclusion - If process Pi is executing in its critical section, then no other processes can be executing in their critical sections 2. Progress - If no process is executing in its critical section and ther ...
... Solution to Critical-Section Problem MUST satisfy the following three requirements: 1. Mutual Exclusion - If process Pi is executing in its critical section, then no other processes can be executing in their critical sections 2. Progress - If no process is executing in its critical section and ther ...
Linked
... The OS picks and begins execution of one of these jobs. If the job needs to wait for an I/O device the OS switches to executing another job. The CPU therefore can be kept busy more of the time. We say these jobs are being run concurrently. This is an aspect of operating systems that adds much of its ...
... The OS picks and begins execution of one of these jobs. If the job needs to wait for an I/O device the OS switches to executing another job. The CPU therefore can be kept busy more of the time. We say these jobs are being run concurrently. This is an aspect of operating systems that adds much of its ...
Fonctionnement de la Messagerie Electronique or Email
... communiquer entre familles et amis. On dirait de préférence qu’une meilleure connaissance d’utilisation d’un système informatique est vraiment utile, nécessaire et indispensable à tous pour pouvoir maîtriser ses avantages en profitant de savourer le système de la globalisation pour une participation ...
... communiquer entre familles et amis. On dirait de préférence qu’une meilleure connaissance d’utilisation d’un système informatique est vraiment utile, nécessaire et indispensable à tous pour pouvoir maîtriser ses avantages en profitant de savourer le système de la globalisation pour une participation ...
operating- system concepts
... d. Real time. Often used in a dedicated application, this system reads information from sensors and must respond within a fixed amount of time to ensure correct performance. e. Network. Provides operating system features across a network such as file sharing. f. SMP. Used in systems where there are ...
... d. Real time. Often used in a dedicated application, this system reads information from sensors and must respond within a fixed amount of time to ensure correct performance. e. Network. Provides operating system features across a network such as file sharing. f. SMP. Used in systems where there are ...
STICS: SCSI-To-IP Cache for Storage Area Networks
... services. New standards and products emerge very rapidly for networked data storage. Given the mature Internet infrastructure, the overwhelming preference among the IT community recently is using IP for storage networking because of economy and convenience. iSCSI is one of the most recent standards ...
... services. New standards and products emerge very rapidly for networked data storage. Given the mature Internet infrastructure, the overwhelming preference among the IT community recently is using IP for storage networking because of economy and convenience. iSCSI is one of the most recent standards ...
OS Portal: an economic approach for making an embedded kernel
... former is used for a client to register itself to the OS Portal, while the latter is used to load a specific module from the OS Portal. The OS Portal performs the following tasks when it receives a REGISTRATION request. First, it authenticates the client (for security or billing purpose). In our curr ...
... former is used for a client to register itself to the OS Portal, while the latter is used to load a specific module from the OS Portal. The OS Portal performs the following tasks when it receives a REGISTRATION request. First, it authenticates the client (for security or billing purpose). In our curr ...
No Slide Title
... If the request cannot be granted immediately, the requesting process must wait to acquire the resource. The process can operate on the resource. ...
... If the request cannot be granted immediately, the requesting process must wait to acquire the resource. The process can operate on the resource. ...
INF 5070 – Media Storage and Distribution Systems
... avoid resource conflicts making worst-case reservations potentially under-utilized resources guaranteed QoS reserve according to average load high utilization overload may occur ...
... avoid resource conflicts making worst-case reservations potentially under-utilized resources guaranteed QoS reserve according to average load high utilization overload may occur ...
P2P
... r Single network called FastTrack used by other clients as well: Morpheus, giFT, etc. r Eventually protocol changed so other clients could no longer talk to it r popular file sharing network with >10 million users (number varies) ...
... r Single network called FastTrack used by other clients as well: Morpheus, giFT, etc. r Eventually protocol changed so other clients could no longer talk to it r popular file sharing network with >10 million users (number varies) ...
A Routing Underlay for Overlay Networks Department of Computer Science Princeton University
... recently proposed overlay services use similar approaches to topology discovery and self-organization, and for this reason, could benefit from a shared routing underlay. Such an underlay might also help some overlays take more scalable approaches to resource discovery. Below, we discuss a few repre ...
... recently proposed overlay services use similar approaches to topology discovery and self-organization, and for this reason, could benefit from a shared routing underlay. Such an underlay might also help some overlays take more scalable approaches to resource discovery. Below, we discuss a few repre ...
Classification of network topologies
... Topological ideas are present in almost all areas of today's mathematics. The subject of topology itself consists of several different branches, such as point set topology, algebraic topology and differential topology, which have relatively little in common. We shall trace the rise of topological co ...
... Topological ideas are present in almost all areas of today's mathematics. The subject of topology itself consists of several different branches, such as point set topology, algebraic topology and differential topology, which have relatively little in common. We shall trace the rise of topological co ...
Deadlocks - KSU Web Home
... processes such that P0 is waiting for a resource that is held by P1, P1 is waiting for a resource that is held by P2, …, Pn–1 is waiting for a resource that is held by Pn, and P0 is waiting for a resource that is held by P0. ...
... processes such that P0 is waiting for a resource that is held by P1, P1 is waiting for a resource that is held by P2, …, Pn–1 is waiting for a resource that is held by Pn, and P0 is waiting for a resource that is held by P0. ...
