Name (Please print legibly)
... a) Runs a new program in a child process. b) Provides an exact copy of the current process’s address space to an existing child process. c) Creates a new child process and gives it an exact copy of the current process’s address space. d) Creates a new child thread and gives it an exact copy of the c ...
... a) Runs a new program in a child process. b) Provides an exact copy of the current process’s address space to an existing child process. c) Creates a new child process and gives it an exact copy of the current process’s address space. d) Creates a new child thread and gives it an exact copy of the c ...
slides
... – API specifies behavior of the thread library, implementation is up to development of the library – Common in UNIX operating systems (Solaris, Linux, Mac OS X) ...
... – API specifies behavior of the thread library, implementation is up to development of the library – Common in UNIX operating systems (Solaris, Linux, Mac OS X) ...
Multicores
... 8, of 16 lanes per slot. Each lane has two pairs of wires from the switch to the device — one pair sends data, and the other pair receives data. This determines the transfer rate of the data. These lanes fan out from the switch directly to the devices where the data is to go. The PCI - E is a replac ...
... 8, of 16 lanes per slot. Each lane has two pairs of wires from the switch to the device — one pair sends data, and the other pair receives data. This determines the transfer rate of the data. These lanes fan out from the switch directly to the devices where the data is to go. The PCI - E is a replac ...
Chapter 2 Operating Systems Concepts
... — The OS allocates and controls system resources A process may need to communicate with other processes — The OS must provide communication mechanisms ...
... — The OS allocates and controls system resources A process may need to communicate with other processes — The OS must provide communication mechanisms ...
PPT - Surendar Chandra
... - Introduces a new kernel which outsources policy *and* some mechanisms to applications - Applications are made up of OS libraries (that interact with a non-portable exokernel). OS does not trust OS libraries. Hence, applications can trust the application libraries. ...
... - Introduces a new kernel which outsources policy *and* some mechanisms to applications - Applications are made up of OS libraries (that interact with a non-portable exokernel). OS does not trust OS libraries. Hence, applications can trust the application libraries. ...
Operating Systems Lab.
... An operating system's le system structure is its most basic level of organization. Almost all of the ways an operating system interacts with its users, applications, and security model are dependent upon the way it stores its les on a storage device. A file system can be seen in terms of two differe ...
... An operating system's le system structure is its most basic level of organization. Almost all of the ways an operating system interacts with its users, applications, and security model are dependent upon the way it stores its les on a storage device. A file system can be seen in terms of two differe ...
Real-Time Operating Systems Lecture for the Embedded Systems
... All tasks in the same priority share the CPU Context Switch in each (predefined) time slice period Real-Time Operating Systems ...
... All tasks in the same priority share the CPU Context Switch in each (predefined) time slice period Real-Time Operating Systems ...
Microsoft`s Disk Operating System CS-550
... The transient portion is primarily responsible for interpreting user commands. It is loaded into high memory where, if necessary, it can be overlaid by application programs. With newer versions of DOS installed on systems with more memory, this feature is not as important since main memory sizes hav ...
... The transient portion is primarily responsible for interpreting user commands. It is loaded into high memory where, if necessary, it can be overlaid by application programs. With newer versions of DOS installed on systems with more memory, this feature is not as important since main memory sizes hav ...
Process Management
... in ready queue or in blocked queue (depending on circumstances) – When an event occurs, all the processes waiting on that event are moved from blocked queue onto ready queue. ...
... in ready queue or in blocked queue (depending on circumstances) – When an event occurs, all the processes waiting on that event are moved from blocked queue onto ready queue. ...
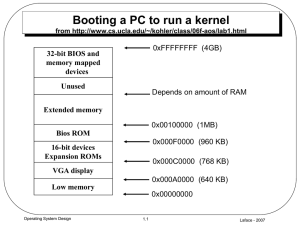
Booting a PC
... Operating system kernels often like to be linked and run at very high virtual address, such as 0xf0100000, in order to leave the lower part of the processor's virtual address space for user programs to use. ...
... Operating system kernels often like to be linked and run at very high virtual address, such as 0xf0100000, in order to leave the lower part of the processor's virtual address space for user programs to use. ...
os02_syllabus
... Email: [email protected], URL: http://www.cis.nctu.edu.tw/~ydlin Course Objective: This course covers classic materials of modern operating systems which control computer hardware to provide services to application programs. After a brief overview of computer systems and operating systems, we re ...
... Email: [email protected], URL: http://www.cis.nctu.edu.tw/~ydlin Course Objective: This course covers classic materials of modern operating systems which control computer hardware to provide services to application programs. After a brief overview of computer systems and operating systems, we re ...
Process Scheduling
... Any process that does not share data with any other process is independent. A process is cooperating if it can affect or be affected by the other processes executing in the system. There are several reasons for providing an environment that allows process cooperation: • Information sharing. Since se ...
... Any process that does not share data with any other process is independent. A process is cooperating if it can affect or be affected by the other processes executing in the system. There are several reasons for providing an environment that allows process cooperation: • Information sharing. Since se ...
