Computational Number Theory - Philadelphia University Jordan
... But, how about security? What if a bad guy intercepts the secret message s, together with e and n? Well, he will yet have to find d in order to read the message, and that in turn he also will need the factors p and q in order to compute φ. Woe to him, n = pq has over 200 digits and factoring a large ...
... But, how about security? What if a bad guy intercepts the secret message s, together with e and n? Well, he will yet have to find d in order to read the message, and that in turn he also will need the factors p and q in order to compute φ. Woe to him, n = pq has over 200 digits and factoring a large ...
File
... For example, the answer is always your age repeated three times. 8. ANS: In step 2, the “4” in “n + 4” was not multiplied by 2. In step 3, the expression on the left should be 2n + 8. 9. ANS: ...
... For example, the answer is always your age repeated three times. 8. ANS: In step 2, the “4” in “n + 4” was not multiplied by 2. In step 3, the expression on the left should be 2n + 8. 9. ANS: ...
Limit velocity and zero--one laws for diffusions in
... We prove that multidimensional diffusions in random environment have a limiting velocity which takes at most two different values. Further, in the two-dimensional case we show that for any direction, the probability to escape to infinity in this direction equals either zero or one. Combined with our ...
... We prove that multidimensional diffusions in random environment have a limiting velocity which takes at most two different values. Further, in the two-dimensional case we show that for any direction, the probability to escape to infinity in this direction equals either zero or one. Combined with our ...
Fermat`s little theorem, Chinese Remainder Theorem
... is congruent to a sum of thirty zeroes (the cases ai ≡ 0) and ones, with at least one one. Therefore it is congruent to a nubmer between 1 and 30, and so not divisible by 31. ...
... is congruent to a sum of thirty zeroes (the cases ai ≡ 0) and ones, with at least one one. Therefore it is congruent to a nubmer between 1 and 30, and so not divisible by 31. ...
a classification of gaussian primes
... having a norm of two, so any number that divides them must have a norm of either one or two, a fact provided by lemma 1 or 2, take your pick. But now we’re in troublesome territory, for if we factor one of them, say σ, as σ = α · β then one of the two factors must have a norm of one, and hence it wi ...
... having a norm of two, so any number that divides them must have a norm of either one or two, a fact provided by lemma 1 or 2, take your pick. But now we’re in troublesome territory, for if we factor one of them, say σ, as σ = α · β then one of the two factors must have a norm of one, and hence it wi ...
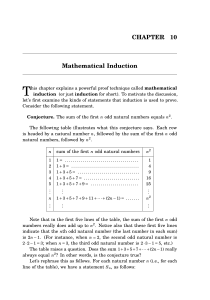
Mathematical Induction - Penn Math
... For more examples of the constructive uses of induction, including the FFT, Quicksorting, finding maximum independent sets in graphs, etc., you can download Chapter 2 of Algorithms and Complexity from ...
... For more examples of the constructive uses of induction, including the FFT, Quicksorting, finding maximum independent sets in graphs, etc., you can download Chapter 2 of Algorithms and Complexity from ...
A formally verified proof of the prime number theorem
... Overview of the formalization Some statistics regarding length, and time, are given in the associated paper. A lot of time and effort was spent: • Building basic libraries of easy facts. ...
... Overview of the formalization Some statistics regarding length, and time, are given in the associated paper. A lot of time and effort was spent: • Building basic libraries of easy facts. ...
Chapter 12 - Princeton University Press
... ourselves to proving the k = 2 case for very special α, which highlight how the algebraic structure of α can enter proofs as well as the different notions of sizes of sets. There are other methods to prove this theorem which can handle larger classes of α; we have chosen the method below because of ...
... ourselves to proving the k = 2 case for very special α, which highlight how the algebraic structure of α can enter proofs as well as the different notions of sizes of sets. There are other methods to prove this theorem which can handle larger classes of α; we have chosen the method below because of ...
Random geometric complexes in the thermodynamic regime
... shown to hold for all the complexes listed above, most of our arguments should easily extend to obtain similar theorems for these cases as well. ...
... shown to hold for all the complexes listed above, most of our arguments should easily extend to obtain similar theorems for these cases as well. ...
patterns in continued fraction expansions
... It is well known that any real number has a unique (or almost unique) decimal expansion. Since we do not typically write an infinite string of zeros down, these expansions can be either finite or infinite. For instance in base 10, 31/25 has decimal expansion 1.24, 1/3 has decimal expansion 0.3333…. ...
... It is well known that any real number has a unique (or almost unique) decimal expansion. Since we do not typically write an infinite string of zeros down, these expansions can be either finite or infinite. For instance in base 10, 31/25 has decimal expansion 1.24, 1/3 has decimal expansion 0.3333…. ...
Fermat's Last Theorem

In number theory, Fermat's Last Theorem (sometimes called Fermat's conjecture, especially in older texts) states that no three positive integers a, b, and c can satisfy the equation an + bn = cn for any integer value of n greater than two. The cases n = 1 and n = 2 were known to have infinitely many solutions. This theorem was first conjectured by Pierre de Fermat in 1637 in the margin of a copy of Arithmetica where he claimed he had a proof that was too large to fit in the margin. The first successful proof was released in 1994 by Andrew Wiles, and formally published in 1995, after 358 years of effort by mathematicians. The theretofore unsolved problem stimulated the development of algebraic number theory in the 19th century and the proof of the modularity theorem in the 20th century. It is among the most notable theorems in the history of mathematics and prior to its proof it was in the Guinness Book of World Records for ""most difficult mathematical problems"".