The Knowledge Level
... • Organizations may share resources only if the process is guaranteed to be secure. • There are various proposals for security on Grids, such as Grid Security Infrastructure (GSI), the Security Assertion Markup Language (SAML), etc. • WSNs are prone to security problems. • Techniques to address thes ...
... • Organizations may share resources only if the process is guaranteed to be secure. • There are various proposals for security on Grids, such as Grid Security Infrastructure (GSI), the Security Assertion Markup Language (SAML), etc. • WSNs are prone to security problems. • Techniques to address thes ...
paper
... Select a root vertex (any choice suffices) and build a depth-first search (DFS) numbering beginning at the root vertex. The collection route is a walk that traverses nodes as they are considered by the DFS numbering algorithm. Fig. 3 illustrates this process: thick, solid lines represent edges (arc ...
... Select a root vertex (any choice suffices) and build a depth-first search (DFS) numbering beginning at the root vertex. The collection route is a walk that traverses nodes as they are considered by the DFS numbering algorithm. Fig. 3 illustrates this process: thick, solid lines represent edges (arc ...
introduction
... Operating systems differ from user (i.e., application) programs in ways other than where they reside. In particular, they are huge, complex, and long lived. The source code of an operating system like Linux or Windows is on the order of five million lines of code. To conceive of what this means, thi ...
... Operating systems differ from user (i.e., application) programs in ways other than where they reside. In particular, they are huge, complex, and long lived. The source code of an operating system like Linux or Windows is on the order of five million lines of code. To conceive of what this means, thi ...
Topological Properties and Broadcasting Algorithms of the
... The node degree and diameter are key properties of the interconnection networks. The node degree is the maximum number of the neighbors of a node in the whole network and the diameter is the value of maximum shortest distance of all pairs of the nodes. Node degree represents the port number of a swi ...
... The node degree and diameter are key properties of the interconnection networks. The node degree is the maximum number of the neighbors of a node in the whole network and the diameter is the value of maximum shortest distance of all pairs of the nodes. Node degree represents the port number of a swi ...
P2P Systems and Technologies - Department of Computer Science
... Gnutella is not a system: it is a protocol, with various existing gnutella clients that implement it. Membership: Through a predefined static list with addresses or through “host caches”, a peer can connect to a set of gnutella clients. After connection a client expands its list of known addresses ...
... Gnutella is not a system: it is a protocol, with various existing gnutella clients that implement it. Membership: Through a predefined static list with addresses or through “host caches”, a peer can connect to a set of gnutella clients. After connection a client expands its list of known addresses ...
WIRELESS SENSOR NETWORKS
... finding system, power generator, and mobilizer. sensors and analog-to-digital converters (ADCs): The analog signals produced by the sensors based on the observed phenomenon are converted to digital signals by the ADC, and then fed into the processing unit. The processing unit, which is generally ass ...
... finding system, power generator, and mobilizer. sensors and analog-to-digital converters (ADCs): The analog signals produced by the sensors based on the observed phenomenon are converted to digital signals by the ADC, and then fed into the processing unit. The processing unit, which is generally ass ...
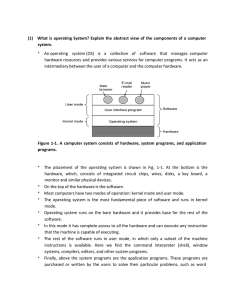
(1) What is operating System? Explain the abstract view of the
... Networks of tiny sensor nodes are being deployed (developed) for numerous purposes. These nodes are tiny computers that communicate with each other and with a base station using wireless communication. These sensor networks are used to protect the perimeters of buildings, guard national borders, det ...
... Networks of tiny sensor nodes are being deployed (developed) for numerous purposes. These nodes are tiny computers that communicate with each other and with a base station using wireless communication. These sensor networks are used to protect the perimeters of buildings, guard national borders, det ...
presentation source
... 1. Allow preemption. Not always possible (how to preempt a printer, tape drive, or other non-shareable resource?) 2. Avoid mutual exclusion: Create virtual instances, where each processes has the illusion of mutex (again, not always possible). 3. Avoid “Hold & Wait”: One technique is to force proces ...
... 1. Allow preemption. Not always possible (how to preempt a printer, tape drive, or other non-shareable resource?) 2. Avoid mutual exclusion: Create virtual instances, where each processes has the illusion of mutex (again, not always possible). 3. Avoid “Hold & Wait”: One technique is to force proces ...
Architectures for Disruption Tolerant Networking Implementation for
... No processor chip or A processor is embedded software component in the in FPGA design Higher reliability Reliability of software component to be addressed Fast realization of a flight Faster realization as worthy implementation protocol features are with minimum features implemented as software Diff ...
... No processor chip or A processor is embedded software component in the in FPGA design Higher reliability Reliability of software component to be addressed Fast realization of a flight Faster realization as worthy implementation protocol features are with minimum features implemented as software Diff ...
Distributed operating system
A distributed operating system is a software over a collection of independent, networked, communicating, and physically separate computational nodes. Each individual node holds a specific software subset of the global aggregate operating system. Each subset is a composite of two distinct service provisioners. The first is a ubiquitous minimal kernel, or microkernel, that directly controls that node’s hardware. Second is a higher-level collection of system management components that coordinate the node's individual and collaborative activities. These components abstract microkernel functions and support user applications.The microkernel and the management components collection work together. They support the system’s goal of integrating multiple resources and processing functionality into an efficient and stable system. This seamless integration of individual nodes into a global system is referred to as transparency, or single system image; describing the illusion provided to users of the global system’s appearance as a single computational entity.