Chapter 3: Operating Systems
... Memory Manager • Allocates space in main memory • May create the illusion that the machine has more memory than it actually does (virtual memory) by playing a “shell game” in which blocks of data (pages) are shifted back and forth between main memory and mass storage ...
... Memory Manager • Allocates space in main memory • May create the illusion that the machine has more memory than it actually does (virtual memory) by playing a “shell game” in which blocks of data (pages) are shifted back and forth between main memory and mass storage ...
1.01 - Fordham University
... Timer: generated by a timer with CPU I/O: generated by I/O controller to signal completion of operation or error condition Hardware failure: triggered by power failure, memory parity error… An operating system is interrupt driven. ...
... Timer: generated by a timer with CPU I/O: generated by I/O controller to signal completion of operation or error condition Hardware failure: triggered by power failure, memory parity error… An operating system is interrupt driven. ...
PPT Chap 1103
... – Graphical user interface (GUI) • Kernel: Performs basic required functions – File manager – Device drivers – Memory manager – Scheduler and dispatcher Copyright © 2012 Pearson Education, Inc. ...
... – Graphical user interface (GUI) • Kernel: Performs basic required functions – File manager – Device drivers – Memory manager – Scheduler and dispatcher Copyright © 2012 Pearson Education, Inc. ...
Operating System
... Since both processes do not have all the resources they need to execute, they are in a permanent state of suspension. Thus the scheduler must be responsible for detecting deadlock and removing it. ...
... Since both processes do not have all the resources they need to execute, they are in a permanent state of suspension. Thus the scheduler must be responsible for detecting deadlock and removing it. ...
Notes
... PC – Program Counter, contains the address of the next instruction to be fetched from memory. IR – Instruction Register, contains the instruction most recently fetched. MAR &memory_buffer /* Address of buffer location for next read or write. */ MBR (&memory_buffer) /* Contains data to be written ...
... PC – Program Counter, contains the address of the next instruction to be fetched from memory. IR – Instruction Register, contains the instruction most recently fetched. MAR &memory_buffer /* Address of buffer location for next read or write. */ MBR (&memory_buffer) /* Contains data to be written ...
Lecture_01
... distribution. Most users consider it a more stable and reliable OS than Windows. It's an alternative to Microsoft's dominance of the software market. It is multi-tasking, multi-user. Good support of multiple CPUs. Many utilities and APIs are now included in most distributions, like the g++ compiler, ...
... distribution. Most users consider it a more stable and reliable OS than Windows. It's an alternative to Microsoft's dominance of the software market. It is multi-tasking, multi-user. Good support of multiple CPUs. Many utilities and APIs are now included in most distributions, like the g++ compiler, ...
Module 3: Operating
... – in case of errors: print message and exit – if no error: a loop where characters are read from file1 and copied to file2 (2 system calls, with possible errors returned in case of a problem, such as space on disk exhausted) – close both files – terminate ...
... – in case of errors: print message and exit – if no error: a loop where characters are read from file1 and copied to file2 (2 system calls, with possible errors returned in case of a problem, such as space on disk exhausted) – close both files – terminate ...
presentation source
... no deadlock will occur. VMS uses a timer of 10 seconds after a resource request is started. If when the timer goes off the request is still not granted then the deadlock detection/recovery algorithm is invoked. – Recovery from the deadlock can involve a number of techniques: • Rollback - return a pr ...
... no deadlock will occur. VMS uses a timer of 10 seconds after a resource request is started. If when the timer goes off the request is still not granted then the deadlock detection/recovery algorithm is invoked. – Recovery from the deadlock can involve a number of techniques: • Rollback - return a pr ...
Operating Systems: Principles and Practice, Introduction
... • Sole interface between user and kernel • Implemented as library routines that execute trap instructions to enter kernel • Errors indicated by returns of –1; error code is in errno ...
... • Sole interface between user and kernel • Implemented as library routines that execute trap instructions to enter kernel • Errors indicated by returns of –1; error code is in errno ...
Abstract View of System Components
... – Part of PSW in Motorola architecture When an interrupt or fault occurs hardware switches to monitor mode. ...
... – Part of PSW in Motorola architecture When an interrupt or fault occurs hardware switches to monitor mode. ...
os03_syllabus
... Email: [email protected], URL: http://www.cis.nctu.edu.tw/~ydlin Course Objective: This course covers classic materials of modern operating systems which control computer hardware to provide services to application programs. After a brief overview of computer systems and operating systems, we re ...
... Email: [email protected], URL: http://www.cis.nctu.edu.tw/~ydlin Course Objective: This course covers classic materials of modern operating systems which control computer hardware to provide services to application programs. After a brief overview of computer systems and operating systems, we re ...
NGSCB
... Human nature to control over things and not to be controlled by others. “People will not use it if it blocks and restricts them doing what they want to do.” Quote NGSCB will fails: Companies will not tolerate attestations on the network and through the firewall every time their employee wants to ...
... Human nature to control over things and not to be controlled by others. “People will not use it if it blocks and restricts them doing what they want to do.” Quote NGSCB will fails: Companies will not tolerate attestations on the network and through the firewall every time their employee wants to ...